Aim of the project
The main aim of this project is the development of IP telephony as a means of communication in the Qatar Ports Management Company (QPMC). IP telephony is a mode of communication which is employed by companies in the enhancement of mobility and flexibility in that communication within and without the building is made possible and hassle free. When this project is implemented, the company will have the advantage of a reduced cost in communication and have an added security considering that IP telephony is a concept that enhances privacy (Schulzrinne 1997; Pan and Schulzrinne, 1997) (b).
Project objectives
The IP telephony technology will provide additional data and voice security to the company as all voice movement will be closely monitored with ease. This will result from the sense that the employees will be suited with specially configured departmental phones. The quality of the voice in the company will be improved greatly. (Rosenberg and Schulzrinne, 1998)
Other features which are targeted are instant messaging systems in all lines and the use of VoIP. (Schulzrinne 1997) (a). On completion of the project, it will be fully documented and all the workers provided with copies of user guides which will enhance some smooth transition into the new system (Andersson et al 2006; Schulzrinne, 1997 (b)).
Primary research
The existing problem within the organization is closely linked with the absence of the effective communication tool for the team, and the absence of opportunity to make long distance calls. In fact, the offered project of IP telephony network creation will be used for resolving the existing communication problem and providing an opportunity for the team to have the properly adjusted connection.
The problems that have been found at the current stage are as follows:
- Existing PSTN networks are not able to realize the required functionality, and do not provide the required security level.
- VoIP provides the opportunity to add more than one call within the frames of the only high speed connection. Hence, it may be useful for decreasing the informational load of the office in general, and adjust a better connection within the organization (for making internal calls)
- Conference call, call diverts, automatic redial, number identification are the opportunities that are cheaper (or even free), and of higher quality over the IP network. While the costs for phone calls are unreasonably high in the PSTN networks
- PSTN networks are less safe, and digitization is more reliable in VoIP networks
- The company needs to get additional information such as whether a subscriber is available for a call. Moreover, conference integrations are often required, while traditional networks are not able to provide such a service.
Secondary research
A lot and in depth research was done on the implications, benefits, disadvantages and cost of the system. This helped in the ensuring of the feasibility of the project. When IP telephony is used in an organization, some benefits that come with it is the use of the voice over IP. This mode of communication has advantages to both the user and the signal carrier in a variety of ways. (Singh and Schulzrinne, 2004)
- There is provision of adjustability in the network. The end users of the system can chose the usability mode in the amount of compression and data manipulation that they use.
- Some protocols used in this network help in securing it to such an extent that it gets very secure using some techniques like encryption, cryptography and other techniques which ensure that the communication is safe.
- Real time transport protocol has been known to support user identification in all levels like in bridged multi-conferences where caller ID has been of question. This has an advantage over common protocols like POTS and ISDN
There are more other additional benefits that come with this required of telephony service like the integration of computers and telephony, easy to customize, use of multimedia, voice separation, silence suppression and so on. All this combined makes this mode of telephony the requisite mode for any company which wants to integrate the latest technology in its operations (Faulkner 2000).
A standard architecture for IP telephony is shown below.
