Goal (Specific, measurable, attainable, relevant, timely)
- The main goal is to deliver security protection over Cloud to savvy mobile device users (software version) and businesses (hardware version). “Security, trust, dependability and privacy are issues that have to be considered over the whole life-cycle of the system and software development from gathering requirements to deploying the system and service in practice” (Röning).
- Secondly, to popularise our Cloud Sec market by the late of 2012. Looking to the fact that mobile phones are becoming popular, it is expected that if a proper marketing plan is formulated, the product Clod Sec will be a huge success.
- Finally, to bring revolution in the security aspect of smart mobile device sector. The number of mobile users is increasing day by day and so are the frauds pertaining to mobile phone users. The mobile culture has overrun the sales of all devices. “Mobile is disrupting many industries – two of the most prominent being media and commerce and it is all driven by how consumers perceive the value of mobility, how they interact with content and devices” (Sharma). In such circumstances, it is the necessity of the moment that some security is provided to the mobile phone users.
Value propositions – benefits
- Security- Our product is aiming to provide enhanced security over Cloud, which includes user’s day to day software applications. If you feel unsecure because the photo in your iPhone automatically goes into Cloud and it can be exposed to others via text messaging between friends then Cloud Sec will make you feel secure.
- Seamless integration- Cloud Sec provides seamless integration to all of the current smart mobile devices that use a software market. The user interface is very friendly which brings high simplicity. All that the users need to do is to have our product downloaded and installed on their smart devices with a few presses in setting up. Cloud Sec will operate in the background just like the antivirus software on your PC.
- Economical- Cloud Sec has similar functions as VPN, but is a lot cheaper. With Cloud Sec application, you only need to make single purchase and receive benefits of multiple applications and lifetime updating.
- Mass market- Unlike VPN which is costly for individual to apply, Cloud Sec is ideal for individuals and is also designed to be powerful for business demands. Cloud Sec has software version which will be available for download via the Android and Apple markets. It also has hardware version which could be likened to Google servers. For businesses that demand additional security to their already full product line, Cloud Sec is the best choice.
Value Chain
The sudden rise of Skype to be globally accepted as a favoured means of communication shocked the entire telecommunication sector. Actually, the one who starts any particular feature is always the winner. “Fuelled by the increasing saturation of mobile technology, such as phones and personal digital assistants (PDAs), m-commerce promises to inject considerable change into the way certain activities are conducted” (Barnes).
The investment done by the promoters of Skype was not much but the idea was unique and people liked it. Similarly, by launching Clod Sec we expect to have the benefits of the torch bearers. Being reasonable priced and of innovative idea, our product is bound to have an encouraging response from the masses.
Trade Offs (Can’t be the best & cheapest at the same time)
As we initially target the mass market with pricing at $29.95, we lose the significant opportunity to position Cloud Sec in the field of high-level software application. This creates major challenge if we want to enter into high-level software application market later as our business successfully grows. However, in return we receive characteristic of affordability and revenue at the beginning of product launch.
As Cloud Sec heavily positions itself as security appliance, it may face tough competition immediately after its launch. As a result, market share could be possible to be taken by other innovative and competitive similar security appliances. However, the centralised focus on security will have large impact on customer like the way Google did.
When Google came out, its design was very focused as just a simple search bar on the webpage. Although many better search engines came out later on, but Google by that time had already dominated the market. Similarly, Cloud Sec initially is very focused on providing security support. Therefore an equal sign is there when ever customers hear Cloud Sec or security.
FIT (How to keep on being the best?)
In the introduction and growth stages of product “Cloud Sec” lifecycle, we only focus on one market which mainly targets at providing security. We run the business with previously stated objectives and our product uniqueness. In the mature stage of product lifecycle, we will still focus on developing “Cloud Sec” competitive advantage based on its natural core functions.
However, we may introduce new features and extend the business to reflect the market. As the market and customer needs are highly unpredicted, we have organised team structure and clear assignment of responsibilities as shown in the following diagram. “Organizational structure is particularly important for decision making” (Suttle). We have each part of the business integrated with others in managing to deliver the right product to the demanded users in a timely manner.
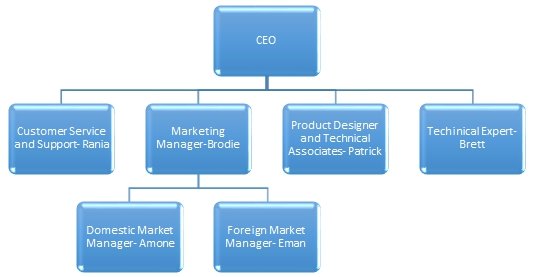
Continuity of Direction
Periodic meetings help in understanding the latest market trends. The business can be followed up constantly and if any changes in the plan are felt necessary, the same can be done. As a result, the business is expected to be on the right track. “Directors may find it makes sense to set up a schedule of periodic meetings – to be held quarterly, for example – that take place on certain fixed dates” (Steingold & Steingold 2010).
It is very important to do frequent analysis of the business. There are various methods available but the most commonly used methods are the SWOT analysis and the PESTEL analysis. SWOT means the strengths, weaknesses, opportunities and threats of any business. PESTEL means the political, economical, social, technological, environmental and legal aspects that may have impact on any business.
Doing these analyses will bring forward all the facts and figures of the business. “To help make decisions and to plan for future events, organizations need to understand the wider ‘meso-economic’ and ‘macro-economic’ environments in which they operate” (CIPD). We surely will benefit from these analyses.
Customer satisfaction is of utmost importance in any sort of business. The feedback from customers, by way of surveys, will help us in knowing the drawbacks and plus points of our product. Simultaneously, we can make the required changes in our product to make it more user-friendly. “A business is composed of a number of different people who exert influence on the company’s buying decision, while a consumer is a person who conclusively makes the purchasing decision” (Manalastas 2010).
We understand that proper monitoring is required in order to ascertain that we are on the right path and are working towards achieving our goals. A better way to achieve goals is to set milestones. This makes the process of achieving goals easier and the business moves ahead in a systematic manner. “Monitoring allows correcting before it’s too late, and allows uncovering drift away from the goals, or costly ‘repairs’ if the goals aren’t being achieved” (Bacal).
References
Bacal, R., How does Monitoring Progress Towards Strategic Goals Result in Better Implementation? Web.
Barnes, S. J. 2002, ‘The Mobile Commerce Value Chain: Analysis and Future Developments’, International Journal of Information Management, vol. 22, pp. 91-108.
CIPD 2010, PESTLE Analysis. Web.
Manalastas, R. C. 2010, How to Ensure Customer Satisfaction in Business-to-business (B2B) Selling Relationship. Web.
Röning, J., Cloud Security. Web.
Sharma, C. 2012, Mobile Breakfast Series – How Mobile is Impacting Media, Commerce, and Consumer Behaviour. Web.
Steingold, F. S. & Steingold, F 2010, Legal Forms of Starting & Running a Small Business, Nolo, USA.
Suttle, R., The Importance of Organizational Structure. Web.