Scope of the ISMS
The security policy in this document has been prepared in accordance with the needs of MilkChurn, a leading diary firm based in the United Kingdom. The strengths of the companies lie in the sales and marketing, retail & convenience, wholesale and food services. The company records an annual turnover of approximately £ 250 million. The firm management believes in a variety of market segment with its product line that includes yoghurts, baking products, cereals, flavoured butters, ice cream, butter, cream, spreads, mayonnaise, fruit juices, soft cheese, prebiotic dairy, frozen desserts and milk.
The operations, which consist of the company’s central part activities, include trade dealing, blending, associate production, brand administration along with development and manufacture. The firm is successful and holds an eminent share in the internal UK market, leading to booming chains of supermarkets, convenience and specialty stores. In addition, the company also employs overseas sales of its products to various foreign markets including the Caribbean, Middle Eastern and North American markets.
MilkChurn aims to reach a very standard and aims to maintain their strong presence in the dairy service market by presenting itself as an exclusive and efficient sourcing choice. The company opens various activities in order to complete its goals and meet its growth objectives. Such functions include comprehensive brand management and market development moves. Further, the company ensures close teamwork in its supply chain and carefully oversees all its operations such that the implemented plans are logical and in agreement with market demands.
MilkChurn uses the support of 70 full time on the job employees to ensure the smooth running of the I.T. infrastructure of the company. These personnel are well spread across five operational divisions, namely purchasing and export, retail sales, production, food service and trading and marketing. The information technology framework in the firm comprises 50 networked workstations in addition to four servers. Minor connectivity is obtained by means of a standalone Internet connection. The Internet connectivity is made use of for primarily for Email communication, web browsing and Electronic Data Interchange (EDI) with collaborators and retailers for efficient supply chain activities.
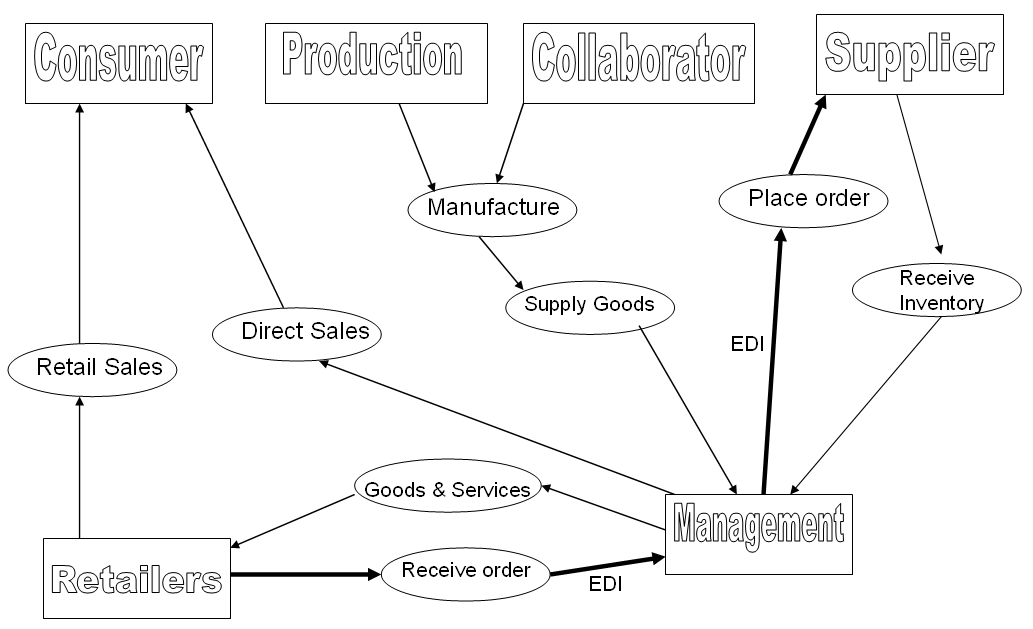
This report keeps the operational structure of the business processes in the firm in mind and a broad based security policy is developed. A systemic approach was identified to be the most proper method to adopt in order to achieve a wide-ranging risk management policy. The system primarily deals with information security in the firm. However, it also pays attention to important business processes which might have an impact on or can be notably affected by the security policy of the firm.
ISMS Policy
The objective of this policy is to provide the management of the firm a sense of direction to help the smooth performance of essential information security. This policy is endorsed by the management and is regularly reviewed to assess and evaluate its effectiveness and understand the overall impacts it has on the entire organization. This policy must be distributed to all members of the firm and well understood by the concerned workers.
