Abstract
Aviation security is one of the most important concerns for the management units of major international airports around the world. The need to ensure the safety and security of passengers, cabin crew members, planes, and airport facilities have become greater than ever before because of the increasing relevance of air travel and the emerging threats posed by criminals and extremists. This paper focused on investigating aviation security at regional and international airports and what the local airport authorities can do to enhance it. The researcher collected secondary data from books, journal articles, and reliable online sources.
Primary data was obtained from a sample of participants. The findings from both sources show that the aviation sector faces numerous threats from terror outfits, criminal organization, and cyber attackers. Although local airports in the United Arab Emirates have not been subjected to serious attacks, the study recommends that the authorities should remain vigilant.
Introduction
The United Arab Emirate has one of the rapidly growing economies in the Middle East and North Africa region. According to Earley and Mosakowski (2016), the government has made deliberate steps to ensure that the economy is highly diversified to reduce overreliance on the oil and gas sector as the main driver of the economy. One of the main sectors of the economy that has registered an impressive growth in tourism.
The city of Dubai has emerged as one of the top destinations for global tourists, especially those from Europe and North America. The heavy investments that have been made in this area and improved security have boosted the city’s tourism sector. According to a report by Drabek (2014), Dubai is also the leading business hub in the region. Companies from the Far East and Europe consider it a gateway to Africa and the regional market in the Middle East.
The trend that is taken to diversify the economy of the country is crucial in ensuring that the country achieves sustained growth. The government is assured that the country’s economy will grow even after the rich oil reserves are depleted. The impressive economic diversification that the country has enjoyed is largely attributed to the improved air transport in the region.
Dubai International Airport is one of the leading global airports. Planes from and to various parts of the world can land and take off from this airport. Most of the airlines serving the African market use this airport as the first stop when travelling to North America. The Abu Dhabi International Airport is also playing a crucial role in the movement of goods and from and to different parts of the global market.
As Taneja (2016) observes, the impressive economic growth and diversification that has been witnessed in the country are largely attributed to the successful aviation system in the country. The country’s major airports have never suffered major incidents such as a terror attack or devastating criminal activities in the recent past. However, that does not mean they are immune to a possible attack. It is the responsibility of the government and stakeholders in the aviation sector to ensure that the security of this sector is considered a priority at all times. In this paper, the focus is to evaluate the security systems at the United Arab Emirates’ airports and determine their efficiency in the face of the emerging threats in the aviation sector.
Background of the Study
Aviation security is currently one of the leading concerns for airports all over the world. According to Tracy (2013), in the past, many airports and airline companies were focused on eliminating accidents and incidents because those were the main concerns. The leading aircraft manufacturers such as Airbus and Boeing have made tremendous advancements in the new airlines to ensure that they are easy to navigate and embrace advanced technologies that reduce malfunctions.
These advancements in aircraft manufacturing technologies do not mean airports and airline companies no longer have to worry about the possible accidents or incidents that may threaten the lives of passengers, crew, and safety of goods and aircraft. Malaysia Airlines Flight 370 that was flying to Beijing Capital International Airport from Kuala Lumpur International Airport, disappeared into the sky and has never been recovered. The fate of the plane and its passengers still remain a mystery to this day. It is a clear indication that even with the advanced technologies embraced in the construction of these planes, the security of the passengers is not guaranteed.
According to Triana (2017), aviation safety and security took a completely different turn following September 11, 2001, al-Qaeda attack in the United States. Before then, airport safety management was relatively relaxed. Measures were in place to ensure that passengers are screened to eliminate incidences where criminals would board planes with sophisticated weapons.
However, the ability of the terror group to plan and successfully execute one of the worse terror attacks against the United States was clear proof of the lapses that existed in the security system. The fact that one of the attackers was able to pass through the screening systems with a bomb wrapped around his waist was a clear testimony of the inefficiency of the measures put in place to screen passengers at the airport at that time.
The attack led to the loss of about 3000 lives, and it marked a major turning point in aviation security (Executive Office of the President 2014). Possible terror attack became one of the major concerns of airlines and airport management authorities. A raft of policies has been developed to enhance the screening of passengers and their luggage to eliminate the possibility of a similar occurrence in any part of the world. A report by Ulmer, Sellnow, and Seeger (2015) shows that the current measures put in place by the management of various major airports around the world have minimized the ability of criminally minded individuals to find their way into the planes with weapons of any kind.
According to Hamner et al. (2015), a new threat to airport security is emerging that is as serious as a possible terror attack. Cybersecurity is currently one of the biggest concerns in the aviation sector. Advanced technologies have made it possible for criminals to access and manipulate data used in flight management and airport traffic control. The digital platform has replaced the manual system in air traffic management and other communication activities within airports.
However, the threat of a possible cyberattack is causing worries to many major airports around the world. A report by Walker (2016) suggested a possible integration of the digital and manual systems to counter the threat posed by cybercriminals. However, integrating the two systems is still a challenge to many, especially given the benefits of the digital system.
The United Arab Emirates has five major airports that serve local and international customers. The Dubai International Airport is one of the busiest airports in the world and the regional aviation hub (Gooderham, Grøogaard & Nordhaug 2013). These airports are playing a critical role in enhancing a diversified economy in the country. The regional travellers prefer using this airport not only because of its efficiency but also enhanced security.
These local airports, especially the Dubai International Airport, have never experienced a major security breach in the recent past. However, that does not mean they are immune to a possible criminal or terror attack. Some of the neighbouring countries, such as Iraq, Syria, and Afghanistan, are struggling with political instability and the emergence of extremists such as ISIS (Haddow, Bullock & Coppola 2014).
There is always the fear that these terrorists may consider attacking regional airports or airlines as a means of punishing the west for their involvement in regional politics. It is in the interest of the authorities managing the local airports and airlines to ensure that security is maintained despite the emerging challenges. The only way of ensuring that these airports remain as busy as they are is to enhance security and thwart any form of criminal or terror attacks. The paper will investigate all forms of aviation threats that the local airports and airlines face and the means through which they can be managed effectively.
Statement of the Problem
On February 10, 2007, Etihad Flight EY42 that was travelling from Dublin Airport to Abu Dhabi International Airport, was instructed to reroute to Al Mini had Airbase in Dubai because of what authorities were convinced was a major security breach. Although no incident or a possible threat was identified after the screening, it was a major reminder to the stakeholders in this industry that the threat of a possible attack is real, and measures need to be taken to enhance the safety of passengers, crew, and security of the airports and planes. Dubai is currently one of the leading global cities in the fields of tourism and trade.
Hundreds of millions of passengers use the Dubai and Abu Dhabi International Airports every year. The ports also process goods worth billions of dollars. However, the constant threat of possible criminal or terror attacks is worrying. A report by Wu and Mengersen (2013) shows that the management of the airport is spending millions of dollars to enhance the security and safety of passengers, employees, cargo, and planes.
Although a major incident or accident is yet to be recorded, hundreds of thousands of cases of successful and attempted hacking have been reported over the recent past. It is an indication that even after making such investments in enhancing security, it is still possible for hackers to have access to airport and airline management data.
As Abeyratne (2013) observes, it seems that these cyber criminals seem to be a step ahead, and that is a real concern. The problem is worsened by the political tensions between the United Arab Emirates. Recently, the two countries accused each other of threats to civil aviation (Harrison & Sharpley 2017). In the past, the two countries worked closely alongside other neighbouring states to enhance regional aviation security.
It was easy to gather necessary intelligence that would be useful in fighting criminals and terrorists both on online platforms and direct physical threats. However, the two countries now view each other with suspicion. The recent accusations show that there is a possibility that one nation can sponsor and facilitate a security breach of another if the level of tension is not properly managed. Hays-Thomas (2017) warns that when terrorists or criminal minded groups are sponsored or directly supported by another state, they pose a grave threat because they can access all the resources they need, including military hardware.
