Introduction
Every organization wants a rigid and high-quality information technology security system that can make it safe, preventing devastating cyber crimes from occurring. Significantly, corporations have the responsibility of ensuring the safety of customers’ and other stakeholders’ personal information. When a company is establishing a system, which can guarantee the highest degree of cybersecurity, it must focus on the dexterity of different options, hence making the appropriate decisions regarding the most effective framework. Denotatively, COBIT5 is a globally comprehensive and recognized business-oriented framework, helping companies to make the best use of their information technology by providing a management and governance outline for enterprises (Astuti et al., 2017). The Information Technology Infrastructure Library (ITIL4) is an advanced framework, having detailed practices of IT service management (ITSM) which focuses on aligning the IT function with the business needs. Therefore, ITIL4 is the better option for cybersecurity over COBIT5, considering that it incorporates different experts throughout the world to formulate the most effective cybersecurity platforms hence reducing hacking incidents.
Background
Adding more IT-related systems to the management of a business company is critical, especially regarding the IT assets and business processes. According to Patón-Romero et al. (2017), different frameworks offer blueprints for attaining organizational goals, including security and compliance. Holistically, there are three popular information technology frameworks of governance which are ITIL4, COBIT5, and TOGAT. Various enterprises globally use these frameworks, hence need to advise on the most effective to bolster cybersecurity and enhance digital resilience.
COBIT5 is created by the Information Systems Audit and Control Association (ISACA) and the IT Governance Institute. The Control Objectives for Information and Related Technology (COBIT) significantly help organizations in the creation, maintenance, and monitoring of IT management and governance practices (Patón-Romero et al., 2017). Currently, COBIT is on its sixth version (COBIT 2019), heavily used by the IT business process, stakeholders, and managers to ensure reliability control and subsequent quality of the information systems within a business organization. The current framework version, COBIT5 promotes shorter feedback loops, better agility, and collaboration, hence being effective in reducing different risks in IT implementation (Patón-Romero et al., 2017). In other words, the framework ensures that an organization effectively uses the IT approach in coordinating its different functions. Connectedly, COBIT5 ensures that an organization oversees its services and progress in a single interface.
Discussions about ITIL4 surround IT service management and even ITSM. Significantly, ITSM is the alignment of information systems and enterprise IT services with business and the needs of the customer who is the end-user. ITIL4 regards IT as a critical mode of delivering value to the customer and business, as opposed to just installing, managing, and securing technology (Nachrowi et al., 2020). ITIL is considered to be the preeminent framework for the implementation of ITSM in business companies. It is trademarked and created by AXELOS, receiving massive adoption from millions of certified enterprises globally (Nachrowi et al., 2020). ITIL offers a series of excellent practices which are interconnected, hence subsequently giving guidance for managing, delivering, and developing IT-related services. Thus, the fourth version of ITIL has been structured to ensure excellent customer experience while interacting with the organization.
Methodology and Data Collection
Formulating an effective research methodology requires one to comprehend the research question. The study query aims at comparing the effectiveness of COBIT5 and ITIL4 frameworks in cybersecurity. Primarily, the research applies the secondary data method, comparing different pieces of literature on the topic. According to Ruggiano and Perry (2019), the secondary data approach incorporates the analysis of data that has already been collected through the different primary sources and subsequently made accessible to the various researchers for use. Significantly, several materials are outlining the effectiveness and importance of both the COBIT and ITIL frameworks and how effective an organization can become by embracing either of the set. In addition, the secondary data method will aid in understanding the diverse areas that each of the outlines best fits and their subsequent abilities, hence deciding on the most effective between the two for better cyber-security. Therefore, this study will majorly depend on the secondary data method, presenting the workability and efficiency of the COBIT5 and ITIL4 systems, enhancing recommendations formulation regarding the most effective framework that business entities can adopt.
Additionally, this research will employ the documents and records data collection method as part of the descriptive analysis approach. The collection method is grounded theory which is an alternative to interviews and observation. Interpretatively, the documents and records information collection formula focus on different studies which have been conducted on the topic of research and furthering the study (Gattiker et al., 2016). The reputability and expertise of the authors dictate whether a researcher can use the specific information provided and its relevancy. This research will use the available data that relates to the research question from scholarly sources and researchers that are experts in the area of information technology.
