Executive Summary
The White Paper is devoted to the description and analysis of threats and information security vulnerabilities in corporate systems. It is shown that a corporate information system is a complex structure in which various services necessary for the functioning of a company are combined. It is constantly changing – new elements appear, and the configuration of existing ones is modified. As the system grows, ensuring information security and protecting business-critical resources becomes an increasingly complex task that requires a preventive and proactive approach, as well as the analysis of risks to reduce them to an acceptable level. It is proposed to consider the security of corporate networks using penetration testing. This approach allows recreating the conditions in which violators usually operate, and quickly eliminating security flaws.
Introduction
The relevance of the topic of the following White Paper is determined by the aggravation of information security (IS) problems in the context of the intensive improvement of technologies and data protection tools. It is evidenced by the increase in information security violations and growing severity of their consequences. Thus, the total number of violations in the world annually raises by more than 100% (Davidoff, 2019). Statistics also show that if a commercial organization allows leaks of important inside information, then it goes bankrupt in 60% of cases (Fowler, 2016). Thus, some factors determine the need for a balanced approach to this problem.
These factors, first of all, include an ever-increasing number of information threats and risks, as well as an insufficient level of security of existing information systems (IS). These risks are realized through the vulnerabilities of modern IS that support various types of economic activities of enterprises. In this context, the White Paper is addressed to top management of enterprises in any field of activity, using corporate information systems in their work, as well as for heads of structural IT departments.
Previous Approaches
During analysis of the history, one can see a clear lag between defending and attacking sides. People in charge of security are reluctant to put themselves in position of a criminal, refusing to believe that one can qualify equal, or even superior to, their ones. Companies create their systems of information security and conduct audits and analyses of data security (Khan et al., 2019). The protection approaches often imply such organizational measures as creating positions for employees responsible for information security, drawing up regulations, rules and procedures for users, the implementation of a backup policy, and others.
Meanwhile, significant loss of profits from security breaches is the most common. Research shows that 29% of companies that experience data leaks end up losing profits (Davidoff, 2019). Of those who suffered losses, 38% experienced a 20% or more of it (Davidoff, 2019). At the same time, business viability threat, even greater than terrorism, is employee error or malice. The situation is aggravated by overly frivolous attitude of enterprises towards disaster recovery plans. Thus, 17% of IT managers do not have emergency recovery plan at all, 57% revise such a plan once a year or less, 6% never revise them, and 25% have never tested such plans (Davidoff, 2019). The impact of security breaches on the activities of IT services is shown in Figure 1 below.
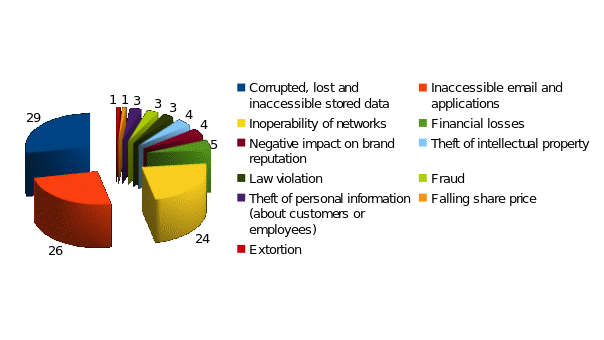
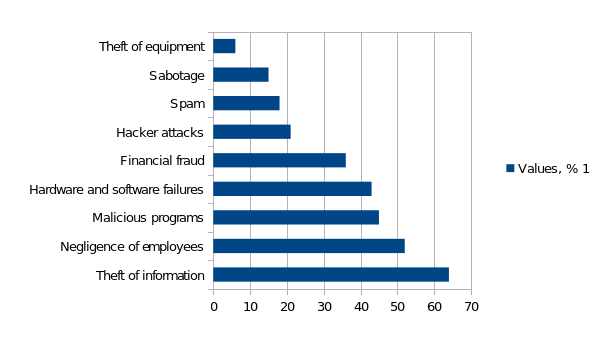
At the same time, unauthorized access is one of the most “popular” methods of computer offenses – that is, a person who makes it violates the rules that are fixed by the security policy. Having such access, they can benefit from security systems errors and can penetrate the information core. Incorrect settings and installations of protection methods also increase the possibility of the above-mentioned violation (Cheng et al., 2017). Access and threats to information security are made both by local methods and by special hardware installations. A fraudster can not only get into information and copy it, but also make changes, delete data. The most dangerous threats to information security are shown in Fig. 2.