The threat is even worse if the two countries are neighbours. It is very unlikely that Qatar can do that to the United Arab Emirates or vice versa. However, the current tension has worsened the security environment in the region. It is necessary to find a lasting solution to this problem, which targets one of the most important sectors of the country’s economy.
Justification of the Study
The research focuses on one of the most sensitive sectors’ of the United Arab Emirates’ economy. In the current globalized society, air transport plays a critical role in facilitating the movement of people and cargo from one part of the world to the other. The aviation sector is currently faced with the threat of possible criminal or terror attacks. The threat may be posed by criminals or terrorists who may want to stage a physical attack using bombs, guns, or any other means to cause mass murder and destruction. It may also come in the form of a cyber attack, especially given that the local airports largely on digitized systems to control various activities.
This study is important because it will highlight each of these challenges and propose possible solutions that may be employed based on emerging trends and technologies. Through this study, the management of the local airlines will have a better understanding of the challenges they have to deal with and measures that they may consider embracing to improve efficiency.
Research Objectives
Aviation security is a relatively wide area of study that has gained massive relevance over the recent past. This project will improve knowledge in this field by providing new insights into this area of study. After identifying the existing research gaps through the preliminary literature review, it was necessary to find ways of addressing them through this research. The following are the objectives that the researcher seeks to realize through the study:
- Evaluate the threats that airports face and methods adopted by the UAE to recognize and address them.
- Evaluate the extent of readiness of UAE airport security to handle major incidents.
- Identify methods used by international airports in the US and Europe and the extent to which UAE airport security systems match them.
- Make recommendations to fill gaps between international and UAE security systems.
Research Questions
The research objectives outline what should be achieved in a study and the questions identifying the specific data that should be collected to ensure that the set goals are realized. Tracy (2013) explains that research questions eliminate cases where one ends up collecting irrelevant data in a given project. It was necessary to have specific questions that were used in the process of collecting the needed information. The following were the research questions used in the study:
- What is the status of air security at UAE airports, and how it can be enhanced?
- What are the possible risks that UAE airports face?
- What are security systems used by airports across the world?
- In what areas should security be enhanced at UAE airports?
- What specific technologies and policies should UAE airports consider?
The researcher used both primary and secondary data sources to respond to the research questions above. The findings that were obtained from the two sources formed the basis of the conclusion and recommendations that were made in the study. The next chapter entails a detailed review of the relevant literature.
Literature Review
The previous chapter focused on a detailed background analysis of the research topic, a clear definition of the problem, and a justification as to why this research is relevant. The chapter also provided research objectives and questions that were used in the collection of data. In this chapter, the focus will be to review the literature relevant to this topic to understand what other scholars found out. Heng (2015) observes that it is prudent for one to avoid duplication of the existing knowledge new study because every research is expected to address the existing gaps in a given field of study. Aviation security is an area of study that has attracted the attention of many scholars over the recent past. It is necessary to review the existing literature in this field before collecting primary data.
Emerging Trends in Aviation Sector
The aviation sector is playing a critical role in enhancing globalization in modern society. Some of the emerging trends in the aviation sector are meant to improve the experience of travelling by air, reduce the negative impact on the environment, and enhance the security of the passengers. Wukich (2015) explains that airlines have been consistently working on ways of making their passengers comfortable, especially on long journeys that take over 5 hours.
The seats have been improved, and entertainment services customized to enhance the experience. Airlines are going green by trying to integrate the use of renewable energy alongside jet fuels. Of interest to them is to ensure that as the number of planes on air continues to increase because of the demand, the impact on the environment remains properly managed. The issue of security is also taking a centre-stage in the management of airports and airlines.
The threat of terror attack that targets airlines and airports is real, as was demonstrated by September 11, 2001, al Qaeda attack against the United States (Yip & McKern 2016). These are issues of concern that the current stakeholders are taking seriously. The next section discusses these issues and emerging trends in aviation security in great details.
The threat to Aviation Security
The aviation sector has undergone a massive transformation since the first commercial flight was made by St. Petersburg-Tampa Airboat Line on January 1, 2014 (Nevin 2016). In the initial years, the main concern of the stakeholders was the safety of passengers and the aircraft. The initial plans were not as sophisticated as the current ones. It heavily relied on the weather and skills of the pilots (Yuen 2015). However, that has been changing over the years.
Modern planes are highly sophisticated and can be piloted automatically, requiring pilots to do simple tasks. Cases of aircraft crashes caused by engine failures and pilot mistakes are becoming uncommon. In fact, the modern aeroplane is designed to withstand some of the worst environmental forces, such as strong winds. However, as these improvements continue to enhance air transport safety, new concerns are emerging. Security threats posed by criminals and terrorists are becoming of greater concern than accidents (Tracy 2013). It is important to look at the major threats to aviation security.
The threat of a terror attack
The threat of terrorist attack is becoming one of the primary concerns of airport management units across the world. The major breach of airport security by al Qaeda operatives when they attacked the United States was just a clear demonstration of the level of sophistication of these criminals when they are keen on achieving their heinous missions. On December 8, 2015, suicide bombers breached the security at Kandahar Airfield and engaged the security officers in a shootout (Nevin 2016).
The outcome of the attack was that 50 innocent civilians and security forces lost their lives. Less than a year later, on June 28, 2016, a group of terrorists invaded terminal 2 of Atatürk Airport in Istanbul, which is often used by international passengers (Ali et al., 2015). They included suicide bombers and snipers. The three attackers managed to kill 43 people and would 230 others before they were neutralized by the security forces. Brussels Airport suffered the same fate on March 22, 2016, when three terrorists breached the security and succeeded in taking 32 innocent lives (Sales 2017).
Recently, a passenger travelling from the United States on a Canadian visa attacked a security officer with a knife while yelling ‘Allahu akbar’ at Bishop International Airport (Triana 2017). Although there were no fatalities, it caused a major scare, delayed the flight as the passengers had to be evacuated for further screening, and reminded the local and international aviation sector of the loopholes that still exist in screening and inspection of passengers.
The fact that the attacker was able to pass through the security checks with a knife without detection was worrying. Other airports that have also experienced various forms of terror attack within the last decade include Orly Airport in France, Jinnah International Airport, Beijing Capital International Airport, Glasgow Airport, Frankfurt Airport, and Sabiha Gokcen Airport (Abeyratne 2016). The trend that the terrorists are taking is clear but highly unpredictable. Their main targets are major international airports across the world. Knowing where or when they are going to strike is almost impossible.
The threat of criminal attack
Major airports around the world have also witnessed cases of criminal activities over the recent past. Yuen (2015) explains that enhanced security at major airports has significantly reduced cases of robbery with violence that targets passengers. The systems and structures make it almost impossible for robbers to breach the security systems and attack travellers. However, other forms of a security breach by criminals who are not part of terror gangs have been reported. Kim Jong Nam, the half-brother of Kim Jong Un, the current leader of North Korea, was assassinated through poisoning at Kuala Lumpur Airport.
The investigation into the breach of security at the airport is yet to give a satisfactory report on how hired criminals were able to poison the North Korean despite the tight security details within the airport. Such sporadic attacks are a major concern in aviation security. Airports around the world are working on measures to ensure that the security of passengers, cargo, and aircraft is not compromised.
Cybersecurity threat
The cybersecurity threat is currently one of the leading causes of concern to many airports and airlines. As Alperen (2017) observes, emerging technologies have been beneficial to the aviation sector. Piloting planes has become simpler and safer than it ever was. Managing the airports and controlling air traffic has also been simplified. However, these positive changes are bedevilled by the increasing ability of criminals and terrorists to access online data.
Valero (2016) reports that hackers are bombarding the aviation sector with more than 1,000 attacks every month. The report notes that cases have been reported in the United States, Spain, Poland, Sweden, and Turkey, where aircraft are infected with security breaches or malware. Such incidences often lead to loss of information, delays, and public concern about security at these airports. Hensel (2016) explains that there are various types of hackers. Economic crime hackers are interested in stealing from airports and airlines.
