Management Summary
The general principles of digital asset management are closely linked with the values of safety, usability, flexibility of adjustments, as well as the availability of patches, service packs, and updates for the software. Considering the fact that every business strategy presupposes unique requirements towards managing data flows, the processes of data storage and sharing are performed differently.
Companies with small computer networks will not require sophisticated DAM systems, especially if all the computers are located in a single building. Large companies, with up to 500 computers will require more reliable, effective, and safe systems, as geography of such a network may be large enough. This means that the type of digital asset management will be based on library asset management principles, while the focus of the data management will be made on the storage and retrieval processes of large amounts of data.
These will be mainly documents, and rarely changing media files. Additionally, the packages should offer the option of data archiving, as documental flow of some companies presuppose storing documents that are addressed rarely, and for they occupied lesser space on the hard drives, they should be archived. The opportunity to make codified archives is optional; though, some companies appreciate this.
The management itself will be focused on offering effective, reliable, operative, and qualified technical assistance for the companies that are served by Green Plan-IT Group were satisfied with the level of the services. Therefore, all the problems should be resolved within the nearest time, remotely, and safely for the data stored in the repositories.
Introduction
Data management problems are generally regarded s the cornerstone of data security for any organization. As a rule, data security is the matter of proper IT management principles, however, most SME do not have an opportunity and sufficient resources for establishing a reliable and effective IT management systems. Therefore, they resort to outsourced IT and Data management. On the one hand, this may be regarded as the violation of the data security principles, as third party persons have access to the key business data, on the other hand, the company does not have to worry on the matters of finding qualified personnel for managing IT and data security spheres.
Green Plan-IT Group is an IT service company that undertakes IT management of SMEs, and looks for the most effective, reliable, and least labour-intense solutions for business needs. The aim of the paper is to analyze three particular variants of data management defined by the CEO of Green Plan-IT Group, and define which one will be the most effective and reliable in the context of data storing and sharing problems. These solutions involve Greenstone software, Dspace pack, and Fedora OS. Considering the fact that all three can not be compared in accordance with a single parameter, the paper will be focused on precise and thorough analysis of all three variants for defining the most reliable and effective.
From the perspective of key digital asset management rules, the data storing process should be safe, comfortable for users, and easy for maintenance. This means, that security must in no way decrease the comfort of using storages, and sharing of the information. The regarded packages are developed for covering the needs of the increased safety, however, they are based on the high usability principles. Nevertheless, each development team used their own imaginations about usability. Considering the fact that these are Open Source projects, the aspect of price or closed program code will not be regarded in the paper. This also means that Green Plan-IT Group may improve the usability or functional set of the regarded packages, however, the general aim and image of data storing, processing and sharing will be the same.
Greenstone is intended for building, storing, sharing, and developing digital libraries that may be used for various aims. Therefore, the usability criteria will be linked with storing text files, media data, passwords and account information, virus safety, presence and comfort of user-friendly interface, as well as the flexibility of adjustments and settings. (Blake and Head, 2007)
As for the matters of Digital Data Management that is used in the controlled companies, this is mainly implemented for managing business, marketing, and financial information. Therefore, the companies need to have a reliable and safe file repository, 24/7 access to the data, and availability of instant technical support. Considering the fact that Green Plan-IT Group serves several companies, this support should be offered distantly.
This means that remote control of data-servers is one of the key priorities that will be required from the packages analyzed. Additionally, the packages should provide instant access to updates and technical documentation by the developer for the Green Plan-IT Group technical experts could solve the problems operatively. Therefore, the general principles of the Digital Asset Management should be based on safety, usability, flexible adjustments, access to technical documentation provided by developers, and properly tested applications, as business systems should be bug-free.
Comparison Matrix
Supporting Information
Definition of the comparison criteria is stipulated by the general principles of the digital asset management which is intended for safe storage, sharing and access of information and data. Therefore, there are no precise regulations and rules that define the order of using the software tools that are suitable for data storage. In general, the tools are defined in accordance with the aims, and not vice versa, that is why the selection of the tools will depend on the needs and requirements of each company. The tools are also defined by the sizes of the company, as smaller companies may not require too sophisticated systems, while larger companies need complex control and protection tools for ensuring the required safety level. Therefore, as it is stated by Betz (2007, p. 418):
Smaller DAM systems are easier to categorize as to content and usage since they would normally operate in a particular operational context. This would hold true for systems attached to audio or video production systems. The key differentiators here are the type of decoders and I/O used for the asset ingest, use and outgest. Since the essence are described by metadata, the metadata can be used as a guide to the playout decoders, transcoders, and channels as well as an input to access control rules.
