Introduction
At the dawn of the new technology and especially in this information age, protecting the same information is very crucial to it. The information technology is propelling development in every field of development including politics, healthcare, manufacturing and agriculture. The corporate world has also benefited a great deal. With such extensive knowledge and competition in place, there are risks that have come to exist and have necessitated the need of information security. This concept means to safeguard information from unlawful persons. This is to ensure that the information is cannot be accessed, used, modified, destroyed or disrupted by any means by unauthorized individual(s). The aim of security assurance for information is to guarantee confidentiality, discretion, attainability and integrity of authentic information.
The Basic Concept of Information Security
For over two decades now three main elements of information security have been developed to form the basis of safeguard information from illegal access. These basic principles include; availability – which refers to the appropriate and dependable access to authentic information and it’s subsequence usage (Kartalopoulos 34) – which is described as protecting information against inappropriate modification or destruction and this entails making sure that information is authentic and not subject to repudiation; and integrity – confidentiality – which is a principles that preserves authorized discretion on accessing and disclosing information and this also covers safeguarding individual privacy as well as proprietary information (Cheswick 83).
Prudence ascertains that information is not exposed to unauthorized people. This is a very important principle since the increased use of online shopping poses a great risk to personal information. For instance, today many people shop using their credit cards and this automatically means that they have to load in their pin numbers for the transactions to be successful (Kartalopoulos 34). There are databases that have been created to enforce confidentiality by reducing the locations that the number has to appear and encrypting the information (Cheswick 85). Nonetheless if an unauthorized individual finds access to the number, then this is breach of confidentiality despite the means used. Over the recent past hacking and subsequent information theft has been very rampant. However it should be noted that this is a serious offence punishable in a criminal court. Intrusion and breach of privacy need to be stopped (Kartalopoulos 37).
Integrity as an information security element is critical to honesty and validity of data. In the corporate world cases of breach of this element are also common for instance when a worker deletes very important information. This is violation of the law whether it was an error or by malicious intent (Cheswick 85). People can increase money on payrolls or delete criminal files. There are some cases when integrity is compromised without malevolent intention for instance a typology error or an automated machine producing numerous mistakes due to improper programming (Kartalopoulos 37).
The purpose of storing or creating information is to be able to access it whenever needed. This is why availability concept is very important. The storage systems should be able to retrieve information very fast and in the original way it was stored. Tampering with accessibility is breach of this principle (Kartalopoulos 39). Therefore unauthorized persons should not interfere with passwords or codes that lead to accessibility of crucial information. It’s with the above principles that security tools were created to help preserve these principles. Firewall is one of the consequential inventions.
Firewalls
Firewalls are currently among the famous network security tools that are offering protection to information systems and continue to increase. Nonetheless these firewalls are most efficient when used in concert with other protective software like anti-viruses, intrusion detecting systems among others (Kartalopoulos 39). This requires a very efficient security plan that is properly designed to meet the requirements of security policy. Efficiency is enhanced this way. A firewall is essentially a set of components that together create a barrier between two networks (Cheswick 85).
These firewalls are able to filter the flow of data coming and leaving a system. The process utilized one or several sets of instructions for inspecting the network packets when they get in or out of the network connection (Kartalopoulos 39). After the assessment, the data can be allowed to come in or blocked accordingly. The instructions can assess one or several properties of the packets with inclusion and not limited to the kind of protocol, the source and target of the hosting system as well as the origin and target of the destination port.
Firewalls are very to a great extent beneficial to the security of the host systems or the said network. They can help in doing one or more functions including:
- Protecting and insulating applications, services and components of interior network from redundant data from public internet (Kartalopoulos 39)
- Limiting or disabling accessibility from hosts of the internal network to the open internet services (Kartalopoulos 39).
- Supporting translation of network address that permits internal network to make use of private internet portals (IP) address and sharing single connection with open internet
Concepts of Firewall
Firewall rule set are often created by use of two methods namely ‘inclusive’ and ‘exclusive’. Exclusive firewall permits all data to get in with the exception of those that match the rule set. Inclusive firewall on the other hand operates in then exact opposite, by allowing data to get in only if they match the rule set. All others that do not match are blocked (Brenton 56). This therefore implies that inclusive firewall is better placed to protect or control the outgoing data and hence the better option for systems that provide their services to the open network internet. This is also efficient in controlling the kind of traffic that originates from the public networks that could possibly gain entry into a private network (Cheswick 92). The data that does not conform to the rules is logged off by design (Brenton 56). The inclusive firewalls are hence safer since they considerably decrease the risk of permitting unwanted data to get in.
