The Padgett-Beale Merger & Acquisition (M&A) has necessitated the implementation of a cybersecurity management plan. Since the acquisition, several developments have taken place, which will need to be taken into consideration in the development of a new high-level plan. The cybersecurity management plan is designed to allow Padgett-Beale Financial Services (PBI-FS) to begin operations on a new on-island location. Additionally, the new plan seeks to comply with U.S. banking laws, standards, and regulations. Most importantly, the plan highlights such recommendations as risk mitigation, security controls, and replacements for outdated software and hardware.
Before developing the cybersecurity management plan, it is important to highlight the key elements that will need to be secured against the cybersecurity risk. According to Vincent and Trussel (2019), cybersecurity is not a single risk but a collection of risks based on such aspects as the firm’s processes, culture, and actors. For the PBI-FS, the key risk areas include telecommunications, workstations, network equipment, electronic mail, public web server, banking applications and servers, and data backups and recoveries. All these items will need to be safe to void future problems, including any breaches and non-compliance to regulations. Therefore, the current plan will define the objectives, goals, and objectives, and scope of the implementation. Additionally, assumptions, constraints, project management plan, strategy implementation, and enterprise IT architecture will be detailed.
Goals and Objectives
The implementation of the cybersecurity management plan pursues both business and project goals and objectives. The difference between the two is the fact that the business goals and objectives have a broader scope that covers the entire company. Project goals and objectives are narrower and are specific to the cybersecurity plan. Each of these categories is a necessity for the success of implementation. The specific goals and objectives are described in detail in the sections below.
Business Goals and Objectives
- Offer more secure banking services and improve the PBI-FS. The sole need for a cybersecurity plan is to secure all IT infrastructure deemed critical to a business. for the PBI-FS, a name ruined through money laundering may need to be addressed with the promise of transparency and greater security.
- To improve the confidentiality of the stakeholders, especially the customers. The merger may offer better experiences to consumers and revive a dying business. However, it is the stakeholders who need reassurance that their confidentiality will be restored.
- To improve the current state of security for the company information system. The merger and acquisition may present certain security challenges to the entire business. Therefore, the current plan seeks to boost the security of the entire business.
Project Goals and Objectives
- To build the framework for the company’s cybersecurity framework based on safety culture. The cybersecurity management plan is built on policies and plans for all employees.
- To develop an action plan for incident response by outlining specific actions to be undertaken in terms of security breaches. The plan is both preventive and reactive, which means it seeks to prevent incidences and offer effective responses to those that occur.
- To build a platform for data security, which will ensure the privacy of all private financial information.
- To forge cooperation between the stakeholders to facilitate the accomplishment of the M&A.
Scope
The scope of the cybersecurity management implementation plan is broad since it covers both the project and the business. From a business perspective, the cybersecurity management plan affects the information system (IS) integration in the M&A. Studies show that businesses have become pervasively dependent on the ISs, which now play a vital role in the value of M&As (Henningsson et al., 2018). The current M&A poses the same issues because it necessitates the implementation of mechanisms to protect its information system as part of the broader IT infrastructure. The cybersecurity management plan focuses on the actions of the entire company regarding the security of the new systems. Once the businesses have become one, stakeholders across the entire firm can affect the security outcomes. Therefore, the broader scope is to protect the company from any breaches in its IT infrastructure following the M&A.
The narrower scope focuses on the project itself, where the primary focus is to implement cybersecurity plans. The main purpose of a cybersecurity plan is to prevent information and other breaches. The effects of these incidences on the performance of businesses have been extensively explored with a key observation being that data breaches cause both financial and non-financial losses (Juma’h & Alnsour, 2020). The current project seeks to provide a framework on which these issues will be addressed. The cybersecurity plan is based on the fact that the M&A operates and ‘internet of things’, as characterized by multiple networks, hardware, and software, which need to be protected from digital attacks (Salam, 2021). Therefore, the scope includes data storage and retrieval, assessment and correction of vulnerabilities, compliance with the regulations, and data backups. As indicated on the project goals and objectives, the scope also extends to the building and maintenance of a cybersecurity culture through joint efforts of all the stakeholders.