In order to understand this policy one should clearly understand the meaning of information security and the need to apply such a policy.
Information is considered to be an asset which is extremely vital to an organization’s business process and thus requires enough protection. The notion of security gains added meaning in an increasingly interlinked business setting. Consequently, due to increased interconnectivity, information is subjected to numerous varieties of threats and weaknesses. Information can be documented on paper, added electronically, communicated by post or transmitted through electronic channels, presented in films, or spoken verbally. Regardless of form, or sharing or storing mechanism, information must be properly protected. Information security refers to the safeguarding of information against a variety of threats and weaknesses to make possible business stability, minimization of business risk, and maximization of investment payback and strategic opportunities. Information security is attained by applying an appropriate range of controls, incorporating strategies, practices, procedures, organizational compositions and software and hardware utilities. These controls are required to be recognized, applied, scrutinized, reviewed and enhanced, when and where it is required to be essential, in order to make sure that the definite security and business ideas of the firm are realized. It should be ensured that this is done in a manner in which the policies are arranged in a line with other business management processes.
Establishing, realizing, protecting and enhancing information security is important to maintain competitive advantage, cash flow, productivity, legal agreement, and commercial reflection of the firm. Information systems and networks are subject to security threats from an extensive variety of sources, such as computer-assisted scams, intelligence, sabotage, destruction, and natural or circumstantial disasters. Reasons for harmful outcomes such as malicious code, computer hacking and denial of service attacks are increasingly growing in amounts, becoming more powerful, and gradually more sophisticated. Information security can be considered an efficient tool to avoid, ease and reduce pertinent risks to the firm. However, the trend of distributed computing has somewhat weakened the efficiency of fundamental specialist control. Thus, the protection that may be attained by technical means is restricted and has to be reinforced by suitable administrative policies and procedures. Information security management necessitates inputs and contribution by all members of the staff of the company. It also calls for involvement of stakeholders, providers, third parties, consumers or various other exterior entities. Professional guidance from external consulting organizations is used if required.
The security requirements of firm’s information communications can be broadly regarded as to comprise of the following related features:
- Availability –Data should be easily reached and services should be capable, regardless of potential unsettling incidents like power supply failures, natural calamities, mishaps or assaults. This is specifically crucial as communication network breakdowns can bring about collapses in other key business processes.
- Authentication –confirmed identity of individuals or users of the information network of the firm should be checked and confirmed prior to access granting. Effective verification instruments are necessary for various important functions and services such as online contract decisions, access control to specific core data sections and classified services and authentication of users using core financial applications. Authentication should also include the prospect of anonymity, as many applications and services may not be necessary to confirm the identity of the user but only require the fulfilment of the vagueness credentials.
- Integrity – Data transactions which involve change of information must either be complete or data must remain unchanged. Confirmation mechanism for this standard must be in place and operational at all times.
- Confidentiality –The security of communications and stored information in the event of interception and access by unlawful entities must at no cost be compromised. It is specifically required for the secure transmission of sensitive and classified data and is a primary requirement while dealing with privacy concerns of users of the firm’s information channel.
The risk assessment bears a comprehensible acknowledgement of critical and fundamental aspects which needs to be controlled. Risk management operations are designed in a cost-effective and practical manner. The policy of the firm is to adopt an effective risk management strategy which introduces a sense of balance amongst the outlay of resources and the requisite level of security. This policy makes certain that the resources spent are united with the latent loss and worth of the assets secured.
The firm as well as its employees is required to adhere to a variety of legislation and regulation and needs special mention in this policy report. The drivers for these rigid rules comprise of Corporate Governance, Electronic Commerce, Identity Theft and Data Security, Health and Safety and Intellectual Property. For information security the legal framework is primarily supported by the United Kingdom’s Computer Misuse Act. The European Union also contributes to the legal framework in the areas of Electronic Signatures Directive, Consumer Protection and Distance Selling Directive, Directive on Privacy and Electronic Communications, Council of Europe, Convention on Cyber-Crime. In addition, all member countries of the European Union have employed a national legislation on account of the European Union Data Protection Directive. Any infringement of national and company legislation with regards to Information Security brought under the notice of the firm’s management will be dealt with a strong hand. A committee would decide on the seriousness of the violation and penalty may also include termination of service.
