Introduction
The Padgett-Beale Merger & Acquisition (M&A) squad works under Padgett-Beale’s Chief Information Security Officer (CISO) straight management. Currently, the team is planning to incorporate a new acquisition, Island Banking Services (a non-U.S. firm), into the organization because Island Banking Services had been announced bankrupt after operating for five years. This incident happened after the firm and its brigadiers were involved in a money laundering offense filed at the bankruptcy courts. After the Padgett-Beale Company merged with Island Banking Services, people will regard the resulting company as PBI Financial Support (PBI-FS). According to Crumpler & Lewis, 2019, performing gap analysis is crucial before merging to facilitate more benefits than losses. The gap analysis also enables businesses to improve their profitability, efficiency, and products by analyzing the possible gaps that may interfere with the organization’s processes.
A gap analysis will enable Padgett Beale to be aware of the potential threats that would have invaded the Island Banking Services system, contributing to its bankruptcy through a third party. Involving a third party during a merger and acquisition is important because it will let Padgett Beale know the potential risks before starting operations (Tirumala et al., 2019). The idea of involving a third party is evident in the case study. Padgett Beale includes the bankruptcy courts during its acquisition with the Island Banking Services to help access the firm’s records to resume Island Banking Service’s processes. Organizations involve third parties to reveal their capabilities and influence their external invention.
Supplementary assets purchased by the Padgett-Beale incorporated in the auction include the certificates, software, and hardware mandatory in operating the company’s internal computer networks. Additionally, organizations involve third parties to achieve their objectives, enhance their cybersecurity, and speed up their processes. Padgett-Beale’s primary intention of merging the company was to relocate the call epicenter to a property owned by the company roughly 10 miles from the company’s previous location and opposite the newly released Padgett-Beale resort. Padgett-Beale’s threat manager recommended people amend the plan of merging the Island Banking services with Padgett Beale to operate Island Banking’s services as a wholly supplementary firm for five years. Padgett-Beale’s threat manager viewed this as the best decision instead of instantly integrating the company as Padgett-Beale’s operational element. Merging businesses is important because it increases the market share of the new company and reduces operating costs.
Padgett Beale’s incorporation with Island Bankers Services will also enable PBI-FS to expand its business to a large firm and prevent a possible closure of the new company. In the meantime, the Padgett-Beale Merger & Acquisition (M&A) leader will act as the topmost functional officer of the PBI-FS. Padgett-Beale’s Topmost Statistics Security General will be renamed PBI-FS as the corporation hunts for an enthusiastic CISO for the subsidiary. Padgett-Beale needs to recognize cybersecurity threats and means to mitigate the risks due to the criminal operations that rendered the company bankrupt; financial service industries have regulatory and legal standards that govern them. In addition, before companies merge, they need to secure their accounts to prevent unauthorized access from other users. Therefore, through risk analysis, the company will be able to identify risks (Sapienza et al., 2018). PBI-FS should ensure that it adheres to the regulatory and permitted standards that govern financial systems. This paper proposes the cybersecurity strategies and actions Padgett Beale should take to achieve its requirements.
This paper starts with a gap analysis to help Padgett-Beale recognize the threats transmitted to PBI-FS for the acquirement process. Step 1 outlines the security issues that attacked the Island Banking Services, including ransomware and IoT attacks. Step 2 creates a risk register that highlights the risks stated in step 1. Step 3 reviews the laws and supervisory rules related to the Monetary Facilities industry. Step 5 studies Risk Management and the Cybersecurity Framework in the NIST Cybersecurity Framework. Step 6 develops a Cybersecurity Plan that presents detailed actions that the corporation should take to device recommended risk vindications. Step 7 sets and documents a projected strategy of action and execution timeline that discourses each component of the cybersecurity approach recognized in step 6. Step 8 generates a summary of commendations regarding vindicating the risks acknowledged in steps 1-7. The last part of this paper offers a conclusion and a memorandum that addresses the Merger & Acquisition Team on the strategies they should consider.
Gap Analysis
Cyber threat landscapes are ever-changing, and the cybersecurity controls that function today may not work for the organization tomorrow. Cyber-attacks occur often, and alteration insecurity may lead to losing customers’ confidential information, contributing to financial consequences and an altered reputation. Gap analysis enables companies to identify their network security witnesses to ensure an effective and robust network. Gap analysis allows companies to know what they should engage in by comparing their actual activities against their best practices and issuing insights on how their organization should put correct controls and structures in place. Performing gap analysis correctly enables companies to benefit more than lose (Crumpler & Lewis, 2019). Gap analysis is an in-depth evaluation that allows businesses to distinguish between their present state of information security and industry requirements. Conducting gap analysis enhances companies’ comprehension of their vulnerabilities and cyber-security risks to work closely on the gaps hindering their security. Additionally, gap analysis helps firms improve their services, efficiency, and profitability by knowing the gaps hindering them from achieving their goals. Once a company completes conducting gap analysis, it will emphasize improving the identified gaps.