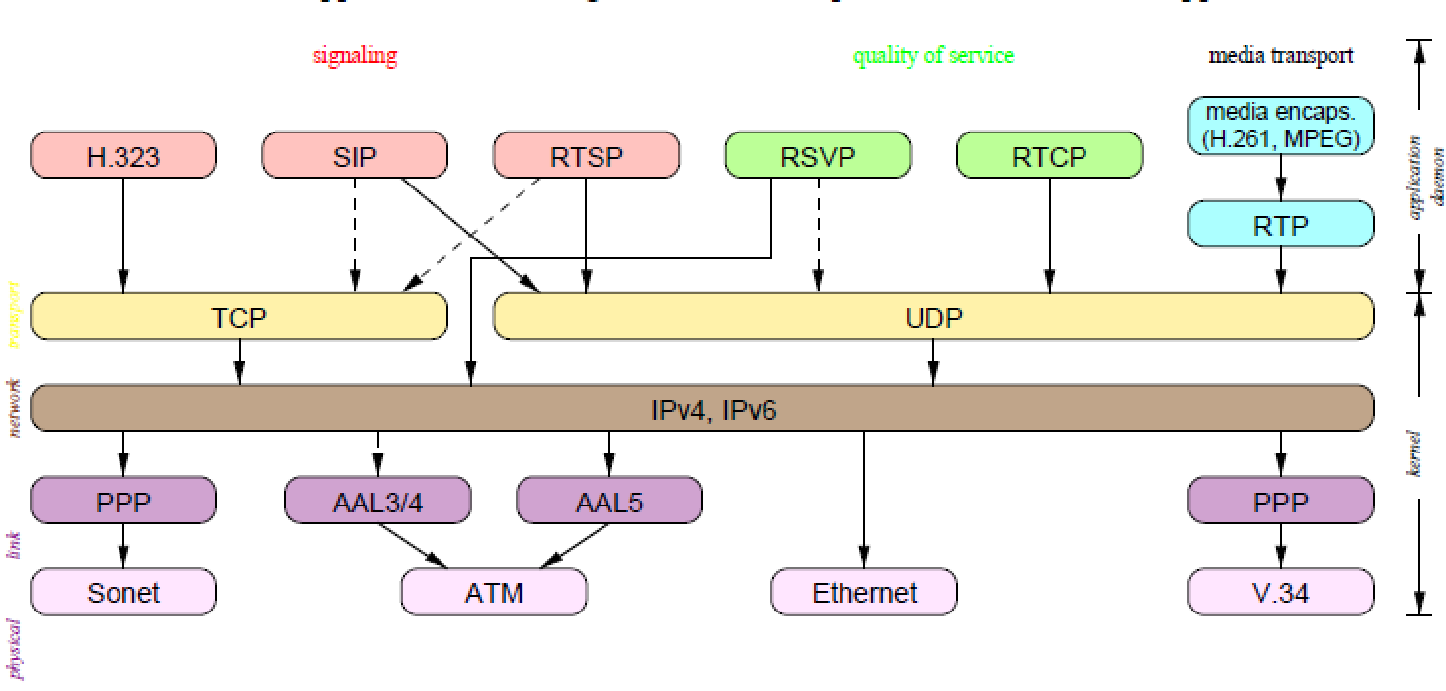
In the transfer of voice and video through IP telephony, some of the features that differentiate them from the other services include the use of sequencing of data packets. If they lose their order during transfer, synchronization between media where the silence between sounds is reconstructed to avoid disturbance, encryption of data, allows feedback on quality of service, multicasting, indication of frames among other features.
Resource requirements
For the implementation of this project, there will be some necessary hardware and software requirements which have to be put in place. In the first place it is necessary to have a network PSTN which will be having an IP address, cables, routers and switches and servers. Of other importance will be computers, IP telephones and an express router (CallManager).
System requirements generally depend in the number of calls made, and the load of the phone line. Hence, in accordance with Stellman and Greene (2005) optimal requirements are as follows:
Hardware
- 1.8 – 2.6 GHz Pentium IV processor or equivalent*
- 1 GB of RAM and higher
- Display with 1024×768 resolution
Every fifty simultaneous calls require up to 1GB of RAM memory, and 2 GHz of processor speed are required if the amount of simultaneous calls is more then 150.
Hardware space required depends on the necessities and objectives of the organization. If the calls are voice recorded up to 1 GB will be required for every 24 hours of low quality records. If the data storage is required for call data storage, then, every 10 000 calls will require up to 100 MB.
Software
These are not critical, as the most effective software packs have been tested for various platforms, and may be used either with windows, or with Linux OS.
Quality management
For this project to comply with the normal standards, it must qualify for ISO authenticity. In order for this to be clear and applicable, the project must be able to ensure that the needs of the end user are met and that it will be able to provide all the desired characteristics of IP telephony.