Risk Assessment
Just as any other organization MilkChurn also faces its share of uncertainty, threats, vulnerabilities and risks. Thus, with the intention of lending some stability and sustainability of services and uphold flexibility, competitive advantage a systemic approach towards risk is adopted. It is crucial to identify the extent to which risk and uncertainty is acceptable to the firm. In addition it is also important to craft out means to manage the risks in a cost-effective manner and do so in a way which is aligned with the ultimate strategic business objectives of the firm. Adopting business-friendly instruments to deal with a variety of risks, hazards, threats and vulnerability that the company faces is important.
It is required that the firm should to recognize and adhere to a methodical system and approach to risk assessment. It is of immense significance that information security risk is dealt with visibly keeping in mind the objectives of the firm. Nevertheless, dealing with the risks can be approached by means of various risk assessment and handling techniques and an assorted level of granularity that fits the requirements of the firm can be attained. It is entirely the decision of the organization which risk assessment approach is chosen. It is essential for the method of risk management to be proper and apposite in order to comply and be aligned with the objectives of the different divisions of the company. Risk identification techniques include activities like Brainstorming, Surveys, Researches which scrutinize each business procedures and illustrate both the in-house operations and external aspects which can leverage those activities, comparisons with Industry Standards, Scenario evaluation, Risk assessment seminars and awareness initiatives, Incident analysis, Auditing and Appraisal and HAZOP (Hazard & Operability Studies). Risk Analysis techniques includes activities such as Market Researches, Prospecting, Business impact evaluation, Test Marketing, SWOT Analysis, Event tree investigation, Threat analysis, Fault tree analysis, etc.
The firm adopts an integrated approach which helps steer clear of segregating and loosing focus on risks. This approach provides a framework by means of which the firm can comprehensively understand the associations of the risk and thus a better and enhanced solution method can be adopted. This influences the viewpoint, awareness and competencies of various divisions and individuals within the company. Due to the low probability and possibly grave consequences of various natural, calculated or unintentional risks that the firm is subjected to, this approach allows the company to prioritize its operations while handling the risks in an economically acceptable manner.
An asset is an entity that holds some large amount of worth, value or efficacy for the firm, its business structure and its preservation. Thus, assets are required to be protected in order to make sure smooth business functioning and business sustainability. The appropriate handling and liability for the assets is very important and is considered to be one of the most important responsibilities distributed amongst all management echelons. The most significant assets embarked by the capacity of the ISMS are unambiguously acknowledged. So as to make certain that no asset is disregarded or ignored; the scope of the ISMS has been described with respect to the traits of the business, the firm, its positioning and assets. Grouping related or linked assets into convenient sets facilitate the reduction of the endeavour required for the risk assessment course of action. Answerability for the assets facilitates in the process of ensuring that satisfactory levels of information security is preserved. It is required that a holder be acknowledged for all of the recognized assets, or collection of assets, and in addition, the accountability for the preservation of apposite security measure has to be shouldered by the holder of the asset. The task of putting security controls into operation can be distributed even though the answerability continues to persist with the designated holder of the identified asset. The asset holder is in charge of delineating the proper security categorization, responsible for laying down access control criteria for the asset. It is his prerogative to provide consent and record these verdicts and to maintain apt asset security management. Further, it is also the asset holder’s duty to frequently appraise the access rights and the security categorizations. Additionally, it is practical to delineate record and apply rules for the adequate utilization of the assets, illustrating allowed and prohibited actions in the daily exploitation of the asset. The personnel making use of the assets are required to be informed about these regulations and should be conscious of the fact that the approved means of handling these assets is an essential part of their everyday jobs.
Assets
- Information: Information is of the most important asset any company possesses. MilkChurn is no exception in this case. Information may take many forms. It may appear electronically in the form of electronic data in databases or data files. It may also be in the form of company or system records or documentation, bonds and agreements, user guidance documents, training brochures, operational records or support documentation or any other crucial business reports, plans or alternative arrangement documents. Regardless of the form in which it appears it demands a certain degree of protection and this concern should be carefully addressed.
- Processes and Services: This includes business process designed specifically to cater to the various divisions of the firm including, sales and marketing processes, retail and convenience services, wholesale processes and food services.
- I.T. Infrastructure: The firm boasts of a well established information technology infrastructure which comprises of 50 networked workstations as well as 4 servers. The firm is also provided with Internet connectivity to facilitate communication and browsing activities.