Step 1: Cybersecurity Issues
Ransomware Attacks
Ransom attacks are malicious software used by cybersecurity criminals to alter an organization’s system. When ransomware infects computers or networks, it prevents the networks from accessing their system by encrypting their data. Ransomware attacks include hacking a user’s information and preventing users from accessing the data without paying a ransom (Sapienza et al., 2018). Ransomware threats are common to individuals, particularly businesses that cannot access sufficient data to run their day-to-day activities. In some circumstances, ransomware attackers do not release data even after users have made payments. Instead, they work hard towards extorting more money from users. Organizations affected by ransomware occurrences have three choices after an attack. First, the organization can either pay for redeeming, eliminate the malware, or revive their devices. Attack vectors often used by coercion Trojans include; software vulnerabilities, phishing emails, and Remote Desktop procedures. Therefore, ransomware attacks can attack both companies and individuals.
Crypto developers regularly add countdowns to their redemption demand; organizations that do not pay their ransom before the deadline lose their files. In addition, due to the high number of individuals who are not aware of the importance of backing up their data in an external physical backup device or the cloud, crypto-ransomware devastating impacts the people. Eventually, many organizations pay the ransom to access their files (Singh & Jain, 2018). Organizations should protect their data against ransomware attacks by avoiding clicking on unsafe links. They should also ensure that they avoid disclosing their information to third parties. Companies should avoid opening suspicious emails, resisting unfamiliar USB sticks, keeping their operating systems and programs updated, using only familiar download sources, and using public Wi-Fi VPN services. Clicking on links available on unknown websites or spam messages may start automated downloads that infect an organization’s systems.
Organizations should not reply to emails asking for their organizational information as cybercriminals may be using the tactic to attack their knowledge, which they later use to send phishing emails to the organizations. In case an organization doubts the origin of an email, contacting the sender is essential. Organizations should also avoid opening dubious-looking files on emails. They must first ensure that the email is trustable by checking if the sender’s address is correct. Infected attachments may run malicious commands that offer malware monitoring of an organization’s computers (Tirumala et al., 2019). Organizations should update their operating systems and programs regularly to eliminate malware attacks.
When conducting updates, organizations should ensure they benefit from the current security batches making it hard for criminals to explore vulnerabilities in their programs. Relying on trustworthy and verified platforms minimizes the risks of ransomware. Organizations can recognize trustable websites by observing trust seals (Tirumala et al., 2019). For instance, organizations should ensure the address pages they are visiting use HTTPS rather than using HTTP. The s in the HTTPS implies that the website is secure. In addition, organizations should be cautious when downloading any attachments. Organizations should also avoid making transactions using public Wi-Fi networks to protect their data against attacks.
IoT Attacks
The devices involved in IoT include mechanical, computing, and digital devices that can transmit data autonomously from one network to another. IoT devices comprise mobile phones, laptops, desktops, and smart security devices, among others. The increasing rate of IoT adoption has increased cyber-security challenges (Tsiknas et al., 2021). Attacks made on IoT devices may lead to the compromising of sensitive client data. Protecting IoT devices is becoming a big challenge because accessing these devices may open doors to malicious attacks. Organizations should update their systems regularly to reduce IoT attacks.
Cloud Attacks
In the contemporary world, many people use cloud facilities for individual and professional purposes. Hacking cloud channels to alter user data is among the cyber-security challenges companies encounter. For instance, exposing users’ private photos poses a massive threat to an organization and may contribute to the collapse of an organization. Organizations should ensure that Multi-Factor Authentication (MFA) is ever for all cloud services (Tirumala et al., 2019). Multi-Factor Authentication provides that stolen passwords alone cannot grant attackers to a company’s critical information. In addition, companies should identify and combine their resources within IT-authorized cloud devices that have been vetted fully for Multi-Factor Authentication support, PII security controls, encryption support, and SOC-2 compliance (Tirumala et al., 2019). Companies should also ensure that all their workers have the least access privileges required to carry out their job. In addition, companies should eliminate stale or unused permissions of workers and external contractors to smoothly minimize their attack surface by reducing the risk of data loss and account takeovers.
Phishing Attacks
Phishing attacks are coordinated engineering attacks that hackers regularly use to rip off user information, such as acknowledgment card numbers and login authorizations. Once the hacker gains access to a user’s confidential information, they use it for their benefit, such as transferring money illegally or shopping online (Singh & Jain, 2018). Phishing attacks are common among hackers because they get an opportunity of exploiting the user’s information until the user realizes it. Organizations should protect their systems against phishing attacks by avoiding clicking on suspicious links and updating their software. They should also avoid sharing their financial or personal information, protect their accounts using Multifactor verification, and avoid clicking on any pop-up links.
Software Vulnerabilities
Advanced software also has vulnerabilities that challenge its cyber-security because the adoption of advanced devices is currently joint compared to the past. Companies and individuals do not update their software because they view it as unnecessary. Nevertheless, updating a business’s software with the latest versions should be prioritized (Singh & Jain, 2018). Old software has a high chance of containing security threats installed by developers in new versions. To reduce software vulnerabilities in organizations, organizations should restrict the number of people accessing their sites, employ solutions that bloc exploitative behaviors, and monitor all logins to recognize Indicators of Compromise (IoC).
