Introduction
Over the years, there has been an increased use of Local Area Networks (LANs) to facilitate the transfer of information and to improve communication in learning institutions and organizations (Fetterolf & Anandalingam, 1992). In large companies and universities, electronic devices are connected using different network devices such as bridges, switches and routers. These devices are able to capture the location of different equipment on a network and forward packets from device to device (Fetterolf & Anandalingam, 1992). To take advantage of this advancement in technology so as to improve its operations, Hanson University has approached Transcend Solutions and wants a LAN infrastructure designed for them.
The main purpose of this report is to provide a description of the proposed LAN infrastructure design for Hanson University. Various recommendations are made concerning different issues such as what network devices to source for, the network operating system to use, the location of devices on the network, security requirements, and Internet connectivity among others.
For security purposes, a client-server model would be the most appropriate for this LAN. Besides offering better security than a peer-to-peer network, a client-server network will allow for centralized administration. It will make it possible to share the available resources among the users and since some of these devices such as the printer are usually quite expense, the university will be able to save substantially on implementation costs.
Again, when it comes to accessing Internet services, all staffs and students will use only one connection shared across the university. A peer-to-peer network is quite cheap and easy to implement but has several limitations. In the first place, the can comfortable support only up to ten users. Maintaining security in this kind of a network is also a bi challenge. As users are left to manage their own security, it very difficult to control how they do it. It very easy for a user to leave his or her machine as well as documents unprotected.
Requirements for the LAN
A wired LAN will be implemented to offer the services required by the university. According to Cisco Systems (2001), a wired LAN offers better rates of data transfer than wireless technology regardless of the distance being looked at. Key requirements for the LAN are;
Hardware Requirements
Server Computers. The LAN will require at least three servers. One of these servers will be used for Internet connectivity while the other two will be used for staff and students. Given the number of users and the amount of work that will need to be done by the servers, each should have the following specifications as a minimum; processors with a speed of at least 2 GHz and 2 GB of physical memory. AAs the servers will be handling so much, 160 GB of hard disk space or greater is necessary.
Routers. As packets move across the network, routers are used to determine the next destination of a packet. Intermediate routers help to forward the packets until they reach the destinations. Hanson University’s network will need a router to link its LAN to the Internet through an Internet Service Provider (ISP).
Switches. Switches are fast replacing traditional hubs. A hub will forward packets to every port connected to it. This creates a lot of overheads since every node connected to the hub will have to undertake unnecessary packet making the network seem so busy. On the other hand, a switch happens to be much smarter than a hub and only forwards packets to the port connected to the target destination equipment. This makes the network quite efficient, ensures that packets are delivered securely and greatly improves the performance of the network (Cisco Systems, 2001).
Cabling Media. A variety of cables exist that can be used to link network devices. The network will be implemented using Unshielded Twisted Pair Cables (UTP) category 5e. As the same suggests, these cables consist of twisted wires that are enclosed in some protective cover. The twists are meant to improve performance of UTP. Although these cables become unreliable when used over distances longer than 100 meters, because of the effect of attenuation; the loss of signal strength, their major advantage is the fact that they are quite easy to configure and work with unlike other forms of cabling media.
Printers. Apart from the labs and classrooms, each department will have one printer. An ideal printer to use for each of the departments will be a network printer. The choice for a network printer is to ensure that the printer will always be available to anyone wishing to use it. This printer will be configured at the proxy server to allow for centralized management.
However, since finance department will sometimes have special needs, it will be necessary to procure other types of printers to help them accomplish their work. When it comes to printing receipts, the dot matrix printer I usually preferred as it has some unique features not available with other printers. One such feature is the support for a continuous paper feed mechanism. Unlike a network printer, the dot matrix printer can only be installed locally after which it can be shared among the users.
Other Hardware Requirements. Network Interface cards incase they are not integrated on motherboards, RJ 45 connectors for connecting computers to the switches and racks to be used to hold switches securely in the various departments.