- EDI Setup: The firm exploits the Electronic Data Interchange framework for the transmission of data and maintains an efficient communication channel with its supply chain including its collaborators.
- Software: Application software specifically designed for the use of the company, system software used by the firm and electronic utility tools provided to the company are considered to be major assets for MilkChurn.
- Production and Manufacture facilities: The Company intends to penetrate into the domestic United Kingdom market and enhance its market share in the dairy consumer goods segment. Thus, the company produces retail ready goods including packaging and direct sales. For some products and materials it engages into partnerships and the production is partner production.
- Collaborators: Just like any other major business concern the firm possesses a range of collaborators in the form of partner producers, retail chains, supermarkets, leading grocery stores etc. The firm has entered into strategic deals with these collaborators in order to gain a competitive edge. These strategic deals with collaborators are key assets in the company’s repertoire.
- Physical Infrastructure: The physical areas such as buildings, offices and storehouses through which the firm operates forms a major part of the firm’s asset list. The technical support such as heating, air conditioning, power and lighting also make up the physical infrastructural assets of the company.
- Physical Items: These include the personal computers, communication equipments, and storage media such as paper, CDs and disks. In addition, any other item used in processing of internal or external data for the company is an asset placed under this category.
- People: This category includes members of the company staff, consumers, suppliers and any third party involved in the processing, storing or sharing of data or information.
Risks
- Technical Equipment Failure: There is a high probability of this risk occurrence and the security policy deems this risk to be mitigated.
- Accidental Leakage of Business Information: A medium probability risk which can be mitigated.
- Theft of Equipment or Information: A high probability risk which can be mitigated.
- Illegal Outsourcing of Confidential Data by company Personnel: A low probability risk which can be mitigated.
- Supplier Failure to Comply with Requirements: A low probability risk which has to be accepted.
- Financial fraud or Scams: A low probability risk which is to be mitigated.
- Database Error: A high probable risk which can be mitigated.
- Eavesdropping or Denial of Service Attacks: A medium probability risk which is to be mitigated.
- Internet Service Failure due to ISP Server Issues: A low probability risk which has to be accepted.
- Application Error: A low probability risk which can be mitigated.
Risk Treatment
After the risk assessment is complete, the management needs to decide on the approaches towards risk treatment based on the outcome of the risk assessment. Subsequent to the choices concerning risk treatment being made, the actual implementation of these conclusions is required to be recognized and designed carefully. Each risk treatment activity needs to be unambiguously acknowledged and categorized into numerous sub-activities as required in order to be capable of assign understandable responsibilities to personnel, calculate approximately resources expenditures, set targets and time limits, chalk out deliverables and track the course of development. The risk treatment designing procedure requirements include the classification of major entities involved for instance resource holders and a discussion process to make sure that resource expenses are correctly calculated and can be feasibly allocated, and that the related echelons of management consent to expend the resources have been acquired. The execution period and commencement times of different risk treatment activities bank on the general precedence with reference to the various activities in the treatment initiative, the resource accessibility as well as reflection on funding aspects and availability of human resources and analysis of pre-requirements prior to the commencement of the process. Other industry and information change initiatives of related fields need to be cautiously synchronized with the risk treatment scheme in order to make sure that any interdependence is identified and considered appropriately. Prioritizing initiative is a management prerogative and is strongly aligned with the outcomes of risk assessment phase. Activity precedence is laid down to make certain that the initiative is paying attention to the most hazardous risks. However, other business circumstances may influence the precedence of various initiatives such as resource required to offset a risk may be presently engaged in a competitive edge gaining activity and thus the risk treatment initiative has to be delayed. After the risk treatment scheme has been established, resources are assigned to specific initiatives and activity to put the risk management measures into operation is commenced. It is essential that at this stage to make certain that there is a comprehensible review procedure prepared to make sure that initiative progresses as intended, deliverables are of the preferred eminence and that targets are met along with optimal exploitation of resource within estimated limits.
The plan to treat the risks identified for the MilkChurn Company is as follows:
- Technical Equipment Failure: This category of risk is judged to be a high probability risk. The treatment plan assigns high priority for the mitigation of this risk. Technical equipment failure can emerge in a variety of forms. It may range from a computer storage equipment failure to a power supply interruption. Thus it is required that all information is regularly backed up in at least two different storage media and should be carefully stored. A general equipment check must be carried out periodically be specialized designated personnel. All network utilities and communication facilities should be connected to a constant power supply. Backup power provisions must be in place at all times. In case of a major equipment crash external professional support must be sought immediately.
