Introduction
The infrastructure that a firm puts in place defines the level of security that will be achieved in protecting data. Cyber insecurity is currently one of the main concerns of governmental and non-governmental entities around the world. In the United States, large corporations and government agencies are often attacked by cybercriminals who are keen on obtaining critical information for personal gains (Jagoda, 2016). As such, there is always an effort to ensure that data is protected from these criminals. Amazon is currently one of the largest companies in the world. The online retailer sells its products to the global market through its website.
Data security for this company cannot be compromised because of its business model. All transactions made by customers, from viewing the product, selecting what should be purchased, and making actual payments, are done on the online platform. It means that if a cybercriminal succeeds in penetrating the system, they can steal from the company and its clients with ease. As such, this company is always in a constant upgrade process, keen on ensuring that the security of its data is not compromised. In this paper, the focus is to discuss the relationship between infrastructure and data security as it relates to Amazon.
The Relationship between Infrastructure and Security
Investing in data infrastructure is one of the best ways through which a firm can ensure that its system is safe from any attack by cybercriminals. At Amazon, digital data is the core of business because of the model of operation the management has embraced. As the largest online retailer in the world, this firm cannot afford to have a situation where criminals or ill-willed individuals can have access to its database or information about its clients. As Sha (2016) notes, online retailers have to ensure that as they protect their own data from infiltration, they also have to protect the privacy and financial information of their clients. In this section, the focus will be on analyzing the current logical and topographical layout of the current network and proposing a new layout for this firm, which is more secure and easy to use for both the employees and customers of this company.
The rationale for the Logical and Physical Topographical Layout of the Planned Network
It is important to understand the rationale for the logical and physical topographical layout for the current and planned network. Logical topology, also known as signal topology, refers to “the arrangement of devices on a computer network and how they communicate with one another” (Ayyavaraiah & Gopi, 2017, p. 45). It is primarily concerned with how devices communicate with one another within the system. Physical topology refers to how physical gadgets (computers, tablets, and smartphones) are interconnected using cables, routers, and other devices (Ayyavaraiah & Gopi, 2017). In order to explain the rationale for upgrading the logical and physical layout of the network, it is necessary to look at the current system to help identify the weaknesses that need to be addressed. Figure 1 below shows the physical topographical layout of the current network used by the company.
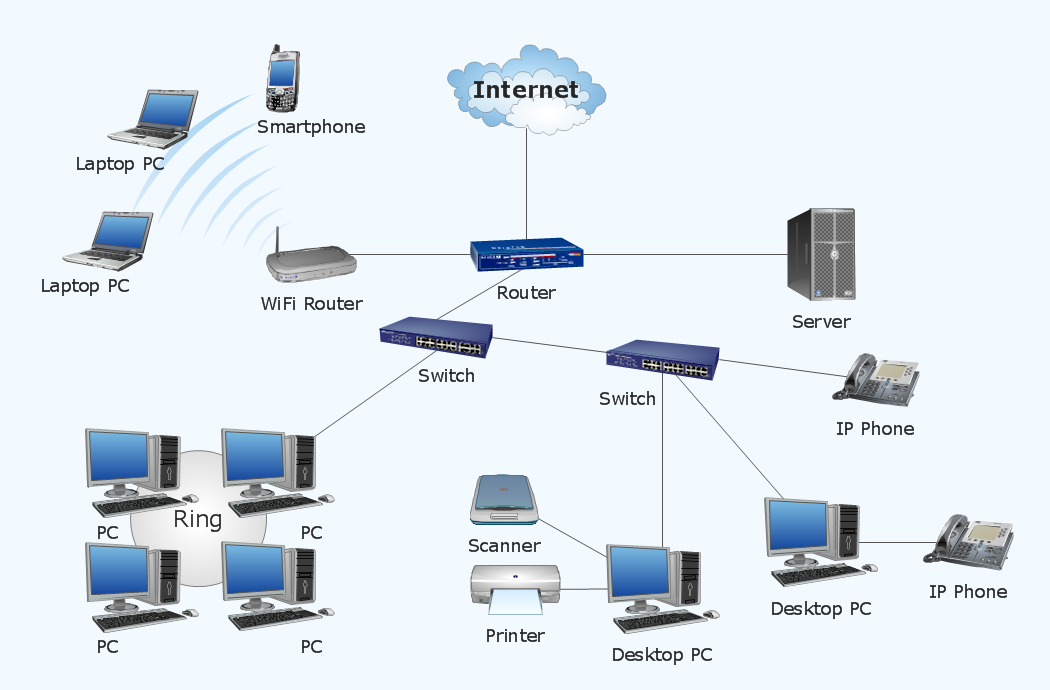
As shown in the figure above, the physical devices the company uses to facilitate data management include personal computers (which act as workstations), bridges, servers (which is the database), smartphones, switches, a router used to make information available in the internet, scanners, and printers. Once relevant information is made available, customers can use their personal computers, smartphones, and tablets to access the information with the help of a Wi-Fi router. It is evident that the company has invested a lot in ensuring that its employees have can communicate easily with customers and share data amongst themselves to enhance operational activities.
