Introduction
Software discoveries are opening new opportunities to improve people’s lives. Following years of significant investments in software innovation, extraordinary technological progresses currently are changing every facet of our lives, growing the economy, and greatly improving lives. However, these achievements are threatened and eroded by software piracy. Software piracy is “the illegal or unauthorized copying, distribution, or use of software” (Crittenden, Robertson, & Crittenden, 2007). It includes intentional copying of specific software by an individual or business. The vice has extended beyond individual copying and has become a part of the world’s counterfeit trade with a big financial stake involved.
The Business Software Alliance (BSA) estimates revealed that nearly 41% of all software that were sold worldwide in 2008 had been acquired unlawfully and that the losses due to piracy were to increase in the following years, courtesy of global increment in PC usage (Business Software Alliance, 2007). Though software piracy is a global affair, available figures indicate that the problem is more established in developing nations. A study to investigate the state of software piracy in the Asia-Pacific region revealed low rates of piracy incidences in developed countries like Japan, Australia and New Zealand and high rates in developing nations like China and Vietnam (Lau, 2003). Technological ease i.e., accessibility of software and the ease of duplicating it, has created room for stealing and circulation of intellectual property related to the computer, video, and music industries. This paper examines the modes of software piracy, the reasons behind it, who are the offenders, the cost of such actions, and how and who to control them. Emphasis is given on factors or attitudes that account for the predominance of the vice in developing nations and on the corollaries of software piracy, especially economic losses.
Forms of Software Piracy
BSA has identified five types of software piracy. The first one is end-user piracy that involves a person replicating copies of software unauthorized. The second type client-server overuse where many people, beyond the licensed number, use a main copy of the program at the same time. The third one is internet exchange or downloading of unapproved copies of copyrighted programs from the net. The fourth type is hard disk downloading by computer venders who illegally copy software into machines in order to attract customers. The fifth type is the commercial counterfeiting of software with the goal of imitating the copyrighted software (Business Software Alliance, 2007). In hard-disk transfer and counterfeiting, a legal copy of the software is reproduced and circulated to a large number of PCs as if it were a legitimate software application.
Reasons for Piracy
Several reasons have been suggested to explain software piracy behavior. Many individuals until now seem to be uninformed about or are confused about the laws concerning software piracy. The confusion typically stems from the fact that many venders permit differing amounts of copying for backups and other uses. In addition, some have supported copying, with a reason that those who are introduced to the software would become purchasers. How this translates into increased software purchases is a subject of debate since the users get the software, thus reducing their demand for it. Others argue that software piracy is acceptable, especially if it is for purposes of evaluating the software or when there are no monetary gains. Closely linked to this reason is the social acceptance of the malpractice. The people’s opinions on a particular habit are molded by the value system of the society. They change their outlooks, principles and behaviors in reaction to actual or imaginary social influences (Gopal & Gupta, 2010).
In many developing nations, the idea of copyright is vaguely understood and accepted. Thus, those involved in software piracy do not have the knowledge of the consequences of their actions. The initiatives to tackle this ignorance are lacking and if the policies are present, they only exist on papers.
The total cost of software ownership – the purchase price, the cost sustained in ensuring that the software installation does not lead to an unstable computing environment, the cost to learn to use the software to its full potential, and in making it work with other software – may be high and prohibitive to many consumers. A substantial body of empirical evidence indicates that the price of software is a leading determinant of piracy. While software industry has practiced price discriminations in the form of site licenses, volume discounts and according to customer segments in the USA, it has followed “the old trend of global uniform pricing policy where a piece of software costs the same irrespective of the country where it is sold” (Gopal & Gupta, 2010, p. 1948). The uniform pricing policy mainly accounts for the wide disparity in piracy rates across countries, as many people in developing nations resort to cheap counterfeits.
Lenient laws, regulations, and policies contribute to increased illegal acquisition of software. The absence of the threat of punishment is posited to increase an individual’s inclination and desire to acquire illicit software, as there is no personal accountability for piracy violations. In addition, the problem of corrupt law enforcement systems, especially in developing countries makes it difficult to bring illegal software consumers to accountability. That is so because corruption becomes an obstacle to crack down any social, legal and economic evils in such an establishment. Furthermore, the justification by software buccaneers that their actions contribute to equitable resource distribution since they ‘take from the rich and give to the poor’ seams to gain support especially in the many urban slums which harbor numerous information technology SMEs operating almost entirely on pirated software.
Other reasons for the predominance of piracy include not being aware of the procedure of buying software, interest in one feature of the software, and not being able to justify the whole software cost (Crittenden et al., 2007). In addition, the need to have the software at home to complete chores instead of staying late at work or school and accessing the software to benefit the family or the community also contributes to piracy (Crittenden et al., 2007).