- Accidental Leakage of Business Information: The outcome of the risk assessment carried out deems this risk as a medium probability risk. Thus the risk treatment initiative for this risk lies in the bottom half of the precedence list. Long term initiatives such as proper training and awareness programs must be carried out periodically. The members of the staff must be aware of there responsibilities and should process, share or store sensitive information in a secure manner. Proper procedures for the same must be taught to the individuals handling data. Discretion while handling or sharing data and information must be sought.
- Theft of Equipment or Information: Business competitors are always on the lookout for sensitive data of the firm to gain a competitive edge. Thus this category of risk is deemed to be a high probability risk and thus mitigation of this risk is of high precedence. Firewalls and encryption technologies must be put in place. Company personnel engaging in information exchange with legal entities should be trained to use secure channels. Data and information storage areas must be put under strict surveillance. Physical and electronic security measures such as security guards and surveillance cameras must be installed at sensitive locations.
- Illegal Outsourcing of Confidential Data by company Personnel: Even though this category of risk is adjudged as a low probability risk, risk mitigation initiatives countering this threat is given high priority. Access control mechanisms are extremely important while dealing with this kind of threat. Security clearance levels must be established in order to access specific information. Personnel accountability awareness must unambiguously be chalked out.
- Supplier Failure to Comply with Requirements: Not all risks can be mitigated by use of technical support or resource allocation. As it is adjudged to be a low probability risk the risk is deemed to be acceptable by the risk treatment plan. However, levels of acceptance must be clearly delineated.
- Financial fraud or Scams: It is deemed to be a low probability risk. Nevertheless, measure dealing with the treatment of this risk need to be strict. Periodic internal reviews and audits must be carried out. Transaction tracking processes must be regularly monitored and any attempt to engage in a fraud must be nipped in the budding stages. However, scams or attempts to carry out a fraudulent transaction should be dealt with a strong hand. Any report of such activities must be investigated by a committee of management personnel and apposite measures must be taken against the individuals attempting to engage in such activities. These measures may include heavy fines, termination of service, and cancellation of contracts or legal cases against the identified party depending upon the severity of the crime.
- Database Error: Database errors are very common and thus deemed as a high probability risk. However, even a small database error can have serious consequences on various business processes and can even lead to a major operational catastrophe. Thus it is extremely important to ensure that the integrity and consistency of the database is maintained. Firstly, trained and skilled professional must be hired to work with databases, specifically which contain sensitive data. Technical constraints must be put on all database transactions and access control layers should also be delineated.
- Eavesdropping or Denial of Service Attacks: With network hacking techniques becoming increasingly sophisticated, complicated and growing in ambition it is extremely important to have network security measures in place. A reliable firewall must first be installed which can control the access to the firms network efficiently. Encryption technologies must be applied properly and it should be ensured that the communication channels are safe and secure. Software and hardware must be upgraded periodically to provide protection against newer attacks.
- Internet Service Failure due to ISP Server Issues: It is adjudged as a low probability risk by the risk assessment process. The risk treatment plan follows a short-term acceptance policy for this form of risk. However, if the problem persists and it has a significant impact on the running of various business processes alternative options must be explored.
- Application Error: Deemed to be a low probability risk it should be attended to by the software vendor’s support and maintenance staff. The reporting mechanism to the software vendor should be easy and uncomplicated and it must be ensured that the problem is addressed with immediate effect.
Statement of Applicability
The risks identification in this document has been done bearing the business operational structure of the dairy company named MilkChurn in mind. The risks and threats identified and treated in this report are the ones which have the most serious consequences on the business functions of the firm. A systemic and causal approach has been taken in order to manage the threats and vulnerabilities in which the assets are first identified. Subsequently, the risks are identified and classified according to the probability of occurrence. Thereafter, the risk treatment policy is designed in which the precedence of the risk treatment initiatives are delineated and a decision is taken on whether to mitigate the risk or to accept the risk. This is done in a systematic manner after analyzing the business scenario, resource availability and management concerns. The risk treatment plan is designed to be economically optimal. Control initiatives have been planned in a manner such that it bears significance on the short term and long term impacts of the risks on the business process. The acceptance levels of the risks have been defined and course of actions have also been determined.