Abstract
Network resources should be available to legitimate users whenever they are demanded. The concept of network security has emerged to prevent any unauthorized modification or access to computer systems. Such features address the problem of network attacks and support the goals of programmers, organizations, and institutions. Despite such measures, the global society continues to grapple with the problem of denial-of-service (DoS) attacks.
These attacks present one of the greatest challenges to all Internet users. The selected research papers indicate that DoS attacks pose numerous challenges in different networks. Fortunately, the authors acknowledge that exerts have managed to identify and present various mechanisms to minimize the problems associated DoS attacks. The papers acknowledge that new studies are needed in order to have a clear understanding of different DoS attacks.
Such an achievement will present or inform the creation of efficient strategies and procedures to combat any form of DoS attack. Some of the articles provide detailed analyses of the existing measures to deal with DoS attacks and provide meaningful evaluations that can guide future research studies. The purpose of this discussion is to give a detailed summary of the proposed solutions and provide evidence-based propositions that can result in effective defense mechanisms against all DoS attacks.
Introduction
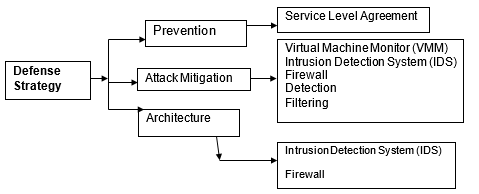
The presented paper gives a comparative analysis of the solutions proposed by four different papers and offers evidence-based proposals to mitigate the targeted problem. The first one is “A Survey of Denial-of-Service and Distributed Denial of Service Attacks and Defenses in Cloud Computing” and it proposes several techniques for dealing with DoS attacks. These are grouped into these three categories: prevention (service level agreement), attack mitigation (filtering, detection, firewall, ad virtual machine monitor), and architecture (firewall, cryptography, and intrusion detection system).
The second paper is “An Attack Detector Based on Statistical Approach for Detection and Prevention of DDoS Attack”. According to this article, two methods have the potential to prevent DoS attacks. The first category is composed of these general techniques: firewalls, updated security patches, and global defense infrastructure. The article also encourages users to disable all unutilized resources or services (see Figure 1). The second one is that of filtering techniques. These include a capability-based method, source address validity enforcement (SAVE), secure overlay service (SOS), history-based IP filtering, router-based IP filtering, and egress/ingress filtering.
The third article, “A Survey of Distributed Denial-of-Service Attack, Prevention, and Mitigation Techniques” provides evidence-based solutions to the DoS challenge. The first one is that of prevention. The proposed measures include changing IP addresses, disabling dormant services, and using security patches. The use of filters can prevent DDoS attacks. The targeted areas should include all inbound, core, and victims’ routers. Another proposal is the inclusion of accountability and auditing functions throughout the Internet.
The fourth paper is “Denial of Service Attacks – An Updated Perspective” and it offers appropriate solutions to mitigate DoS attacks. The first mechanism is known as an access control list (ACL). This framework provides powerful surgical capabilities for mitigating DoS attacks. Another one is the use of firewalls. These should be combined with ACLs and Intelligent DoS Mitigation Systems (IDMSs). Other potential strategies identified in this publication include aggressive ageing, active verification, dark address prevention, and SYN proxy.
Taxonomy: Detection, Prevention, and Mitigation
The selected papers provide different approaches and measures that companies, computer users, and systems managers can consider to deal with DoS attacks. The articles indicate that similar approaches can be put in place to deliver positive results. Each of the presented suggestion method has its unique mode of action. In the first article, the authors acknowledge that it is usually hard to protect different systems against DoS attacks.
However, computer technologists and programmers should identify the possible sources of threats and block them. Service Level Agreement (SLA) is an effective approach that maximizes trust, availability, and confidentially between two users. The model promotes data encryption and segregation, regulatory compliance, and ensures that data is inaccessible to unauthorized users. The idea of mitigation is also presented in this article.
The use of an Intrusion Detection System (IDS) in a virtual switch blocks illegal users’ addresses. Firewalls are also presented as powerful tools for filtering port numbers (Bonguet & Bellaiche, 2017). They also analyze existing protocol syntaxes and disable connections whenever necessary. Clustered firewall is effective for protecting Cloud services or data. The use of Infrastructure and Application Layer Defense (IALD) is presented in this article as a powerful procedure for blocking unknown URLs, IP addresses, and HTTPs.