However, several items are beyond the scope of this project. Examples include the actions of the other M&A teams assigned to different tasks. The cybersecurity team may operate autonomously from the rest but all the stakeholders will have different implications on the outcomes of the cybersecurity implementation. Other success factors may also be beyond the scope, which may include such external aspects as changes in IT legislation and compliance guidelines.
Assumptions
The primary assumption made in this project is that the IT infrastructure will remain vulnerable to both internal and external threats. The rationale is that a financial institution would be inherently prone to targeted attempts by hackers and other malicious intentions. Therefore, the primary aim would be to protect the company finances and, most importantly, the money and information about the clients. This assumption is further backed by the idea that financial institutions’ weakest points are their networks and other shared IT resources, which can be accessed remotely. Based on these assumptions, the cybersecurity management plan targets to strengthen all the weak points and to design them to raise the necessary red flags once attempts have been made.
Constraints
Project Constraints
- The main project constraint is the fast-changing technologies and the emergence of new and disruptive ones. The current project involved the development of technical aspects to support and protect the current and new hardware and software. However, rapid development means that the current solutions could become obsolete within a short time.
- The second constraint is time, which affects all projects and hampers their progress. The M&A has to be accomplished within a defined timeframe, which means that the team tasked with cybersecurity management will have limited time. Additionally, the fact that there will be new hardware and software to replace old ones means time will be consumed in configuration attempts, as well as any tests needed.
- Legal compliance is another constraint that will affect all the project efforts. With new developments in technology, new laws are emerging, most of which are intended to safeguard the interests of the consumers (Selby, 2017). The implementation of the cybersecurity plan will be bound by these legal constraints that must be incorporated into the project tasks.
Barriers to Success
The greatest barrier to the success of the project is the incompatibility of the systems, especially with the new industry 4.0 transformation. According to Tripathi and Gupta (2019), industry 4.0 transformations cover such dimensions as organization culture, strategy, innovation, data availability, agility, and smart analytics. The M&A will have this consideration to make, which means that the cybersecurity team will have to give priority to any potential developments in this regard. The main argument is that companies are increasingly becoming interested in the new applications of recent technologies (Horvath & Szabo, 2019; Herceg et al., 2020). Therefore, the environment in which the cybersecurity management plan will need to work is extremely uncertain. New security requirements, most of which may still be under development, will be needed. If the team fails to anticipate the new needs and requirements, the security plans will fail to achieve the desired effects in terms of cybersecurity.
Another potential barrier to the success of the project is financing. It is important to consider that the current project is being implemented as part of a broader undertaking involving the M&A. therefore, limited finances may be allocated to the team, which might make its accomplishment difficult. As mentioned earlier, the fact that novel technologies may need to be considered means that it could be necessary to test certain aspects over time before full implementation. Such tests can be hampered by inadequate finances and, hence, the success of the project. However, it can be argued that the primary focus will be on existing IT infrastructure, which may alleviate the need for novel solutions.
Project Management Plan
Projects involving IT tend to constitute considerable investments that are intended to continue growing as a business seeks to improve operational efficiency. Therefore, firms have to learn how to leverage people, processes, and technology in the mitigation of IT project risks (Maruping et al., 2019). The cybersecurity project takes the form of a digital transformation where several factors are to be considered. People, process, and technology are the key dimensions in this project management plan where the main activities are outlined below.
People
People comprise the stakeholders who will be using the systems and who affect their security. The cybersecurity plan is intended to adopt a risk-based approach as described by Boehm et al. (2019), which begins with the governance of people and their activities. This dimension involves protecting the IT infrastructure from such incidences as unauthorized access and malicious activity from both internal and external stakeholders. Therefore, the plan for the people dimension in this cybersecurity management implementation includes the following:
- Access control – one of the best initiatives in cybersecurity is controlling the access of the IT systems and the shared IT resources. Access control means restricting and authorizing access to the infrastructure, which is achieved through such means as passwords and other forms of protection. The fact that cybersecurity seeks the protection of financial information means that effective restrictions need to be implemented where only a few people can access sensitive data.
- Data policy – a data policy dictates how data can or cannot be used in an organization. The cybersecurity management plan takes into consideration the fact that the previous protections were inadequate and that they made it possible for users to launder money. Strict data policy seeks to prevent such usage of data in addition to protecting any sensitive information.