The primary goal is to steal from these institutions. Terror-driven hackers are interested in taking control of aeroplanes and airports and causing as many deaths, damage, and destruction as possible. It is still not yet clear if Malaysia Airlines Flight 370 suffered such an attacked because it mysteriously disappeared from the sky and has never been traced. Taneja (2016) explains that some attacks are acts of espionage sponsored by other governments or institutions to gather intelligence.
Some hackers are working for rival companies and are focused on mining data needed by the competitors. Some just do it for fun without having any ill intention or a clear motive. Irrespective of the motive, any successful hacking into the data systems of airports or aeroplanes is a major breach that must be taken seriously and addressed effectively to avoid incidences or accidents.
State-sponsored security threats
Malaysia Airlines Flight 17, scheduled to land at Kuala Lumpur Airport from Amsterdam, was brought down while crossing the Russian-Ukrainian border on July 17, 2014, killing everyone on board (283 passengers and 15 crew members) (Triana 2017). A report released by NATO directly accused the Russian government of providing surface-to-air missiles that were used in bringing down the civilian plane.
The tension between the United States and Russia has been demonstrated effectively in the airspace. Andersen (2013) argues that the two countries have been accusing each other of breaches and cyber attacks in their aviation sector. In the Middle East, the tension between the United Arab Emirates and Qatar intensified after they each accused the other of espionage and compromising their national security (Triana 2017). State-sponsored security threats are rare but deadly. Hoijtink (2017) explains that the kind of resources that are always at the disposal of national security agents makes it dangerous for them to pose a security threat to another nation.
Airport security management lapses
According to Sales (2017), a significant portion of the attacks that have been witnessed in the aviation sector in the recent past is largely blamed on security lapses at the airports. One of the widely used examples of serious consequences of security lapses is the September 11, 2001, al-Qaeda attack. The fact that terrorists were able to smuggle dangerous weapons, including explosives, into the aircraft was an indication that the screening process was extremely poor.
A report by Holz (2016) shows that baggage handlers at Heathrow Airport have not been following the standard procedures of screening cargo and passenger luggage before they are allowed into the airport. Most of them are relaxed despite major incidences of a security breach that have been witnessed in various parts of the world. One of the funniest incidents happened when a Nigerian teenager hid in the wheel compartment of Med-View Airline Boeing 747 from Murtala Mohammad International Airport to Gatwick Airport in London (International Civil Aviation Organisation 2016).
When the opportunity to disembark from the plane was lost, the teenager remained in the compartment and travelled back to Nigeria. The authorities at both airports have not given satisfactory reports on how such a breach could go undetected at the two major airports. Baaghil (2015) laments that airport security management lapses are more common in developing nations than in developed countries. Poor or ageing screening equipment, underpaid and disgruntled security officers, and high levels of corruption have been blamed for such lapses.
The illegal goods on transit and human traffickers
Smuggling drugs from one country to another is a major issue in the aviation sector. These cartels have very powerful connections that enable them to facilitate the movements of their illegal merchandise without detection. The problem has been common in South and Central American countries where cartels are keen on smuggling drugs into the United States. In a recent case, Jamaican airline crew members were arrested trying to smuggle drugs worth hundreds of thousands of dollars (Chin & Trimble 2014).
It is worrying that these cartels have infiltrated the aviation sector and are now using employees of the airports and airlines to facilitate the transportation of their illegal merchandise to their desired locations. Beckhusen (2016) released a more worrying report that Sinaloa Cartel, one of the world’s largest drug trafficking and money laundering syndicate headquartered in Mexico, has more planes that Mexico’s national carrier.
It has hundreds or aircraft operating as cargo and passenger planes that facilitate the movement of their goods from one place to another. Other than the problem that these syndicates are breaking the law by trafficking contraband goods, their level of sophistication is worrying to stakeholders in the aviation sector. The level of infiltration and their financial muscle can enable them to breach any form of security both in the developed and developing nations. In case these criminals can form an alliance with terrorists, they can execute some of the worst attacks ever witnessed in the aviation sector because of their connections.
Radicalization and homegrown terrorism
A new trend is also emerging in aviation that is worrying as it poses a serious threat to aviation security. Howson (2017) explains that there is an emerging trend of radicalization and homegrown terrorism, a problem that many had not anticipated in the past. On March 24, 2015, first officer Andreas Lubitz deliberately locked out his captain on flight Germanwings Flight 9525 that was travelling to Düsseldorf Airport from Barcelona–El Prat Airport.
The first officer proceeded to crash the Lufthansa airline, killing 144 passengers and the six crew members on board (Bolman & Deal 2017). This was not an isolated case. Similar incidences had been witnessed in the past where pilots deliberately crashed their planes in acts of suicide or when working closely with terror groups. According to Sales (2017), LAM Mozambique Airlines Flight 470 had suffered the same fate.
The problem with this emerging problem is that it is not easy to detect or stop. These radicalized pilots do not need any form of weapon to commit their crime. They report to work as usual and are allowed into their plane as per their duty. It means that the screening at the airports and the use of sophisticated methods to fight security breaches cannot help in combating this form of crime. Rossi (2014) suggests that it may require close coordination between policy-makers, aircraft manufacturers, airport management authorities, and airline companies to find effective ways of battling the problem.
Managing Security Threats
The aviation sector has never been as critical to the global society as it is today. Hyndman and Hyndman (2016) argues that about 8 million people travel by air daily, which translates to over 3.1 billion people every year. Security has become a top priority among players in the aviation sector. As this industry becomes crucial to the international community, it has attracted the attention of terrorists and criminals. As such, emerging trends in this industry increasingly focuses on enhancing passenger safety and cargo security. It is important to find ways of enhancing passenger and cargo safety despite the numerous emerging problems that the industry currently faces. The following are some of the strategies currently used in enhancing safety and security in the aviation sector:
Improved screening systems
One of the best ways of addressing the current aviation security concerns is to improve the screening systems. Some of the terrorists who succeeded to penetrate the security systems at various airports in the past did so because of the poor screening systems. According to Taneja (2016), the current international aviation laws restricts passengers from boarding planes with guns, explosives, knives, or any other object that can act as a weapon. Using state-of-the art screening systems, it is possible to determine any object that a person may be hiding while passing through security checks.
Other than the full-body scan, the travelling bags and other belongings of the passengers should be inspected thoroughly to ensure that the risk of smuggling any form of the weapon is eliminated. As Johnstone (2015) advises, it is necessary to ensure that the threat of a passenger using weapons while on the planes should no longer be a possibility if the screening systems work effectively and security officers remain committed to their job.
Intelligence sharing by regional and international partners
According to Conyers and Kiyuna (2015), intelligence sharing is one of the most effective ways of fighting threats posed by criminals and terror suspects around the world. Many airports have embraced the use of biometric systems in managing security.
The system can be enhanced to read, analyze, and store faces, besides other details such as name and identification number. When a government agency suspects that an individual is a potential terror suspect, it should share the information with all the airports that the individual is likely to use when travelling. Once the information is received by the initial airport, the passenger should be treated as a person of special interest. His or her luggage should be inspected thoroughly, and the security officers should ensure that the individual does not carry any form of weapon.
The flight booked by such a terror suspect should also be subjected to thorough screening to ensure that there is no form of collusion between the individual and employees of the airport or airline to facilitate the smuggling of weapons. All passengers boarding that flight should be screened appropriately, especially those identified to be closed to the suspect. Once the plane takes off, the management of the airport of origin should alert the management of the airport where the plane will be landing of the high profile nature of the traveller.
The data of such a passenger should remain in the biometric database of these airports so that they can easily identify him or her when making other trips. Kahan (2015) reiterates the importance of sharing information among airports and governments. Once vital information has been obtained about a potential threat, all the relevant stakeholders should be engaged to ensure that the safety of passengers and crew members and security of the airport and aircraft are maintained.