The author of the second article focuses on attack detection and mitigation. The most appropriate detection methods for potential DoS attacks include SNMP-based tools, NetFlow analyzer, and firewall logs. Many users and corporations have embraced these measures since the year 2010. The article acknowledges that many programmers and technologists use SNMP-based tools (Kumar, 2016). These systems identify malicious files, queries, and IP addresses and warn every user.
The article indicates that detection is a critical aspect whenever mitigating DoS threats. Just like in the first article, this paper proposes that firewall usage can reduce chances of an attack. Many programmers embrace the power of Intelligent DoS Mitigation Systems (IDMs) since they can offer superior capabilities by identifying queries and denying entry. They also block unauthorized users from accessing certain resources. Access Control List (ACL) is another powerful tool that mitigates DoS attacks in a timely manner.
The author goes further to present additional measures that individuals can consider to minimize such attacks (Kumar, 2016). Some of them include aggressive ageing, connection limiting, dynamic filtering, anomaly recognition, white list-black list, and active verification. In order to deliver positive results, there is a need for professionals to combine these tools and techniques. This strategy will deliver positive results and address most of the problems associated with DoS attacks.
The third article expands the information presented in the first two to explain how DoS attacks can be prevented. The authors acknowledge that the implementation of powerful preventative measures is something that can deliver positive results. The authors provide five different approaches for achieving this objective. The first one is the use of filters. This means that filtering measures will be applied to different routers. This strategy will ensure that only legitimate or authorized users have access to the targeted systems. This is an additional solution that is captured in the first two papers.
Some of the common filtering techniques identified in this paper include ingress/egress, route-based packet, hop-count, Martian address, path identifier, and history-based filtering. The second method is known as secure overlay (Mahjabin, Xiao, Sun, & Jiang, 2017). This method is usually aimed at building an overlay network on a given or existing IP network. A distributed firewall is also needed to allow specific or trusted traffic. According to Mahjabin et al. (2017), a honeypot is the third mechanism for preventing DoS attacks. By mimicking a threat, this mechanism forces hackers to believe that they have entered the targeted system. This will make it easier for users to prevent attacks before they can take place. Load balancing is another approach whereby users monitor all systems to ensure that they are not overloaded. This is aimed at maximizing productivity and decreasing chances of attack.
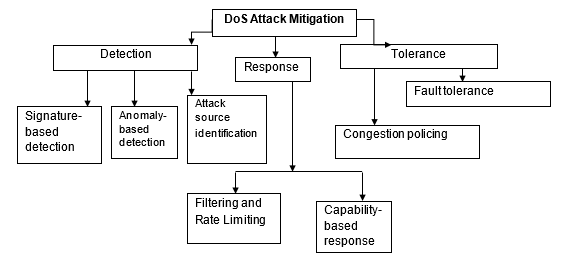
The third article proposes awareness techniques as powerful measures to prevent attacks. Users can consider these techniques: apply security patches, change IP addresses frequently, and disable unusual services. When it comes to mitigation, the authors support the effectiveness of powerful detection mechanisms (see Figure 2). Some of them include signature-based, anomaly-based, and spectral analysis detection mechanisms. Once an attack has been identified, it becomes crucial to mitigate it using various initiatives (Mahjabin et al., 2017). Some of the common measures proposed in this article include rate limiting or filtering and capability-based response. The final defense mechanism is that of tolerance. The purpose of this strategy is to minimize the impacts of an attack that has already succeeded.
In the fourth article, a statistical model is proposed as a powerful solution to dealing with DoS attacks. This is a distributed model whereby users monitor existing traffic patterns and parameters continuously. After an attack is identified, it becomes necessary to perform protocol changes within the shortest time possible (Pande, Borkar, Nimbarte, Pohane, & Thakur, 2016). The insights presented in this paper are similar to the ones highlighted above. The authors offer evidence-based ideas for detecting both DoS and DDoS attacks. The common ones include the use of covariance analysis and Dempster Shafter Theory (Pande et al., 2016).
These measures discover and collect alerts from various Intrusion Detection System (IDS) sensors. The authors support the use of Six Sigma whereby tolerance factors can be implemented to denote threshold values. Misuse-based detection systems monitor abnormal behaviors and alert the user. Anomaly-based intrusion detection is a model whereby misuse in a given network is identified and classified. The acquired information can then inform the most appropriate initiatives.