- Safety culture – in cybersecurity, a safety culture can be referred to as a cybersecurity culture (CSC). According to Corradini, (2020), CSC is unique to organizations because it cannot be replicated by others in terms of people’s values, processes, and technologies. The CSC is intended to create the necessary values that are currently lacking regarding the safe use of the IT infrastructure. In other words, the cybersecurity plan teaches people that security will not merely be an IT department problem but a collective effort from all organizational members.
- Accountability – in cybersecurity, accountability can be described as the principle that all individuals entrusted to safeguard and control the IT infrastructure are answerable to the proper authority in case of such incidences as loss or misuse of the information or other key IT material. Holding people accountable begins by highlighting what people will be responsible for and how they are expected to handle the systems.
Processes
The dimension of the process involves outlining the activities within the systems. In the cybersecurity management plan, the process entails the specific actions intended to protect the IT infrastructure. The plan seeks to address several problems that have been observed with the previous security efforts, including fraud and money laundering. The processes that should help to protect IT systems and prevent the occurrence of these acts are summarized as follows:
- Fraud prevention – the cybersecurity management plan monitors all transactions, their sources, and the parties involved to help prevent fraudulent activity. Verifications for each transaction will be required regardless of the amount, which should help ensure the people initiating them are validated.
- Authentications for online banking – the M&A will be involved in online banking services, one of the most vulnerable operations for any financial institution. As a further effort to prevent fraud, the cybersecurity plan implements a mechanism for authenticating both the users and the transactions. The authentication protocols will be continuously updated as the online banking environment remains highly dynamic.
- Restricting access to personal information – fraud and theft in online banking are often facilitated by the ability of authorized users to access the personal information of the customers. Therefore, the key protection process will involve an access protocol to be followed when such access is required. Most importantly, only account holders and the selected company personnel will be allowed access, all of whom will need to be accountable for both the access and use of the data.
Technologies
- Artificial intelligence and deep learning – these new technologies will be used in access control and restrictions to personal data access. Artificial intelligence can be applied in such processes as two-factor authentication, which is intended to confirm the users’ identities based on two or three parameters. Deep learning can also be useful in data analysis, including such aspects as real-time communications, transactions, and logs. The data analysis from deep learning serves the purpose of detecting threats and unwarranted activities.
- Embedded hardware authentication – PINs and passwords have proven inadequate because they do not offer foolproof protection to hardware. Embedded hardware authenticators are emerging technologies that can be used to verify users’ identities. Examples include Intel’s Sith-generation vPro Chips, which have been designed to revolutionize authentication security. Banking systems and their inherent vulnerability requires that such extreme steps be taken to protect even the hardware.
- Data encryption – data shared across the networks will need to be encrypted to prevent hackers from easily copying and reading it. Decryption codes will only be available at the destination of the data, which means that only the intended recipients will be able to read it.
- Firewalls – firewalls remain one of the basic security technologies used to filter incoming packets from the internet. The primary purpose is to prevent unauthorized communications into and from the system. The online banking systems will be particularly vulnerable and the cybersecurity management will ensure adequate firewalls for packet filters, stateful inspection, and network addressing translation.
Strategy Implementation
Security Controls
Baseline Controls
- Strict authentication protocols – authentication protocols will be necessary for access to the shared resources and all access points. Internal access will require access controls for both hardware and software. For external users, two-factor authentication will be the primary security control, which will be accompanied by such measures as firewalls.
- Data encryption – all sensitive data shared across the networks will be encrypted to prevent malicious attempts to copy and read information.
- Data backup – a backup infrastructure will be created to caution against any system failures. All user data will be backed up and regularly updated to allow access when needed.
Compensatory Controls (Administrative, Operational, Tactical)
- Firewalls – firewalls will be used as the primary perimeter defense, especially for all access points over the internet. The firewalls will filter all internet packets to control who accesses the systems and specific data.
- Recovery and response plans – the recovery plan is intended to support the data backup operations in case of system failures. The recovery plan provided a guide on how to respond to any incident, especially after a system failure. The response plan handles all other incidences and seeks to address problems as hacking or other malicious activity.