Discussion and Analysis
Effective cybersecurity requires business organizations to take a continuous and layered approach to security. Van Grembergen and De Haes (2018) opine that the adoption and embracement of risk-based thinking is a critical mantra in digital resilience. Understandably, before a corporation decides regarding the necessary framework to adopt between the COBIT5 and ITIL4, it must have a full overview of the risks, investments, and control in security to attain excellent business outcomes. These two systems differ in terms of audience and scope. According to Berger et al. (2020), ITIL is considered as an IT service framework that provides more guidance in the IT arena. Moreover, COBIT is relatively broader than ITIL, whereby it provides a narrative that is more detailed regarding the issue of service management enabler within the enterprise’s information technology system (Berger et al., 2020). Connectedly, these two approaches are excellent and can be used interchangeably to achieve better security, digital resilience, and organizational compliance.
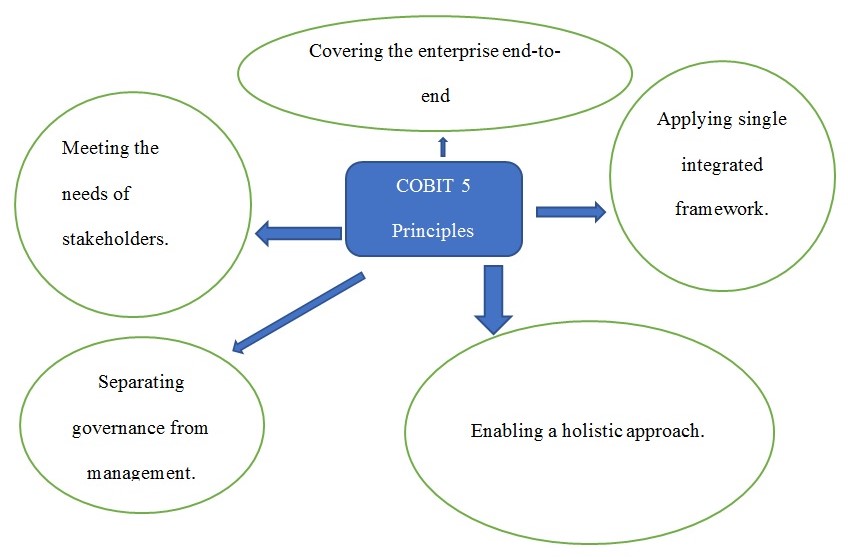
COBIT5 has a robust set of best practices that organizations can use ineffective information technology management. Chaudhari and Mulgund (2018) allude that COBIT’s primary principles provide guidelines that can help a corporation improve its service delivery. Statistically, one of the COBIT5 principles is to meet the needs of the stakeholders (Chaudhari & Mulgund, 2018). An organization needs to set concrete and appropriate IT objectives and KPIs, authenticating a critical path to meet the stakeholder needs. COBIT allows organization management to assign individual duties to employees. As a result, the employees comprehend the specific areas to maintain within the system. Covering the enterprise end-to-end is the second principle of the COBIT5 (Chaudhari & Mulgund, 2018). The system information updates the corporation members regarding the information assets which facilitate their service design needs and business objectives. The third principle in the COBIT5 principle is separating management from governance (Chaudhari & Mulgund, 2018). Therefore, the principles of COBIT’s best practices make it a significant framework that is better for cyber-security as shown in figure 1 below.