Embracing international standards in aviation security management
The International Civil Aviation Organization (ICAO), working closely with other international civil aviation authorities such as the International Air Transport Association (IATA) and Airports Council International (ACI), has come up with policies and standards that should be observed by airports and airlines around the world (Cuervo-Cazurra et al. 2014). One of the areas that the new standards put emphasis on is the need to maintain regular training among security officers. Threats to the security of airports and airlines keep changing with the advancements in the field of technology. Officers charged with the responsibility of maintaining the security of the airports should be properly equipped with skills that can enable them to thwart various security threats.
Triana (2017) says that it is necessary to ensure that these officers go through some form of training after every two years to enhance their skills. ICAO also emphasizes the need to use emerging technologies when screening passengers and inspecting cargo.
A Biometric system that can recognize the faces of travellers is becoming a common best practice around the world. Rossi (2014) also explains that ICAO has set guidelines that airport and airline management units should follow to ensure that their employees do not turn into potential terrorists or sympathizers of extremist groups. The body has recommended that employers in this industry should ensure that their employees are motivated and their concerns addressed in time. Any suspicious activities of these officers, especially pilots, security agents, and air traffic controllers, should be noted, and appropriate action is taken to avoid calamities.
Advanced computing technologies to manage cyber threats
The international civil aviation bodies can set standards that each airport and airline companies need to follow. However, Taneja (2016) states that the management unit at each airport and each airline must take initiatives to improve security at their own facilities. It is important to understand that unique socio-political factors in a given region make security concerns vary. In an unstable country such as Syria, the threat of infiltration and attack is higher than it is in Switzerland.
If the management of the Syrian airports solely relies on the recommendations of the international aviation bodies without addressing the serious local dangers, then it may be open to attacks from these terror groups. Advanced computing technologies can help in addressing unique security concerns. SAS Cybersecurity is one of the cyber analytical tools that have proven in enhancing security, even in highly challenging environments. The system is capable of processing data rapidly to help in predicting potential attack based on the gathered information. It offers guidance on issues about security that the management needs to take care of within a given setting.
Improved training of cabin crew on security management
Regular training of the security agents and cabin crew members is critical, and it forms some of the recommendations made by ICAO as a means of improving security at the airports. Sichuan Southwest Vocational College of Civil Aviation in China has introduced Kung Fu classes to empower its crew members. The classes are meant to ensure that the crew members acquire martial arts skills to physically combat criminals or terror suspects who may attack colleagues in the plane.
The approach may need to be embraced in the region and should extend to the security officers. Other than having skills in the use of firearms, the officers should be quick and capable of responding to various threats within the shortest time possible. The security officers and the cabin crew should also understand how to share data relevant for maintaining security. Intelligence sharing among airport employees can thwart terror attacks. Kaplan (2016) suggests that the slightest suspicion of a possible terror attack should be reported to the relevant security agents instead of ignoring it. When these airport employees are equipped with a high level of skills, they will know how to respond whenever there is a potential threat.
Passenger awareness about security breach detection and response
Intelligence is critical in enhancing aviation security. Critical information about a potential security threat may come from passengers. In many cases, terror suspects and criminal elements often pose as normal passengers. They mingle with other passengers during the screening process and after boarding the planes. Kazda and Caves (2015) believe that passengers are in the best position to detect abnormal behaviour of individuals standing or sitting next to them.
They are also best positioned to take immediate action when necessary to thwart attempts by these individuals to cause harm. Sylves (2015) advises that it is more appropriate for such passengers to report such suspicions to relevant authorities instead of taking actions into their own hands. They can only take actions in cases when it is clear that a minute wastage may be too much to save a fellow passenger or entire plane and its passengers.
It is necessary to take these passengers through a brief session on how to detect security threat and the right action that one should take. They should be provided with an effective platform for reporting the potential threat. When it is unavoidable, they should know how to act to prevent criminals or extremists from taking actions that may have serious consequences to passengers and crew members.
Thorough cargo inspection
On October 29, 2010, a tip from the Saudi Arabian crown prince, Muhammad bin Nayef, to the American authorities helped to frustrate attempts by al-Qaeda to attack O’Hare International Airport in Chicago (Daft & Samson 2015). The terror group had succeeded in concealing a bomb as part of cargo from Yemen to New York using cargo and commercial planes. The quick action taken by the international authorities after getting the tip made it possible for the explosives to be intercepted at the Dubai and East Midlands Airport international airports.
Without the tip from the Saudi authorities, the bomb would have caused a devastating impact in the aviation sector, especially the one that was being transported by the passenger plane. It was an indication of poor cargo inspection at major airports around the world. Margulies (2017) says that international airports need to embrace sophisticated technologies to inspect cargo before they are loaded into the planes. It is also necessary to have highly trained security agents and sniffer dogs to ensure that nothing is left to chance.
Theoretical Framework
It is important to look at the relevant models that can enhance the security of airports and airlines across the world. Laroche and Yang (2014) warn against embracing conspiracy theories because of the fact that they are always based on personal beliefs and perceptions instead of evidence. Whenever there is a security scare, potential threat, or an actual attack, conspiracy theories should be avoided at all costs.
The investigation should be based on hard evidence, witness accounts, and reports from the investigators. It is also important to embrace quality models in the management of airports. International Organization for Standardization (ISO) certification is becoming popular around the world as a way of improving quality in the management of large organizations (DeLange, Samoilovich & VanDer 2013).
Markov model is also becoming a common predictive tool at various airports. It makes it possible to predict possible attacks so that counterattack measures can be taken. Although some security experts have criticized the effectiveness of this model in managing security in sensitive places such as airports, Maktoum (2017) explains that it can help in eliminating sporadic attacks that cannot be tracked easily by the conventional security management systems. The next chapter will focus on a detailed analysis of the methods used in data collection.
Methodology
The previous chapter of this dissertation provided a review of the literature. In this chapter, the focus will be to provide a detailed analysis of the method that was used in collecting data for the study. The researcher used both primary and secondary data sources to inform the study. Secondary data was obtained from books, journal articles, and reliable online sources. Findings from these sources have been discussed in the literature review section above. Information obtained from these sources was also used in the discussion chapter of the dissertation. Primary data was obtained from a sample of respondents. Given that the researcher was keen on addressing the existing literature gap, information from primary data formed the basis for analyzing the questions that were set in this project. This chapter provides a detailed analysis of the methods used to collect and analyze the primary data.
Research Philosophy
According to Brennen (2017), research philosophy focuses on the source, nature, and approach taken in the development of knowledge. It is the primary belief that a researcher embraces the manner in which data regarding a phenomenon under investigation should be collected. The philosophy that a researcher embraces defines the assumptions and beliefs that will be made throughout the study. It defines the pattern that a researcher must embrace when collecting the relevant data. As shown in the research onion below (figure 1), it is the first step that should be taken when determining the assumptions to be embraced. It is in the outermost layer of the research onion.
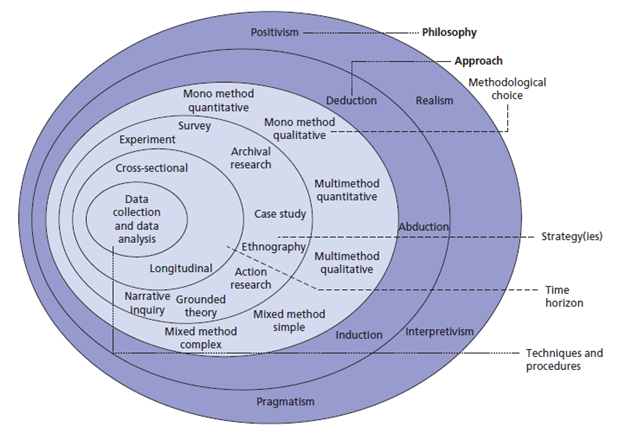
As shown in the figure above, a researcher can choose any of the four possible philosophies to guide the process of data collection and analysis. Örtenblad (2016) advises that it is critical for one to ensure that the chosen philosophy is in line with the goals and objectives of the project. It is prudent to discuss each of the four philosophies briefly before stating the one which was considered most appropriate for the research.
