Introduction
Background
Zara is among the leading textile and apparel companies in the world. The company was founded in 1963 by Amancio Ortega Gaona and was later joined by Jose Maria Castellano in 1985. Zara is a force to reckon with in the global textile and apparel market (Thomas, 2006, p. 47). Locally, it is considered to be among the biggest success story in the history of Spain.
Zara’s success is a lesson on how to develop and maintain a groundbreaking strategy (Ferdows, Lewis & Machuca, 2003, p. 62). The consumer is always at the centre of the company’s business model.
The two founders shared the belief that swift response to consumers, the use of IT (Information Technology), and decentralized decision-making were important for the success of the business (McAfee, Dessain, & Sjoman, 2007, p. 5).
Inditex owns more than 2000 stores across the globe out of which 600 stores are exclusively part of Zara chain. The largest share of Inditex’s sales is generated by Zara. Zara offers a variety of clothes for people of all walks of life at a reasonable price. However, the major portion of Zara’s revenue is from the female clothing (McAfee, Dessain, & Sjoman, 2007, p. 7).
Zara developed a marketing model which relies entirely on trends and styles, with minimal advertising. The vertically integrated marketing model emphasizes on swiftness, efficiency and the global fashion trend. However, the company’s approach to IT is not in-line with its marketing model. In addition, its websites are only for display and not for sales purpose (Ferdows, Lewis & Machuca, 2003, p. 64).
According to Azuma and Fernie (2003, p. 413), Zara’s success in the apparel industry can be linked to the application of successful competitive marketing strategies, which encourages global expansion. Zara’s successful entry into the global apparel market was a result of their spirited marketing strategies, for instance, promotional techniques which increased the contents of their fashion line.
Zara classifies its products into three fundamental groups namely: gentlemen, ladies, and young ones. The company’s low priced products attract and retain customers, thus creating sustainable growth of their value chain in the apparel market (Azuma & Fernie, 2003, p. 415).
Report Purpose
The general purpose of this report is to explore the problems and challenges facing Zara Textile Company. Our study will be narrowed to the company’s ICT which has been criticized by a number of authors for being outdated.
The study will explore the extent of the problem and the risks it poses to the company. The study will also evaluate strategies that the company can take to arrest this problem. In addition, the paper will look at other alternatives that the organization can pursue.
Nature of the problem
In the last two decades, the company has been developing its own applications rather than purchasing the commercial ones. The company has an outdated operating system known as P-O-S. Zara entirely depends on P-O-S, which lacks full-time network for its store terminals. P-O-S (Point of Sale) runs on DOS which is not compatible with Microsoft applications (Bhagwat, 2011, p. 3).
The company’s management argues that the operating system is easy to maintain and operate. On the other hand, experts feel that it’s time for the company to upgrade the current system or risk reliability. They argue that the current system will not be attuned to the future changes in the fashion industry (McAfee, Dessain & Sjoman, 2007, p. 6).
Zara’s use of IT is not in line with its goal of swiftness and autonomy in decision-making. The company has spent very little on IT and does have any definite budget for it. It has more confidence on individual brainpower than on the machines in decision-making (McAfee, Dessain & Sjoman, 2007, p. 6).
The company prefers to develop its own system than purchasing the commercial software. Zara’s IT department is separated into three sections: data storage solutions, logistic support and management system. This department has witnessed a very low turnover since its inception (Bhagwat, 2011, p. 5).
Analysis of the Problem
Before moving to the problem, the study will make use of the conventional model designed by Michael Porter to get a grasp of the company’s operations. Porter came up with a set of activities that can be used to assess a company’s competitive advantage.
It is important to model a company as a string of value-adding activities. The value chain helps to identify areas of weaknesses and strengthens (Porter, 2008, p. 83). The model is important in determining the best strategies to be adopted by the company.
The value chain categorizes company’s operations into crucial and secondary operations. The crucial activities are company’s operations that are linked directly to the production of goods and services, whereas the secondary activities comprises of operations that support and facilitate the crucial activities (Porter, 1980, p. 12).
The company’s ability to survive in the industry depends on its efficiency in performing these activities (Kroenke, 2012, p. 51). The figure below shows porter’s value chain model for Zara.