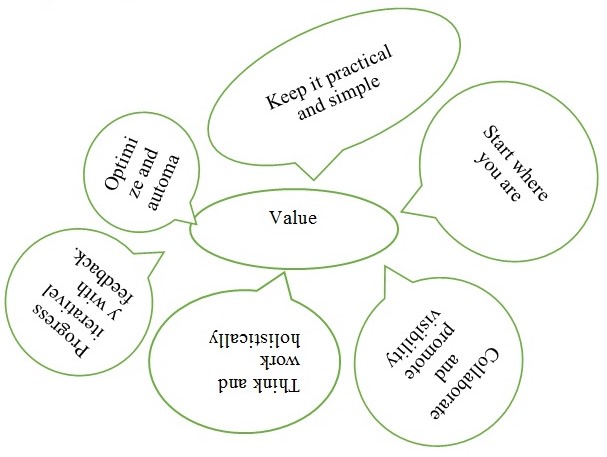
ITIL resembles COBIT, in that, it comes with a significant set of principles which inspire different best practices for the business company’s information technology service management. According to Borges (2018), there are seven guiding principles for ITIL, which are eventually ingrained in the ITIL activities and processes, making it more straightforward for corporation structures to benefit from it. The regulations include a focus on value, commence from scratch and progress depending on feedback, promote and collaborate visibility, work and think holistically, keep it practical and straightforward, and lastly automate and optimize (Borges, 2018). Significantly, the ITIL framework upholds that continuous improvement is key to an organization success in the implementation of the IT system. Continual improvement model adoption is a best practice which lets the organization management think and develop an iterative approach to the vision of the organization. Borges (2018) further notes that ITIL4 promotes the adoption of the service value chain approach. Thus, ITIL has seven principles which enhance effective functionality of the organization as shown in figure 2 below.
Findings
Both the COBIT5 and ITIL4 information technology service management standards have traversed critical revamps in the previous years. Distinctively, COBIT5 superseded COBIT4.1, and it was launched in the year 2012 being more flexible since it incorporates collaborative strategies of governance (Chaudhari & Mulgund, 2018). The service provides fluid and frequent updates to aid in addressing changing and new technology. Contrary, ITIL4 system development embraces a more community-based approach, whereby it collaborates with the broader information technology experts and industry globally to update ITIL features for future present and future effectiveness. Connectedly, whereas COBIT5 provides regular and fluid updates to help in addressing the shifting technological trends, ITIL4 works collaboratively with multiple companies which use the same technology and experts worldwide to ensure topnotch security.
ITIL4 is the latest trend and update in the ITIL framework. It updates the framework according to the latest IT developments, and holistic software realms (Nachrowi et al., 2020). Arguably, the ITIL4 focus is towards providing a more practical and flexible foundation to support a business corporation’s endeavors for making critical steps and progress towards the new digital transformation world. The system has four dimensions that should be part of the IT program of service management within a business. The dimensions include people and organizations, information and technology, suppliers and partners, and lastly processes and value streams. Holistically, the ITIL4 principles and dimensions project towards enhancing effective service delivery and communication within an organization.
The organizations adopting COBIT5 and ITIL4 range from educational and government institutions to the large Fortune 500 corporations around the world. Astuti et al. (2017) develop case studies regarding the different companies that have implemented either the COBIT or ITIL systems successfully. This gives the audience an understanding of the frameworks’ coordination, hence making informed decisions concerning the most effective approach. According to Chaudhari and Mulgund (2018), Maitland is one of the companies on a global perspective which has implemented the COBIT5 system. This advisory firm implemented COBIT5 to increase information technology accountability and business oversight. Moreover, the European Network of Electricity Transmission System Operators (ENETSO) is another electricity supply corporation that implements COBIT5 for the governance of IT enterprise. Comparatively, Spotify and Newcastle University are among the many institutions that have implemented the ITIL4 system’s framework. In 2017, Spotify used ITIL4 to necessitate its objective of going public and expanding its reputation (Chaudhari & Mulgund, 2018). In addition, Newcastle University, an Australian institution adopts ITIL4 to improve incidence management and subsequently address other business problems (Chaudhari & Mulgund, 2018). Therefore, various organizations are adopting the framework which serves their interests.
Both COBIT5 and ITIL4 offer ample learning resources which guide the organization implementation, from the white papers to the framework documentation, which are helpful for an organization to conduct online conferences and training. For COBIT5, meetings, online resources, and white papers are coordinated to support business goals. In contrast, ITIL4 offers resources plethora, enabling the team to implement ITIL standards (Berger et al., 2020). Groups like LinkedIn and Educause ITSM Community Group bring the world together for discussions surrounding the ITIL topic.
