Abstract
Network virtualization is a relevant study because assumptions about system gadgets, topology, and administration must be reconsidered based on self-administration, versatility, and asset sharing prerequisites of cloud computing foundations. Network virtualization (NV) is characterized by the capacity to make consistent, virtual systems that are decoupled from the core system equipment to guarantee the network can incorporate and support progressively virtual situations.
The paper also highlights the structures and layer of the OSI model. OSI is a reference concept on the communication of applications over a system. A reference display is a calculated structure for understanding connections. The motivation behind the OSI reference framework is to assist merchants and designers in creating products that interoperate and to encourage an unmistakable formation that depicts the elements of a network or transmission framework.
Introduction
This paper reviews the concept of network virtualizations and its importance to data centers and organizations. The research will be conducted using secondary sources such as academic journals and related literature.
This paper will be structured with four sections, which include an abstract, introduction, an overview of network virtualization, and a conclusion. Network consultants focus on server virtualization when they examine cloud computing; however, they do not consider the underlying ramifications of that innovation. The capacity to build virtual situations implies that network providers can make, obliterate, actuate, deactivate, and move them around in the cloud framework.
This versatility and portability have significant ramifications for how network services are characterized and managed to provide cloud services. Thus, servers and network assets benefit from virtualization. System virtualization is turning into a debated issue and not only for exchange but also for organizations like Oracle and other firms who have net virtualization centers.
Network virtualization is a relevant study because assumptions about system gadgets, topology, and administration must be reconsidered based on self-administration, versatility, and asset sharing prerequisites of cloud computing foundations. Static, network and traffic flow should be reevaluated and redesigned to exploit innovations such as virtual NICs and switches, transmission capacity control, load control, and network separation.
For instance, conventional multi-level Web administrations that offer net activity over Ethernet wires would now be able to be virtualized and facilitated on shared-asset frameworks that communicate in a large server at high speed, expanding execution and diminishing wired system traffic. Virtualized activity streams can be observed and balanced as expected to upgrade network execution for cloud infrastructures and requirement.
Furthermore, as virtual environment evolve, system setup strategies cannot accommodate the routing and adaptability requirements; virtualizing the network is a necessity. Network virtualization is relevant because it decreases the number of physical gadgets required for computing, effortlessly segments networks, grants quick change, versatility and smart development, secure physical devices, and creates a failover mode.
Network Virtualization
Virtualization is the capacity to simulate an equipment platform, for example, a server, or system asset in programming. The functionality is isolated from the hardware platform and duplicated with the capacity to work like the conventional equipment (Abdelaziz et al., 2017). A single equipment platform can support different virtual gadgets or machines. Accordingly, a virtualized framework is much more compact, adaptable and financially savvy than conventional hardware-based arrangement.
Network virtualization (NV) is characterized by the capacity to make consistent, virtual systems that are decoupled from the core system equipment to guarantee the network can incorporate and support progressively virtual situations. NV conceptualizes connectivity network and services that have been conveyed using hardware into a virtual system that is decoupled and operates autonomously over a physical interface. NV integrates virtualized L4-7 services and comprehends systems challenges, helping data centers to program and organize network on-request without making physical contact with the infrastructures (Han, Gopalakrishnan, Ji, & Lee, 2015).
With NV, associations can rearrange how they take off, scale, and alter capacities and assets to meet computing requirements. Virtual networking empowers server centers to organize and control suitable and effective routing structures for cloud applications and to adjust the system configurations utilizing programming based management (Jain & Paul, 2013). It is possible to build intelligent systems that are decoupled from physical servers and arrange tasks over virtual space.
Table 1: Network Virtualization Capabilities.
The Operating Concept of Network Virtualization
One of the methods of virtual network is that it disaggregates the hardware service capacities from hardware, into programming. Portions of the elements of a physical device include switches and router infrastructure.