Software Requirements
Server Operating Systems. Windows Server 2008 is the latest server operating system from Microsoft and is quite secure when compared to the previous releases of Microsoft servers. It comes with numerous other features that make its performance far much better. It bots much faster and presents the user with easy update options.
Mail Server Software. All staffs and students will require email accounts. To make this possible, mail server software will be installed on the staff server as well as on the students’ server to facilitate email communication. A good option for Hanson University will be Microsoft Exchange Server 2008. Exchange 2008 has improved performance with in-built protection that keeps viruses and spam away.
End User Software for Client Machines. Microsoft office will be installed on all client computers. Users; staffs and students, will have outlook configured on their machines to allow for email communication. In addition, computers in the finance department will also require an installation of the tally software. The marketing department will need graphics software such as adobe illustrator or Photoshop to allow then them create marketing materials to be used for their promotional activities. Some departments will also require customized software to meet specific needs.
Main Report
Detailed LAN Structure
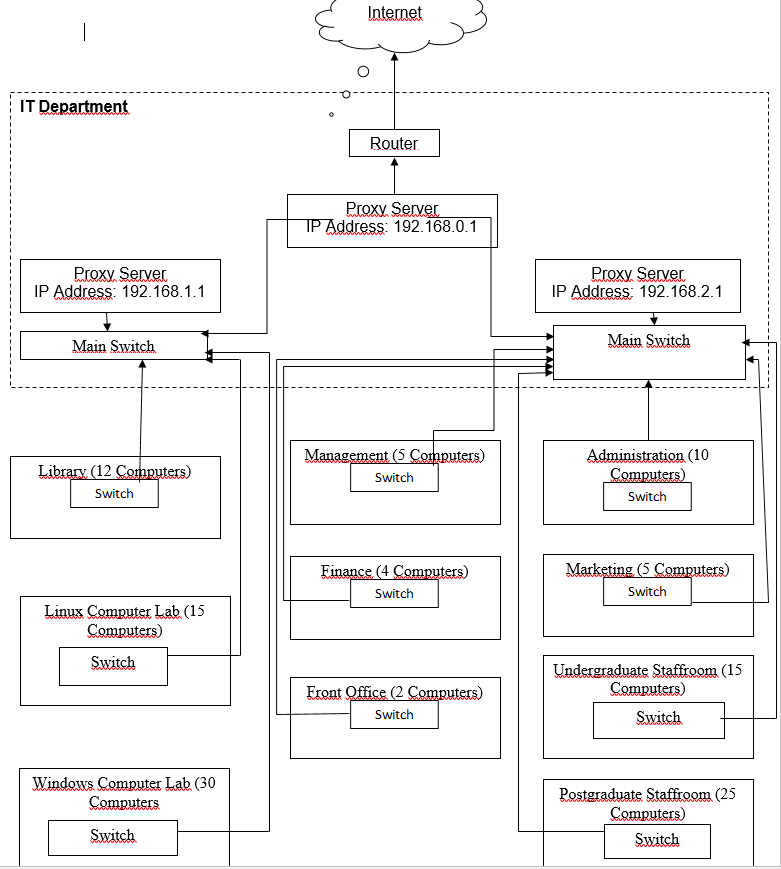
As indicated earlier in this report, a server – based network will be implemented for Hanson University. With this kind of a network, it will very easy to control various activities on the network. There will be three domains and three main servers in this network located in the IT department which will be the central location for all IT operations. Also placed in the IT department will three computers for use by staff in this department. One of the domains; hanson.edu, will be the main domain and on the domain controller installed for this domain, a proxy server will be configured to provide external connection to the Internet Service Provider (ISP).
This server will be connected to a router linked to the ISP network. Any communication that is not local will pass through the proxy server and then the router on its way out. This will be a server running Windows Server 2008 operating system and will be configured as a domain controller. It will also have a Domain Name System (DNS) server installed and configured on it to process any requests to access resources within or outside the internal network.
The main purpose of the DNS is to resolve names to IP addresses and maintain a mapping table of the same for future accesses. This is necessary because the system used by the computer to reach others is completely different from the one familiar to human beings. While humans appreciate working with words, computers use the binary system to communicate. The name resolution to IP addresses in binary form is therefore required to allow computers to communicate easily with one another.
