Structure of BS7799 Framework
BS 7799 is an Information Security Management Standard, the creation of which started in the 1990s.
The first part of BS 7799 (that has been adopted as ISO/IEC 17799) is named the “Code of Practice for Information Security Management” and consists of 10 headings that include 127 security controls, which are further detailed (Gamma Secure Systems, 2001). The implementation of each control is not necessary for every firm, but their number ensures the possibility of customizing the guidelines for a particular business. The second part of BS 7799 that appeared in 1998 is called the “Specification for Information Security Management Systems” and is meant for the assessment and registration of firms (BSI, 2002, para. 6).
Following 1998, the standard continued to develop. The new BS7799-3 is a framework that is consistent with ISO 27001 (BS7799 and ISO 17799 Awareness, n.d., para. 3). The latter standard has been characterized as an “internationally recognized best practice framework for an information security management system” (BSI, 2015, para. 2). Therefore, while still carrying the name of the standard created in the past century, BS7799 is adapting to the changing environment.
The BS7799 framework is aimed at improving the security of information through several controls (Trinity Security Services, 2004, para. 4). The ten primary control areas include “security policy, security organization, asset control and classification, personnel security, physical and environmental security, communications and operations management, access control, systems development and maintenance, business continuity management, and compliance” (Trinity Security Services, 2004, para. 5; Gamma Secure Systems, 2001, para. 4-8, Theobald, 2005, p. 6). To sum up, BS 7799 is aimed at providing security for all the assets of an organization in compliance with the specifically created security policy and through specifically created systems and procedures. The protection is directed against external and internal threats (see personnel and environmental security) and is required for the possibility of uninterrupted business conduct. Finally, BS 7799 is concerned with regulation and law compliance. As a result, BS 7799 provides a framework for defining, managing, and minimizing a wide scope of the external and internal risks that typically threaten information with the intent of covering all the possible threats (BSI, 2002, para. 6-7).
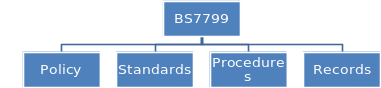
In consistency with its aims, the key elements of BS 7799 include information policy, standards, procedures, and records (see Fig. 1). Obviously, the first three elements are customised; the last one is of particular importance for the process of reviewing the effectiveness of a system. The latter is a crucial part of the BS7799 implementation methodology (Theobald, 2005, p. 9).
Implementation Methodology
The second part of BS7799 defines the methodology for the implementation of the framework. The methodology can be boiled down to the four-step guideline that is characterised by the Plan, Do, Review, Act (PDRA) framework. Every step is supposed to direct people, exploit systems, and define the processes to ensure the consistency of the company’s actions (Trinity Security Services, 2004, para. 3-4).
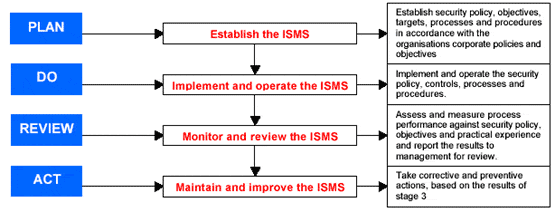
The idea of PDRA was not created exclusively for BS7799, but it is used to implement the standard (see Fig. 2). As can be seen from the figure, the key aims of the first part of the methodology include the processes of defining the policy, objectives, and selecting the standards that are two key elements of the BS7799 system (see Fig. 1). Procedures, the third element, are also planned during the first stage and implemented during the second one. As for the records that are the fourth element of BS7799, they are used during the Review stage of the implementation process. The Acting stage includes the actions aimed at correcting the procedures or objectives in consistency with the information concerning the effectiveness of the current ones (Trinity Security Services, 2004, para. 3-8; Theobald, 2005, p. 7). This stage serves to “encircle” the methodology, ensuring its repetitiveness and adaptiveness.
Advantages and Disadvantages
According to BSI (2002) and BSI (2015), the primary advantages of BS 7799 include:
- A consistent security policy: the first element of BS 7799.
- Adaptiveness: reviewing the work of the security is embedded into the implementation framework (see Fig. 2).
- Increased security and protection through the identification of risks and placement of appropriate controls.
- Customization possibilities.
- Security education.
- The usage of internationally recognized standards results in improved credibility: customers realize that their information is safe.
- Saving costs: reduced number of threats means a reduced number of breakdowns and attacks. As a result, less money is spent on the process of fixing the problems.
- Compliance with new regulations and the law.
Possible disadvantages include the following points.
- Possibly outdated: while being revised, the standard is still based on the framework that was developed in the 90s.
- Customization difficulties.
- Practical problems that are difficult to predict in theory (Qi, Qingling, Wei & Jine, 2012, p. 355).
The two final disadvantages can be explained by the fact that BS 7799 is a framework that is expected to be general. The number of controls of the first part demonstrates the fact that the framework must have predicted most difficulties. The rest of the problems are expected to be solved by local risk management.
References
BS7799 and ISO 17799 Awareness. (n.d.). Web.
BSI. (2002). Information security. Web.
BSI. (2015). ISO/IEC 27001 Information Security Management. Web.
Gamma Secure Systems. (2001). BS7799 How it Works? Web.
Theobald, J. (2005). The Road to BS7799 Certification and Using ISO17799 as an Information Security Framework. Web.
Trinity Security Services. (2004). Is BS7799 For You? Web.