Purpose of an IDS System
Among the reasons behind the use of an Intrusion Detection System (IDS) in the company are in relation to access control (Stewart, Tittel, and Chapple, 2008). The financial impact of such intrusions often results in heavy remedial expenditure (See Figure I). This entails controlling the files and resources that a user on a given network can access. These access controls are crucial in maintaining confidentiality, integrity, and availability of objects on the network. Controlling access on a network can be accomplished using both physical and computer-based mechanisms (Stewart, Tittel, and Chapple, 2008). The purpose of this report is the identification of an appropriate IDS solution for a mid-sized company.
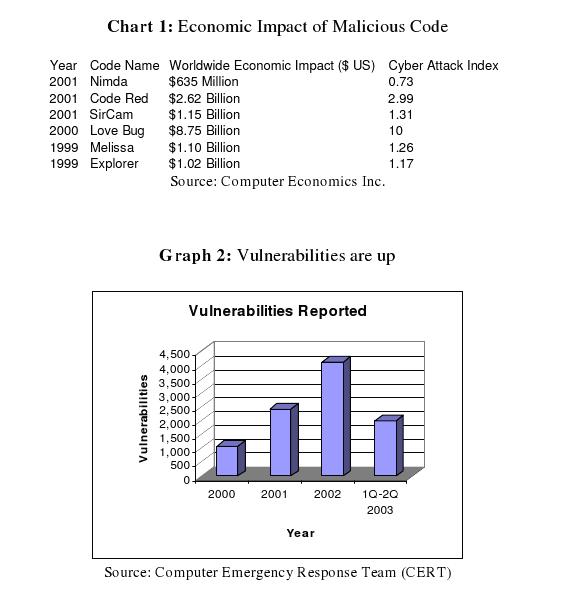
What Is the Degree of Risk?
First of all, it is important to keep in mind that not all attacks occur outside of the firewall. It is not uncommon to find users out of ignorance setting up independent connections that circumvent the firewall entirely (Kozushko, 2003). In such a case the firewall is useless as it can not mitigate risk on a network connection it does not ‘see’. Secondly, it has been noted that a majority of the treats on a network emanate from within the network itself. Just as in the previous case firewalls will do little in such cases as they mainly monitor traffic from outside entering the network (Kozushko, 2003). Lastly, firewalls are also prone to attacks since there are many individuals who make profits from developing means to circumvent the firewalls. From this, it is possible to understand why a software-based solution is inadequate for this problem.
Proposed Solution
The first and reasonably easy-to-use sensor on the system is the use of an effective software-based IDS. It has been observed that a network-based IDS will be more appropriate than a host-based IDS. The host-based IDS monitors a single computer thereby allowing potential threats through the computer network so long as they do not affect the specific PC. Network-based solutions observe illegal activity on the network media.
This IDS is useful in monitoring and preparation of audit reports on the recent activity on the computer network. Other than the tasks related to intrusion detection such software products are also used in the detection of system failures and rating of overall performance (Stewart, Tittel, and Chapple, 2008). These systems can also provide a variety of responses to illegal activity such as; physically preventing the completion of the requested operation, allowing the activity but at the same time recording data pertaining to the activity or prevent the activity and provide a report to the administrator.
A second sensor that can be used for intrusion detection is a honey pot. The honey pot is basically a single computer or network of computers that can act as trap for intruders. The honey pots look ad behave like an actual computer or network but are entirely fake (Stewart, Tittel and Chapple, 2008). The honey pot allows the IDS adequate time to collect information about the user and their potential activity. A third sensor that can prove useful on a computer network is the padded cell. This cell resembles the honey pot but performs intrusion detection using an alternative approach. The difference being upon intrusion detection by the IDS the intruder is isolated in the padded cell which resembles the network or a computer but restricts the user from performing any unauthorized actions.
In addition to the above methods for deterring intruders an vulnerability scanner needs to be in place for occasional audits. These test a computer or a network and measure its performance in relation to various weaknesses of vulnerabilities (Stewart, Tittel, and Chapple, 2008).
Other than the above measures identified, the computer network an be secured using controlling access to password files. In which case only the administrator and such personnel can observe the data. This an be performed by physically placing barriers between other computers and the administrator’s computers (Stewart, Tittel, and Chapple, 2008). In addition to that it would be wise for the administrator to develop and enforce a strong password policy. The stronger the password the harder it is to break so stronger passwords are added security on any system.
In addition to the above-mentioned it may also be wise to enable a two factor authentication process. This may entail the use of bio-metric scans as well as passwords. A good example is the fingerprint scan or voice identification scan (Stewart, Tittel, and Chapple, 2008). This in collaboration with a password is likely to provide very strong security to the system.
It is also essential to encrypt passwords with the strongest available encryption algorithm to ensure their safety. There should be rigid control over files and media that contain password information. Passwords alone have been found to be a very inadequate where computers are concerned. Brute force attacks can often decipher them in reasonably short periods of time. For this reason, a good policy will require passwords are changed often. A policy requiring change of passwords every day or after a specified period can go a long way in ensuring the system is secure from external attacks.
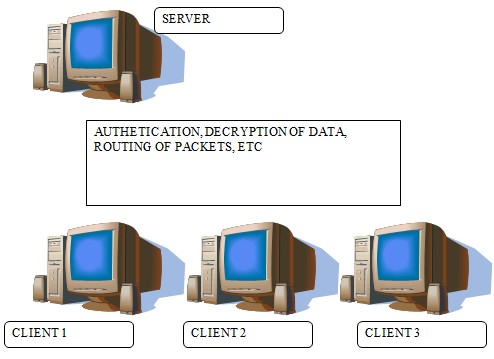
The last sensor to be discussed is related to insider attacks which the administrator may have difficulty identifying from within the firewall (Oppliger, 2002). Properly designed authentication procedures are among the best means to prevent these attacks (Oppliger, 2002) (See Figure II).
References
Kozushko, H. (2003). Intrusion detection: Host-based and Network-based Intrusion Detection Systems. Independent Study, 1-23.
Oppliger, R. (2002). Internet and Intranet Security. Norwood, MA: Artech House Inc.
Stewart, J. M., Tittel, E., & Chapple, M. (2008). CISSP: Certified Information Systems Security Professional. Indianapolis: Wiley Publishing Inc.