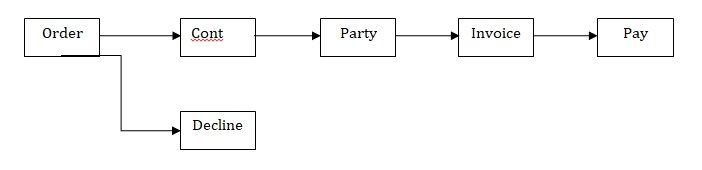
Rich Picture of Situation
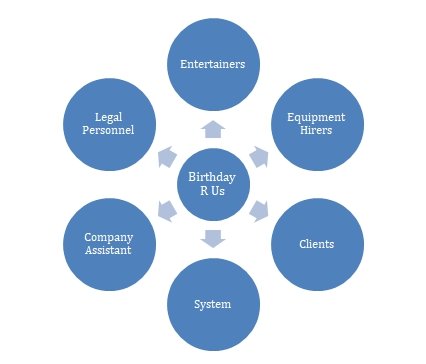
Birthday R Us is in dire need for a computerized system. There are critical areas that need a quick intervention to streamline operations. There are three major areas namely:
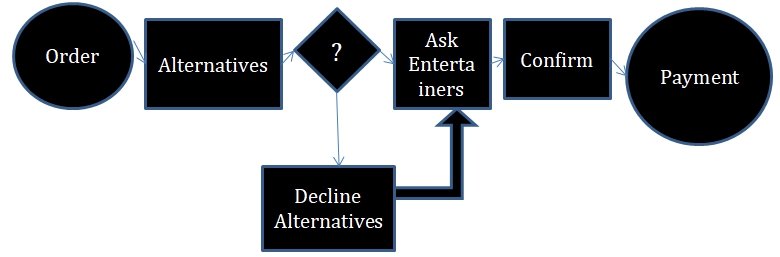
- Ordering: Once a customer places an order for a party, they are obliged to take at least one catering option out of the ten available. The others (entertainment and equipment hire) are optional. However, if needed, the administrator checks availability from the diary.
- Logistics: The Company has made certain concessions in terms logistics. These include minimum times and fixed payments for particular services. For example, entertainers can only be booked for a minimum of 2 hours while customers make fixed payments for a catering option per head.
- Payments: The Company has several payment requirements. For example, the company receives a minimum payment of 50% on order placement. The rest is paid at most seven days after the party. Entertainers charge an hourly rate of which the company takes 20%. However, the company collects the monies. Collection of monies is one of the most critical areas of the company. Equipment is charged a flat rate regardless of the time of usage.
Company affairs have been in jeopardy and the owner is intent on introducing a computerized system that handles all operations. The staff need some training and positive reinforcement to mitigate the risk of feeling left out. The system is likely to increase customer numbers and iron out grey areas in operations such wrongful application of entertainer commissions experienced currently.
Functional Requirements and Non-Functional Requirements
Functional Requirements
The following may form the proposed list for functional requirements:
- Invoicing: Once the party is over, the system will automatically send an invoice to the customer detailing the remaining amount to be paid in seven days. Usually, the amount will be 50% of the total since the customer will have paid a deposit of 50%.
- Ordering: the system will prompt a customer to take at least one of the ten available catering options in order to continue with order placement. The customer has to pick one of the options in order to choose alternatives such as entertainers and equipment hires.
- Birthdays’ reminders: the system will keep a list of clientele and their respective birthdays and will automatically remind them of the services they offer a month prior to the birthday.
Non-Functional Requirements
- A day after the party is over the system will send the relevant invoice to the client.
- After the party is over and the client fails to pay after 7 days, as agreed, the company will wait up to the thirtieth day. On the day, the system will automatically dispense letters threatening legal action.
- The entertainers will be paid according to the commission rate that the system reflects at a particular time regarding the entertainer. For example, a magician may be charging a rate different from the musician. However, their payments must be dispensed 7 days after the party.
Systems Lifecycle
Methodology to be used: Waterfall Model
This methodology is most appropriate, for many reasons. In the case study provided, the parties are apprehensive of the possible negative effect that the introduction of the new system may have on their jobs. This model has the capability to mitigate that worry. The following are some of the advantages of using the model:
- The model is sequential. This means that it has several stages that carefully detail the steps and the activities that will occur in each step. It has six distinct stages that are discussed later.
- The model’s definition of each stage allows easy introduction of the system. It also allows for careful review of some of the steps.
- The system can be remodeled to reflect changes and other aspects that may come up during the introduction of the system.