Outdated Software
Not all cyber-security challenges come in the form of software threats. Software developers have realized the risks involved in software vulnerabilities. Hence, they are offering periodic updates. Nevertheless, the new updates may not be friendly with the device hardware, contributing to out-of-date hardware. Outdated software lacks ransom protection, disrupts business processes, exposes a system to third-party vendors, and exposes an approach to IoT (IoT) risks (Tsiknas et al., 2021). Organizations should update their software regularly to secure their devices against attacks.
Denial of Service
Denial of service is a cyber-attack that interferes with networks or computers not responding to inquiries. Denial of service attacks shuts down machines and makes them inaccessible by sending information that destroys the machines. In addition, DoS attacks interfere with the services expected by account holders, members or employees. DoS attackers often target highly-performing organizations, including trade organizations, government organizations, media companies, and commerce and banking organizations. DoS attacks do not contribute to the loss of important information or theft but cost organizations money and time to ease the situation. DoS attacks occur by crashing services or flooding the assistance of an organization (Gupta & Agarwal, 2017). Flood attacks happen when an organization’s system receives more traffic that slows down servers and stops them from functioning. Organizations can eliminate DoS attacks by preventing spoofing, limiting broadcasting, streamlining their incident responses, and ensuring all endpoints are protected to eliminate familiar vulnerabilities. In addition, businesses should ensure that their firewalls limit traffic entering their systems, and they should monitor their networks to detect DoS attacks.
Unencrypted Data
Data encryption is an essential part of good cyber-security. Organizations need to encrypt data stored in computers to avoid being accessed by hackers once they steal it. Unencrypted data makes it easy for hackers to access user information and create severe issues for the financial institution (Gupta & Agarwal, 2017). Organizations should encrypt their data to provide security, maintain their integrity, protect their privacy, comply with organizational rules, and protect the data transmitted against other networks.
Manipulated Data
This threat may be complex to detect because financial institutions may incur a lot of dollars. Precisely, data manipulation refers to cyber activities where malicious activities alter, modify, and tweak an organization’s valuable documents and data rather than directly stealing an organization’s data to cause misery to the firm (Gupta & Agarwal, 2017). Organizations can protect themselves against data manipulation by achieving optimal security with a famous cybersecurity paradigm that involves data integrity, endpoint security, manual data monitoring, and encryption.
Spoofing
Spoofing occurs when an invader impersonates a certified user or device to spread malware, intrude into access control systems, or steal data. Spoofing can occur through servers, IP addresses, texts, phone calls, emails, and websites. Usually, spoofing aims at accessing personal information, spreading malware attacks, or stealing money. Scammers will always use spoofing to steal an organization’s identity and assets (Lamba, 2020). The most common types of spoofing include; Caller ID Spoofing, Websites Spoofing, Email Spoofing, Text Message Spoofing, GPS Spoofing, DNS spoofing, ARP spoofing, and IP address spoofing. In Internet Protocol Address spoofing, an attacker manipulates the Internet Protocol (IP) header that the packet looks like from a verified source.
Spoofing lures the target device into enhancing invaders to access sensitive information or accommodating malicious code. Assailants use internet Protocol spoofing to perform attacks like denial-of-service, whereby attackers feed the network with more information than it can handle by sending millions of Internet Protocol Packets from several spoofed addresses. Hackers can also trick the IP address of specific machines into sending several packets of information to other devices on a similar network (Lamba, 2020). Since engines spontaneously send responses once they accept an IP packet, this causes the spoofed machine to get knocked offline. Attackers also use Internet Protocol spoofing to undergo authentication that depends on the IP address of a device. Hackers may trick systems built by organizations to assume particular IP addresses are trustworthy to accept connections from untruthful machines that fake the IP address of a trusted engine.
Address Resolution Protocol (ARP) spoofing can identify legit devices on networks by resolving Internet Protocol addresses to particular Media Access Control (MAC) addresses. During ARP spoofing, attackers send ARP packets to networks, which appear to be from legit devices. Since the devices on a similar network may think the attackers are legit, they may send their data, which attackers use for more attacks (Lamba, 2020). Organizations should protect their systems against attackers by switching on their spam filters. System protection prevents spoofed emails from appearing in their inboxes and examining their communication to detect spoof attacks through observing unusual sentence structures and poor grammar (Gourisetti et al., 2020). Organizations should also confirm the senders of the messages, invest in cyber-security software, and set up two-step verification to reduce spoofing attacks.
Step 2: Risk Register
Step 3: The Laws and Regulatory Guidance Which Apply To Financial Services Industries and Companies
Law and regulatory guidance which apply to Financial Services Industries and Companies refer to the regulations and laws that govern insolvency, operation, and creation of financial industries. These industries include; security settlement, payment, trading, investment, insurance, broker-dealers, and banks (Rosella et al., 2019). The regulations and laws that govern the industries are statutory (legislation, commodities, securities, and banking laws. Companies design these laws to enhance the soundness and safety of financial companies, consumers, investors, and fiscal stability. Law and regulatory guidance differ from one organization to another. The government restricts some law institutions from issuing financial regulatory guidance to specific financial industries, such as insurance companies and banks (Rosella et al., 2019). Other law firms emphasize bank acquisitions and mergers. Only a few financial firms practice legislative advice and financial regulations, investments, and mergers when the government targets financial institutions, capital market transactions among financial institutions, and enforcement when the perpetrator is a financial firm. Financial regulations and laws also protect organizations from financial fraud.