Pragmatism
Pragmatism is a research belief that holds that a concept can only be accepted to be relevant if they support actions (Bryman & Bell 2015). The philosophy holds that different people can interpret the world in different ways based on the approach that they consider relevant. It is unfair to insist on a specific way of viewing realities in society. As such, people should be pragmatic enough to accept the views and versions of their colleagues about their views about the world.
The only guiding principle of accepting one’s argument should be the capacity to support action. The interpretation that one pushes forward should be practical irrespective of the approach taken. As Eriksson and Kovalainen (2015) observe, this philosophy allows researchers to take different approaches to data collection, analysis, and interpretation as long as the chosen approach supports action. It is popular philosophy, but it was not used in this study.
Positivism
Positivism, as research philosophy, holds that knowledge can only be considered factual and trustworthy if it is gained through observation and the use of measurement. It emphasizes the need for a researcher to embrace the role of data collection and interpretation objectively without allowing their knowledge or biases to affect the entire process (Saunders, Lewis & Thornhill 2015). The primary argument in this physiology is that people tend to be biased when conducting research.
They often desire to have a given outcome that is in line with their beliefs, knowledge, or personal interests. Hair (2015) warns that getting into a research process with a fixed mind and with the goal of having a given pattern of response is dangerous. It defeats the very purpose of the research itself. As such, one should be committed to remaining objective and unbiased even if the outcome of the study shows a complete opposite of what one expected (Yanow & Schwartz-Shea 2014). This philosophy emphasizes the use of statistical methods when conducting the analysis. It is a good philosophy for a research such as this, but it was not embraced.
Realism
The fundamental belief of realism as a research philosophy is that reality is independent from human mind. What people believe or embrace may not necessarily be the truth. As such, it is necessary to conduct experiments to determine the validity and relevance of a given issue under investigation (Reis & Judd 2014). The philosophy is popular when conducting research in pure sciences. It uses various scientific instruments to facilitate collection and analysis of scientific data. The knowledge of the researcher or personal beliefs may not matter in such analysis. The primary concern is the outcome of the analysis conducted. The research belief was considered inappropriate for the study.
Interpretivism
Interpretivism holds the belief that knowledge is constructed through the interpretation of the world by the researcher. Unlike pragmatism that strictly limits a researcher to an independent observer, Interpretivism allows a researcher to integrate realities, experience, and interest into the study (Nestor & Schutt 2014). A doctor who is assigned a task of conducting a research about the challenges that farmers face may not do an excellent job as a farmer would because of lack of interest. As such, it is not possible to ignore the interest of the researcher on a given study. Philosophy also holds that knowledge and experiences of a researcher cannot be ignored. A senior security officer may be able to determine whether a response given by a specific participant is misleading or not (Pierre & Jackson 2014).
It may be possible that the respondent answered the question without necessarily having expert knowledge on the issue. Forcing such a researcher to analyze such misleading data and provide conclusion and recommendations based on them is unfair. A researcher should be allowed to interpret the presented data, but in a way that makes sense. Interpretivism was considered the most appropriate philosophy based on the research objectives.
Research Approach
The next step after identifying the appropriate research philosophy is to select research approach. Principles of the approach selected must be in line with the major assumptions and beliefs of the philosophy. According to Pierre and Jackson (2014), a researcher can use deductive or inductive reasoning based on the nature of the research. Each of the three approaches may be relevant in different contexts.
Deductive
Deductive reasoning starts with identifying a theory that is used in the development of a hypothesis. Robinson (2014) says that this approach is appropriate when one wants to confirm the validity of a popular concept. The developed hypothesis is often analyzed using statistical data to confirm its truthfulness. It can be confirmed or rejected based on the findings. The researcher did not consider it to be appropriate based on the nature of the study. As such it was not used in this research.
Inductive
Inductive reasoning takes a complete opposite of the approach taken in deductive reasoning. Instead of starting with a theory, it starts with observation. It requires a researcher to come up with objectives then conduct observation (gather evidence) to achieve the set objectives. It emphasizes the need to come up with tested laws and principles instead of generalized ideas (Neal 2016). In this study, the researcher considered it appropriate to use inductive reasoning. Figure 2 below shows the pattern that is often taken when using this research approach.

The approach was selected because it was necessary to investigate security threats in the aviation sector and come up with valid recommendations that can be implemented by the relevant institutions. The researcher was not interested in making generalizations but coming up with effective solutions to the current security threat in the aviation sector.
Research Strategy
After defining the research philosophy and approach relevant to the study, it is important to discuss the research strategy. The strategy should be capable of meeting the research objectives. Mixed research method was considered the most appropriate for the study. The researcher used semi-structured approach in order to facilitate statistical analysis of data but in a way that allows the respondents to provide further explanation to their statements whenever it was necessary. The closed-ended questions made are possible to collect data in a structured format for the purpose of analysis.
This approach of analysis was critical when analyzing the magnitude of varying threats to aviation security. As Kahlke (2014), when analyzing various variables, it is important to note that some variables have greater impact than others in a given setting. The magnitude of threat that is posed by a terror outfit is far greater than the threat of a person keen on stealing a luggage from a fellow passenger. Although both vices are undesirable and the managements of the airports and airlines are keen to avoid them, the consequences of a terror attack are by far greater than that of theft of property. The structured format of questioning the respondents also made it possible to have a standard approach of asking and answering the questions. It simplified the process of coding and analyzing primary data.
It was equally important to obtain some detailed explanations from the sampled respondents on specific issues. As explained below, the participants in this study are individuals who have knowledge and experience in aviation security (McNabb 2015). They have the capacity to give informed opinion on specific issues regarding threats that airports and airlines face and how these threats can be managed. As such, unstructured questions were needed to enable them to provide a detailed explanation about specific issues of concern. The need to have both approaches when analyzing data was advisable because of the need to provide justification to the statistical data. It was also needed to facilitate an effective integration of primary and secondary data.
Sampling and Sample Size
The time available for the research and the availability of the respondents made it necessary to select a sample of respondents to take part in this study (Gitterman 2014). The researcher wanted to collect data from two categories of people. The first category is the airport security officers from various airports in the United Arab Emirates. These officers have a responsibility of ensuring that any security concern in the airport is addressed.
They range from the officers responsible for the screening of passengers, those that inspect the cargo and luggage of the passengers, those manning various security points, and any other officer tasked with ensuring that physical security of the airport, planes, passengers, crew members, and employees of the airports is maintained. The second category of the participants include the IT experts who are tasked with responsibility of dealing with cyber threats posed by cybercriminals, terrorists, and other unauthorized individuals who may want to obtain critical data used in managing the airports.
A stratified sampling technique was considered appropriate in collecting and analyzing data from these individuals. The two groups formed two strata used in the collection of data. In each stratum, the researcher used simple random sampling to identify specific participants for the study. A sample size of ten respondents was considered appropriate based on the availability of these officers and the limited time within which this study had to be completed.
Data Collection
Primary data collection involved engaging the sampled participants in a face-to-face interview. First, the participants were contacted on phone and the relevance of the study explained to them. The researcher explained the role they were expected to play and reasons why they were chosen to be part of the study. The researcher went ahead to book varying dates to meet with each of the selected respondents. Katz (2015) says that it is always important to have a face-to-face interview because it increases chances of obtaining complete response. The physical presence of the researcher increases chances of the respondents answering all the questions.
It also reduces chances of providing misleading answers. Sometimes the respondents may be tempted to lie because of their personal interests or fear of repression because of their varying views from that of the rest. When a researcher is physically available, the respondents may not have time to develop an appropriate lie. Fraga (2016) also notes that face-to-face interviews also makes it possible to explain the concerns that some of the respondents might have. The researcher developed a simple questionnaire to facilitate the process of data collection from the respondents.
