Abstract
This research shows elements of wireless intrusion detection and intrusion prevention. It shows the main areas of wireless intrusion and detection together with advantages and challenges of using a wireless intrusion and detection systems. Overall, the research concludes that a wireless IDS offers many advantages than challenges it may present to users.
Wireless local area networks (WLANs) have many threats, which could have significant impacts on the network. Threats to WLAN technologies include “wrongly configured wireless access points (WAPs), Denial of Services (DoS) and possible system hijacking” (Max, 2009, p. 3).
Wireless networks are also prone to common attacks like TCP/IP and 802.11 threats. TCP/IP threats also are common in networked technologies. WLANs must incorporate security techniques that can detect and defend against potential threats. These are intrusion detection system (IDS) solutions.
Introduction
WLANs have the same IDS as a Network Intrusion Detection System (NIDS) because they can also evaluate network traffic for potential security threats. However, IDS can evaluate specific areas, which only relate to WLAN. These include WAPs, rogue WAPs, and offsite users. The growth in wireless technologies has allowed networks to support wireless devices at different sections of the network typology.
This suggests that WLAN IDS have critical roles to play in network securities. WLANs may have unconnected wireless sensors to analyze traffic. The physical location of a sensor is critical for effective analysis of network traffic. The location normally influences what a network sensor can detect and monitor. Network sensors should have the ability to monitor all gadgets that can gain access to the network.
Some wireless networks may have more than a single sensor. These sensors go beyond the normal scope of network operations. In most cases, the WLAN may have a single channel, but it also has options of running on several channels. Thus, WLAN sensor may effectively serve a single channel. However, regular changes can ensure that WLAN sensors can analyze several channels.
IDS has many parts, such as consoles, databases, and system sensors. Users can run the system on either a centralized or decentralized platform.
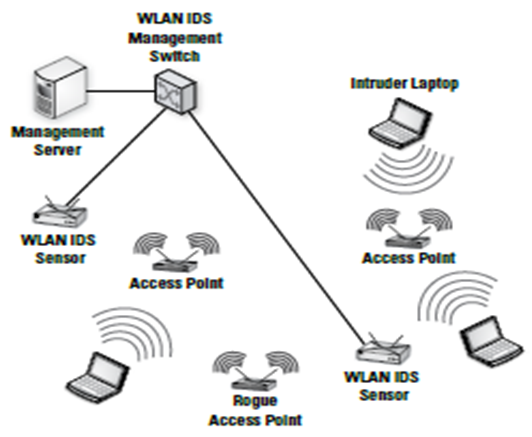
Figure 1: WLAN IDS
Wireless Threats
Wireless local area networks are susceptible to a number of threats. The normal 802.11 encryption has become susceptible to attacks (Max, 2009, p. 7). In addition, the Wired Equivalent Privacy (WEP) may not withstand constant brute force attacks. In other words, encryption alone cannot protect the network because the intruder can still attack and decrypt sensitive information in wireless networks.
Attackers also rely on rogue WAP to attack WLANs and gain access to sensitive information in the system (Vladimirov, Gavrilenko & Mikhailovsky, 2004, p. 435). Attackers normally construct rogue WAPs in a similar manner as real WAPs. Most users have the tendency of connecting to any WAP with appropriate signals. At this point, users can accidentally connect to a rogue WAP.
This provides an opportunity for the attacker to monitor all forms data transmission across the connected devices. At the same time, some users may also “introduce rogue WAPs in the wireless network” (Low, 2005, p. 89). This happens because of low costs and ease of connectivity in the WLAN systems. Users can install other access points in the network and render other security features ineffective.
This makes the network an easy target for attackers (Low, 2005, p. 89). Users must consider the deployment of a wireless IDS security solution to protect the network from such vulnerabilities. IDS solutions can protect the network from installed rogue WAPs.
DoS may also affect networks that rely on 802.11. Hackers can derail such networks. Physical objects may also affect communication systems across wireless networks. These may include tall buildings, trees, and even rain. Other physical objects that have signal systems may also affect 802.11 networks. There are attackers who use fake requests to congest the system in order to force the system reboot.
At the same time, such attackers can also make repeated requests as a way of denying services to authentic users. Other security threats include poorly secured network devices, man in the middle, and unauthorized systems on the network. WLAN IDS sensors should have the ability to detect these threats (Kent & Mell, 2006, p. 87).
There are other forms of WLAN threats, including new ones. These threats have critical repercussions on networks they attack. WLAN that lacks any form of threat intrusion detection and prevention may find it difficult to notice threats on the network. A lack of awareness about threats creates vulnerable networks for attackers. Thus, organizations should have effective ways of detecting and preventing intrusion in the network.
