Introduction
Identity theft refers to stealing of other individuals’ personal and financial information and consequently using it for monetary gains Federal Trade Commission. Criminals stealing such information intend to impersonate their victims, so they can access databases containing financial information and private data. Fact that regaining access to the information that was stolen is very difficult has resulted to identity theft victims loosing their identity completely (Garfinkel 256). The lucky few have been able to salvage their identities form their attackers. The aftermath of this crime should convince potential victims that only by aggressively protecting their identities that could lead that they can be assured of private information’s safety.
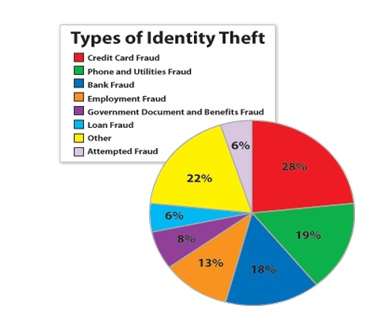
Advancement of information technologies have heightened the crime in United States and globally. This is because criminals can now access personal and financial information of their victims with more ease than before. Despite the increase of information regarding self protection, criminals have been getting smarter and have thus embarked on attacking victims’ identities from various corners as indicated in Figure 1, below:
Avoid Unsolicited Emails
The above scenario means that it is up to individuals themselves and merchants holding client information to ensure that criminal do not gain access at all. Reinforcing ways to efficiently protect consumers from this crime, which could completely tarnish their credit histories for many years, is a matter of great importance? The next will extrapolate on several measures that should be undertaken at both individuals and institutional level to ensure that personal information is always safe and out of reach from criminals. Several key measures (Stancil and Parkes) are detailed below; a conclusion entailing on vital points made in the paper shall follow.
The use of unsolicited emails in collecting victim’ information, also called ‘phishing’, is rapidly becoming a technique of choice for many criminals (OnGuardOnline). This is because many people easily fall victim to email ploys: information requests and URLs are designed to resemble those of credible financial institutions. Victims should understand that financial institutions would hardly ask for their personal information through emails. If anything, institutions already have all the necessary need in their databases. In addition, some of the information requested in the emails is too sensitive; thus more appropriate to be asked during one-on-one meetings in institutions’ branch offices. Individuals should at all costs avoid clicking on hyperlinks integrated unsolicited emails.
Indeed, links included therein lead to websites that depict those of credible institutions, especially those that the affected victims happen to deal with. What is different between both websites is the URL address, whose little alterations could easily be overlooked by victims. Criminal websites could even be spruced to look more professional and attractive than those of credible institutions—this convinces victims that they are dealing with regular institutions. In addition, criminal websites have a tendency to provide too-good-to-be-true offers that entice culprits, who end up leaving their personal and financial information in hope of qualifying for the offers being made therein. But little do they know that they are performing actions which could be regretted in later days. To avoid this scenario, people must avoid responding to such emails. Potential victims should consider contacting their institutions should it appear that some information could have originated from there. Only then can they be sure of protecting personal and financial information.
Invest in a Shredder
Individuals should consider investing in a shredder so they can destroy documents with personal information. It is vital to go through all paperwork before disposing to the garbage or recycling bins. Consequently, documents with personal information such as name, phone number, address, banking and insurance information as well as social security number should be fed to the shredder right away (Foley & Foley 41). Indeed, individuals should consider destroying all paperwork after reading and taking note of information contained in them—this would be the most favourable preventative measure. It is important to remember that some criminals happen to study their prey and thus collect personal and financial information in bits; today they much collect address, tomorrow telephone number, and the next day something else.