The management of the project has set aside a quality assurance team which will make sure that the project meets all the required standards through assessments. The installation of the IP telephony should meet all the basic requirements of a standard IP telephony system.
In this establishment, the team should dig deep into the required control measures in the standardization of an IP telephony network. This should be followed by the necessary quality control measures which should meet all the requirement measures and criteria. This can be done using various tools like PRINCE2. (Strathmeyer 1996).
After the control is done the team should keep a record of the measures which have been adhered to such that at the end of the day, the team will have been able to tell what should be looked into again. (Pan and Schulzrinne 1997).
Table 1. Risk assessment (Busse et al 1996; Low 1996).
Design
Functional diagram of the IP telephony network is based on the key principles of effective gateway creation. In general, these are common for any IP network creation regardless of the actual size of the network, and disperse of subscribers within a single building:
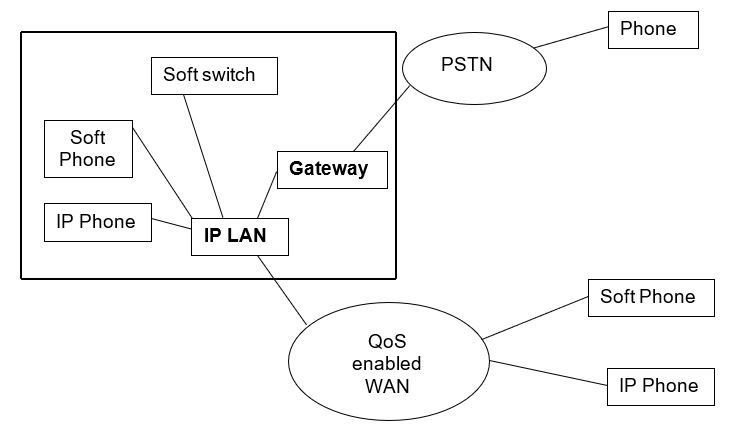
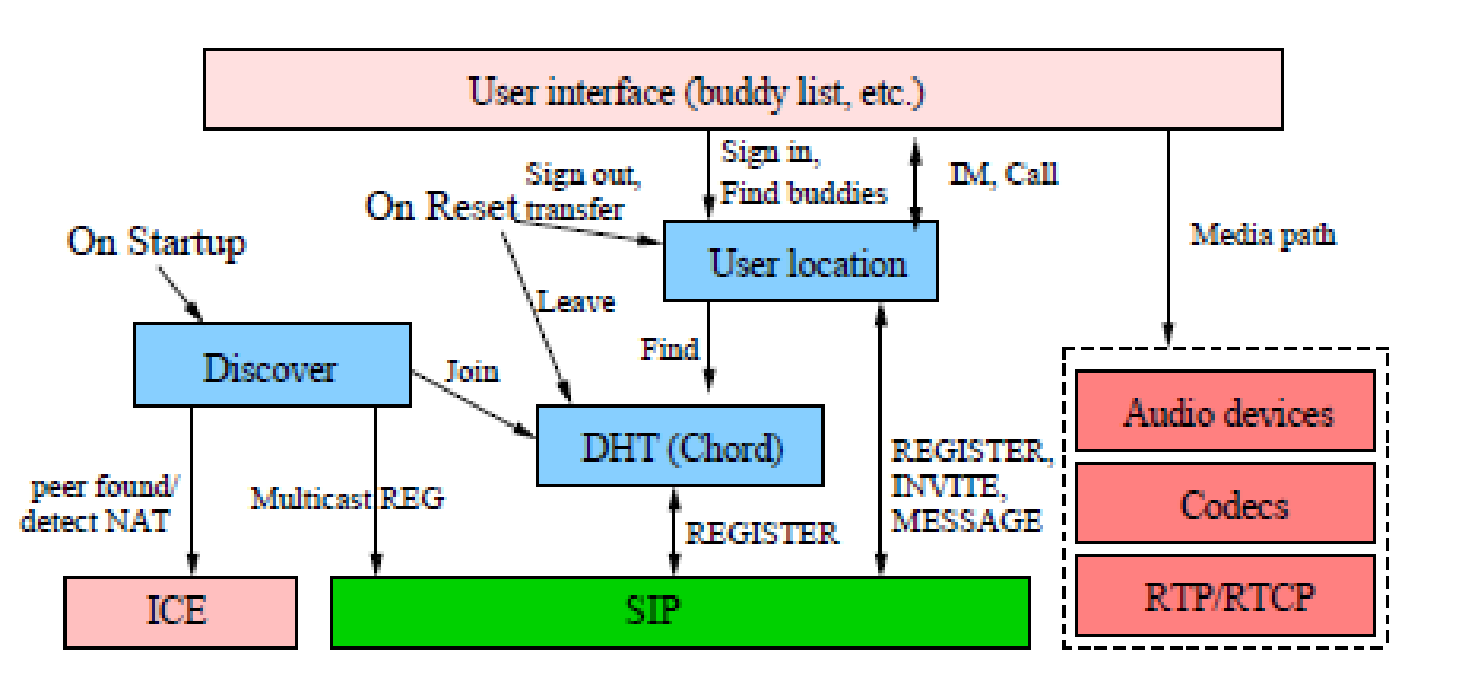
The design of the system will be base on the SIP protocol. In the identification of the names, the nodes will be named according to the mode of SIP URLs. The key of the node in this place is used together with the IP address of the place that the node is listening to. A good example is a node which is