Instrument of data collection
It was necessary to have a careful plan before going to the field to collect data from the sampled respondents. Given that the analysis of data required some form of statistical approaches, it was necessary to standardize the responses obtained. As such, the researcher considered it appropriate to develop a simple questionnaire to facilitate the data collection process. The questionnaire used in this study had three parts. The first section focused on the background of the respondents. Issues such as age, gender, and special interest were captured. Capturing these demographical factors may help in determining any form of bias that might exist in the responses obtained from the participants.
The second section of the questionnaire focused on the academic background and experience of the participants in their respective fields. Bendassolli (2013) says that highly educated and experienced individuals are often considered to have a greater authority to provide trusted response on specific issues. The last section of the paper focused on specific questions regarding aviation security and how it can be enhance within the local airports. A sample of the questionnaire is attached in appendix 1 of this document.
Data Analysis
Data collected from the primary sources was analyzed both qualitatively and quantitatively. Quantitative data analysis helped in determining the prevalence of specific threats to aviation security and the magnitude of their impact (Fowler 2013). Some threats are more common than others. Similarly, the occurrence of some risk factors may have crippling effect on the operations of the airports while others can easily be managed. Statistical methods made it possible to provide such clarity in the analysis. Closed-ended questions were used to facilitate this approach of data analysis. The researcher also used qualitative analysis in addressing the issue under investigation. With the help of open-ended questions, the researcher was able to get the expert opinion of the respondents on various issues relating to aviation security. Their explanations were integrated in the analysis of the results.
Ethical Consideration
According to Alsos, Eide, and Madsen (2014), when conducting research, it is important to embrace ethical requirements set by relevant authorities. One of the most important issues that were taken into consideration was the need to get permission from the management of the chosen airports before contacting their employees. Aviation security is a critical issue and when a researcher intends to get such information from airports, Bernard (2013) advises that it is prudent to get the relevant permissions. The participants were only contacted after obtaining the relevant management approval. The researcher took time to explain to every participant the relevance of the study and their role in it. All their questions and concerns were addressed before proceeding with the process of data collection. The respondents were informed that they were at liberty to withdraw from the study at any stage without facing any consequences.
Brennen (2013) explains that one of the most important ethical requirements in many forms of research is the need to protect the identity of the respondents. This is necessary to ensure that in case the response given by a participant is not part of the popular opinion, he or she will not be subject to any form of prejudice or any other consequence directly arising from their involvement in the research (Card 2016).
In this study, the identity of the participants remained anonymous. The questions were structured in a way as to ensure that they do not go against the principles and beliefs of the local society. It was also academically ethical to avoid plagiarism and all forms of academic malpractice. The researcher ensured that the document produced was original and any information obtained from secondary sources was properly referenced using the Harvard style. The research was done and completed within the set deadline and the document delivered based on the instruction provided by the instructor.
Practical Constraints
It is necessary to briefly look at the constraints that were faced in this study. One of the major issues faced in the research was the unwillingness of most of the targeted individual to get involved in the study. Many responded to the request by explaining that their roles are so sensitive that they cannot ethically engage in this study. Others simply turned down the request without giving any explanation.
The researcher was able to overcome this challenge by contacting other potential participants. Time available for this study was limited to the timetable set by the school. It was not a great challenge as the researcher was able to complete all the activities within the set deadline. It was also very challenging to have successful face-to-face interviews with some respondents. In some cases, the interviews were interrupted by urgent duty calls and had to be rescheduled. Through persistence, the researcher was able to gather the needed data from all the identified participants. The next chapter will provide an analysis of the findings obtained from the sampled respondents
Analysis of Findings
In the previous chapter, the researcher provided background information about the method used in data collection and analysis. In this chapter, the focus will be to present the findings made from the analysis. The questions were analyzed both quantitatively and qualitatively. The first question focused on determining if passengers are scanned for bombs and contraband goods. The figure below shows the outcome of the analysis.
- Passengers, males, females, children, babies are very thoroughly scanned for bombs, contraband, and other unauthorized items
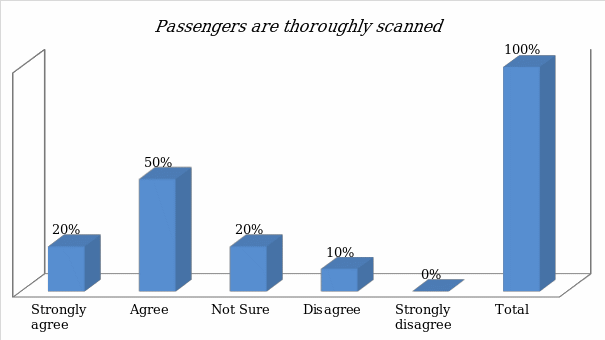
The outcome shows that majority of the respondents feel passengers are often scanned for bombs and contraband goods. The next question focused on determining whether the local airports conduct effective passenger verification when issuing the boarding pass.
- Passenger verification is done when issuing the boarding pass
Data was collected from sampled respondents. Figure 2 below shows the outcome of the analysis of the primary data.
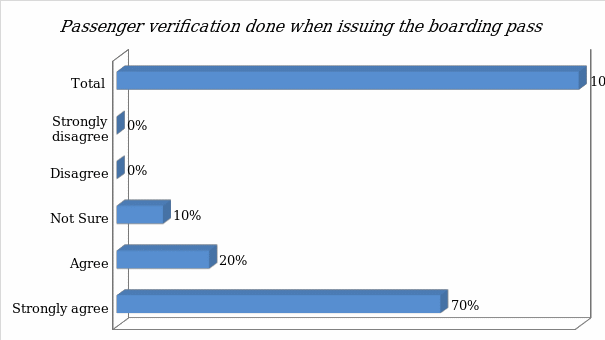
The analysis of primary data shows that majority of participants agree with the statement that passenger verification is often done when issuing boarding pass. The next question focused on determining whether the local airports conduct proper passenger verification when tickets are issued.
- Passenger verification is done when tickets are booked
The respondents were requested to state their views based on their experiences. The following figure shows the outcome of the primary data analysis.
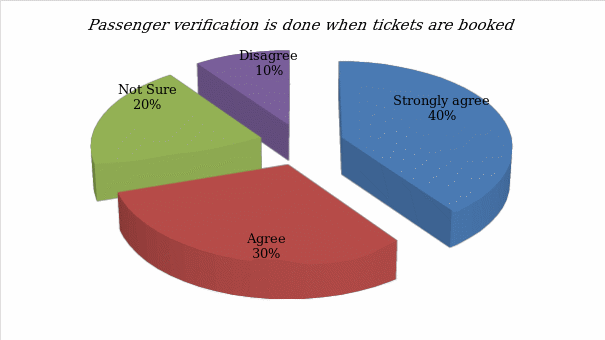
It is evident that the majority of the respondents feel passenger verification is done when tickets are booked. The next question focused on determining if passenger verification is done with cross reference to criminal databases.
- Passenger verification is done with cross reference to criminal databases
The information collected from the respondents was analyzed mathematically. The figure below shows the outcome.
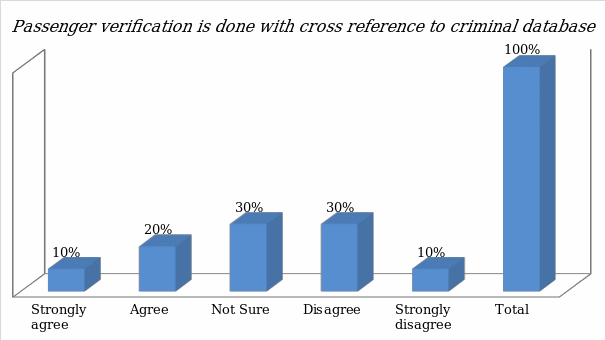
The outcome shows that the majority of respondents are not convinced that passenger verification is done with cross reference to criminal database.
- How effective are the passenger scanning methods used in UAE airports?
The majority of respondents feel that passenger scanning at the local airports is done in an effective manner. Although they felt that there are some weaknesses that need to be addressed, they were convinced that enough is being done to address the security concerns.