Intrusion detection
Intrusion detection systems (IDSs) have the ability to recognize any unusual usages and access on the network (Base & Mell, 2001, p. 78). They can analyze data in the system and detect any anomalies (Caswell, Beale and Baker, 2007, p. 411). IDSs have the capacity to recognize intrusions and abnormal usages in the network system.
The new IDSs for wireless devices can sense, monitor, collect, and analyze data in order to locate known attacks, reveal abnormal network usages, and show misuse within the network (Yang, Xie & Sun, 2004, pp. 553-556). IDSs collect information and generate corresponding alerts based on the type of intrusion detected. A wireless IDS may be the same as networked IDS. However, WLAN IDS has specific security features for wireless networks only.
WLAN intrusion detection
Organizations can develop their own wireless IDSs or obtain them from vendors. While wireless IDS technologies are new, the available ones are effective security solutions. Moreover, they also have extensive security features. The most common IDS solutions include RogueWatch, Airdefense, and Airdefense Guard (Kent & Warnock, 2004, p. 8). There are also Internet Security Systems and other system scanners. Users can develop their own wireless IDS by using free software from Open Source.
Configuration
There two types of a wireless IDS configuration. These are centralized and decentralized configurations. A centralized wireless IDS uses several independent sensors on the network to gather information. The sensors collect information and transfer them to a central place for analysis and storage. On the other hand, a decentralized intrusion system has different gadgets for data collection, analysis, and reporting.
This type of intrusion detection is appropriate for small networks because it is expensive to run and maintain (Rhodes-Ousley, Bragg and Strassberg, 2003, p. 263). Moreover, decentralized systems may require much time from the organization.
WLANs may cover a large area. This could weaken the signal strengths. Therefore, it is appropriate to install several WAP to provide extra strength for the network. However, one should deploy a sensor in every access point with WAP. Several sensors in every access point can easily detect intrusion in the network. Moreover, the sensor can identify sources of threats within a given geography.
Physical Location
The wireless detection systems should be able to locate physical locations of attackers. Most hackers attack the network in locations close access points and WAPs in order to reduce the time for attack. Organizations should deploy people physically to respond to attacks in a timely manner. Attacks on networked systems could occur several miles away.
However, in a wireless system, the attacker could even be in the same location. Effective wireless IDS can assist in providing a physical location in which the hacker could be located. Information obtained from the 802.11 and the location of the WAP can “aid in quick detection of the attacker’s actual location” (Calabrese, 2003, p. 29).
In some cases, directional antennae aid in tracking the location of the attacker by tracing the source of the attacker’s signals. The IDS and other scanning systems are effective for this role. The physical response team can rely on these other teams to intercept the attacker.
Policy enforcement
Organizations can “use wireless IDSs to enforce their policies” (Calabrese, 2003, p. 32). WLANs may have many security challenges. However, there are solutions for these issues. Effective organizational policy can ensure that wireless networks remain secure. Enforcing organizational policies on wireless devices is an effective way of ensuring wireless network security.
Organizations should ensure that all its data are encrypted before transfers (Calabrese, 2003, p. 34). The wireless IDS can analyze the system and detect any attempts to transfers data without encryption. Effective configuration of WAPs can ensure that IDSs have the ability to easily identify rogue WAPs as soon as they attempt to gain access to the network.
Detection of a rogue WAP and enforcement of organizational policies on wireless communications can enhance the level of wireless network security. Policies on automated systems can eliminate the use of human to monitor possible rogue WAPs on the network. This can enhance effective use of resources in an organization.
Detecting threats
A wireless IDS is effective in identification of threats in the network. It can help in identifying rogue WAPs and any non-encrypted data during transfer in 802.11. Moreover, wireless IDSs can also detect attackers’ location and monitor the system for known attacks. Hackers rely on scanning devices and software as tools for detecting possible points of attack on the network.
Scanning tools like Kismet have been effective in identifying weak areas within the network. Attackers target such points on the WAP and apply GPS (Global Positioning System) to locate the most vulnerable geographical spot on the network. Scanning software and other detection tools are common, and organizations can use wireless IDS to identify such software on the network.
This can help in reducing vulnerability of the network from external analysis by hackers (Hsieh, Lo, Lee and Huang, 2004, pp. 581-586). Reliable wireless IDS can detect some DoS threats on the network (Trost, 2010, p. 53). DoS attacks are the most common attacks on wireless networks. Physical objects may cause conflicts in frequencies. Attackers may exploit such opportunities to deny users services from the network.
A wireless IDS has the ability to detect these forms of attacks, which aim to flood the network with requests or generate unauthorized requests. There are also other threats that a wireless IDS can detect on the network. For instance, many attackers may masquerade as authentic wireless device or a client. In such cases, a wireless IDS can detect threats from MAC address spoofing.