listening to 192.168.0.9 and the key that identifies this communication is put as 8, the User resource identifier of that node in particular will be sip:8 @ 192.168.0.9. This code will be used by all the nodes in the building in ensuring that communication is logged and that all the nodes that are using a particular line are traceable (Zhang et al 1998).
There will be a mode of authentication for first time users. This will have to depend on the likelihood of the user having a public key infrastructure. For those who do not have, the system will generate one for them automatically and send it to their emails. The password is then stored for future use. The block diagram below shows how a standard node in the company would look like (Davies 2007).
The architecture of the project will be dependent on a distributed hash table. This will make sure that the architecture of the project maintains a standard client server model. The DHT will also act as a server in some extremes. This will be initiated using the ends that do have super fast nodes (Stellman & Greene 2005). The diagram below shows how the super nodes make use of as servers to other nodes
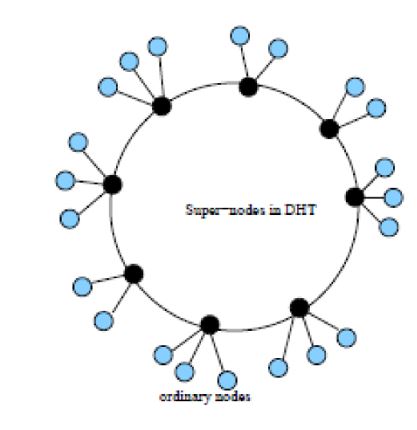
The system discussed in the preceding paragraphs has been shown to take keen interest in scalability and is more reliable. It can also be interoperable with the current infrastructure.
Gant Chart
The following tables provide a general overview of the stages of the projects and their schedule. Detailed Gantt charts can be seen on the figures below.
