Background
Online security is a complex issue as possible dangers constantly evolve, pushing protective software to change as well. However, some problems can only be partially prevented by a program and should be addressed by professionals to teach the general public about them. Phishing is one of the most dangerous and common ways of stealing personal information, and a user should understand what it is and be able to recognize and avoid it.
Definition and Example
Phishing is a form of online scam that involves a fake email designed to motivate the user to open the attached file or click the provided link. This can be used to spread malicious malware or extract banking information (Gillis). An example email provided by Community Bank (Figure 1) shows how this technique might work (Community Bank & Trust). It can look like an official email from an online service or other organization informing the receiver that they need to update their information to prevent the deletion of an account.
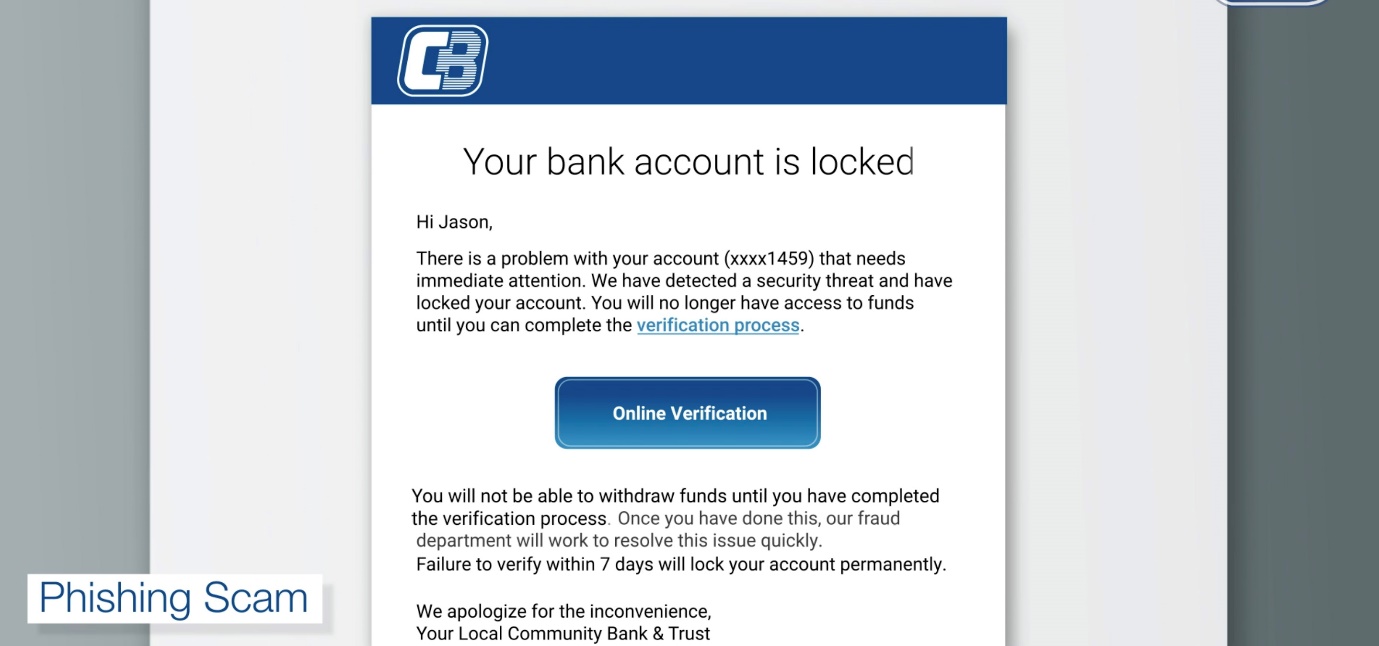
The link will take them to a fake site to gather and transfer the data to the scammer. This artificial sense of emergency and unwanted consequences moves the user to act quickly and think less about the possibility of fraud. Other examples might include a postal notification, prize offerings, or a government notice (Federal Trade Commission; Toohil). Thus, phishing is a type of spam targeted at gathering personal information by deceiving the user with a fake email.
Threat Determination
To recognize this type of scam, the user has to pay attention to phrasing and correct addresses. A person should consider the possibility of a phishing attack if the email has a generic greeting, notifies the receiver of a billing problem, or suggests updating payment details (Federal Trade Commission). If the user notices these signs, they should check the address that sent the message. If it has typos or unusual symbols that try to mimic the original, this email is surely phishing. Any suspicious attached files also indicate the possibility of a scam.
Prevention Strategies
Therefore, a user should be aware of these possible signs of a malware email and recognize them in daily life. Proper and quick action may prevent the scammer from further activity, and users can help. If someone notices suspicious emails, they must add them to the spam folder (Federal Trade Commission). Even though modern spam filters are effective, scammers constantly improve their methods to pass through them.
If an email has an attached file, the user should avoid opening it. In case the receiver has an account in the company that is mimicked by the mail, they can try contacting the customer support service using official emails or phone numbers, not the ones presented in the mail.
Constantly upgrading the security software on computers and phones may prevent attacks that target outdated versions (Federal Trade Commission; Gillis). Multi-factor authentication is also a great way to protect accounts, even if the information is leaked. Finally, backing up the data may be useful if some of it is lost due to an attack. Thus, there are several methods of protecting one’s personal information that common users should utilize.
Conclusion
In conclusion, phishing is a problem that can potentially ruin a person’s life. Losing the credit card information may become a serious issue. However, these consequences are preventable if a person learns how to notice suspicious details in the mail they receive and knows what to do with these letters. Limiting the interaction with malware emails, marking them as spam, and keeping the security software updated is a good practice that is effective in avoiding further attacks.
Works Cited
Community Bank & Trust. Phishing E-Mail. Web.
Federal Trade Commission. “How to Recognize and Avoid Phishing Scams.” Consumer Advice, Web.
Gillis, Alexander S. “What Is Phishing? How It Works and How to Prevent It.” Security, TechTarget, Web.
Toohil, Ryan. Phishing Email from “U.S. Postal Shipping.” Identity Guard, Web.