In the light of this fact it should be stated that small DAM systems may be used by small companies, or the companies that do not have extensive documentation flow. Hence, the Greenstone software may be used for such companies, however, they should follow the network security rules, as the system is not intended for protecting data from serious network attacks. Moreover, 90% of data security is users awareness and following of the safety rules. (Chu, 2004).
Since the main aims of data management are storage, access, viewing, editing and sharing, it should be stated that relevance of the selected tools is defined by the overall implementations. Hence, as it is stated by Wiltrout (2008), the closer the asset to the data management tool (any tool is considered), the more complicated and reliable technical architecture is required for adapting the company’s needs towards the data management requirements and principles.
Hence, the architecture of the data storage is defined, which stipulated the requirements for a file system and type of data based used. In accordance with Lancaster (2008), the influence of these needs, the possible design of the system is outlined. The aim is to minimize the resources available, and each of the offered software is not restricting minimal or maximal requirements towards the system. While all the systems are free and based on open source licenses, there is no need to consider the factor of the price, while the criteria selected help to compare the general information about the system, as well as assess the productivity of each solution. (Thierauf, 2007)
The information that was selected for comparison is divided into several key sections: general information, usability and interface, data safety, administering, and availability of the latest updates. The type of license is crucial for the financial expenses, and there is an opportunity to customize them for the company’s needs as all the solutions are open source. Developers are compared for defining the other projects if further research is needed. Hence, the development potential, and experience of the teams may be assessed. Platform definition is needed for identifying the implementation potentials and restrictions.
Therefore, while Greenstone and DSpace are compatible with MS systems, Fedora may be used for administering the network, and the data storage may be created for Linux, Microsoft, or Mac systems. Website is given for specifying the source where the distributions may be found. Development status is helpful for defining the availability of the latest distributions, as these are the most reliable, stable, and secure. (Ye, 2007)
The technical parameters are not regarded as these could be actual only when software packs are selected for systems and computers with similar parameters. On the contrary, adjustment, security, maintenance, and availability are crucial. As it is stated by Chopoorian and Khalil (2009, p. 45):
Desktop solutions represent the simplest type of DAM. They serve the needs of individual users using relatively small collections of content. This model can be to a handful of stations in a low-security file-sharing network and sometimes even to larger studios, if one person is managing one type of media asset, such as design files. While desktop solutions allow for descriptions and keyword searches, they typically only catalogue thumbnails and references to the actual files, as opposed to the files themselves.
In the light of this fact, it should be stated that the solutions will de defined by the data management objectives outlined by the companies, and collaborative solutions that will be implemented in small companies will not change their business performance effectiveness. This is explained by the fact that small solutions like greenstone offer just the basic tools for data storing and sharing, however, this is more comfortable then storing data on CDs, and flash drives.
DSpace is more process-oriented solution, as his helps to increase the effectiveness of the workflow, and create ‘orbits’ around the centralized data core. However, this does not maintain the option of prioritizing tasks, and the entire progress of data storing is based on effective and comfortable access to the information. This system is able to track the history of events, control the accessibility, and safety of the data.
Another process-centric solution is the installation of Fedora data management system. This will help to make the data management merchant oriented, or industry-centric by customizing the interface, and installing applications that are suitable for business goals. However, Lin and Yang (2006, p. 117) emphasized that specific requirements would be issued for these applications:
Merchant-centric solutions for e-commerce enable an enterprise to serve a high volume of online customers who will browse and purchase media assets. Merchant-centric systems routinely process secure financial transactions, drive order fulfilment processes, interface with inventory systems, and report to accounting systems that can manage things like royalty payments to represented parties.
System architecture building will be the crucial moment, and examination of each system in practice, however, this will be performed only after definition of the goals.