System Development Life Cycle/Schedule
The system development life cycle comprises seven stages, as shown in Figure 1: planning, requirements or analysis, design, development, testing, deployment or integration, and maintenance. PBI-FS will use this framework in the implementation of the cybersecurity management plan, especially because new security systems will be developed and implemented. The planning stage helps define the problem and scope of activities. Additionally, the planning stage determines the objectives of the new systems and helps secure the necessary funding. PBI-FS requires new security systems for the IT infrastructure to facilitate the M&A. Among the problems identified include the lack of a formal IT security platform and the loopholes that have been exploited to facilitate fraud and money laundering. The planning stage clarifies that these problems are to be resolved and helps to accomplish the second stage: the requirements analysis. In this phase, both software and hardware requirements are outlined, as well as any potential alternative solutions identified in stage 1. Research and analysis will determine the security needs of all end-users, which will be used in the creation of a requirement specification document.
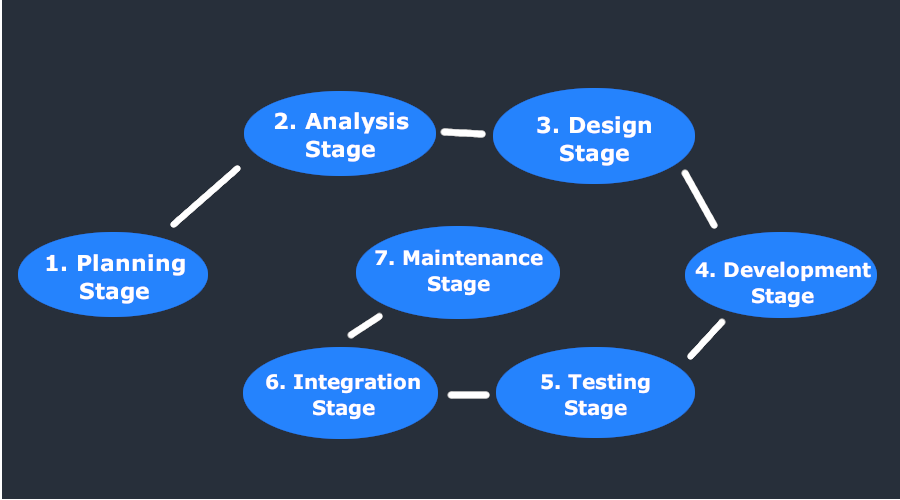
The design stage outlines the details for the overall system implementation. In the cybersecurity plan, the design stage will involve specific aspects of the security infrastructure, including security controls for both hardware and software. In other words, the design state covers the requirement specification document into a more logical structure that can be developed in a programing language or other system applications. The development phase follows the design stage where all the coding and applications are built to mirror the designs and to meet the specifications. In the cybersecurity management plan, the actual security platform is built, including all controls and frameworks. The technologies are either developed or applied to the security infrastructure as necessary.
Once the development is complete, the stage that follows is testing, which is done to assess whether the problem is solved. The testing phase is critical because it helps the team assess whether the design works as desires or whether it meets the requirements. Any challenges, deficiencies, and defects are monitored and corrected until the system perfectly solves the problem. When the testing is successful, the deployment or integration step is carried out, which means the actual installation of the security infrastructure. All modules and items in the framework are integrated and configured and protocols implemented.
The last phase of the system development life cycle is the maintenance stage, which can be a one-off activity or a continuous process. As a one-off activity, the maintenance stage entails addressing any residual bugs not covered during implementation. Additionally, any changes that might be necessitated by such processes as the configuration are implemented at this stage. As a continuous process, the maintenance stage involves continually monitoring and updating the system as necessary. This is because cybersecurity does not end with the implementation of a plan and technologies. The rationale is that technological development means that new requirements emerge, which necessitates new updates on the existing IT security infrastructure.