Statutory (legislation) Laws
Governing bodies enact these and pass them within a financial institution. Organizations use these laws to restrict, declare, sanction, outlaw, authorize, regulate, or provide funds.
Commodities’ Laws
These laws regulate futures trading and all commodity activities and need organizations to exchange commodity options and futures in an organized way. These laws promote transparency, efficiency, and competitive financial markets that protect clients from malicious and fraudulent practices.
Securities Laws
Security laws enable investors to acquire financial and important information offered for securities. Securities laws are essential for financial industries because they provide transparency, allowing the investors to get consistent and accurate information about company profitability. They aim at protecting investors by maintaining efficient, orderly, and fair markets. They also facilitate the formation of capital within the financial industry.
Banking Laws
Banking Laws cover the regulation, liquidation, examination, and operation of financial banks. They discuss the legal necessities that govern structural changes, such as mergers and acquisitions, branching, divestiture expansion, and company information. They also examine the activities of financial banks, such as negotiation and transfer of notes and checks, electronic banking, credit cards, investment, and loans. In addition, banking laws discuss the assessment of financial industries by the regulatory agencies of federal banks. They also examine the influence of national securities and federal income laws.
Step 4: Laws and Regulations Which Apply To All Companies
Sarbanes-Oxley Act
The government implemented the Sarbanes Oxley act due to the unexpected and stunning bankruptcy in 2001. This law deals with the reform of accounting and auditing procedures such as internal controls, and oversight responsibilities of officers and corporate directors. It also deals with conflicts of interest, extraordinary bonuses and compensation disclosure, and insider dealings (Gupta et al., 2018). It also deals with stock analysis, completes an earlier disclosure of activities that impact financial results, and violates disclosure rules (Gorshunov et al., 2020). Additionally, this law requires certification of financial results by the chief executive and the signing of federal income tax files.
SEC Disclosure Obligations
SEC regulations involve publicly owned companies disclosing particular financial and business data categories to the organization’s stockholders and SEC. SEC also necessitates disclosing appropriate financial and business information to reliable investors when novel securities, including bonds and stocks, are issued to citizens (Rosella et al., 2019). However, organizations exempt private placements and minor issues from the disclosure. This regulation also requires publicly owned companies to prepare two yearly reports for the shareholders and the SEC. On top of that, SEC regulations need annual reports to have specific items and verified financial statements.
Generally Accepted Accounting Principles (GAAP)
Generally accepted accounting principles refer to accounting rules that require companies to disclose their audited financial statements. Once companies adopt these rules, they get followed and acknowledged by individuals (King, 2019). Organizations must disclose important information for auditing purposes. Pension details, lease information, mitigation, accounting policies, and financial records are among the information companies have to disclose
IRS Regulations for Business Records
This regulation requires businesses to keep their records until they make income deductions on tax returns, implying that companies must maintain their tax records. These records help businesses monitor their progress, gather financial statements, recognize their income sources, track deductible expenses, track properties, prepare tax returns, and support assets reported on a company’s tax returns (Hodge, 2016). Businesses may choose record-keeping systems that favor their businesses and show their expenses and income clearly. In some circumstances, this regulation does not need particular records from firms. However, enterprises impact the category of records they may require for federal tax commitments. Businesses generate supporting transaction documents such as payrolls, sales, and purchases. The supporting documents of businesses contain crucial information that companies must record in books. Most importantly, this regulation requires businesses to keep their employment tax records for approximately four years.
Reporting Requirements
Reporting requirements are the applicable regulations, rules, laws, directives, instruments, and regulatory requirements that mandate reporting of business transactions. Reports are required to provide crucial details that may improve decision-making, planning, and development of future forecasts. Businesses also use accounts to identify irregularities, and growth and track their progress. In addition, reporting requirements refer to data and information supplied by companies to government agencies. All insurance organizations play a significant role in adhering to reporting requirements. In addition, government agencies use reporting requirements to safeguard companies, policyholders, and investors, who depend on reporting requirements to obtain insurance coverage. Companies that fail to comply with reporting requirements face penalties and punishment.
Step 5: Risk Management and the Cybersecurity Framework in the NIST Cybersecurity Framework
National Institute of Standards and Technology (NIST) aims at supporting and facilitating the advancement of cybersecurity risk structures. NIST must recognize cost-effective, performance-based, repeatable, flexible, and prioritized approaches such as information measures and security control that operators and owners of vital infrastructure may implement to assist in identifying, assessing, and managing cyber risks (Almuhammadi & Alsaleh, 2017). NIST framework is applicable in the Padgett-Beagle Solutions in recognizing the essence of privacy in creating public privacy and protecting civil liberties and individual privacy when conducting its cybersecurity activities. The framework will be adequate to Padgett-Beale because it references different practices, guidelines, and standards within the organization. In addition, the framework will help Padgett-Beale to describe its current cybersecurity postures, target cybersecurity state, opportunities, progress, and communicate with external and internal stakeholders about cybersecurity risks.