Tightening the security can be made possible through the use of the stateful firewall. This type helps to track the connections that are opened via firewall and discriminately permit data through when it matches the existing connection or creates a new opening(Cheswick 92). Nonetheless this has a major disadvantaged of being susceptible to service denial attacks when there are several new connections that are opened in a very short time or very fast (Brenton 56). Many firewalls allow combined use of stateful and other operations to create most advantageous firewall for the specific site.
Firewall Types
There are basically three categories of firewalls in sue. The different varieties are made to address different needs of various users.
Application Gateways: These are the primary firewalls, also referred to as proxy gateway. They are comprised of bastion hosts that operate unique software to function as the proxy server. The software operates as the application level of ISO reference system and therefore derived the name from this fact (Cheswick 92). Users behind firewall therefore have to known how to operate proxy for them to make use of the internet services (Brenton 56). Conventionally, they have been very secure since they do not permit anything to go through by mistake (by default), but they require programs designed and turned on for them to start allowing data to pass. It’s also pertinent to note that these firewalls are also the slowest as they have to start a lot of processes for them to be able to carry out the requested service (Wright 11).
Packet Filter: this involves a system where the Access Control Lists located on the routers are switched on. In normal usage, routers just allow data through them without any restrictions. When ACL’s are employed, security is enforced with regard to what types of access that permit accessing the public internet or vice versa (Brenton 56). There is little overhead in packet filtering compared to use of application gateways since aspect controlling access is carried out at a lower ISO/OSI. This is characteristically the session/transport layer.
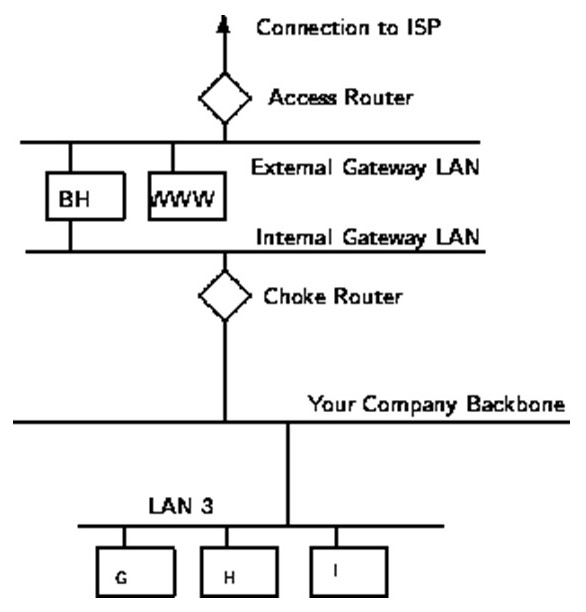
Bearing in mind that the operation is at lower overhead and that the filtering is not done by routers (special design computers intended for networking duty), the packet filtering is usually quicker that later firewall (Brenton 56).
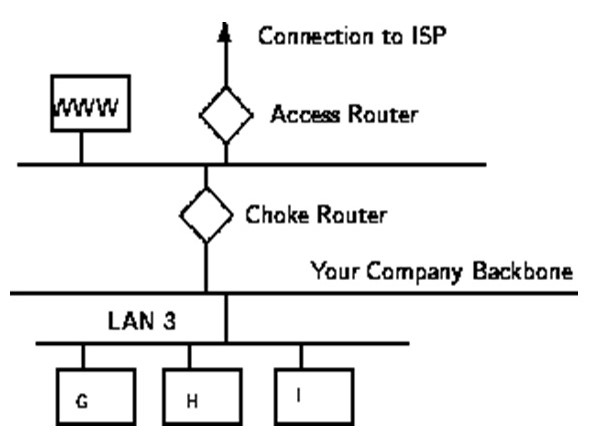
Hybrid System: in an effort to combine application security gateway with the fluid and faster packet filtering model, some experts have devised a system that uses aspects of both models. In a number of these new models, several connections have to be authenticated and supported at the level of application (Brenton 58; Cheswick 92). Once accomplished, the remaining connection is moved to the succeeding layer where the packet filters monitor the connections to make sure that data belonging only to the outgoing (authentic and permitted) conversations are allowed to pass. Other alternatives include use of both proxies (Brenton 56). The advantage here includes offering a measure of safety against systems that offer services to the internet and also offer security to application level to the local network. In addition, this model, an intruder cannot get in the local network unless by breaking the access router and other barriers like bastion host.