Lessons, Limitation, and Recommendations
The lesson learned is that different enterprises should choose ITIL4 because it is the best systems framework for their productivity and efficiency. Every organization should strategically analyze and comprehend its abilities before deciding the exact framework to adopt. Moreover, implementing an information technology service strategy like ITIL4 or COBIT5 can effectively lead to organization expansion. Institutions become competent and able to manage service transition and change, improving incident management, and equally developing a more service-oriented culture which better serves the needs of the different customers. A business company can combine these two frameworks where necessary to tailor the implementation to the enterprise needs.
The limitation of this research is that it lacks to incorporate other system frameworks which work towards combating cyber threats. The study only presents a comparison between the COBIT5 and ITIL4, leaving the TOGAF framework outside. Other organizations can find TOGAF more proficient compared to both COBIT5 and ITIL4. Therefore, the study should have presented the other frameworks, to enable different organizations make a holistic decision about the exact program to uphold. Another limitation is that the research compares COBIT5 and ITIL4, whereby the latter is outdated since it is superseded by COBIT 2019. The study is old-fashioned, considering that it compares an old system to a new ITIL4 model. Therefore, the non-inclusion of all the system frameworks and the comparison of COBIT5, which is old-fashioned with ITIL4 are the significant limitations of the study.
The study develops a recommendation that ITIL4 is a better option for cybersecurity because of the excellent pros that are associated with it. The framework allows global integration with corporations that embrace the system with experts. As a result, an institution becomes aware of the trending incidences of cybersecurity and combating emerging threats. ITIL4 equips the service providers with a capability model, aligning them to customer needs and business strategy. The framework will aid businesses to navigate successfully through this new era of technology.
Conclusion
In summation, companies yearning to apply repeatability and structure to their information security and the subsequent compliance efforts critically must embrace the ITIL4 systems framework. Notably, cybersecurity digital resilience and efficacy are extraordinary measures per organization and can subsequently be attained through different framework arrays that are relevant to the business. Digital resiliency and cybersecurity should be enhanced from security, integrity, and even the compliance angle. Above all, further research needs to be conducted on the different approaches that can be applauded to improve cybersecurity and digital resilience, in general.
References
Astuti, H. M., Muqtadiroh, F. A., Darmaningrat, E. W. T., & Putri, C. U. (2017). Risks assessment of information technology processes based on COBIT 5 framework: A case study of ITS service desk. Procedia Computer Science, 124(1), 569-576. Web.
Berger, D., Shashidhar, N., & Varol, C. (Eds.) (2020). Using ITIL 4 in Security Management. In 2020 8th International Symposium on Digital Forensics and Security (ISDFS), IEEE Xplore. Web.
Borges, B. S. L. (2018). Comparison of COBIT 5 and ITIL V3 using Semantic Analysis. Semantic Scholar. Web.
Chaudhari, G., & Mulgund, P. (2018). Strengthening IT governance with COBIT 5. In Information Technology Risk Management and Compliance in Modern Organizations, IGI Global, 48-69. Web.
Gattiker, A. E., Gebara, F. H., Hylick, A. N., & Kanj, R. N. (2016). Document retrieval using internal dictionary-hierarchies to adjust per-subject match results. Patent and Trademark Office. Web.
Nachrowi, E., Nurhadryani, Y., & Sukoco, H. (2020). Evaluation of governance and management of information technology services using Cobit 2019 and ITIL 4. Journal Rest, 4(4), 764-774. Web.
Patón-Romero, J. D., Baldassarre, M. T., Piattini, M., & García Rodríguez de Guzmán, I. (2017). A governance and management framework for green it. Sustainability, 9(10), 1761. Web.
Ruggiano, N., & Perry, T. E. (2019). Conducting secondary analysis of qualitative data: Should we, can we, and how?Qualitative Social Work, 18(1), 81-97. Web.
Van Grembergen, W., & De Haes, S. (2018). Introduction to the Minitrack on IT Governance and its Mechanisms. In Proceedings of the 51st Hawaii International Conference on System Sciences. Web.