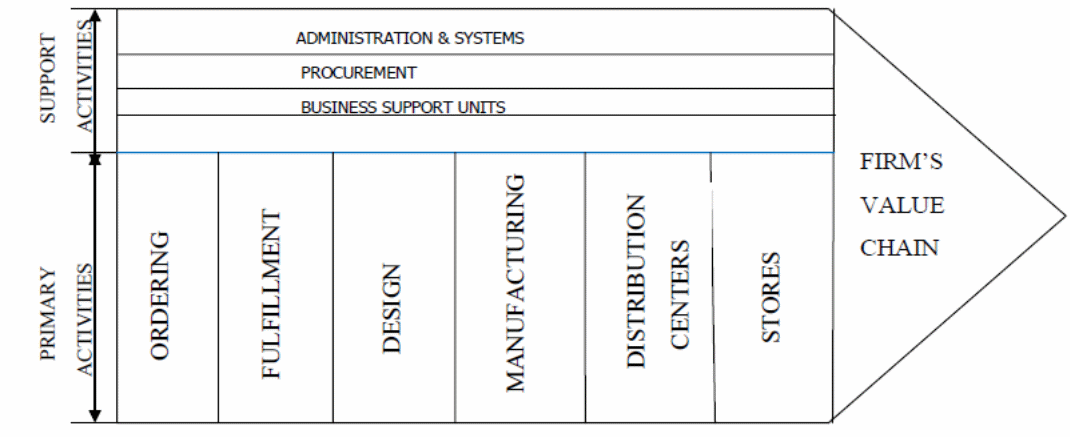
Source: Bhagwat (2011, p. 7)
The figure above shows the various activities performed by the company. The crucial activities include ordering, completion, designing and manufacturing. Among these activities, ordering is the most popular, specifically defined, and consistent around the globe (Bhagwat, 2011, p. 7).
Zara’s competitive advantage lies in its value addition in every stage right from production to marketing. The company has a decentralized structure and therefore the store managers are allowed to make decisions on behalf of the company (Ferdows, Lewis & Machuca, 2003, p. 63).
Inbound logistics, warehousing and stock control are done at the distribution centres (DC).Zara’s DC receives large volumes of inventory and distribute them to company’s stores all over the globe (Waarts & van Everdingen 2006, p. 645).
IT helps the company to keep track of the stock keeping units (SKU). The company’s distribution centres and the stock keeping unit control the outbound logistics (Ferdows, Lewis & Machuca, 2003, p. 65).
As mentioned earlier, the company has an internal IT department which is mandated to develop applications used in different operations. This department is managed by the company’s Chief Executive Officer (CEO) instead of the Chief Information Officer (CIO) (Bhagwat, 2011, p. 8).
IT is used both in the functional areas and in decision-making. Zara’s operating system is outdated, and as a result primary activities such as ordering, design and production are inefficient (Bhagwat, 2011, p. 9).
The PDAs are used for ordering, handling returns and conveying information to the headquarters (McAfee, Dessain & Sjoman, 2007, p. 9). The P-O-S terminals make it so hard for the staff to monitor incoming inventories, to verify stock in other stores, and share information among the stores.
In most cases, the store managers have to make a phone call to verify stock, which consumes a lot of time given the large volume of inventories handled by the company (Bhagwat, 2011, p. 9).
In addition, Zara has not taken advantage of the internet to market its products. The company has been criticized for using its website for display purpose only. The company is believed to rely too much on the word of mouth to market its products instead of advertisement (McAfee, Dessain & Sjoman, 2007, p. 9).
The company’s decentralized structure, where store managers make decisions on behalf of the CEO, deserves the best IT system to enhance efficiency and productivity. For this reason, the company has to invest heavily in a suitable IT infrastructure to enhance its value chain operations (Brïdson & Jody, 2004, 404).
Current position of the company
The company has maintained the use of P-O-S terminals based on DOS system up to date. The management argues that the current system is cost effective compared to other systems, for instance, it requires minimal maintenance and generally costs less.
Besides, the company has an internal IT department which develops applications that are compatible with the system. This IT department has less than 50 staff, which account for less than 0.45 percent of the total number of employees. They also argue that managing operations using the commercially available software is not easy (Bhagwat, 2011, p. 3).
Previously, the company used to make orders using a fax machine. At the moment they are using PDA which they consider effective (Capell, 2008, 66). Zara’s stores are not interconnected and therefore the employees have to make phone calls to check on the stocks. This not only increases phone costs and time wastage but also decreases the company’s productivity.
In addition, the lack of interconnectivity translates to lack of numerical data that can be used to make a comprehensive evaluation. In a nutshell, the current outdated IT infrastructure hinders the growth of the company through countless inefficiencies and information loss (Ferdows, Lewis & Machuca, 2003, p. 64; Bhagwat, 2011, p. 13).