These infrastructures transcend the second and third layers of the open system interconnection (OSI) model. A virtual network adapter serves as the bridge or interfaces unit between the server and the system. Utilizing a virtual network, a user can replace many physical assets with software programming. For instance, a virtual switch contains the entire bundle-forwarding algorithm captured in a physical hub. As a result, the algorithm performs forwarding, locating the addresses of different packet destinations and direction (Jain & Paul, 2013). Thus, network virtualization is an act of decoupling physical devices with hardware addresses and destinations.
Physical Network and Virtual Network
The physical network includes system links, server units, workstations, switches, adapters, connecting cables, and physical servers used to create networking capabilities between one or more links (Figure 1).
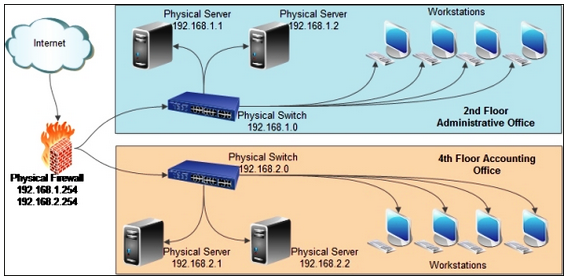
However, a virtual network builds on logic sensing, creating virtual nodes and links while replacing physical infrastructures. The fundamental motivation behind a virtual system is to empower a service center to provide a reliable network for different application hosts. A virtual network is clarified into three categories namely, virtual private network (VPN), virtual LAN, and virtual extensible LAN (Khatibi & Correia, 2015).
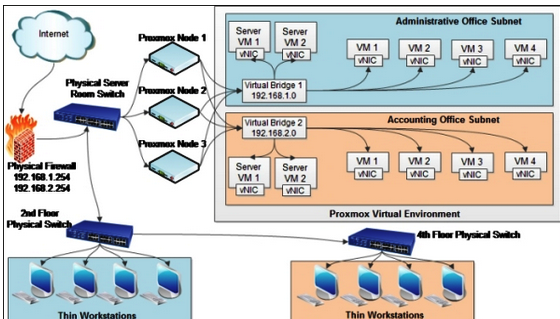
General Approach to Network Virtualization
Virtualization is a strategy to link or separate assets of a PC. Virtualization abstracts from the physical server yet give the client the impression of collaborating straightforwardly with it through the portion of equipment assets.
Other than the quick advancement of virtualization of working frameworks, scientists started to consider the virtualization of switches. This capability implies running a few virtual switches on the same machine from the premise of controlling different systems. Each switch or router belongs to a dedicated server, giving the user full access and control. Although virtual private networks provide a virtualized channel over a physical server, they have a couple of weaknesses in correlation with VN (Khatibi & Correia, 2015). Virtual networks must be founded on similar conventions, topology and address configurations. It makes it difficult to convey or deploy different systems.
Virtual local area networks (VLANs) are the most widely recognized case of link virtualization, permitting the establishment of separated systems or networks where every isolation hub is in a secluded communication area (Khatibi & Correia, 2015).
Most Ethernet routers support link virtualization, which include tagged and untagged VLANs. Other than the virtual local area network, tunneling infrastructures exemplification of Ethernet casings to IP datagrams and protocol label routing are used to make VPNs and in the long-run assemble the establishment for virtual systems in Wide Zone Networks. Links could be wired virtualization or wireless virtualization (Liang & Yu, 2014).
In wired link virtualization, time-sharing frameworks permit clients to work from remote terminals associated with a centralized computer PC, with the impression of working at an individual computer. A node or PC equipment is a physical gadget that can decide the result of abstract activities through physical controls. The components of a node include input, storage, processing, and output. The input is the instantiation of active operations in a physical state.
Virtualization expands asset proficiency and offers clients enhanced functionality. The reviews give additional data about handling virtualization methods, and an incredibly intriguing and enlightening narrative on the compatibility of time-sharing frameworks. One strategy for storage virtualization is a virtual memory, which is another component of node virtualization (Liang & Yu, 2014). The utilization of virtual memory not just mechanizes the storage allotment issue effectively, but empowers machine autonomy, program modularity, sufficient memory addressing and the ability in organizing structured information.