- How much time is spent for scanning each passenger and is this sufficient?
When asked the time that it takes to scan each passenger, most of the respondents stated that the average time is about 120 seconds. They felt that with the modern technology, the time is sufficient to scan the passengers.
Discussion
The previous chapter provided a detailed outcome of the analysis obtained from the sampled respondents. In this section of the research, the focus will be to discuss the findings from primary data, triangulating it with the information obtained from the secondary sources. The primary data analysis shows that aviation security is a major concern in the country. The government of the United Arab Emirates has invested billions of dollars in expanding different airports in the country to international levels. The Dubai International Airport is currently one of the largest and busiest airports in the world (Marschan-Piekkari, Welch & Welch 2014).
The Abu Dhabi International Airport has also received major renovation and expansion and is playing a major role in facilitating movement of people from the country to other parts of the world and back. The impressive growth of the country’s air transport sector, as Maszka (2017) observes, was not an accident. It was a deliberate effort that involved major financial and time investment to achieve what the country currently enjoys. The issue of aviation security will need the same approach to realize the same success. The government and all the stakeholders in the aviation sector must understand that they have a role to play in enhancing security in the airports and airlines.
It is important to note that Dubai and Abu Dhabi international airports have never recorded major terror attacks in the recent past. However, that does not mean they are prone to such attacks. A report by McHoes and Flynn (2017) show that although airports in the UAE have not been subject to major terror attacks, they remain vulnerable and measures need to be taken to prepare the local stakeholders in case such an attack may occur. Stahl et al. (2016) says that cases where active bombs and explosives are transported through this airport have been reported in the past, which is an indication that that a potential attack is a possibility. The level of sophistication of these criminals is also a further warning that the security of these airports can no longer be taken for granted.
Dubai International Airport is a regional hub, critical for planes from North America to Europe, Middle East, Far East, and various parts of the world. It is responsible for the movement of tourists from all over the world to the country and back. The fact that the airport has not experienced a major security breach and a terror attack is a major assurance to the local and international community about the safety of the airport. However, any attack on any of the major local airports can have devastating consequences. These are some of the reasons that make aviation security in the country a primary concern not only to the players in the aviation sector but also those in tourism, hospitality, travel, and real estate sectors among others.
Identification of Aviation Security Threats
The importance of the aviation sector to the country’s economy is enormous, and the security of this sector cannot be taken for granted. The information obtained from the review of the literature demonstrates that criminals and terror outfits are increasingly becoming sophisticated. Cyber attacks targeting airports have become common and it is feared it may become serious in the time to come. The findings obtained from the primary sources appreciates that the local authorities have done a lot to enhance security at the airports, but cases of security lapses have been witnessed in the past. In this section, the focus will be to determine how the airports can identify security threats.
Having sophisticated screening systems
The information obtained from primary and secondary data sources strongly suggests that there is a need to enhance screening of passengers as a way of identifying a potential security threat at the airports. One of the issues that the respondents identified as a major threat to aviation security is the limited inspection of passengers and cargo. The same problem was also stated in the review of literature. Most of the terrorists and criminal elements pose as innocent passengers. McLoughlin and Aaker (2014) explain that it is rare for these ill-intentioned individuals to announce their motive on arrival at the airport.
They often try to remain as calm as possible to avoid detection. It is the responsibility of the security officers and the screening systems to identify these individuals. Mor-Barak (2014) explains that the screening process should be broadly categorized into three stages in the airport. The first category should focus on the effective screening of passengers to determine whether they are carrying any form of weapon, however simple it may be.
A new imaging system that scans the entire body has become popular in many airports because it addresses the lapses common with the previous systems that relied on human intelligence. The second stage of screening should be the facial scanners that can detect an individual who is already in the database as a criminal element, a terror suspect, or a sympathizer of terror groups. The goal of this facial reader is to identify people who are classified as high-risk passengers hence should not fly. When such an individual is identified, the management of the airport, working closely with the relevant airline company, should decide the fate of such a passenger before boarding the plane.
If the passenger poses a serious threat even without having sophisticated weapons, he or she may be advised to consider other alternatives of transport. In case they consider allowing such a high-risk passenger to travel, there should be mechanisms put in place to monitor and control their activities once on board to ensure that passengers are not exposed to any form of threat. As Muḥammad (2017) warns, safety and security of passengers, cabin crew, airline, and airport should be given priority over the need to please a passenger identified to a terror suspect or a sympathizer of terror outfit.
The last stage of screening should be the inspection of cargo before they are loaded into the planes. Respondents stated that sometimes it may not be easy to determine the strategy used by terrorists. They know that the sophisticated systems of screening may limit their ability to pass the checkpoints with dangerous weapons and explosives without detection. As such, they conceal their explosives as part of a large cargo. It has happened in the past.
As such, cargo should also be inspected thoroughly before they are loaded into the plane. The respondents recommended the use of an integrated system that relies on emerging technologies, human expertise, and the use of highly trained canine units. Any contraband goods, from drugs, banned ivory, to any illegal weapon and explosives should be identified however much the criminals may try to conceal them.
This thorough approach to screening cargo should not just be limited to passenger planes. An explosive planted in a cargo plane can equally be dangerous to the crew and the airport facilities if it goes off. Nemeth (2016) warns that when inspecting cargo, it is important to inform customers of the customary approach of opening any wrapped goods to ensure that the airline can determine without a doubt, whatever is on transit as a measure of security.
Improving multi-stakeholder intelligence
The information obtained from primary and secondary data strongly suggests the importance of improving multi-stakeholder intelligence as a way of improving aviation security. The security systems at the airports are not often involved directly in the investigation of criminal and terror activities within the country. It is not possible for the officers to know if an individual has been radicalized or is a sympathizer of radical groups. The airline companies also have limited capacity to gather such crucial information, as Molinsky (2013) observes. However, government agencies have that capacity and responsibility.
The United Arab Emirates State Security and National Electronic Security Authority (NESA) are the bodies responsible for gathering intelligence in the country (Meifert, Ulrich & Potter 2013). These agencies should work closely with airport and airlines to help share crucial information about individuals considered dangerous. The local airports should also work closely with international airports to identify any form of threat that may be posed by some of the travelers or cargo that may have explosives. The findings show that the cabin crew and passengers should also be empowered to ensure that they can identify any potential threat and take necessary actions that can help save passengers, crew, and the airline.
According to Shafieezadeh and Ellingwood (2015), embracing a multi-stakeholder approach to maintaining aviation security is crucial in the modern aviation industry. In this approach, there is a sincere appreciation that mistakes can be made by one agency. However, when different agencies are involved in the identification of potential threats, chance of identifying and addressing threats are enhanced. When airports share information, they limit chances of suffering attack. As Smith (2014) explains, the nature of operation of the airports makes a threat at one airport dangerous to almost all other airports around the world.
When a terrorist boards a plane at the Dubai International Airport with explosives, all other airports that the plane will use may face the same threat. Working in an integrated system ensures that any potential threat is identified as early as possible and addressed before it can escalate. The respondents also emphasized the need to empower all stakeholders, including passengers and employees of airlines and airports who are not directly involved with the work of security, to be on the lookout for anything that may be suspicious. Being keen to any detail is crucial in managing aviation security.
Intergovernmental coordination
The respondents stated that one of the most important ways of identifying potential threats in the aviation sector is by having a close intergovernmental coordination. As shown in the review of literature, a tip from Saudi Arabian crown prince, Muhammad bin Nayef, to the United States made it possible to thwart a serious threat of terror attack that targeted the United States. The intelligence made it possible to track and eliminate an explosive planted in two different planes headed for the United States on October 29, 2010 (Sales 2017).
Such initiatives are important. When a government identifies a potential threat, it is necessary to share the information with other airlines so that necessary actions can be taken. Nevin (2016) explains that since the end of the Second World War, the relations between the United States and Russia has been strained.