Conclusion / Recommendations
Analysis of three software solutions for data management revealed the fact that all three are suitable for the operations required. However, the entire data management is defined by the business and organizational goals of each company. Therefore, their usability and functionality is the matter of proper and detailed examination. These solutions are DAM based, therefore, the operations that may be performed are process-oriented:
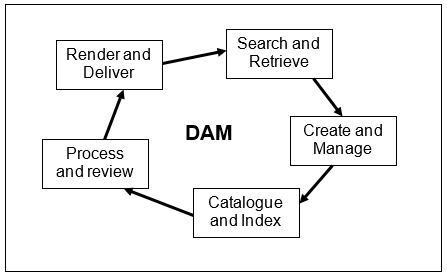
The general scheme of data management is given on the figure below:
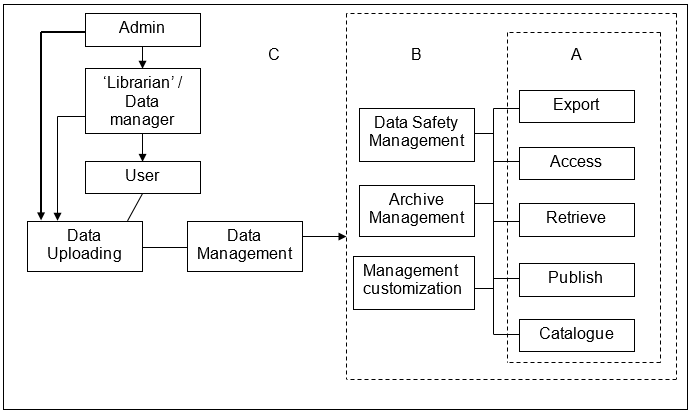
Schematically, the block A represents the opportunities of Greenstone application. Block B – DSpace. Block C – Fedora OS. This means that the task process may be resolved by various tools, sophistication of which depends on the matters of the organizational requirements.
Recommendations that should be given to the Green Plan-IT Group will involve the individual requirements of each customer. In fact, all the three solutions may be integrated into a single system for more effective technical management of the data bases. It is stated that Greenstone and DSpace are cross platform solutions, while Fedora is the entire OS with the set of tools for various aims, including data management, network solutions, and remote administering.
Additionally, the solutions may be based on the sizes of the companies, and their aims: greenstone is suitable for small companies, as cataloguing capacities of this software are weak. DSpace is for larger networks, and Fedora, with all its tools and daemons are for giants. Therefore, the main aim is to define the goals and objectives for each company, and then define the most suitable software solution. Therefore, the implementation of the analyzed solutions will depend on the qualification of the technical personnel, as well as the requirements of the company.
Reference List
Betz, F. 2007. Executive Strategy: Strategic Management and Information Technology. New York: John Wiley & Sons.
Blake, S., Head, J. F., 2007. Using Electronic Data Management to Create a Recruitment Advantage: the ‘digital Back Office’ Provides a New Measure of Stealth Competition. College and University, 82(4), 33.
Chopoorian, J. A., Khalil, O. E., 2009. Mind Your Business by Mining Your Data. SAM Advanced Management Journal, 66(2), 45.
Chu, M. Y. 2004. Blissful Data: Wisdom and Strategies for Providing Meaningful, Useful, and Accessible Data for All Employees. New York: AMACOM.
DSpace. 2011. Introducing DSpace. Web.
Lancaster, G. 2008. Research Methods in Management: A Concise Introduction to Research in Management and Business Consultancy. Oxford, England: Elsevier/Butterworth Heinemann.
Lin, W., Yang, H., 2006. The Implementation of Enterprise Resource Planning and Product Data Management in Semiconductor Related Industries: an Empirical Study in Taiwan. International Journal of Management, 23(1), 117.
Thierauf, R. J. 2007. Knowledge Management Systems for Business /. Westport, CT: Quorum Books.
Wiltrout, R. 2008. Jedmics – Further Expansion of Automated Data. DISAM Journal of International Security Assistance Management, 20, 93.
Ye, N. (Ed.). 2007. The Handbook of Data Mining. Mahwah, NJ: Lawrence Erlbaum Associates.