On the other hand, node virtualization facilitates productive sharing and separation of processing assets, for example, CPU, and memory, with the goal that different working frameworks can run simultaneously in physical hardware. Procedures for virtualizing physical nodes incorporate full virtualization, paravirtualization, holder based virtualization. Full virtualization gives a wholly copied machine whereby a guest-operating device can function properly.
Full virtualization supports the best level of isolation in a virtual network; however, it could create performance and asset challenges. Paravirtualization systems create a VM monitor to operate and manage multiple virtual machines (VM). Each VM shows up as a different system with its practical framework and programming (Liang & Yu, 2014). Paravirtualization offers expanded adaptability when several operating devices are required in a physical hub.
This ability results in extended overhead contrasted with compartment-based virtualization. Container-based virtualization builds numerous allotments of operating framework assets, called holders or containers, depending on propelled planning for asset isolation. Thus, the level of achievable seclusion usually is lower in correlation with paravirtualization components (Han et al., 2015). Every container is bound to run the same form of the operating framework from the host machine.
Link Virtualization
The purpose of links is to exchange data between nodes in a dependable way. Links consist of conceptual entities and physical assets which instantiate that data can be transferred between hubs as seen in figure 3.
Thus, connections must be virtualized in theory space, as inks can be wired or remote. There are critical contrasts among wired and remote links, due to the idea of the physical assets utilized. Both wired and remote links transfer data utilizing the electromagnetic range. However, in wired networks, the electromagnetic spectrum is segregated from different connections using physical links. In remote systems, since all connections are transmitted, the network user provides effective isolation and consistent quality.
Links could be wired virtualization or wireless virtualization. In wired link virtualization, time-sharing frameworks permit clients to work from remote terminals associated with a centralized computer PC, with the impression of working at an individual PC (Abdelaziz et al., 2017). Network communications are executed either utilizing dial-up lines or through private lines rented from the PSTN administrators. The dial-up lines are considerably less expensive, but experience security challenges and functionality. However, virtual lines are secured and costly.
VPN services offer the security and performance at cheaper rates exploiting the nature of network traffic between nodes. In this manner, physical connections can be time-shared to give the figment of private connections, known as virtual circuits. VPNs can be scaled and customized to suit client inclinations. Although virtual private networks can separate diverse network systems over a common framework, they are inclined to a few impediments (Abdelaziz et al., 2017).
For example, the conjunction of various organizing arrangements is not conceivable, and virtual systems are not entirely autonomous. Another restriction is that transmission is not supported like other naïve systems. Consequently, it builds additions cost of operations while limiting the network, quality, consistency, and latency (Panchal, Yates, & Buddhikot, 2013).
Although wired connection virtualization has existed for a long time, wireless connection virtualization is a functioning examination zone. Wireless connection virtualization is the procedure of virtualizing remote connections, making virtual assets that are separated and can utilize different innovation and designs freely. Wireless asset sharing is generally unique with virtualization since wireless asset sharing does not make free resources.
Furthermore, virtualization enables the grouping of assets, which asset sharing does not permit. A few difficulties that exist in wireless connection virtualization do not exist in wired connection virtualization because of the distinction between the wired network and the wireless network (Panchal et al., 2013). Due to the characteristic disparity of remote channels, it is difficult to forecast the data throughput of remote connections. Secondly, remote connections are broadcast, and in this way can meddle with a different wireless connection, though in wired connections this does not happen. Another difficulty for remote connections is that wireless nodes have a tendency to be exceptionally versatile, which implies it is difficult to forecast the data exchange between nodes.
Node Virtualization
Some terms are required in the study of network virtualization. Abstraction refers to the act of disregarding or concealing elements to study general qualities, instead of solid realities. Based on this premise, abstraction deals with the manner by which frameworks collaborate, and the intricacy of the communication, by concealing points of interest that are not significant to the association. Thus, abstraction enables structures to be utilized more effectively, however, this comes at the expense of diminished adaptability and customization.