Alternative Approaches
The company has two major alternatives for improving the current system and at the same time maintaining lower cost. First, the company can upgrade its system using the latest operating systems. Examples of the latest operating systems include UNIX, Linux (Ubuntu) or Windows 8.
According to McAfee, Dessain and Sjoman (2007, p. 10), the best option among the new operating systems with regard to cost is Linux since it has no one-time license cost. Both Windows and UNIX have one-time license costs of $145 and $160 respectively, therefore are relatively expensive. However, Linux has a relatively high ongoing cost, for instance cost of servicing contract.
Nonetheless, this cost depends on the knowledge of the company’s IT staff in the operating system. These costs are very important and must be considered by a company, especially Zara which has massive numbers of computers (McAfee, 2004, p. 19).
To improve the current system the company will also have to install latest hardware and replace the outdated P-O-S terminals (McAfee, 2004, p. 20). The cost of outdated P-O-S is currently above $6000, whereas the cost of wireless routers and Ethernet plus associated expenses per store connectivity will not cost more than $240. Even though this somewhat expensive in the short-term, the cost will go down with time.
The overall system upgrade will have tangible benefits to the company. It will enable the company to minimize general expenses, minimize operational expenses and enhance efficiency. In addition, the company can continue developing its own applications. System upgrade will also mean less IT staff and IT expenses (Bhagwat, 2011, p. 13).
The second and most recommended approach is the use of cloud computing. Cloud computing is a novel term in the computing world, but it is not a new concept (Catteddu & Hogben, 2009, p. 3). Cloud computing is an IT infrastructure delivered as a public utility where companies are allowed to pay for what they use. Computers and data can be accessed from any corner of the world.
In other words, the company does not have to install state of the art system or develop applications they only have to hire it at an affordable fee (Williams, 2010, p. 6). Cloud computing can be delivered as a platform, infrastructure or software depending on the client’s needs.
The three categories can be delivered in four deployment forms namely: private cloud, public cloud, hybrid cloud and community cloud. Cloud computing has no definite architecture and depends on the models used by the provider and the needs of the consumer (Catteddu & Hogben, 2009, p. 3).
According to Khajeh-Hosseini et al. (2010), the third party infrastructure presents numerous prospects for businesses to enhance the management of their revenues and information exchange.
Cloud computing improves cash-flow management given the fact that it reduces the overall costs and periodical billings as well as minimizing the inconsistency of expenditure on energy. It also assists companies to reduce administrative costs.
According to Miller (2009, p. 15), the pricing methods for data storage service depend on three distinctive characteristics namely: durability, accessibility and speed. Therefore, according to him the cost of cloud computing decreases with the number of the service groups. He also argues that the cost of cloud computing is twice less than that of the in-house data centres.
Williams (2010, p. 6) stress that small and medium businesses are the most suitable for cloud computing services. He argues that these businesses are incapable of developing huge data centres. Catteddu and Hogben (2009, p. 6) add that changes in the cloud computing cost variables come with new opportunities.
As said by Khajeh-Hosseini et al. (2010), cloud computing offers easy access to an organization’s computing and storage infrastructure via the web.
They also assert that cloud computing conceals the intricacy of information technology infrastructure management from the consumers and offers increased flexibility, steadfastness, soaring performance and specific configuration. All the above capabilities of cloud computing are offered at less cost in comparison to in-house data centres.
As already been mentioned, many businesses are migrating to cloud computing to save cost. Cloud computing provides cheaper and scalable data storage for these businesses; however, the biggest question that lingers in the mind of many people is whether the data stored in the cloud are secure.
Thus, the most imminent task for businesses is the security of data. In accordance with the survey conducted by Catteddu and Hogben (2009, p. 65), the biggest concern of many organizations is the security of cloud computing.
Security controls for cloud computing are almost similar to security controls in a conventional IT environment. However, cloud computing uses a divergent service model, functional model and technologies which present new types of risks (Cloud Security Alliance (2009, p. 19). The business IT security is normally tackled in different faces ranging from physical security, network security, system security, and application security.
The security responsibility of the cloud computing service providers and users depends on the type of model used. In most cases the cloud provider is responsible for physical security, environmental security and virtualization Security (Cloud Security Alliance (2009, p. 20). On the other hand, at the lower levels of the platform consumers are tactically responsible for the security, especially of the application and data.