The framework will manage PBI-FS cybersecurity risks using three parts; framework profile, implementation tiers, and the framework core to strengthen the association between cybersecurity activities and mission/business drivers. The framework core refers to cybersecurity activities, applicable references, and desired outcomes that are mutual across acute infrastructure sections (Almuhammadi & Alsaleh, 2017). The framework will provide the PBI-FS with practices, guidelines, and standards to permit cybersecurity communication across the company from the executive to the implementation level. The National Institute of Standards and Technology (NIST) framework identifies, protects, detects, responds, and recovers cybersecurity issues. If Padgett Beale implements these functions well into PBI-FS, the company will easily manage its cybersecurity risks (Almuhammadi & Alsaleh, 2017). Identifying involves understanding cybersecurity risks to manage an organization’s capabilities, data, assets, people, and systems; protecting consists of developing and implementing appropriate securities to ensure the distribution of essential services.
Detecting involves developing and implementing appropriate activities to recognize cybersecurity risks and developing and implementing proper operations to detect cybersecurity issues. Similarly, recovering consists of implementing and developing the activities that retain an organization’s resilience plans and restoring impaired capabilities due to cybersecurity incidents. The framework tiers give organizations a clue on how they view and manage cybersecurity risks. They describe the extent to which cybersecurity risks have altered with an organization’s practices.
The risk management process will enable Padgett-Beale to manage its risks appropriately because it will help the company detect the likelihood of cybersecurity risk. With this information, PBI-FS will recognize the possibility of risks occurring and the potential impacts the risks will pose to the organization (Almuhammadi & Alsaleh, 2017). Comprehension of risk tolerance helps companies prioritize their cybersecurity activities to make better expenditures, implement programs that manage risks, and communicate and quantify cybersecurity programs adjustments. PBI-FS may also implement the following risk mitigation strategies depending on the impacts of the dangers on the critical services of the organization:
- Accepting the risk- Padgett-Beale may take risks if it acknowledges that the potential impacts of the risks are not many to the extent of the organization incurring more money to eliminate the risks.
- Mitigating the risk- Padgett-Beale may take actions that reduce its exposure to cybersecurity risks and decreasing the probability of the risks occurring again in the future. The organization can mitigate the risks by identifying the risks, analyzing the risks, and mitigating the risks.
- Risk transfer- involves transferring risks from one individual to another or from one company to another. Padgett-Beale may share its risks by purchasing insurance to share the risks to a third party.
- Avoiding the risk- Risk avoidance includes eliminating exposures, activities, and hazards that negatively affect a company’s assets. While risk management looks forward to controlling financial consequences or damages that threaten an organization, risk avoidance aims at avoiding events that compromise a company.
Risk management processes will enable PBI-FS to prioritize and inform decisions about cybersecurity. It funds recurring business validations and risk assessments to allow firms to select objected cybersecurity activities that contribute to desired outcomes. Therefore, the National Institute of Standards and Technology (NIST) cybersecurity framework will enable Padgett-Beale to direct and select improvements in the management of cybersecurity risks for ICS and IT surroundings (Almuhammadi & Alsaleh, 2017). The framework will give the organization a shared language for expressing, managing, and understanding threats to external and internal shareholders. The framework can also prioritize and identify actions that reduce cybersecurity risks and align policies, technological, and business approaches that manage risks. In addition, the organization can use the framework to manage cybersecurity risks to deliver critical services.
PBI-FS can also protect its data from data breaches and phishing by using multifactor authentication. Data protection is an authentication technique used to confirm devices, users, or applications by presenting various identifiers. Multifactor authentication will provide PBI-FS additional security layer by requesting users to deliver more than one verification factor to access their accounts, decreasing cyberattacks or the likelihood of data breaches or phishing attacks (Byun et al., 2019). Multifactor authentication gives organizations a strong identity and access management policy (IAM). It is the most reliable security control strategy. In addition, PBI-FS should protect its online accounts by making long and strong passwords, securing its local systems, and visiting websites with SSL certificates.
Using password managers, avoiding storing their passwords on computers, and using programs that support multifactor authentication will also significantly protect PBI-FS’s online accounts. PBI-FS should keep its systems and software updated to prevent hackers from accessing their networks. Installing firewalls can also benefit PBI-FS by defending it from cyberattacks (Byun et al., 2019). Firewall systems block any suspected attacks before they damage a system. Firewalls monitor network traffic; data coming in and out of an organization’s systems develop opportunities for risks to compromise activities (Marinova-Boncheva, 2007). By analyzing and monitoring network circulation, firewalls influence pre-established filters and rules to protect an organization’s systems. Firewalls can monitor the entry points of a system and stop virus attacks. In addition, firewalls will help organizations prevent hackers, eliminate spyware, and promote privacy.