Milestones
Milestones in project management are critical because they help inform the progress of the project. According to Eik-Andresen et al. (2016), milestones can also be used as performance indicators depending on the nature of the project. The system development life cycle can be used to derive critical milestones involving the strategy implementation, including requirement specifications, prototype developments, and a fully functioning system or actual deployment. The success of the cybersecurity management plan depends on the development of a cybersecurity infrastructure to address the current problems. Therefore, the key milestones will include problem identification, proposed solution and alternatives, prototypes and testing, and solution implementation. The problem identification simply involves an analysis of all security issues that need to be addressed, and its achievement can be evidenced by a requirement specifications document. Solutions and alternatives can involve designing potential solutions and any suitable alternatives. The actual development will begin with prototypes that will be tested before they can be implemented as a solution. When the system is online and fully functional, it will mark the final project milestone.
Resource Requirements
The resource requirements for the cybersecurity management plan help outline what will be needed to facilitate the accomplishment of the project. As in all projects, the key resources are people and finances. People include the project team and any other personnel hired throughout the project. In this case, cybersecurity experts, program developers and designers, and other IT personnel will be engaged throughout the project. Finances are used to make purchases and payments for services, including the labor offered by people. In this project, some systems will be purchased rather than developed, especially the hardware. Software vendors may also offer ready-made alternatives which will also be considered. The amount of money will depend on the labor costs and prices of both hardware and software purchased.
Enterprise IT Architecture 1000
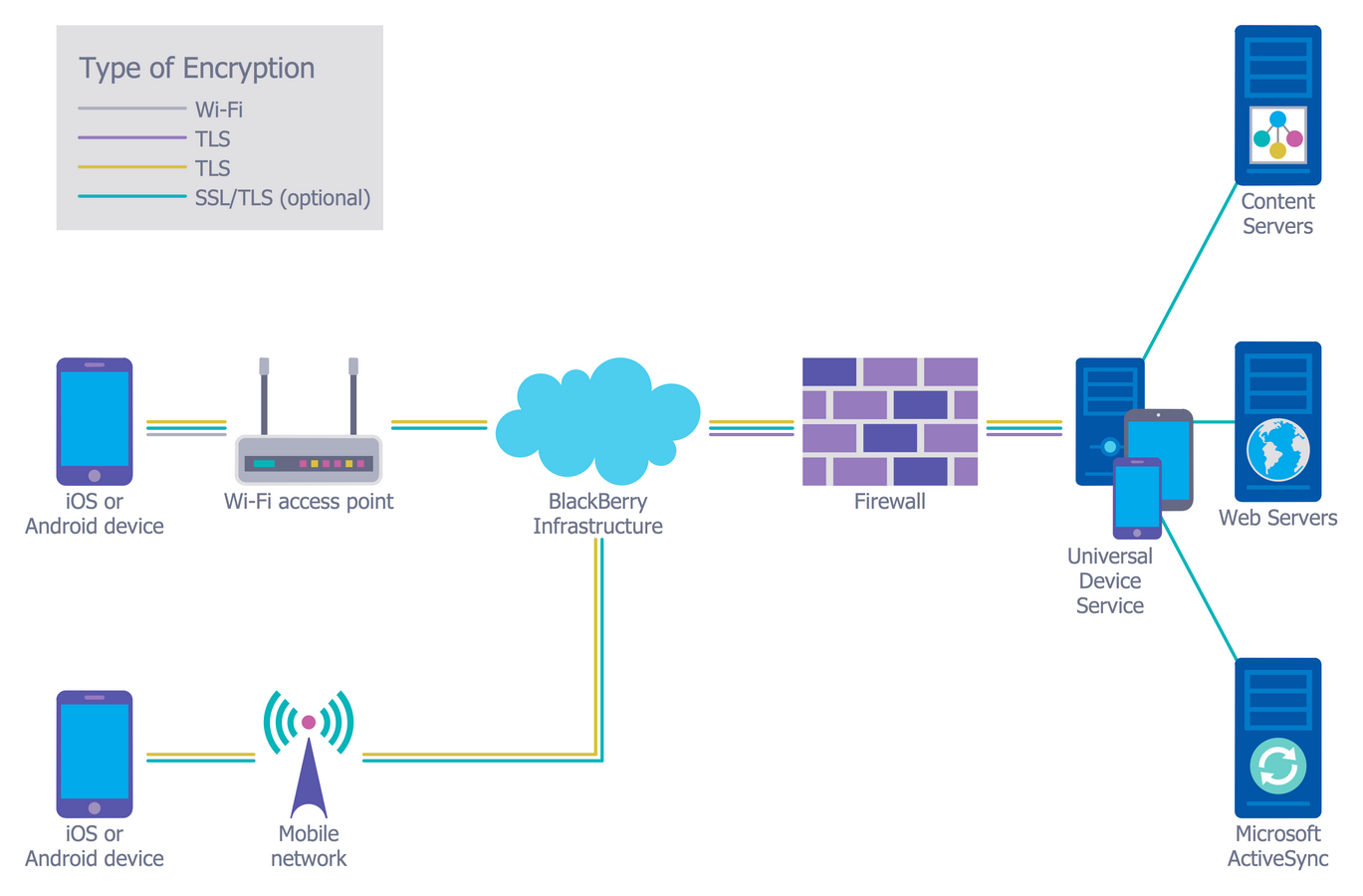
Hardware
The cybersecurity plan seeks to implement massive changes to the current security infrastructure, which includes various hardware resources. As indicated in Figure 2 above, servers form much of the internal networks for which the company must protect. The hardware will also include computers used by the company staff to access the IT systems. Other forms of hardware may also be considered, for instance, laptops, phones, and printers. It is important to acknowledge that the cybersecurity plan seeks to update some of the hardware. The fact that the current IT security infrastructure is outsourced means that the M&A will have to invest huge sums of money on new hardware for both the active system and the backups.
Regarding the servers, the cybersecurity team must have to make critical decisions, including which servers to use and how to protect them. According to Aaron (2019), different server hardware is available for businesses, whose primary purpose is to manage networks and their shared resources. Additionally, the servers provide services to users, both internal and external. Due to the different functionalities, the cybersecurity groups will need to examine the current servers and their efficacy for servicing the current user needs. Replacement or updates will be made depending on several factors determined by the team as outlined in the requirement specifications. Besides the servers, internal computers, laptops, printers, and phones are to be updated or replaced accordingly. Such issues as usability, capacity, and scalability of capacity will be used to determine the course of action.