The Perpetrators
Software piracy is a global affair and, sad to note, involves many people. In fact, there is a high prospect that most computer-literate persons were at one point in life engaged in this malpractice. The continuum of software pirates is wide spanning from students, cyber cafes, company managers, owners of private PCs and large business organizations. Research reveals that software piracy is linked to culture. Those societies that uphold capitalism as the overriding moral philosophy (North America, and Western Europe) appreciate that the software manufacturers are in business for profit and that revenue created fund the endless cycle of next-generation software. On the contrary, regions of Asia/Pacific, the Gulf and Africa are inclined towards a socialist economic ideology that supports optimization of the overall group’s interest (Nill, Schibrowsky & Peltier, 2010).
Negative Impacts of Piracy
Undoubtedly, software piracy has vivid, negative economic impacts for the manufacturers and distributors struggling to compete in a competitive global market space. Companies that use dishonestly obtained software put more scrupulous competing companies and countries at a disadvantage. A study conducted and published by Microsoft showed that “software piracy in Brazil, Russia, India and China created an aggregate competitive disadvantage amounting to $8.2 billion over five years for companies that play by the rules’ (Meisner, 2011). The study revealed further that for Chinese firms that utilized legal copies of Windows, the finding transcended into a yearly damage of $837 million, a sum that was enough to build roughly 66 manufacturing firms or hire 217,000 workers (each netting $ 3857). The pirating companies (both foreign and local) benefit from the unfair advantage that accrues from the use of stolen information technology by illegally chopping their costs. Piracy also leads to additional monetary lose in unpaid value added taxes.
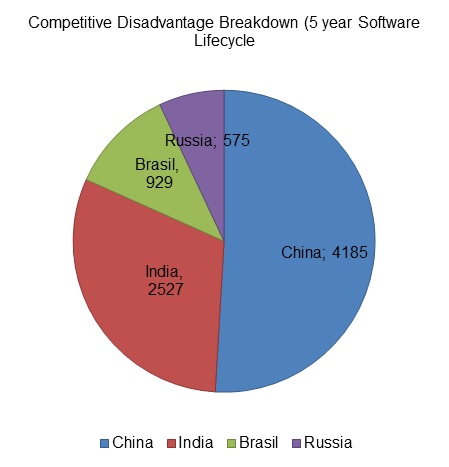
A pie chart showing the monetary competitive disadvantage suffered by the four most vibrant economies in the world because of piracy (Meisner, 2011). The same data can be represented in a table format as shown below.
Table 1. Competitive Disadvantage Breakdown of Four Countries.
Pirated software is likely to be unreliable and insecure. The user is at a risk of viruses and fatal system crash because of corrupted and defective software. Again, the users lose since they do not enjoy the full benefits of technical support, warranty coverage, or product improvement information. Software piracy also benefits scofflaws instead of those who worked hard to create it.
It endangers the future growth and development of the IT industry, which in turn unduly affects countries with the highest piracy incidences. Software piracy discourages software developers as they gain very little from their effort. It hampers research and development. For instance, in the USA where the rates of software buccaneering are low, software developers are highly motivated to invest in R & D. BSA estimated that in 2014, these companies committed $52 billion in research and development, the money being channeled into developing new data analytics and breakthrough technologies like cognitive computing (Business Software Alliance, 2007). Indubitably, these companies cannot commit huge sums of money in the development of software in environments where piracy and counterfeits are the order of the day.
How to Control Software Piracy
Software firms and the governments can explore numerous options to protect intellectual property rights. The precautionary, deterrent and economic approaches may be technical, legal/moral, or product and pricing measures. To start with, there is a necessity to reinforce the existing copyright laws in order to discourage consumers from committing software piracy. Practical methods as copyright protection techniques and reactive responses such as closing service to illegal web distributors can be effected. Hardware-based checks like “nonstandard disks, coder cards and hardware locks, and software-based restrictions like unique password cords and encryption are tenable” (Gopal & Gupta, 2010, p. 1949). Deterrent measures emerge from the legal defense extended to creators of intellectual property from the laws that are aimed at rewarding and fostering innovation. Deterrent control covers informative, investigative, and legal campaigns to enforce the law and dissuade consumers from engaging in the act of piracy. It aims at increasing both the likelihood of detection of illegal activity and the severity of punishment when caught.
Conclusion
This research paper shows that the importance of the software industry is immense and that piracy continues to threaten these benefits. In order to optimize these benefits and ensure that they reach the right persons toiling for them, there is a need to develop mechanisms that incorporate cultural and ideological differences, and consider diverse modulating variables that influence piracy rates globally.
References
Nill, A., Schibrowsky, J., & Peltier, J. W. (2010). Factors That Influence Software Piracy: A view From Germany. Communications of the ACM, 53(6), 131-134.
Business Software Alliance. (2007). The $1 Trillion Economic Impact of Software. Web.
Gopal, R. D., & Gupta, A. (2010). Trading Higher Software Piracy for Higher Profits: The Case of Phantom Piracy. Management Science, 56(11), 1946-1962.
Lau, E. K. (2003). An Empirical Study of Software Piracy. Business Ethics: A European Review, 12(3), 233-246.
Meisner, J. (2011). Microsoft Examines the Financial Harm of Software Piracy on Play Fair Day. Web.
Crittenden, W., Robertson, C., & Crittenden, V. (2007). Hard Facts About Software Piracy. Business Strategy Review, 20(5), 28-33.