The Fundamentals of a Public Key Infrastructure (PKI)
The PKI, as well as encryption, is used by all users and promotes the security of data transmission (Ballad, Ballad, & Banks, 2011). The PKI is a structure that helps to avoid the dangers that may appear in the process of asymmetrical algorithms’ practical implementation (Schmeh, 2003). For the best understanding of the PKI, it is necessary to analyze the core issues related to the employment of asymmetrical algorithms.
These issues are of four types: the authenticity of the key, revoking keys, non-repudiation, and policy enforcement (Schmeh, 2003). The first problem is concerned with the fact that it is not always easy to identify the owner of the key. The issue with revoking keys is that it is not possible to say whether a public key has been invalidated or not. The non-repudiation trouble is that it is rather difficult to prove the ownership of the key. Finally, there is a problem of policy enforcement.
This dilemma is associated with the need to implement additional measures if one wants to execute asymmetric algorithms (Schmeh, 2003). There are three trust models with the help of which it is possible to manage the problem of public key authenticity. The simplest trust model is direct trust, and it presupposes users’ confirmation of the authenticity of their public keys to other users. The second model is called a web of trust, and it incorporates the use of digital certificates, which makes the process of revocation more complicated. Thus, the web of trust model is more effective than direct trust (Schmeh, 2003). However, taking into consideration that the web of trust is not always practical, specialists created a hierarchical trust model. With its help, the local policy is pursued the fastest.
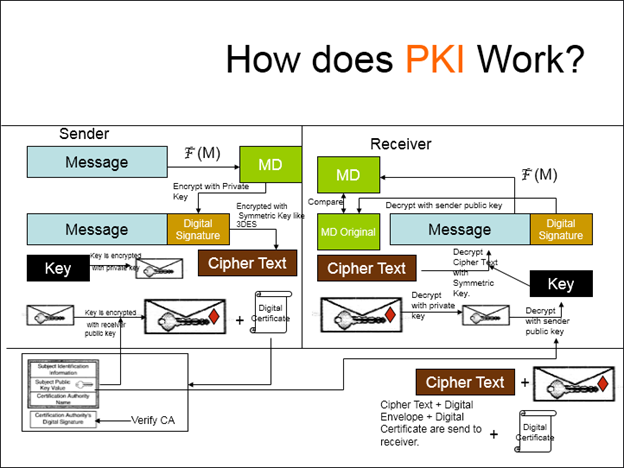
Figure 1 shows the structure of the PKI. The PKI is the totality of the elements necessary to apply the public key methods with the use of the hierarchical trust model (Schmeh, 2003). The most essential component of a PKI is a digital certificate. This certificate certifies the belonging of a certain public key to a certain user. Digital certificates, as well as PKIs, may be employed with a beneficial effect for “authentication with a challenge-response method” (Schmeh, 2003, p. 245). The process is contingent on whether the certificate will be exploited for a digital signature or a key exchange. Apart from the authentication with a digital signature, there are also options for mutual authentication and the authentication by exchanging keys.
The hierarchical trust model presupposes several variants of PKIs: a two-level hierarchy, a web model, cross-certification, and certification authority (CA) hierarchies (Schmeh, 2003). Due to users’ need to communicate not only between themselves but also with the CA, there is a number of standards within the PKI. One of the oldest and most significant standards is X.509 that is an element of the X.500. X.509 consists of three parts: the protocols for authentication with a trusted third party, the protocols of authentication without a trusted third party, and the description of configurations for digital certificates confirmed by the CAS (Schmeh, 2003). Other important PKI standards are PKIX, ISIS, and the German signature law, Identrus, and SPKI.
The PKI with one CA has the following components: the CA, the registration authority, the certificate server, and the time-stamping service. The decentralized elements of the PKI are the local registration authority, the revocation authority, the recovery authority, the end entity, and the personal security environment (Schmeh, 2003).
Privacy Protection of Data Transmitted Across the WAN
A wide area network (WAN) is one of the most significant domains that cover a large area (Johnson, 2015). An example of WAN is the Internet. It is possible to create a private WAN for a particular organization in order to connect offices across one country or even all over the world. Many companies employ the Internet to connect departments in various regions. Since the Internet has become affordable and reliable, it is often the first choice of organizations. The communication through WAN is secured with the help of encryption.
Another domain that is closely associated with WAN is the local area network (LAN). This infrastructure creates a connection between two or more computers within a limited area (Johnson, 2015). Agreement in the LAN-to-WAN domain relies upon the security of the most effective control measures (Weiss & Solomon, 2016). LAN-to-WAN domain includes the technical functions allowing the company to arrange a connection between LAN and WAN.
One of the best ways of securing privacy protection of data transmitted across the WAN is by controlling the traffic flowing across the LAN-to-WAN (Weiss & Solomon, 2016). This task is time- and energy-consuming, but it guarantees the best security opportunities. Another approach is a demand that all configuration changes should pass the procedure of change-management. This process may seem “intrusive,” but it provides an opportunity to control all of the authorized changes and use only the ones that have been approved (Weiss & Solomon, 2016, p. 246). Therefore, a PKI will be helpful in securing the privacy of the company’s LAN-to-WAN domain.
Application of Patch Management
The operating system presupposes the application of patch management (PM) in order to arrange the work at the best level. PM is a process incorporating the acquisition, checking, and the implementation of patches to the administered systems. Prior to introducing PM, the organization needs to ensure that it has the following options at its disposal:
- efficient operations and employees that realize their functions and roles;
- tools and methods suitable for the effective PM;
- strong project management processes (Trent, 2006).
There are several prerequisites for the successful PM process: the awareness of the organization’s computer environment, the arrangement of end-user education, the appointment of responsibilities, the comprehension of the ongoing processes, the creation of a communication chain, the baseline, and the acquisition of management buy-off.
The process of PM consists of four elements: the assessment, the identification, the evaluation and planning, and the deployment (Trent, 2006). The PM process starts with the evaluation of the company’s production environment and the analysis of its challenges and threats. Thus, the assessment phase involves inventory and baselining. The identification phase allows discovering the available software updates in a safe way. The evaluation and planning phase presupposes making decisions regarding the introduction of updates and testing them. The deployment phase includes three stages: preparation, patch deployment to targeted computers, and post-implementation analysis (Trent, 2006).
An effective solution would be to perform the analysis of the current production environment at the company and identify the need for PM. Upon the investigation, it is recommended to apply PM to the computers that require patches.
References
Ballad, B., Ballad, T., & Banks, E. K. (2011). Access control, authentication, and public key infrastructure. Sudbury, MA: Jones & Bartlett Learning.
Johnson, R. (2015). Security policies and implementation issues (2nd ed.). Burlington, MA: Jones & Bartlett Learning.
The rules of a public key infrastructure. (2017). InfoSec Institute. Web.
Schmeh, K. (2003). Cryptography and public key infrastructure on the internet. West Sussex, UK: John Wiley and Sons.
Trent, R. (2006). Patch management best practices. In R. Trent (Ed.), The administrator shortcut guide to patch management (pp. 20-38). Web.
Weiss, M. M., & Solomon, M. G. (2016). Auditing IT infrastructures for compliance (2nd ed.). Burlington, MA: Jones & Bartlett Learning.