Step 6: Cybersecurity Strategy Padgett-Beale should take to implement the recommended risk mitigation strategies
Among the cybersecurity strategies Padgett Beale should implement, the risk mitigation strategies include developing assurance frameworks and creating secure cyber systems. The first strategy Padgett Beale should implement is creating specific cyber ecosystems, including broad devices such as computers, technologies, and communication. This strategy will enable Padgett Beale to have a robust ecosystem where devices can work together to eliminate cyber-attacks. The plan will also allow Padgett Beale to allow secure means of organized actions within its devices. Vital cyber ecosystems have authentication interoperability and automation (Goel et al., 2019). Automation will ease the implementation of Padgett Beale’s advanced security strategies, enhance their swiftness, and optimize their decision-making procedures. Interoperability will toughen the collaborative activities of Padgett Beale, improve their awareness, and accelerate learning processes. Authentication will improve Padgett Beale’s verification and identification technologies that provide scalability, interoperability, ease of usage, affordability, and security.
The second strategy Padgett Beale should implement is creating assurance frameworks that will help develop an outline that complies with security strategies via technology, people, processes, and products. Padgett Beale should adopt the NIST framework to implement this strategy, accommodating critical infrastructure through endorsing and enabling actions (Almuhammadi & Alsaleh, 2017). Also, the assurance frameworks will help Padgett Beale to maintain a resilient, vigilant, and secure environment and identify particular characteristics and domains that interfere with Padgett Beale’s processes. The third strategy that Padgett Beale should implement is motivating open standards. Open standards will play a significant role in defining Padgett Beale’s cybersecurity issues by enhancing the effectiveness of their many processes, enabling the incorporation of their system, organizing new approaches, and interpreting complex surroundings. Implementing ISO 27001 will motivate Padgett Beale’s implementation of standard structures where clients will understand Padgett Beale’s processes and minimize auditing costs.
The fourth strategy PBI-FS should implement installing a Demilitarized User Zone (DMZ). DMZ is a subnetwork between private and public websites (Rababah et al., 2018). It exposes exterior-facing amenities to suspicious networks and supplements an additional security layer to safeguard sensitive data in internal systems using firewalls to clean data circulation. A demilitarized zone (DMZ) will protect the PBI-FS’s interior LAN (Local Area Network) from untrusted traffic (Iskandar et al., 2019). DMZ will allow PBI-FS to access suspicious networks (the internet) while ensuring the safety of its private network (LAN) (Rababah et al., 2018). DMZ will restrict other servers from accessing the LAN, making it hard for hackers to access an organization’s internal servers and information through the internet. The DMZ will enable PBI-FS to implement network segmentation, making it hard for unauthorized users to access the private network (Rababah et al., 2018). It will also allow the company to prevent network reconnaissance by issuing a buffer in the middle of the private network and the internet, preventing hackers from engaging in network reconnaissance. Lastly, the DMZ will block spoofing threats by discovering such attempts and eliminating them from the system.
The fifth strategy Padgett Beale should implement is the Barracuda CloudGen Firewalls which will protect its online accounts. These firewalls will generate a buffer between an external network and an organization’s IT systems by controlling traffic and blocking activities that may damage networks, techniques, and computers. Controlling traffic will eliminate the mentioned gaps from interfering with the company’s networks and blocking outgoing circulation instigating from a Trojan horse. Additionally, implementing the Barracuda firewalls will separate Padgett Beale’s workstation devices from threats, allowing the company to choose the data of the port received or sent manually (Byun et al., 2019). Implementing the Barracuda firewalls will also reduce the risks associated with data loss via the firewalls that safeguard the firm from external threats. The firewalls will also protect Padgett Beale’s applications, users, and data against malicious attacks. It will also eliminate unauthorized access to the company’s data by monitoring traffic entering its system. Hence, the Barracuda firewalls will ensure Padgett Beale’s system is also secured from theft, and hackers and will enhance the assessment of threats.
The sixth strategy PBI-FS should implement installing the antivirus software will root for possible viruses that may interfere with the organization’s software. Remarkably, the antivirus will protect Padgett Beale’s systems against spyware, adware, worms, Trojan horses, key loggers, ransomware, and malware. The software will also scan PBI-FS’s network or computers to look for malicious programs in the database and eliminate them (Marinova-Boncheva, 2007). Advanced software has a high chance of accommodating more extensive databases and detecting problems. Even though many cyber threats are computerized, with attackers exploiting and looking for known vulnerabilities, the software will enable PBI-FS to scan its data to recognize its weaknesses. Vulnerability scanning will also allow the organization to determine the general efficiency of its security measures to save money and time afterward.
The seventh strategy Padgett Beale should take is executing the IBM Guardian to encrypt data. Encrypting data will help the organization prevent attackers from viewing important files, mitigate the risks associated with data breaches, and control General Data Protection Regulation (GDPR) violations. In addition, data encryption will help Padgett Beale to protect its sensitive data and private information by facilitating security between client applications and servers (Brewer, 2016). Encrypting data will prevent hackers from reading Padgett Beale’s sensitive or confidential information. On top of that, encrypting Padgett Beale’s data will enable the company to easily detect malicious users to protect the company’s integrity and confidentiality. This strategy will also address the gaps relating to unauthorized access and hackers.