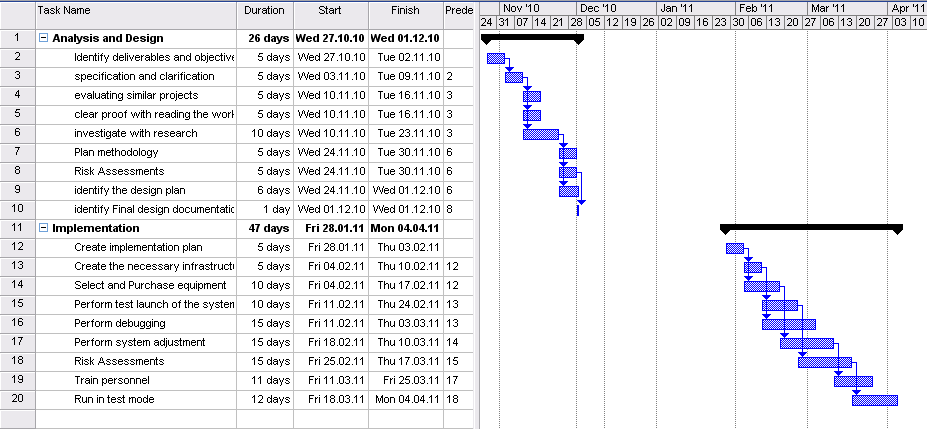
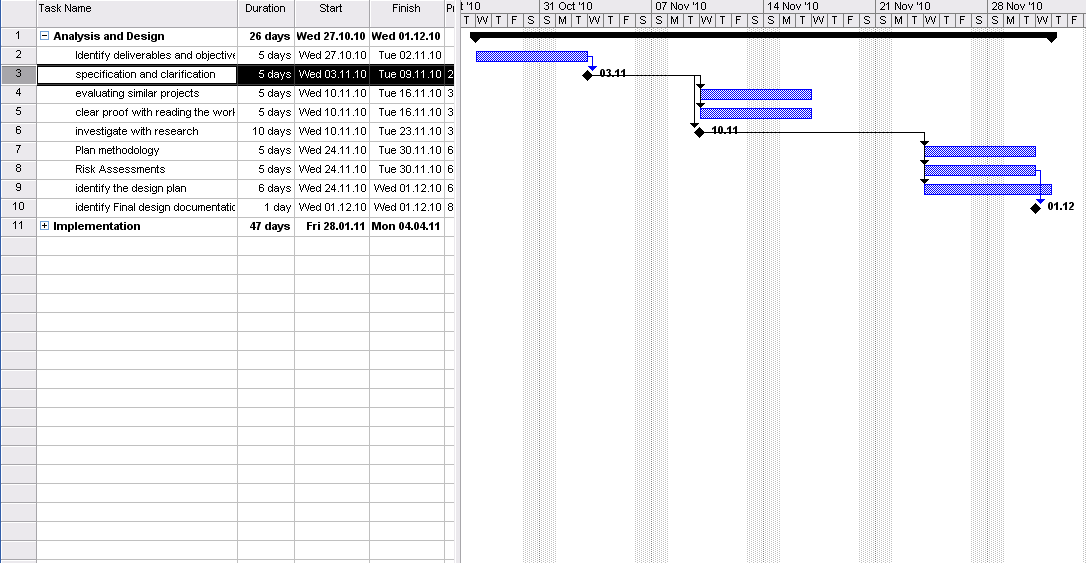
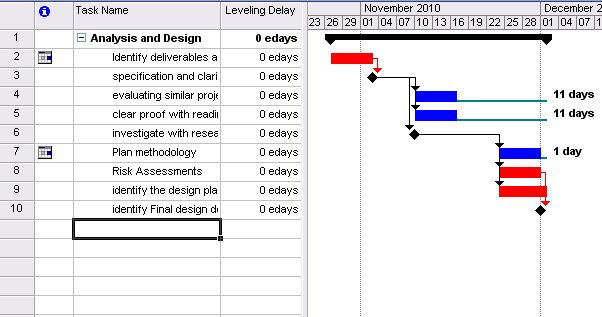
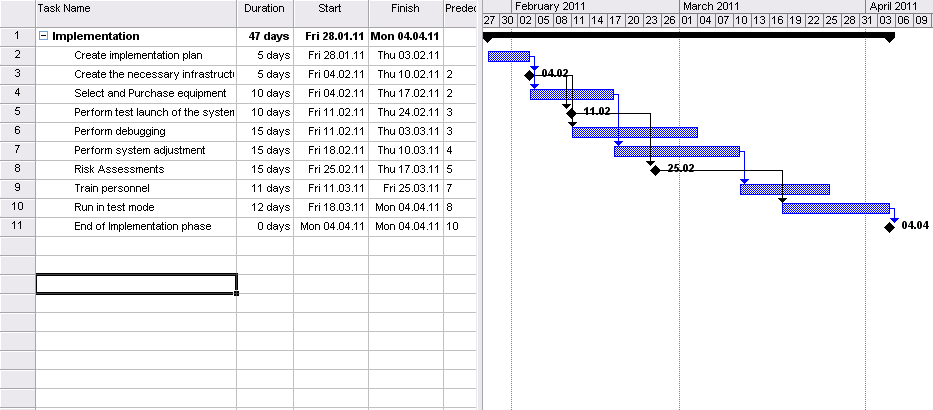
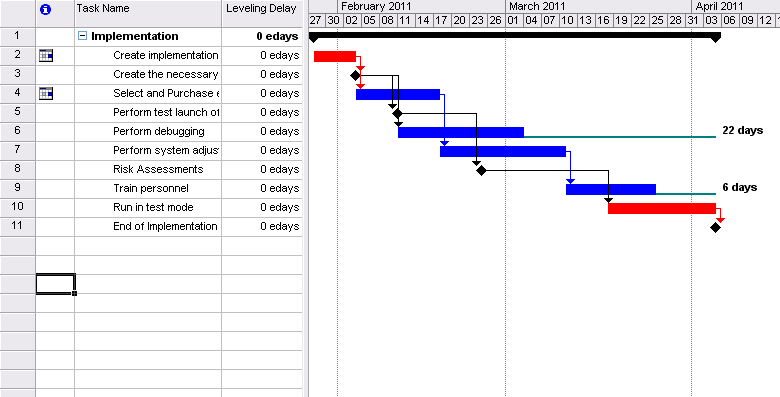
The basis for the chart can be seen through PERT analysis below.
Table 2. PERT Table.
References
Andersson, E. et al 2006. Software engineering for Internet applications. Cambridge : MIT.
Braden, B. et al 1997 “Resource ReSerVation protocol (RSVP) – version 1 functional specification,” 2205, Internet Engineering Task Force.
Busse, I et al 1996, “Dynamic QoS control of multimedia applications based on
Davies B. 2007, Doing Successful Research project, using qualitative or quantitative methods. USA: Palgrave Macmillan
Faulkner, X. 2000. Usability Engineering. London: McMillan.
ITU. 2003. The Essential Report on IP Telephony. International Telecommunication Union. Web.
Low, C. 1996 “The internet telephony red herring,” in Proceedings of Global Internet, (London, England), pp. 72–80.
MITEL. 2005. Advancing Business Communications with IP Telephony. Mitel Networks Corporation. Web.
Pan, P & Schulzrinne, H. 1997 “Yessir: A simple reservation mechanism for the internet,” Technical Report RC 20697, IBM Research, Hawthorne, New York.
