Employees of HATI may abuse their privileges. This leads to the emergence of the first vulnerability for this organization that occur in cases where these employees perform other functions, which are beyond their job responsibilities. On the same note, HATI employees may share classified information for the organization with third parties.
Moreover, HATI organization may face platform vulnerabilities for its laptops. Such situation leads to denial of services, corruption of data, or even unauthorized access to data (Cybercrime, 2012). An example of this is the “Blaster Worm”, which may deny the organization services in case the laptops have Windows 2000 as their operating system. Database communication protocols are also vulnerabilities for HATI Company.
SQL injection attack is one threat, which HATI organization may experience while performing its functions. SQL injection creates an opportunity for the attackers to access the whole database for an organization. HATI may also have a weak audit trail, which indicates that the organization may have higher risks in several levels, which include detection and recovery, deterrence, and regulatory risk.
Furthermore, HATI may have a Denial of Service (DOS) attack, which may be created by several vulnerabilities. DOS techniques include network flooding and corruption of data among others (NIST, 2007). Finally, weak authentication for the database, as well as exposure of the back-up data for the database is a threat, which HATI organization may face while conducting its financial transactions.
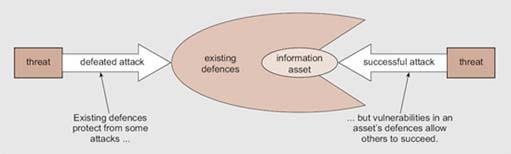
Personal opinion on the risks, which HATI faces, is that denial of service; weak authentication of database, privilege abuse, and weak audit trail of all data processes are the significant risks to the organization. If the organization cannot control these risks it will eventually collapse due to the fact that the organization will incur losses, be attacked, and lose confidential data. Figure 1 shows how the organization may be at a risk because of a threat.
HATI has an opportunity of using query-level access control (QLAC) as a measure of eliminating the vulnerabilities of employees’ privileges abuse. QLAC illustrates a mechanism, which has the power to restrict privileges of the database to the minimum operations of the SQL, as well as data.
This mechanism has the ability of issuing an alert in case an employee is engaged in malicious activities. However, this mechanism needs to use SecureSphere’s Dynamic Profiling Technology, which enables the creation of various algorithms that contribute to the generation of query-level usage profiles for the organization employees (Perrin, 2009). In addition, HATI should develop a database access control which limits unspecified access to the database.
HATI may also adopt intrusion prevention systems (IPS), which aid in the inspection of database traffic of any potential vulnerability. IPS does this by either blocking access to a procedure that is vulnerable, or procedures, which may result in an attack to the organization (Pfleeger, 2003).
The functionality of IPS should be improved by the incorporation of query access control indicators, which determine whether requests correspond to normal behavior of users or not. An IPS has the ability of minimizing attacks as the one indicated in figure 2. Platform attacks for HATI can only be prevented by the adoption of intrusion prevention systems and having regular software updates. This will ensure that vulnerabilities, which the organization may experience over time, are minimized effectively.
SQL injection, which may have tremendous negative impacts on the processes and functions of HATI Company should be combated by combining three techniques, which are event correlation, query-level access control, and intrusion prevention (IPS).
Weak authentication and audit of the database activities should be addressed by having a strong authentication and high performance of the auditing platform (Learning Space, 2012). On the same note, Denial of Service (DOS) should be combated by protection of database, applications, and networks. Finally, attack of database communication protocol should be prevented by adaptation of protocol validation measures.
Characteristics of a policy statement
A policy statement should be clear and easy to understand and should ensure that it delivers its message effectively. Further, the quality for such a statement should be measurable for employees to implement its concept effectively (Shulman, 2006). Moreover, a policy statement should be realistic and useful to an organization. Finally, the objectives of the policy statement should be aligned with the goals of the organization.
Policy Statement
Purpose: To provide adequate information on the necessity of protecting client and corporate data.
Scope: This policy is applicable to all employees of HATI Company involved in the process of handling both client and corporate data.
Henry Advanced Technology, Inc. (HATI) recognizes that client and corporate data are vulnerable to various threats. Handling data is a responsibility of each employee in the company since such data may lose its value or worth in case it is tampered with. Therefore, all members must depict higher levels of professionalism and responsibility while handling data for the organization.
It is the policy for this company to:
- Ensure that the safety level of both client and corporate data is high.
- Data is not rendered unusable because of compromising the same.
- All employees stick to job responsibilities, which they are allocated and handle data at higher confidential levels.
- Employees do not engage in malicious acts of altering data, which is stored in their laptops.
- Employees will be held liable for any malicious acts detected while handling either client, or corporate data.
Reference List
Cybercrime. (2012). Financial Organizations Must Improve Data Security Practices. Web.
Learning Space. (2012). Threats and Vulnerabilities. Web.
NIST. (2007). National Vulnerability Database (NVD). Web.
Perrin, C. (2009). Understanding Risk, Threat, and Vulnerability. Web.
Pfleeger, C. (2003). Security in Computing (3rd Ed). United States of America: Pearson Education, Inc.
Shulman, A. (2006). Top Ten Database Security Threats. Web.