Implementation Schedule
Enterprise IT Architecture for PBI-FS
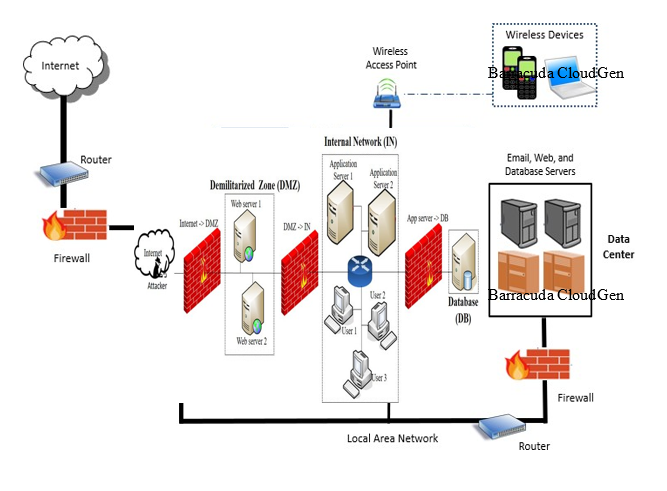
Step 7: Plan of Action and Implementation Timeline
Step 8: Summary of Recommendations
For the successful merging and acquisition of Island Banking Services to create PBI-FS, Padgett-Beale should first analyze the gaps that contributed to the bankruptcy of the Island Banking Services and adopt appropriate strategies that will mitigate the risks and prevent them from reoccurring. Padgett-Beale should follow statutory laws, commodities laws, and security laws that guide all financial companies when implementing their activities. Statutory regulations will enable the organization to restrict its data. Commodity laws will promote transparency within the organization and security laws will facilitate proper circulation of information, and banking laws will examine the institution’s operations.
PBI-FS should also follow the rules and regulations that guide all companies, including; Sarbanes-Oxley Act, SEC Disclosure Obligations, Generally Accepted Accounting Principles (GAAP), IRS Regulations for Business Records, and Reporting Requirements. These regulations will enable the organization to know the activities it should engage in for its well-being. PBI-FS should manage its risks by employing risk mitigation strategies and multifactor authentication to eliminate unauthorized access. Padgett-Beale should install Barracuda CloudGen Firewalls, and antivirus software, Encrypt sensitive data, and Conduct vulnerability scans to implement the recommended risk mitigation strategies. It should also conduct a cybersecurity risk assessment, install a Demilitarized User Zone (DMZ), and install Intrusion detection software to eliminate intruders from the system. Lastly, Padgett-Beale should implement a plan of action that includes the resources, time, effort, and costs required to mitigate the risks and contribute to the smooth running of BPI-FS.
Conclusion
Gap analysis is essential to every organization because it facilitates easier recognition of risks. Companies should follow the standards and rules that guide businesses to ensure that they are not against the standards that drive industries. Risk management strategies also play a vital role to businesses because it helps companies to mitigate the risks that alter companies’ operations. Adhering to the measures that eliminate risks will help organizations eliminate threats and run business operations smoothly.
Memorandum
- To: Merger & Acquisition Team
- From:
- Date 13th July 2021
- Subject: Recommendation for mitigating the identified risks.
The primary purpose of this recommendation is to address the proper strategies that Padgett-Beale should implement on its acquisition with Island Banking Services to mitigate risks. Various risks interfered with Island Banking Services’ hardware, software, and files, bankrupting the organization. Some of the dangers that attacked Island Banking Services include; Ransomware attacks, IoT attacks, cloud attacks, phishing attacks, DoS, software vulnerabilities, outdated software, unencrypted data, manipulated data, and spoofing. These recommendations will facilitate PBI-FS’s security and ensure attackers will not alter its data files.
The Cybersecurity Strategy and Plan of Action consisted of Gap Analysis, Legal & Regulatory Requirements Analysis, Risk Analysis & Risk Register, Cybersecurity Strategy, and Plan of Action and Implementation Timeline. Gap analysis analyzed the risks that attacked the organization. The study of legal and regulatory requirements highlighted statutory laws, commodities laws, and security laws that guide all financial companies when implementing their activities. Additionally, it analyzed the rules and regulations that guide all companies, including; Sarbanes-Oxley Act, SEC Disclosure Obligations, Generally Accepted Accounting Principles (GAAP), IRS Regulations for Business Records, and Reporting Requirements. Risk analysis and risk register provided the risk mitigation strategies that the new company should adopt. The plan of action provided the resources, time, effort, and costs required to mitigate the risks and contribute to the smooth running of BPI-FS.