Rosenberg, J. & Schulzrinne, H. 1998 “Timer reconsideration for enhanced RTP scalability,” in Proceedings of the Conference on Computer Communications (IEEE Infocom),San Francisco: California. RTP,” Computer Communications, vol. 19, pp. 49–58.
Schulzrinne, H. 1997 (a) “A comprehensive multimedia control architecture for the Internet,” in Proc. International Workshop on Network and Operating System Support for Digital Audio and Video (NOSSDAV), St. Louis, Missouri
Schulzrinne, H. 1997 (b) “Re-engineering the telephone system,” in Proc. of IEEE Singapore International Conference on Networks (SICON), Singapore.
Singh, K. & Schulzrinne, H. 2004 Peer-to-peer internet telephony using SIP. In New York Metro Area Networking Workshop, New York, NY.
Stellman, A. & Greene, J. 2005. Applied Software Project Management. Cambridge, MA: O’Reilly Media
Strathmeyer, C. 1996 “Feature topic: Computer telephony,” IEEE Communications Magazine, vol. 34.
WANG, D. Voice over IP (VoIP). Arlington: College of Engineering. Web.
Zhang, L et al 1998, “Separating identifiers and locators in addresses: An analysis of the GSE proposal for IPv6,” Internet Draft, Internet Engineering Task Force