Virtual Private Network
This technology permits conditioning of local or private network for a company over the shared or public network like the internet. The internet in such structure is referred to as the VPN backbone and it’s used for transporting data to several VPNs and also to non-VPN systems (Cheswick 102). VPN is a very characteristic element of the security systems in networking. It ultimately offers security to two or more subnets connected top the internet (Brenton 56). Each of the subnets that are served has a specific gateway to the internet which is in turn connected through a protected port to the security gateway of another subnet. This VPN in the context of internet access had been very successful in making connections in office setup, field workers and even for business associates (Cheswick 102). VPN can find use in transfer of information at a smaller portion of the expense of very distinct calls or private hired connections. It offers resources through which corporate network accessible all over the world. Nonetheless, the public nature of the internet requires addressing several security issues (Brenton 56).
VPN Firewalls
A very critical accompaniment to the VPN security is a proper firewall plan or policy. Firewalls permit authorized staff in a company network to access other resources outside the local network through the internet whereas preventing outsider from accessing them company network (Wright 12). VPNs are thus secure in extending the company network beyond the firewall and allow trusted persons and networks restricted access back to the company network. Many organizations can find security services from both VPN and firewall and hence their information is not risked even with open access to the internet (Brenton 57).
There are risks of insecurity on the internet particularly the wide area network no matter how much innovation that is introduced to the security systems (Wright 12). The risks related to the authentication of users and unauthorized snoopers of sensitive information are always present. Nonetheless, internet use has magnified this despite its existence for years (Wright 13). In addition, internet use in transporting private corporate information has created keen disquiet among information managers and users. VPN makes use of the novel security machinery that integrate security network itself so offer answers for the worry concerning the general use of internet. An internet oriented VPN that makes use of this model is evidently safer (Brenton 58).
VPN Architecture
Designing a VPN into a company network plan ought to be carried out as an essential aspect of the corporation general information security arrangement. The arrangement has to appreciate that security of the company information is only good as the ‘loose connections’ to safety (Wright 13). Loose connections characteristically involve individual and not the technology that is used. In practical use, it’s been discovered that many security breaches are as a result of inadequate training of the individuals anticipated to use these systems (Cheswick 102). VPN is only designed to safeguard the risk that is presented by using the internet to transfer information especially very sensitive information about a corporation and so on. Properly executed VPN offered the best security profile for networking (Brenton 58).
VPN and the Internet Security
Internet offers a far-fetched instrument for information sharing. Furthermore it’s cheap, flexible and dominant as offers simple accessibility through well defined system that is widespread. The only setback related to the use of internet net is its directness and hence does not have privacy and consequently a serious challenge for using the internet for carrying sensitive information (Wright 14). VPN has to be implemented properly and carefully to achieve reliability, confidentiality and validity.
It’s possible to create some security measures by manipulation of the general Internet protocol (IP) address which is the communication protocol used by everybody for enable communication across the internet, its possible to create securities for specific information that travel through it (Cheswick 123). An IP security set has been developed by international experts of networking which conveys safe communication capacity. This extension is very critical in presenting a secure internet – oriented VPN. This design differs from the older models in that it works on the information already on the move by safeguarding the network itself rather than the applications beings used or individuals (Wright 14). The main presumption in this mode is that network divisions outside the user’s network are insecure. VPN has hence found extensive use as it’s safer than the conventional WAN and/or dial-in remote accessibility option.
The main aspect that enables secure communication through VPN is the ability to employ tunneling technique. This technique has been very consequential in transferring data through the public networks (Wright 14). This technique regards all the packets from private networks as information (payload) that has to be fetched across the public network. VPN acts as a tunnel that encapsulates the whole packet from private users in a new IP packet ahead of their transport across public lines (Wright 14). The new packets transporting the private addresses of the origin and destination of the data as simply targeted to a second VPN gateway which safeguards the other side of network transmission. The recipient receives decodes and disassembles the infused packet and then passes the contents to the right address on private network.
Conclusion
Despite increased knowledge of information security concern many people have not taken precaution considering that they are vulnerable to infringement as long as they use the internet. Yet so many people are not aware of how their personal information is stored and how much of it can be accessed by another person or get used by the organization they are in. people have no control over their private information. Code of practice however states that there shall not be any information system that uses personal data which is to be kept secret from the public. However there are social rights to information systems which when breached, result in ethical problems. Such rights comprise the right to information confidentiality, the right to owning a computer as well as the right to liberty.
Works Cited
Brenton, Chris and Hunt, Cameron. Mastering Network Security. New York, Wiley Publishers. 2002
Cheswick, William. Bellovin, Steven and Rubin, Aviel. Firewalls and Internet Security: Repelling the Wily Hacker, (2nd Ed). Addison-Wesley Longman Publishing Co., Inc. Boston, MA, USA 2003
Kartalopoulos, Stamatios. Security of Information and Communication Networks. New York, Wiley-IEEE Press. 2009
Wright, Marie. Virtual Private Network Security, Network Security, Vol. 2000, Issue 7, Pp 11-14 New York, Prentice Hall