Although abstraction is an essential idea in computing, as it administers the communication between people and PCs, it is not really of significance to virtualization. Nevertheless, it is imperative to note the contrast between abstraction and abstract. The term abstract alludes to thoughts and ideas that do not have physical manifestations. This section considers how virtualization applies to remote systems. A remote system or wireless network is as an arrangement of nodes that can exchange data through links, where a portion of the connections might be broadcast (Figure 4). Thus, wireless systems comprise of two sections, which include links and nodes.
A node or PC equipment is a physical gadget that can decide the result of abstract activities through physical controls. The components of a node include input, storage, processing, and output. The input is the instantiation of active operations in a physical state. All capacities are required in a hub because it is futile to have processing component with no input. Therefore, these four capacities are reliable with the IPO+S framework of registering. It is important to note each of these assets can be represented in the abstract field and virtualized, which enables assets to be utilized more proficiently, and can create new functionality.
Nevertheless, virtualization must be done in theory space. As a result, a network representative can virtualize these assets simultaneously using an additional level of “representation.” If every one of the four capacities is to be virtualized, it is essential to present an extra level of representation. Node virtualization facilitates productive sharing and separation of processing assets, for example, CPU, and memory, with the goal that different working frameworks can run simultaneously in physical hardware. Procedures for virtualizing physical nodes incorporate full virtualization, paravirtualization, holder based virtualization.
The capacities and function of node virtualization make them vital in wireless systems. Process virtualization and storage virtualization are some types of node virtualization. Time-sharing was created to beat the constrained man to machine communication of cluster computing, which had prompted programming blunders and investigating time, and more overwhelming programs. As a result, time-sharing empowers people to make utilization of a PC at the same time. Other than offering clients authorized links to processing assets, which can prompt work overloads and memory issues, the network operator buffer input and consecutively runs client programs effectively.
The full succession of client programs happens much of the time enough that a PC seems to be entirely receptive for all clients. By mapping client-computing time and coordinating strict isolation, clients have the view of the selective utilization of committed processors. As a result, the illusion of different ‘virtual’ processors is made. Thus, virtualization expands asset proficiency and offers clients enhanced functionality.
The reviews give additional data about handling virtualization methods, and an enlightening narrative on the compatibility of time-sharing frameworks. One strategy for storage virtualization is a virtual memory, which is another component of node virtualization. The utilization of virtual memory not just mechanizes the storage allotment issue effectively, but empowers machine autonomy, program modularity, sufficient memory addressing and, the ability in organizing structured information.
Network Virtualization and Open Systems Interconnection (OSI) Model
OSI is a reference concept on the communication of applications over a system. A reference display is a calculated structure for understanding connections. The motivation behind the OSI reference framework is to assist merchants and designers in creating products that interoperate and to encourage a design that depicts the elements of a network or transmission framework (Scroggins, 2017). Most merchants associated with broadcast communications endeavor to represent their items and administrations in connection to the OSI framework (Suresh, 2016). It is vital for an IT expert to understand the OSI Model. The OSI Layered methodology for investigating system issues facilitates network troubleshooting.
Layer 1 of the OSI Model
The first layer of the open systems intercommunication (OSI) is called the physical layer. It characterizes electrical and physical determinations for gadgets. The physical layer describes the connection between a device and a transmission link, for example, a copper or optical link. The layer incorporates the format of pins, voltages, link determinations, centers, repeaters, network connectors, or bus connectors. The significant functions performed by the physical layer can be summarized in three categories.
- Creating and terminating links to a communication system.
- Building participation capacities whereby the correspondence assets are shared among clients.
- Modulation or transformation between the display of information on client hardware and signals transmitted on the network channel. These are signals working over the physical link or radio connection.