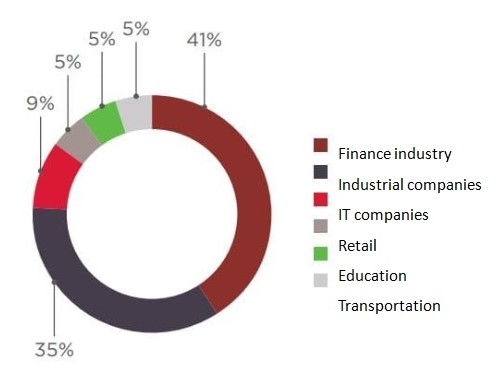
The distribution of hacker attacks by industry is shown in Fig. 3.
Since the process of ensuring information security is ongoing, the existing methodology for designing a safe system is an iterative process of eliminating the vulnerabilities, errors, and malfunctions found. The thesis was expressed and substantiated that guaranteed security in an automated system should be understood as guaranteed compliance with a priori specified security policy (Juma’h & Alnsour, 2020). Previously, such policy guarantees were formulated as standards, with no proof.
However, security requirements are often considered without taking into account the relationship with each other; they are formal and not structured. The mathematical model of the security policy considers the protection system in a certain stationary state, when the protective mechanisms are in effect, and the description of permitted or unauthorized actions does not change. The observance of a given set of qualitative indicators, on the one hand, does not allow quantitative assessment of each indicator, and, on the other hand, hinders a systematic approach.
New Findings
The planning of systems for the protection of economic information is impossible without the implementation of preventive measures. Effective information security provides not only protection against theft of any data from the enterprise network but also financial protection of the business as a whole. Enterprises that want to be distinguished by high-quality information security are constantly working to prevent the following events (Juma’h & Alnsour, 2020):
- Any corporate data leaks
- Remote editing of protected information
- Changes in the level of protection against threats that can provoke a loss of confidence among investors, suppliers, and counterparties.
Threats can have several sources, so it is very important to classify them in a timely manner and create a scheme for their analysis. Only three percent of web applications are reliable enough to resist hackers, and 97 percent of websites have “serious security flaws” (Davidoff, 2019, p. 54). Naturally, it can result in data and systems being compromised for malicious use. In 97% of discovered serious “holes,” almost 40% of applications allowed attackers to gain complete control and access to information. About 23% of defects could lead to privacy breaches, and 21% of errors found made it possible to “steal” goods from electronic stores; 5% of defects allowed attackers to change information, and another 5% allowed them to intercept transactions. Moreover, 2% of software bugs are so serious that attackers can delete websites (Davidoff, 2019). Therefore, it is important to remove all possible threats and create a scheme of their effective elimination.
At the same time, the best results are achieved under the condition of a systematic approach to the problems of ensuring information security of enterprises and the integrated use of protection measures at all stages of the life cycle of an information system, starting from the early stages of its design. An example of an integrated approach to protecting an information system is the Microsoft Forefront family of business security products for a network structure. One of the benefits of this family is the integration of the security system of the Microsoft Application Server and existing infrastructure.
It is impossible to reduce the magnitude of information system risks to zero. Therefore, actions to reduce risk should be primarily aimed not at completely removing a particular risk, but at choosing an effective method of managing it and reducing it to an acceptable level. An effective method of analysis is penetration testing, which simulates a real attack by cybercriminals (Khan et al., 2019). This approach allows to objectively assess the level of security of the corporate infrastructure and understand whether the security tools used in the company can resist attacks. At the same time, the purpose of testing is not to search for all the shortcomings of the system without exception, but to obtain an objective assessment of the level of its protection against attacks by intruders.
Conclusion
Not depending on the form of information storage and usage, there is the obvious need to introduce competent protection measures. Each leader should assess the state of corporate information systems at the current moment on the objective basis, reveal and comprehend the needs for information support and present information problems. Anti-unauthorized access measures should aim to achieve important goals – first of all, it is necessary to create conditions when accidental or deliberate actions leading to the loss of data become impossible. Information security solves this problem by creating a system for user authentication and authorization, separation of access rights to information and access control. It is also important to create a system in which employees or attackers would not be able to hide the committed actions. This is where the security event control system, audit of access to files and folders comes to help the information security specialist.
References
Cheng, L., Liu, F., & Yao, D. (2017). Enterprise data breach: Causes, challenges, prevention, and future directions: Enterprise data breach. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery.
Davidoff, S. (2019). Data breaches: Crisis and opportunity. Addison-Wesley Professional.
Fowler, K. (2016). Data breach preparation and response: Breaches are certain, impact is not. Syngress.
Juma’h, A., & Alnsour, Y. (2020). The effect of data breaches on company performance. International Journal of Accounting and Information Management, 28(2), Web.
Khan, F., Kim, J., Moore, R., & Mathiassen, L. (2019). Data breach risks and resolutions: A literature synthesis. Twenty-fifth Americas Conference on Information Systems, Cancun, 1-10.