Software
The IT architecture can be described as an internet of things (IoT) because it connects systems, data storage, applications, and services. According to Ullah et al. (2019), all these interconnected elements can be gateways for cyber-attacks, which means that they are also the targeted areas in cybersecurity planning. In addition to the protection of hardware, much of the security aspects will cover the software elements and access points to the network servers. Firewall software will be a key element, especially one tied to external access points. The internet will be a key access point to the internal IT infrastructure, which means a perimeter defense will need to be established. Such aspects as two-factor authentication and deep learning software will be used to monitor any activity from the internet.
In the internal network, multiple software applications will be used, including databases and analytics. All software will be protected using the relevant antivirus applications, which will be among the items purchased from external servers. Depending on the developers, the type of antivirus will depend on whether the applications come with integrated antivirus offers alongside the software by the vendors. Alternatively, software without an embedded antivirus will be protected using a purchased antivirus from trusted vendors. The fact that the business offers web-based mobile banking means that mobile applications will be developed. These represent vulnerable software and a critical external access point that will need protection. These will integrate artificial intelligence and firewalls to achieve utmost security.
Network Infrastructure
Network infrastructure entails all resources of a network, including internet connectivity, business operations, communication, and management of applications, users, devices, and services. Internally, the network infrastructure comprises the servers and the interconnected devices. Examples include routers, desktops, laptops, printers, and phones, which will be attached to databases and other shared resources. The cybersecurity plan involves protecting these networks from malicious activity. The concept of network infrastructure security involves the process by which the network infrastructure is protected through preventive measures. Therefore, the security measures will include access control, firewall, virtual private networks, behavioral analytics, wireless security, and intrusion prevention systems.
Multiple approaches to network infrastructure security are available for PBI-FS, from which the best will be selected. Examples include segmenting and segregating functions and networks. This can be achieved through the use of such hardware as routers, whose primary function is to filter broadcast traffic. Another approach is the limitation of unnecessary lateral communications, especially peer-to-peer interactions. The company handles sensitive user data whose communication across a network should be highly restricted. Hardening network devices is another mechanism, which is focused on making sure industry standards are maintained regarding such aspects as available services, restricting physical access, network encryption, protecting routers, and use of strong passwords. Lastly, network infrastructure security can be achieved through securing access to infrastructure devices. The security options for the infrastructure hardware have been explored, and these tend to protect even the network’s access points.