I recommend the Merger & Acquisition team follow statutory laws, commodities laws, and security laws that guide all financial companies when implementing their activities. It should also follow the rules and regulations that guide all companies, including; Sarbanes-Oxley Act, SEC Disclosure Obligations, Generally Accepted Accounting Principles (GAAP), IRS Regulations for Business Records, and Reporting Requirements. The team should manage its risks by employing risk mitigation strategies to eliminate unauthorized access. It should also install intrusion software that will detect any attackers planning to attack their system.
Thank you for your cooperation.
- Signature:
- Name:
References
Almuhammadi, S., & Alsaleh, M. (2017). Information security maturity model for NIST cybersecurity framework. Computer Science & Information Technology (CS & IT), 7(3), 51-62. doi:10.5121/csit.2017.70305
Brewer, R. (2016). Ransomware attacks: detection, prevention, and cure. Network Security, 2016(9), 5-9. doi: 10.1016/s1353-4858(16)30086-1
Byun, M., Lee, Y., & Choi, J. Y. (2019). Risk and avoidance strategy for blocking mechanism of SDN-based security service. In 2019 21st International Conference on Advanced Communication Technology (ICACT) (pp. 187-190). IEEE. doi:10.23919/icact.2019.8701887
Crumpler, W., & Lewis, J. A. (2019). The cybersecurity workforce gap. Center for Strategic and International Studies (CSIS).
Goel, A. K., Rose, A., Gaur, J., & Bhushan, B. (2019). Attacks, countermeasures, and security paradigms in IoT. In 2019 2nd international conference on intelligent computing, instrumentation, and control technologies (ICICICT) (Vol. 1, pp. 875-880). IEEE. doi:10.1109/icicict46008.2019.8993338
Gorshunov, M. A., Armenakis, A. A., Feild, H. S., & Vansant, B. (2020). The Sarbanes-Oxley Act of 2002: relationship to the magnitude of financial corruption and corrupt organizational cultures. Journal of Management, 21(2), 73. doi:10.33423/jmpp.v21i2.2929
Gourisetti, S. N. G., Mylrea, M., & Patangia, H. (2020). Cybersecurity vulnerability mitigation framework through empirical paradigm: Enhanced prioritized gap analysis. Future Generation Computer Systems, 105, 410-431. doi:10.1016/j.future.2019.12.018
Gupta, P. P., Sami, H., & Zhou, H. (2018). Do companies with effective internal controls over financial reporting benefit from Sarbanes–Oxley Sections 302 and 404? Journal of Accounting, Auditing & Finance, 33(2), 200-227. doi:10.1177/0148558×16663091
Gupta, R., & Agarwal, S. P. (2017). A comparative study of cyber threats in emerging economies. Globus: An International Journal of Management & IT, 8(2), 24-28. doi: 10.18411/a-2017-023
Hodge, S. A. (2016). The compliance costs of IRS regulations. Tax Foundation.
Iskandar, A., Virma, E., & Ahmar, A. S. (2019). Implementing DMZ in improving network security of web testing in STMIK AKBA. arXiv preprint arXiv:1901.04081. doi:10.14419/ijet.v7i2.3.12627
King, A. F. (2019). The Convergence of International Financial Reporting Standards and Generally Accepted Accounting Principles. ASBBS Proceedings, 26, 302-302.
Lamba, A. (2020). A Through Analysis on Protecting Cyber Threats and Attacks on CPS Embedded Subsystems. Available at SSRN 3517474.doi: 10.2139/ssrn.3517474
Marinova-Boncheva, V. (2007). A short survey of intrusion detection systems. Problems of Engineering Cybernetics and Robotics, 58, 23-30. doi:10.1145/1330598.1330631
Rababah, B., Zhou, S., & Bader, M. (2018). Evaluation of the Performance of DMZ. Assoc. Mod. Educ. Comput. Sci, 0-13. doi:10.5815/ijwmt.2018.01.01
Rosella, M. R., Avdeychik, V., & Capozzi, J. R. (2019). SEC adopts rules and interpretive guidance designed to enhance and clarify the obligations of financial professionals. Journal of Investment Compliance. doi:10.1108/joic-08-2019-0049
Sapienza, A., Ernala, S. K., Bessi, A., Lerman, K., & Ferrara, E. (2018). Discover Mining online chatter for emerging cyber threats. In Companion Proceedings of the Web Conference 2018 (pp. 983-990). doi:10.1145/3184558.3191528
Singh, A., & Jain, A. (2018). Study of cyber-attacks on the cyber-physical system. In Proceedings of 3rd International Conference on Internet of Things and Connected Technologies (ICIoTCT) (pp. 26-27). doi:10.2139/ssrn.3170288
Tirumala, S. S., Valluri, M. R., & Babu, G. A. (2019). A survey on cybersecurity awareness concerns, practices, and conceptual measures. In 2019 International Conference on Computer Communication and Informatics (ICCCI) (pp. 1-6). IEEE. doi:10.1109/iccci.2019.8821951
Tsiknas, K., Taketzis, D., Demertzis, K., & Skianis, C. (2021). Cyber Threats to Industrial IoT: A Survey on Attacks and Countermeasures. IoT, 2(1), 163–186. doi:10.3390/iot2010009