Besides the architecture, there are other areas that must be taken into account when tackling security issues in cloud computing. Cloud Security Alliance (2009) divides these areas into two namely: governance domain and operational domain. Governance domain encompasses strategic and procedural issues, while the operational domain tackles technical aspects of the security and implementation within the architecture.
Governance domain takes in into account business risks caused by cloud computing, legal and electronic risks, and data management. On the other hand, operation domain consists of operational procedures used to tackle security, operations of data centres, incident handling and forensics, application security, encryption and scalability management, and virtualization (Cloud Security Alliance (2009).
Given the fact that cloud computing is generally implemented in large scale they are cheaper than other alternatives. Therefore, by embracing cloud computing Zara will enjoy better protection at an affordable rate (Catteddu and Hogben (2009, p. 17). Cloud computing also enhances the network effect of collaboration among different businesses using the service.
Other security benefits include multiple locations, edge networks, instant response, and improved risk management (Cloud Security Alliance (2009. With multiple locations the cloud computing providers have adequate resources to avert system failures and data recovery.
The edge networks avert the problems associated with local networks. Lastly, cloud providers have a large scale system that is able to respond to incidences in time.
Conclusion and Recommendation
Zara is among the leading brands in the globe and from a general point of view one would expect it to have the best management practices and state of the art IT system. However, this is not the case. The company has one of the oldest IT/IS infrastructure which is believed to have contributed to its slow rate of growth and inefficiencies.
Some experts believe the company could have been number one in the globe if it had had an upgraded IT system. The company’s management argues that the current system is cost effective compared to other systems, for instance, it requires minimal maintenance and generally costs less. However, in the real sense this is far from the truth.
Indeed, Zara has no alternative but to upgrade the current system. Their focus should be on the operating system and the terminals. Nonetheless, the best alternative is cloud computing which has been covered comprehensively in the report.
References
Azuma N, & Fernie J 2003, ‘Fashion in the globalized world and the role of virtual networks in Intrinsic fashion design’, Journal of Fashion Marketing and Management, vol.7, no.4, pp. 413-42.
Bhagwat, S 2011, Zara: IT for Fast Fashion Case Analysis, University of Houston, Victoria.
Brïdson, K, & Jody, E 2004, ‘The secret to a fashion advantage is brand orientation’, International Journal of Retail & Distribution Management, vol. 32, no. 8, pp. 403-411.
Capell, K 2008,’ Zara thrives by breaking all rules’, Business Week, 20 October, pp. 66.
Catteddu, D, & Hogben, G 2009, Cloud Computing: benefits, risks and recommendations for information security, European Network and Information Security Agency New York.
Cloud Security Alliance 2009, Security Guidance for Critical Areas of Focus in Cloud Computing, Cloud Security Alliance Inc, New Jersey.
Ferdows, K, Lewis, M, & Machuca, JAD 2003, ‘Zara Supply Chain Forum’, International Journal, vol.4, no. 2, pp.62-66.
Khajeh-Hosseini, A, Sommerville, I, Greenwood, D, & Sriram, I 2010, Research Challenges for Enterprise Cloud Computing, Submitted to the 1st ACM Symposium on Cloud Computing November 2010.
Kroenke, D M 2012, Experiencing MIS (3rd ed.), In Organizational strategy, Information Systems, and Competitive advantage, Pearson Education, Inc, Upper Saddle River.
McAfee, A 2004, ‘Do you have too much IT?’ MIT Sloan Management Review, vol.45, no. 3, pp.18-22.
McAfee, A, Dessain, V, & Sjoman, A 2007, ‘Zara: IT for Fast Fashion’, Harvard Business School, 1-23.
Miller, M 2009, Cloud computing: Web-based applications that change the way you work and collaborate online, Que, Indianapolis.
Porter, M E1980, Competitive strategy: Techniques for analyzing industries and competitors, Free Press, New York.
Porter, M E 2008, ‘The five competitive forces that shape strategy’, Harvard business review, vol.5, pp.78-93.
Thomas, RJ 2006, ‘Uncovering Zara’, Apparel Magazine, 27 January, p. 47.
Waarts E, & van Everdingen Y M 2006, ‘Fashion retailers rolling out across Europe, International,’ Journal of Retail & Distribution Management, vol. 348, pp. 645-657.
Williams, M I 2010, A quick start guide to cloud computing moving your business into the cloud, Kogan Page, London.