Security will be implemented by installing a firewall on the proxy server. The firewall is a protective system placed between the local network and the Internet and will prevent any unauthorized access and use of Hanson University’s network. No illegal connections will be allowed into the network. The firewall may be implemented as a hardware device containing various functions or it may be installed and configured on the proxy server. The second option is much cheaper the procuring a hardware based firewall. To caution the network against any system failures, each domain controller will have a backup contain a replica of the domain controller.
The other two domains; hanstaff.edu and hanstudent.edu will cater for the needs of staff and student. Both domains will be trusted by the proxy server domain. No trust is necessary between the staff and students domains as they do not have to share resources. This is arrangement is also meant to help reinforce security.
On these servers, Microsoft Exchange 2008 will be installed to handle emailing services. Each student will have a user account and an email address in the form [email protected] created for them in the domain controller. Similarly, all staff will have a user account and email address in the form [email protected]. This will all be accomplished using the Windows Active Directory. Two main switches will be connected directly to the proxy server. The staff server will be connected to one of the switches and the students’ server will be connected to the other.
Three switches will be connected to the switch linked to the students’ server and these will lead to the two classrooms and the library. Each computer lab will have a switch to which all computers in the lab will connect. To accommodate all the machines in the Windows computer lab will require a 48 ports switch while a 24 ports switch will be sufficient for the Linux computer lab. To allow the two staffs and students to be able to print from the network printer in the lab, the printer will be installed and configured at the proxy server. This is because there is no trust that will exist between the staffs and students domains but each of these domains will be trusted by the hanson.edu domain.
Eight switches will be connected to the switch that the staffs’ server connects to. These will be located in the eight different departments at the university including the IT department. Each of these departments will have a network printer configured at the staffs’ server. Installing all the printers at the server level will make it easy to manage printers and print jobs.
Choice of Network Topology
A network topology is a diagrammatic representation of the network arrangement. Some of these topologies are; star, bus, ring, token ring, mesh and hybrid. A hybrid system includes a mixture of topologies. The Hanson University LAN will be designed using a star topology.
A star topology uses a central switch with nodes connecting to it from different locations. Although in some cases, one may not really visualize the existence of a star arrangement, the fact that there is a switch located centrally makes it a star network. A star network is easy to implement and troubleshoot. When the central switch that connects the whole network together fails, the entire network gets affected. When connectivity fails in a particular department, troubleshooting will localized to that department. The same applies to a single node that fails in the network. Below is diagram showing a star connection with a switch and four devices.
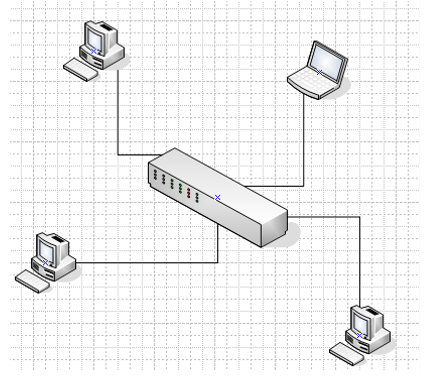
The detailed layout of the LAN is shown below.
Network Operation
Apart from the computers in the computer labs, all the computers will be configured to access Internet services through the proxy server. Students will be able to access Internet services using the computers in the library. All documents that need to be shared by all staff members will be located at the staffs’ server. Permissions will be assigned where needed.
Likewise, resources will be made available to the students by placing them in the students’ server. Staff in the library and students will print using the printer in the library while other staff members will print using printers located in their respective departments. With their user accounts, all users will be able to login and read their emails.