Layer 2 of the OSI Model
The second layer of the OSI model is called the data link. This layer creates the medium to exchange information between system servers and monitor network errors. This layer is planned for point and multipoint media, usually for extensive territory media in the phone framework. It is important to note the ISO framework in Project 802 created the LAN architecture autonomously (Suresh, 2016). The institute of electrical and electronics engineering design accepted sub-layering and administration capacities not required for WAN. In current practice, error discovery is available in data link conventions and LAN networks.
The data link layer also provides a control channel, which is utilized at the transport layer. For example, the TCP is deployed in specialties where X.25 offers execution interest (Suresh, 2016). The ITU-T G.hn standard, which gives a fast LAN speed over existing wires, incorporates an entire information interface layer and error traffic control using selective window protocol. Both wireless area network and local area network, create bits from the physical layer into sequences called frames. However, not all bits are deployed in frames, as some perform physical functions.
Layer 3 of the OSI Model
The third layer of the open systems intercommunication is called the network layer. The network layer implements routing capabilities, disintegration reassembly, and error reports. Switches and routers work on this layer by sending information through the expanded system and making the Internet conceivable. The design is an intelligent non- hierarchical framework whose qualities the system expert picks.
Various layer-administration conventions have a place with the system layer, including routing conventions, multicast administration, network data, and system address task. The network layer of the OSI model is segmented in three sub-layers, which include a sub-network access, a sub-network conveyance dependent, and a sub-network conveyance independent. Sub-network access deals with protocols that integrate with the interface to the network. An example this process is the X.25.
Consequently, the sub-network dependent convergence creates balance among networks on a different level. The sub-network independent convergence regulates and controls communications between different networks. The IPv7 ISO 8473 is a specific example of the sub-network independent convergence (Panchal et al., 2013).
Conclusion
Network virtualization describes the combination of one or more platforms to form a virtual network. Virtualization is the act of combining hardware and software infrastructures. It enables network users to emulate links between services and applications. As a result, IT experts combine one or more foundations, which include network hardware, network elements, networks, storage devices, machine elements, network media, and mobile network devices.
Network virtualization could be internal or external. It is important to note that network virtualization is possible through links and nodes. Network nodes include process virtualization, storage virtualization, machine virtualization, input, and output virtualization. The combination of process and storage network virtualization creates the machine node virtualization. Network link virtualization creates an active connection for data transfer. Link virtualization could be wired or wireless network. There are seven layers within the OSI model. The first three layers are the physical layer, data link layer, and network layer.
References
Abdelaziz, A., Fong, A., Gani, A., Khan, S., Alotaibi, F., & Khan, M. (2017). On software-defined wireless network (SDWN) network virtualization: Challenges and open issues. The Computer Journal, 60(10), 1510-1519. Web.
Han, B., Gopalakrishnan, V., Ji, L., & Lee, S. (2015). Network function virtualization: Challenges and opportunities for innovations. IEEE Communications Magazine, 53(2), 90-97.
Jain, R., & Paul, S. (2013). Network virtualization and software defined networking for cloud computing: A survey. IEEE Communications Magazine, 51(11), 24-31.
Khatibi, S., & Correia, L. (2015). A model for virtual radio resource management in virtual RANs. EURASIP Journal on Wireless Communications and Networking, 2015(1), 67-68.
Liang, C., & Yu, F. (2014). Wireless network virtualization: A survey, some research issues, and challenges. Communications Surveys & Tutorials, IEEE, 17(1), 358-380.
Panchal, J., Yates, R., & Buddhikot, M. (2013). Mobile network resource sharing options: Performance comparisons. IEEE Transactions on Wireless Communications, 12(9), 4470-4482.
Scroggins, R. (2017). Emerging virtualization technology. Global Journal of Computer Science and Technology: Information & Technology, 17(3), 1-7.
Suresh, P. (2016). Survey on seven-layered architecture of OSI model. International Journal of Research in Computer Applications and Robotics, 4(8), 1-10.