The authors go further to propose these two solutions to prevent such attacks: general and filtering techniques. The first category include installing latest security tools or patches, disabling IP broadcast, using firewalls, and disabling underused/unused services (Pande et al., 2016). A global defense infrastructure is also needed in the Internet to record positive results. The outstanding filtering techniques proposed in this paper are SAVE (Source Address Validity Enforcement), secure overlay service (SOS), egress/ingress filtering, and router-based packet filtering.
Discussion
The presented papers offer powerful solutions for dealing with the identified problem statement. It is evident that DoS attacks can make computer infrastructures unusable and incapable of supporting the goals of many organizations. This is the reason why such threats have become leading concerns for computer systems administrators and users. Most of the ideas and solutions appear to converge. This is true because all the authors and researchers believe that the first line of defense should be that prevention (Kumar, 2016). Some of the outstanding measures proposed to achieve this objective include the use of firewalls and complex applications. These techniques can make it impossible for unauthorized people to access specific resources and block unknown IP addresses and query strings.
The introduction of IDSs stands out as a powerful technique for detecting and preventing any form of intrusion. The outstanding rule that is presented in these papers is that users should only have access to limited resources. Users’ sessions can also be synchronized in order to reduce the chances of phishing and attacks. The concept of Statistical Machine Learning (SML) is also outlined as a superior technique for warning systems users, data owners, and administrators about potential risks (Pande et al., 2016). Such technologies also provide evidence-based suggestions and action plans that can divulge initiated attacks.
The idea of prevention is not enough since there should be appropriate mechanisms to deal with attacks that have already been executed. The studied paper offers meaningful insights for detecting and responding to attacks. The outstanding methods presented in the selected articles include the use of threshold value, misuse-based intrusion, and the ability to monitor anomalies. NetFlow analyzers and SNMP-based tools can empower administrators to detect DoS attacks.
When computer and data users take these technology-based measures seriously, it can be possible to minimize DoS attacks and support the goals of many companies (Bonguet & Bellaiche, 2017). However, each of the presented methods has weaknesses since it cannot deliver maximum protection against these threats. This is the case since technological advances are recorded every day. Programmers and data users also encounter numerous threats since hackers and phishers utilize emerging or superior techniques.
From this fact, it is agreeable that there is no specific technology-based strategy or solution that computer technologists can implement to provide adequate defense against any form of DoS attack. The decision to implement a specific solution will increase the vulnerability of the targeted system or data. With this kind of understanding, there is a need for companies and systems administrators to put in place comprehensive protection systems.
A multi-faceted approach characterized by prevention, mitigation, and enabling strategies can deliver positive results and ensure that many data systems are secure. Every system should have a backup since many attacks tend to be unpredictable (Kumar, 2016). Powerful mechanisms aimed at updating existing systems and implementing emerging technological applications will minimize chances of DoS attacks. Key stakeholders should also cooperate and communicate efficiently in order to identify potential areas of concern and present evidence-based solutions.
Conclusion
The above comparative analysis has revealed that DoS attacks continue to pose numerous challenges to many Internet users. Although the selected four papers present meaningful solutions that can deliver positive results, systems administrators and key stakeholders should consider the importance of a multifaceted approach. Such an initiative will ensure that different solutions are merged in an attempt to identify, prevent, and mitigate any possible DoS attack. They should also combine emerging technologies and ideas with existing solutions in order to protect computer systems, connections, and applications. Such an approach will, therefore, support many companies’ goals and make it easier for them to achieve their potential.
References
Bonguet, A., & Bellaiche, M. (2017). A survey of denial-of-service and distributed denial of service attacks and defenses in cloud computing. Future Internet, 9(3), 43-61. Web.
Kumar, G. (2016). Denial of service attacks – An updated perspective. Systems Science & Control Engineering, 4(1), 285-294. Web.
Mahjabin, T., Xiao, Y., Sun, G., & Jiang, W. (2017). A survey of distributed denial-of-service attack, prevention, and mitigation techniques. International Journal of Distributed Sensor Networks, 13(12), 1-33. Web.
Pande, S. M., Borkar, N. A., Nimbarte, C. P., Pohane, A. R., & Thakur, V. (2016). An attack detector based on statistical approach for detection and prevention of DDOS attack. International Journal of Computer Science and Mobile Computing, 5(4), 42-49.