Network Administration Guidelines
The success of any network depends so much on the effectiveness of the network administrator. It is not just enough to configure a network and sit back. So much more has to be done to keep the network alive. Staff members in the IT department will be fully responsible for the daily maintenance of the university network. Some tasks to be undertaken by the IT department are:
Auditing. The main purpose of auditing is to monitor the use of the network and resources. By auditing, IT staff will be able to detect any interference with security and also when users are having problems accessing resources. Auditing will enabled at the domain level and events are logged and viewed using the event viewer. The event viewer records the events that took place, the time it happened and who was logged at the time. This is very important information when it comes to addresses issues on the network. An administrator will be able to know if for example, there was any unauthorized access to computers or resources. Using the event viewer, the LAN administrators will be able to see security, systems and application logs that have been captured by the system.
Storage and Backup. The IT staff will also ensure that user documents are correctly stored and safely stored. Backups will make it easy to recover the system to an earlier state incase problems are encountered. Various backup options are available and can be used depending on the level of sensitivity of the data. Whereas there are those that may not require frequent backing up, some data used by the finance department may need to be backed up quite frequently.
Depending on need, an administrator may perform either incremental, differential or full backup. A differential backup will allow the administrator to backup all files modified from the time full back up was undertaken. An incremental backup is taken for at various intervals and every backup contains different data. Full backup backs up all the information on the server. A good practice is always to use a mixture of these methods to back up.
Another good practice is to ensure that every user on the network has their own home folder where they can store their documents. This will greatly improve storage and backup. When it comes to backing up user documents, the LAN administrator only needs to backup the folder containing the users’ home folders. The entire backup process is therefore simplified.
User Account Management. The network administrator will be responsible of creating, deleting and disabling user accounts. Managing user accounts may also include making sure that all users have the correct privileges and permissions to access resources. This will be accomplished using Active Directory.
Another thing that the LAN administrators will be able to do as far as users are concerned is to restrict the usage of disk space by enabling disk quotas. Disk quotas will let the LAN administrator control how much space each user is entitled to. This will ensure that users do not misuse the available disk resources. This feature is only available when one is using the New Technology File System (NTFS). With NTFS, strict file policies can also be implemented.
Other Administrative Tasks. There are other numerous activities that will be undertaken by the LAN administrator. To ensure protect the institutions against any disasters, the LAN administrator will need to be proactive. It will be very critical to monitor the network at all the time to ensure optimal performance. Any anomalies detected must be dealt with immediately to avoid exposing the network to any failure.
The LAN administrator will also be responsible of performing any upgrades, installing and updating antivirus software, service packs and patches. The administrator may also create a problems log for each department. This will be used to capture any problems encountered within the department. When the LAN administrator is notified about a problem, the first place to check will be the problems log. After addressing a problem, a report should be written indicating what the problem was and how it was dealt with.
Future Recommendations
With the current competitive business environment, the university will have to go an extra mile to distinguish itself. Learning institutions these days are offering different study options so as to reach a wider audience. Gone are the days when we used to only a few institutions that would need to do very little marketing and advertising to reach customers. This they have managed to do by moving away from the traditional ways of running learning institutions.
A number of institutions are now providing various options that include online and distance learning to attract professionals who are very busy working but want to continue with studies and keep abreast with changing times. Over the years, the number of such students has really grown. It will therefore be worthwhile for Hanson University to consider investing in these areas.
To be successful in this, the university will need to configure an extranet that will be accessible by students from any where as long as they have an Internet connection. An extranet is part of a company’s internal connection that is made available to authorized users outside. With an extranet in place, students will not need to visit the institution all the time to do certain things. Most of their needs can be met quite easily online.
Conclusion
A majority of users care less about what really happens in a network. Most people will be very content as long as they are able to access resources on the network as required. Writing this report has given me a great opportunity to expand on my knowledge on networking. Besides appreciating what existing network technologies can do and how best to make use of them, I am now able to clearly figure out how a network works.
Reference List
Cisco Systems. 2001. Lessons on Freedom and Power: An End-to-End Network for Delivering Broadband for Government Organizations. San Jose: Cisco Systems, Inc. Web.
Fetterolf, P. C. & Anandalingam, G. 1992. Optimal design of LAN-WAN internetworks: an approach using simulated annealing. Annals of Operations Research 36 (1992) 275-298. Web.