All these data is then combined to provide a victim profile, which is further followed by the actual attack. Other than waiting for the day of collecting garbage to collect all the paperwork together and start shredding the, individuals could protect themselves better by reading their mails and other documents upon receipt and shredding them immediately. This will ensure that no papers are left lying somewhere. As a result, individuals will be sure that their information is perfectly safe, that is out of criminals reach. As another measure of reducing the amount of paperwork that people have to deal with, individuals should consider enrolling onto online account management systems. This shall enable them to view and manage banking, insurance, social security and other accounts on the internet rather than relying on mail that get into contact with many individuals. Passwords regarding these accounts can easily be kept safely at home, as well as in individuals’ memories.
Make Copies of Wallet Documents
Individuals should ensure making copies of all the documents (credit/debit cards, work IDs, and driver’s licences) carried on their wallets. These copies should be kept on safe places. In case wallets or purses get stolen, it shall be easier for the victims to report to the relevant authorities for quicker replacements. The speed by which cases of stolen documents are reported to the authorities makes it hard for the criminals to have tempered with the documents. Individuals should thus consider reporting quickly so documents like credit and debit cards are cancelled (California Department of Justice). This greatly reduces chances of having ones identity stoles.
Making copies of the documents and keeping them safe is not enough; individuals must take utmost care in protecting documents they travel with. In addition, social security card or its copy should never be carried on wallets or purses. The same applies to the social security number itself (individuals must never-ever write the number down and put it in their wallets either). In any case, the number should be kept in their memories, which is the safest place. In addition, the social security card, its copy or the number itself should never be given to anyone; the number is not a yours-for-the-asking matter which is why it should be guarded jealously. It has to be considered that the number alone can provide criminals with easier access to other information. As a precaution measure, individuals must ensure to destroy documents that happen to have their social security numbers. Employers and other institutions that happen to have this sensitive number should also ensure that documents and databases are safe from criminals’ access.
Read through all statements
Individuals must ensure to read through all bank, insurance and other monthly statements. Any information that is not inline with what was expected should be communicated to the relevant institutions as soon as possible. Some individuals do not bother to read their statements in full, which make it hard for them to notice whether their information is being tempered-with. They instead get to understand what is going on with their information when it is too late. Reporting early to the relevant institutions could even lead to successful apprehension of the criminals. Individuals should also remember to report to their institutions should their monthly statements fail arrive in mail. This could help reduce the chances of having important mails being redirected to another address without addressee’s knowledge. Rather than waiting till month end to read their statements, it is important that individuals consider enrolling in online accounts. This is because accounts based on the web could be reviewed on a regular basis, like daily or several times a week. When this happens, it becomes easier to see any problem because individuals’ minds can still remember whether they are the ones who performed certain transactions. Waiting till month end could lead to forgetting whether certain transactions took place, especially the little ones.
Although institutions storing personal and financial information have to ensure security of their databases, consumers’, too, have to take some necessary measures that include: avoiding unsolicited emails, shredding documents, keeping copies of documents carried in wallets and purses, and reading through all statements. In addition to these measures, individuals should also consider enrolling in online accounts that reduce the number of paperwork to be dealt with. This however needs the institutions providing online account services to invest in systems that will protect against identity theft. The above analysis has shown that the best way to protect ones’ private and financial information is by ensuring that paper trails are eliminated at all costs. Running to the authorities and relying on the upcoming privacy protection firms would not take victims very far.
Works Cited
California Office of the Attorney General. Tips for Victims. 2007. California Department Of Justice, Office of the Attorney General. Web.
Federal Trade Commission. Identity Survey Report, 2006. Washington, DC: Federal Trade Commission, 2007.
Foley, Linda & Foley, Jay. Aftermath of Identity Theft. San Diego, CA: Identity Theft Centre.
JB MacLean Consulting. Forms of Identity Theft. 2007. JB MacLean Consulting. Web.
Garfinkel, Simson. Commerce, Privacy and Web Security. Cambridge, MA: O’Reilly, 2002.
OnGuardonline. Phishing. 2008. United States Government. Web.
Stancil, Radon & Parkes, Rick. Identity Theft: Four Steps of Self Protection. 2007. Carolina Newswire. Web.