However, it is crucial to note that end users are not involved in the development of the system, which makes this process fundamentally crucial to get right. Otherwise, its operation may be a problem in the first few months. Already, this is evident when Elsie Turner, the 19 old assistant that claims to be good at Microsoft, claims that it is unfair to seek external consultancy.
Stages of the Model
The following are the stages of the model and their relationship to the Birthday R Us case study:
- Feasibility study- the managing director John Pilkins will have to undertake a comprehensive study to measure certain aspects regarding Birthday R Us. This will include ascertaining the cost-effectiveness of the system, how long it will take for the system to be operational, and the practicality of the system.
- Requirements analysis- at this stage, Birthday R Us’ Consultant will gather information about all aspects of the organization. This will be achieved through interviews and other data collection methods such as questionnaires and observation.
- Design- the preceding step also makes recommendations which inform this step in terms selection of software, hardware, and the eventual system functionalities and aesthetics (e.g. user interfaces).
- Implementation- Coding and testing are the two main aspects of this step. In addition, hardware and software are acquired.
- Installation- this is the actual running of the system. It involves putting up hardware, cabling the office, training, and conversion of existing files into the system. At Birthday R Us, this may include diary of entertainers and equipment, existing clients and some parameters such as commissions.
- Post implementation review- after implementation some processes may not work well. At this stage, Birthday R Us will observe the working of the system to make any necessary adjustments. Additionally, the organization will undertake necessary maintenance. It is crucial to understand that any additional software adjustments happen at this stage. E.g., Birthday R Us may want to reduce the time taken before taking legal action once a client defaults on payment to 21 days (Elliott, 2004).
Comparison between Waterfall and Spiral Model
The two models are somewhat similar. Spiral Model may be used in place of the Waterfall Model for implementation of a computerized system at Birthday R Us. The model combines the top-down and down-up approach with prototyping in a stage-by-stage process. Similarly, Waterfall assumes a top-down approach and prototyping (Schach, 1999). The model, however, does not complete one stage before going to the next one. Assuming a spiral figure, one trip through the model covers all stages of the system implementation.
The stages are similar to the one in a Waterfall model (Spiral Model, 2012). However, instead of completing one stage at a time, Birthday R Us will implement each stage progressively. For example, all stages regarding creating the ordering part of the system are undertaken. This includes implementation and post implementation review (Hantos, 2012).
Recommendations
Different methodologies may be adopted to carry out planning and strategy in IT effectively. It is crucial to note that IT is the bedrock of current organizational operations. Hence, a possible failure or fault in IT could have catastrophic ramifications. Birthday R Us may adopt a leveraged 6-point IT strategy and planning methodology in its operations. The 6-point methodology is outlined below.
Indentify Business Strategy and Capabilities
In this step, Birthday R Us defines its overall enterprise strategy. This is the strategy developed by top management. Generally, it outlines future goals, vision, and objectives. In addition to this, Birthday R Us divides its operations into units and outlines their strategies, for example, the catering unit. Lastly, the business defines operational capabilities that are prevalent to ensuring the realization of the business strategy (Gerami, 2010).
Outline Business Process Framework
In this step, business processes are defined, roles are outlined and business scenarios forethought. All this is done in respect to the business capabilities outlined. Additionally, the business indentifies areas that starkly differentiate it from other players in the same filed.
Define Targets and Enabling Applications
In this step, Birthday R Us indentifies its main targets and strategies. This way, applications maybe developed to cater for key integration points that the company indentifies. Additionally, Birthday R Us indentifies components and services that will define its business.
Indentify Core Data and their Sources
In this step, the business indentifies and clearly outlines the most critical data and the data points. Birthday R Us cleans these data points to come up with trusted sources of data. These may be clients, suppliers, consultants, or business analysts. The data aids in ensuring smooth business processes. Additionally, Birthday R Us develops standards for which to accept or reject a data point (Castells, 2011).
Reference List
Castells, M. 2011, The Rise of the Network Society: The Information Age: Economy, Society and Culture, John Wiley & Sons, New York, NY.
Elliott, G. 2004, Global Business Information Technology: an Integrated Systems Approach, Pearson Education, New York, NY.
Gerami, M. 2010, “Knowledge Management”, International Journal of Computer Science and Information Security, Vol. 7 No. 2, pp. 234-237.
Hantos, P. 2012, Interpreting the Spiral Model of Software-Intensive System Development – a ULCMsm Approach. Web.
Schach, R. 1999, Software Engineering, McGraw-Hill, Boston, MA.
Spiral Model, 2012, The Spiral Model. Web.