Introduction
Asset misappropriation methods include frauds in which executors use tricks and deceits to acquire ownership of an institution’s resources. In these methods, employees use assets of the organizations that they work in for their personal gains. In many cases, people who commit asset misappropriation crimes are employees of organizations, clients or suppliers. Asset misappropriation differs from other crimes in that trickery is applied.
Force is never applied in execution of asset misappropriation crimes. Two categories of asset misappropriation crimes exist. These include deceitful acquisition of money and non-cash assets. In addition, asset misappropriation crimes can take place at any point in an organization. The circumstances that promote the occurrence of asset misappropriation differ.
The crime can take place before records are made or after reports have been prepared. Asset misappropriation can also take place when purchases are being made, during preparation of payroll or in delivery of reimbursement.
However, in many cases, asset misappropriation involves the theft of money. This paper describes how an employee plans to commit skimming successfully. It also describes the impact of weak controls and the prevention of the crime in a company.
Execution of Skimming
Asset misappropriation is divided into various types namely skimming, misuse of funds and cash larceny. Skimming is a type of cash theft by an employee. It involves the theft of money before records are entered in an organization’s accounts. Hence, skimming is popularly referred to as off the records fraud. John works as a teller at Thomson Home Hardware store where he plans to skim money successfully.
He plans to commit the act on several occasions. He will ensure that a record has not been made before he commits the crime. Absence of a record will make audit trace impossible. Stealing the money before it is recorded will ensure that the company does not know of its receipt. Consequently, it will be difficult for the company to know that John has stolen the money.
John decided to position himself appropriately within the organization to succeed in stealing money. He realized that it is essential to be in a department in which funds are received. In such departments, he will receive and record payments and money. This will give him access to cash.
He plans to slip checks or cash out of the receivables. That is why he chose to be a teller at the hardware store. John plans to post a large quantity of the money received in the appropriate returns or clients’ accounts. However, he will keep a smaller quantity of the received payments in his private account.
Skimming is usually straightforward. A customer comes and makes payment for goods and services. Customers leave the store after they pay for goods bought or services received. The employee then places the received amounts in the cash register.
However, since John plans to steal money, he will put part of the money in his pocket and not record the transaction. The process will be simplified since there is no supervisor who will monitor his activities at the store. However, in case there will be a supervisor around, John plans to make a no-sale record in the registers even if he has received money for cash sale. John plans to use these two strategies.
These will assist him to avoid easy detection. Additionally, he will target donations made by donors instead of receivables. He will do so since it will be difficult to conceal receivable skimming. John realized that customers are likely to make complaints if they detect that their deposits do not reflect in their accounts.
In the execution of skimming, John will ensure that there are no observers. He will sit or stand in a position in which nobody will detect that he hides some of the checks or money. John is aware of the cameras that the hardware’s proprietor has placed in the cash receivable office.
Therefore, John plans to conceal both his identity and the crime. Detection of the crime can result into his imprisonment and loss of employment. Hence, John has carefully planned the execution of the crime. This has taken him a long time, and the crime will begin with concealment of small amounts.
John has planned not to change his lifestyle after he steals the money successfully. He noted that change in lifestyle could result into early detection. In addition, it will be essential that he destroy all physical evidences that can result into detection. Therefore, John has planned to ensure that there is no paper trail. Any document that will link him to the crime will be destroyed.
Furthermore, he will destroy all video evidences that will capture the execution of the crime. In addition, all forgeries that he will use to execute the crime will be perfect. He has planned to forge the signature of the manager. The signature is used in authorization of receipts. Finally, John plans not to act suspiciously at work. He argued that lack of confidence during execution of skimming could result into detection.
Weak Internal Controls
Studies have suggested that asset misappropriation is prevalent in institutions and businesses that have weak controls. Poor isolation of duties and authorization, inadequate supervision and weak accounting systems are some of the internal controls that enable the existence of crimes like skimming. An appropriate internal system can assist an organization deter the occurrence of skimming.
A framework that can assist in the elimination of skimming has to include appropriate environment, activities and accounting strategies, continuous monitoring and effective communication system. The lack of these conditions in an organization enables an employee to succeed in execution of skimming. Internal controls as separation of duties make it difficult for an employee to succeed in skimming.
In the cash receivable room, John can record receipt of mails and the second worker can enter the funds into a register. The third employee can take the money to the bank. This makes skimming impossible. Investigation of no-sale transactions can also assist an organization reduce skimming. Finally, it is appropriate for an organization to conduct thorough background checks before they employ workers.
Prevention of Asset Misappropriation
The occurrence of asset misappropriation results into great loss for any organization. The prevention of asset misappropriation is a strategy that an organization can use to reduce losses. Hence, numerous organizations have implemented fraud preventive measures.
However, the implementation of these strategies does not necessarily result into a reduction of asset misappropriation practices. According to the triangle shown below, all employees can commit asset misappropriation even if preventive measures are in place.
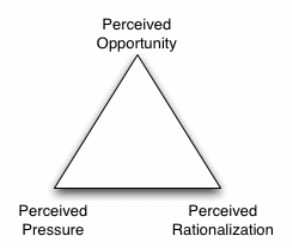
Employees have pressures, opportunities to commit crime and can rationalize the practice. Therefore, it is appropriate for organizations to introduce other strategies to complement internal controls. These other strategies include the creation of a culture of honesty within the organization, provision of assistance to employees, and the elimination of opportunities for crime.
In creating an honesty culture, an organization should hire and train workers on fraud awareness. In addition, an organization should create a good work environment and establish an aid program for employees.
The elimination of asset misappropriation includes maintenance of appropriate internal controls, implementation of crime deterrence strategies and inclusion of clients in management of the problem. It can also include the creation of a whistle blower method and performance of audits.
Fraud Detection
Organizations must implement fraud detection methods to avoid losses. The basic technique is to identify and monitor symptoms of fraud. Asset misappropriation is normally accompanied by accounting anomalies like inaccuracies in ledger books. In addition, overrides in the internal control systems may indicate the existence of asset misappropriation practices within an organization.
Changes in lifestyles of employees and suspicious behaviours can also be indicators of fraud within an organization. An employee who steals money from his employer is likely to increase in his lifestyle. He is also likely to act suspiciously when he is at work.
Analytical systems can also be used to detect fraud in an organization. Analytical systems can include investigation of unusual activities. For example, activities and transactions that take place at odd times can be indicators of fraud. Finally, organization can introduce the use of modern technology in detection of crime.
Conclusions
Asset mismanagement includes frauds in which employees use trickery to acquire ownership of a company’s property. One of such method of asset mismanagement is skimming. This paper aimed to describe a method through which an employee could execute skimming. It provided methods through which an employee will successfully execute skimming in a company.
Secondly, it examined some of the internal controls that a company can employ to reduce the occurrence of asset mismanagement. Thirdly, the paper discussed prevention and detection of asset mismanagement in an organization. In the discussions, it provided recommendations that can be used to reduce the crime.