Cybersecurity Defenses
- Data encryption at every point – one of the best cybersecurity defenses is data encryption, which should be implemented at all points. This defense seeks to protect all sensitive data that is in use, transit, or at rest. Therefore, PBI-FS should focus on purchasing software with the necessary encryption capabilities.
- Cyber threat awareness – PBI-FS will be faced with both generalized and specific cyber threats. The generalized category comprises ransomware, data breaches, and malware, which should all be addressed. The specific category of cyber threats includes specific intensities of the generalized threats. For example, data breaches may involve access to sensitive data, deletion, or copying or manipulation of information within the storage devices. Cyber threats awareness is a defense that focuses on raising red flags and alarms when these threats occur.
- Threat intelligence – the use of artificial intelligence is growing rapidly, which means that the nature of threats is also continually evolving. Threat intelligence entails the use of artificial intelligence systems to assess unexpected applications, data, and user behaviors. Most importantly threat intelligence should help isolate and contain suspicious activity using early warning.
- Cybersecurity awareness training – the employees working for the company can also pose a threat to IT security. Therefore, a good cybersecurity defense should include training all users regarding security matters and equipping them with the ability to detect threats. The workers can be taught how to avoid infections and which red flags to look for within the network.
References
Aaron, J. (2019). Which type of server hardware is best suited for your business?Data Center Post.
Boehm, J., Curcio, N., Merath, P., Shenton, L., & Stähle, T. (2019). The risk-based approach to cybersecurity. McKinsey & Company.
Corradini, I. (2020). Building cybersecurity culture. In Building a Cybersecurity Culture in Organizations. Studies in Systems, Decision and Control (pp. 63-86). Springer.
Eik-Andresen, P., Johnsen, A., Landmark, A., & Sørensen, A. (2016). Controlling a multibillion project portfolio – milestones as key performance indicator for project portfolio management.Procedia – Social and Behavioral Sciences, 226, 294-301.
Henningsson, S., Yetton, P., & Wynne, P. (2018). A review of information system integration in mergers and acquisitions. Journal of Information Technology, 33(4), 255-303.
Herceg, I., Kuc, V., Mijuškovi´c, V., & Herceg, T. (2020). Challenges and driving forces for Industry 4.0 implementation.Sustainability, 12(10), 1-22.
Horvath, D., & Szabo, R. (2019). Driving forces and barriers of Industry 4.0: Do multinational and small and medium-sized companies have equal opportunities?Technological Forecasting and Social Change, 146, 119-132.
Juma’h, A., & Alnsour, Y. (2020). The effect of data breaches on company performance.International Journal of Accounting and Information Management, 28(2), 275-301.
Maruping, L., Venkatesh, V., Thong, J., & Zhang, X. (2019). A risk mitigation framework for information technology projects: A cultural contingency perspective. Journal of Management Information Systems, 36(1), 120-157.
Preston, M. (2021).System development life cycle guide.Cloud Defense.
Salam, A. (2021). “Internet of things for sustainability: Perspectives in privacy, cybersecurity, and future trends. In Internet of Things for Sustainable Community Development. Internet of Things (Technology, Communications and Computing) (pp. 299-327). Springer.
Selby, J. (2017). Data localization laws: Trade barriers or legitimate responses to cybersecurity risks, or both?International Journal of Law and Information Technology, 25(3), 213-232.
Tripathi, S., & Gupta, M. (2019). Impact of barriers on Industry 4.0 transformation dimensions. International Conference on Precision, Meso, Micro and Nano Engineering, (pp. 1-6). Copenhagen.
Ullah, F., Naeem, H., Jabbar, S., Khalid, S., Latif, M., Al-Turjman, F., & Monstarda, L. (2019). Cyber security threats detection in internet of things using deep learning approach. IEEE Access, 7, 124379-124389.
Vincent, N., & Trussel, J. (2019). Predicting reported cybersecurity breaches using financial measures.Journal of Forensic and Investigative Accounting, 11(3), 494-514. [PDF Document]