Once a client places an order, the information will be received by the company router from the internet and be made available to the relevant departments. A confirmation will be sent back to the customer informing them that their order is being processed and will be released for delivery once the payment is made. It takes a few seconds to process the information. The physical layout of the network shows that the router is the primary security wall that protects the company’s database. However, it is important to enhance the security system to make it more secure as the firm’s operations continue to expand. Figure 2 below shows the logical topological layout of the planned network. The focus of the new infrastructure is to improve the security of the company’s database and the privacy of its clients, which was identified as the facility’s main limitation.
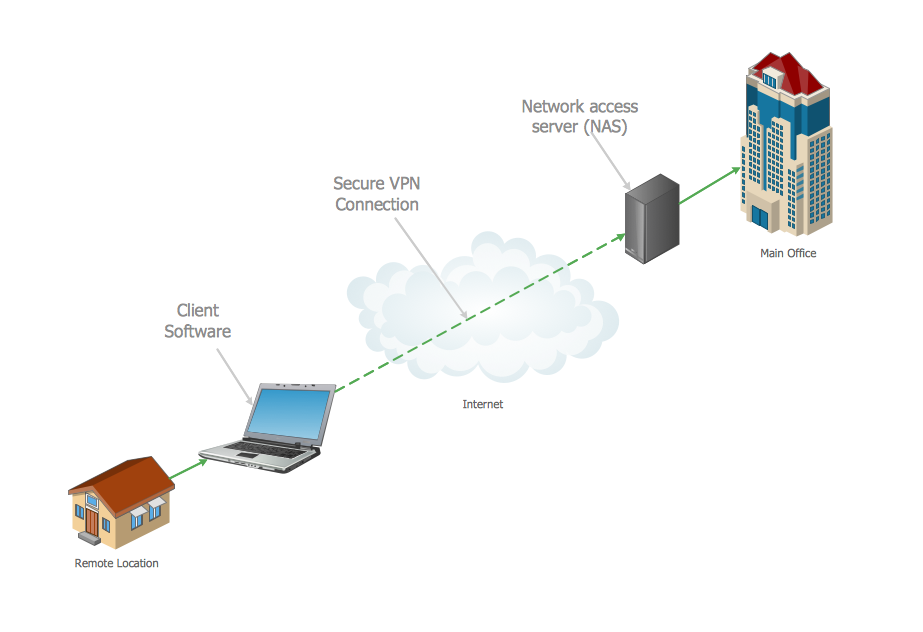
In the proposed logical topographical layout, there are two entities. On the one end is a customer in a remote location who needs the services of Amazon. On the other end is the company that seeks to offer services needed by the client. The two entities are connected through the internet. The client can use personal computers such as desktop and laptop or handheld devices such as a tablet or a smartphone to access the database of the company. The main difference between the proposed infrastructure and the previous one is that the new layout has two main security points. The first one is on the internet where the firm will need to use a secure VPN Connection. This was not used in the previous case. It is meant to add a layer of security to the current firewall at the network access server (NAS) at the offices of the company. The intrusion detection systems (IDS) should help determine when unauthorized individuals try to access the database of the firm. The proposed layout is benchmarked from best practices of the Central Intelligence Agency (CIA) that uses multiple layers of security to ensure that it protects its database from unauthorized individuals.
Comprehensive Security Policy for this Data-Collection and Analysis Company
When the firm has put in place an appropriate infrastructure to manage data, it is also important to have policies, which would guide the behavior of different parties involved in managing the information. According to Jagoda (2016), the CIA is one of the government entities that handle classified information that defines the country’s security. Its comprehensive policies have enabled it to ensure that information is not leaked to unauthorized individuals. Such policies would help this company in protecting its data. In order to protect the firm’s infrastructure and assets, the management would need to apply principles of confidentiality, integrity, and availability. The following regulations should be embraced:
- Employees of this company should be reminded that they have a moral and legal obligation to protect the confidentiality of the firm’s client. Using clients’ details for reasons other than what is authorized should be a reason enough for job termination and subsequent legal action.
- The firm should ensure that both the physical and logical topographical layout of the network enhances easy access to information for clients and employees.
- The integrity of data should be upheld by ensuring that there is always a backup system just in case cybercriminals succeeds in infiltrating the secured database.
The company should encourage all the relevant stakeholders to embrace ethical behavior as a way of enhancing further security. Customers and employees of the firm should have passwords, which they have to use when accessing information from the system. They should be reminded that such information should not be shared with third parties. Contractors assigned to work in the upgrade process or in any other department where they can access critical databases should sign confidentiality and ethical agreement forms that prohibit them from accessing and using information from the system without express authority from the management.
Conclusion
Amazon is one of the leading retailers in the world. The business model that the company uses, which is purely based on online transaction, requires a high degree of data security at all times. Cybercriminals often try to infiltrate the system to steal from the company or its clients. In this paper, the researcher has proposed an upgrade of the physical and logical topographical layout of the network system to enhance security. The new system will introduce an additional layer of security by ensuring that the firm uses a secure VPN connection. The management will also need to ensure that its employees, contractors, and any other person who has access to confidential information remain ethical at all times.
References
Ayyavaraiah, M., & Gopi, A. (2017). Database management system. Lansing, MI: Horizon Books.
Jagoda, P. (2016). Network aesthetics. London, England: The University of Chicago Press.
Sha, K. (2016). Security, privacy and reliability in computer communications and networks. Copenhagen: Denmark: River Publishers.
Vanderplas, J.T. (2016). Python data science handbook: Essential tools for working with data. Sebastopol, CA: O’Reilly Media.