A wireless IDS uses a series analysis to “detect the presence of MAC address spoofing on the network” (Trost, 2010, p. 76). It can only detect ad-hoc networks. This is a configuration issue, which provide opportunities for attackers to use wireless devices and gain access to the network. A wireless IDS can also identify some uncommon or new forms threats by using users defined requirements.
In this context, it provides flexibility that other general IDSs may not have. Hence, users can use wireless IDSs to define their security features for locating unique threats. It is an effective method of building strong security features for WLAN. People who may know that the network relies on IDS features may not be interested in attacking the system. This is a way of deterring threats on the network.
Wireless IDS issues
Clearly, wireless IDS offers numerous advantages to users in detecting and preventing threats to the network. However, organizations should consider some aspects of wireless IDS, which may affect the effectiveness of their systems. Wireless intrusion detection is a field that is still evolving. Thus, it is important for users to be careful when deploying new systems with no proven track records on their networks.
New technologies may present new challenges or bugs to the network. Such challenges could be new forms of vulnerabilities, which would render the network unsafe and prone to attacks. One must also recognize that wireless technologies have evolved rapidly in the recent past. Hence, organizations may find it difficult and costly to keep pace with new discoveries in technologies.
Maintaining a wireless security system could be expensive, especially when they come from vendors. Organizations have opportunities of developing their own IDS solutions. However, this could present new challenges like qualified human capital and additional resources for such projects.
Costs of monitoring wireless IDS solutions normally increase as the size of the network also increases. A large network may require several sensors or other monitoring devices, which increase costs of developing and maintaining a wireless IDS solution.
Effectiveness of a wireless IDS may depend on the expertise of the user and the extent of responses to detect threats (Mandia, Prosise & Pepe, 2003, pp. 12-32). This process may require extensive experiences, resources, and expertise for effective response to threats. Responses must be both physical and logical in order to get hackers.
Costs of a wireless IDS is prohibitive for small firms. In addition, they may not have the required human resources to implement and maintain such systems. Overall, a wireless IDS provides effective security solutions against intrusions.
Conclusion
Wireless intrusion detection and intrusion prevention solutions provide protection against potential attacks on the network. Implementing and maintaining a wireless IDS may have some drawbacks. Nevertheless, it offers effective network security against intrusions.
It has abilities to detect different types of 802.11 threats, DoS, and analyze the system. Organizations with wireless policies and can enhance the effectiveness of wireless IDSs significantly. IDS does not offer total security solutions to networks. Instead, WLANs need other forms of security systems.
A wireless IDS reinforces security features that already exist in a network. Users must recognize that technologies have focused on improving the use of wireless system. These changes bring about new complexities and security challenges. Thus, systems for detecting and reporting new threats can improve the effectiveness of a wireless network.
References
Base, R., & Mell, P. (2001). Intrusion Detection Systems. Washington, DC: National Institute of Standards and Technology.
Calabrese, T. (2003). Information Security Intelligence: Cryptographic Principles & Applications. New York: Cengage Learning.
Caswell, B., Beale, J., and Baker, A. (2007). Snort IDS and IPS Toolkit. Burlington, MA: Syngress.
Hsieh, W., Lo, C., Lee, J., and Huang, L. (2004). The implementation of a proactive wireless intrusion detection system. Computer and Information Technology, 581- 586.
Kent, K., & Mell, P. (2006). SP 800-94, Guide to Intrusion Detection and Prevention (IDP) Systems. Washington, DC: National Institute of Standards and Technology.
Kent, K., & Warnock, M. (2004). Intrusion Detection Tools Report (4th ed.). Herndon, VA: Information Assurance Technology Analysis Center.
Low, C. (2005). Understanding wireless attacks & detection. Bethesda, MD: The SANS Institute.
Mandia, K., Prosise, C., & Pepe, M. (2003). Introduction to the Incident Response Process. California: Osborne.
Max, T. (2009). Information Assurance Tools Report – Intrusion Detection Systems (6th ed.). Herndon, VA: Information Assurance Technology Analysis Center.
Rhodes-Ousley, M., Bragg, R., and Strassberg, K. (2003). Network Security: The Complete Reference. New York: McGraw-Hill.
Trost, R. (2010). Practical Intrusion Analysis: Prevention and Detection for the Twenty- First Century. Boston: Addison-Wesley.
Vladimirov, A., Gavrilenko, V., & Mikhailovsky, A. (2004). Counterintelligence: Wireless IDS Systems. Boston, MA: Pearson Education, Inc.
Yang, H., Xie, L., & Sun, J. (2004). Intrusion detection solution to wlans. Emerging Technologies. Frontiers of Mobile and Wireless Communication, 2, 553-556.