However, that has not stopped the two nations from sharing intelligence about potential threats and how to deal with them. Regionally, governments need to ensure that they share intelligence about any potential threats to aviation security. One of the respondents noted that the current strained relations between the United Arab Emirates and Qatar may be a serious blow to the regional intelligence community. When two neighboring countries start accusing each other of espionage, Notarnicola (2015) warns that sharing of intelligence becomes one of the rarest things. However, such an environment may be detrimental to the aviation stakeholders.
Dealing with Potential Threat to Security
Once a potential threat to aviation security has been identified, it is crucial to take immediate measures to manage it. Ozbilgin (2015) explains that quick action taken by the relevant authorities may help in avoiding unfortunate events in the airports or airlines. Some of the respondents explained that their experience in the industry has taught them to be quick and effective in their actions whenever a security threat is identified.
Indecisiveness must be avoided in such situations. The response unit must understand each unique situation and determine the most appropriate action to take. The approach and team needed to diffuse a bomb that has been identified in a cargo will be different from that needed when it is established that a passenger is carrying a loaded gun. The action that needs to be taken will always depend on the nature of security threat and its location. The following should be considered when dealing with a potential security threat.
Having highly trained explosive experts
The findings made from the primary data supports the need to have a team of highly trained explosive experts who can detect and diffuse different types of bombs. In a report by Scott and Trimarchi (2017), terrorists are currently using explosives disguised as packages to be delivered from one airport to another. The ability to use suicide bombers is diminishing because of the enhanced screening systems at various airports.
It is not easy for suicide bomber to go through security checks with explosives wrapped around their body. The new approach is to use baggage. Each airport should have a highly trained team of experts who can deal with such threats within the shortest time possible. Schellwies (2015) explains that a large airport such as the Dubai International Airport should have different units that have knowledge and experience in diffusing bombs. One of the major issues of concern when dealing with explosives is the time factor. It may be crucial to ensure that the explosive is disabled within a short time to avoid casualties. Regular training and enhanced education may be necessary in facilitating a speedy response to such cases in the airport.
Physically fit and well-trained crew members
Information gathered in this study shows that it is crucial to have a team of physically fit and well-trained cabin crew capable of responding to security threats in appropriate manners. Under normal circumstances, the work of managing security threat is often handled by security teams within the planes or at the airport. The cabin crew members are expected to ensure that passengers are moved from one place to another in a pleasant experience.
However, it is important to understand that when extraordinary conditions arise, the team may need to take extra ordinary actions. A gang member or a terror group may attempt to take control of the plane. Sometimes they may try to take hostages using weapons that they succeed in smuggling into the plane. When that happens, there may be no time to wait for the security officers on the ground. The cabin crew will be forced to act to save their lives and that of their passengers.
Parhizgar (2013) argues that it is critical to ensure that these officers have some form of self-defense training that can enable them to engage the criminals and take them down within the shortest time if that is possible. With enhanced screening systems, it may be expected that these criminal elements may not have sophisticated weapons in the planes. However, they can still cause disturbance if they physically attack their targets in the plane. The crew members should be capable of taking down such individuals to restore sanity within the plane.
Strategically positioned snipers
Dubai International Airport has advanced systems of security that makes it almost impossible for one to smuggle any weapon into the planes, as evident from the statement obtained from the respondents. However, that does not mean criminals and extremist groups cannot try to penetrate the system. Some suicide bombers may come to the airport with the primary intention of blowing themselves up at the point of screening. Such eventualities can result into fatalities, massive destruction of properties, and possible delays within the airport. As such, it is necessary to neutralize such threats within the shortest time possible and with high level of efficiency.
Rossi (2014) suggests that it may be necessary to have snipers strategically positioned within the airport to take down such threats. The moment it is confirmed that a target is wearing an explosive with the intention of detonating it, Rothaermel (2013) states that the most appropriate action would be to neutralize the threat. Once the individual is taken down, most preferably incapacitated instead of being killed, the explosive experts can rush to the site to diffuse the bomb before it can go off.
The information obtained from the participants recommends neutralizing the threat other than a mere incapacitation. When a person has a bomb that he or she can easily diffuse by simply pressing a button, it is not advisable to shoot them twice. The shot should come as a surprise, it should be precise, and should render them unconscious, even if it means the individual can die in the process. It is only after that action that it would be safe for the bomb experts to approach the suspect to diffuse the explosive.
Emerging incidences of criminals and extremists finding their way to the plane with dangerous weapons may also need policy adjustments to ensure that snipers with special weapons are allowed into the planes, especially the large passenger planes. Strategically positioned, they should be capable of acting with precision to neutralize any form of threat that may emerge after the take off and before the landing of the plane. Such officers may require thorough training and regular practice to enhance their efficiency.
Efficient disaster management teams
Disaster management is one of the critical aspects of airport management. In an active airport such as the Dubai International Airport, anything that may pose a serious threat can happen, and when it does, it may be necessary for the relevant authorities to act with speed to ensure that the threat is neutralized within the shortest time and minimal casualties possible. One of the possible incidences of security threat may be a case of crash-landing because of technical problems in the plane. Price and Forrest (2016) warns that depending on the impact, a plane that has crash landed can easily split into several pieces and can go up in flames in the process.
The primary goal of the disaster management team will be to fight fire as a way of reducing the number of casualties as much as they can. As such, the firefighters may be the first response team that should rush t the site. Once it is confirmed that the threat of fire is eliminated, the rescuers should then move in to identify and rescue casualties. As Rossi (2014) observes, most major airports around the world have clinics where the injured can get emergency medical attention before being transferred to major hospitals. Another team will be needed to ensure that the stalled plane is safely moved out of the runway.
According to Percy, Kostere, and Kostere (2015), other than cases of crash landing, it may be possible that the plane is hijacked by criminals and extremists keen on attacking an airport. In many cases, the air traffic controllers are able to identify such cases based on the response and actions taken by the approaching pilots. In other cases, terrorists would issue warnings about their impending attacks crashing the plane. When it is established that a plane is likely to be crashed into an airport, an emergency management team will need to warn everyone to evacuate the potential targets of the criminals.
Evacuation of people and passengers from the possible targets may reduce the number of casualties. The airport management can then have a team of experts ready to act as soon as the plane lands. If it is crash landed, the primary goal will be to rescue anyone who survives and to reduce damage and destruction. If it lands successfully but with a clear knowledge that it is under the control of criminals, the security experts will take over the case to rescue the passengers by any means possible. The disaster management team should also be alert to cases of natural calamities and others forms of safety and security threats. The next chapter will provide conclusion and recommendations based on the findings obtained from both primary and secondary data sources.
Conclusion and Recommendations
The discussion chapter integrated the findings from both primary and secondary sources. In this chapter, the focus will be to provide conclusion and make recommendations about measures needed to improve aviation security within the country. It is clear that the aviation sector plays a crucial role in the growth and diversification of the United Arab Emirates. Tourism, trade, and real estate industries are booming in this country because of the ease with which people can travel in and out of the country.
The importance of the aviation sector makes it necessary to enhance safety and security at the local airports. As shown in the data collected from both primary and secondary sources, the United Arab Emirates is an oasis of peace in a region that has suffered political instability for decades. Countries such as Iraq, Syria, Yemen, and Afghanistan do not have stable political leadership, making it easy for insurgencies and extremists such as Islamic State to thrive in these regions. The management of the local airports such as Dubai International Airport will need to put measures in place to ensure that security is maintained at the highest level possible.
The findings show that threats to security may emerge from various sources. Terrorist and extremists pose a serious threat to the safety and security of the local airports. As shown in the review of the literature, although no major attacks or incidents relating to activities of terrorists have been reported in the recent past, explosives destined to the United States was discovered at one of the planes at the Dubai International Airport.
It was an indication that the local airports are not free from the activities of terrorists. Criminals targeting travelers or employees within the airport also pose significant security threat. Sometimes their intention may be to steal from the passengers. The report identifies cyber threat as another major issue. Criminals and extremists are shifting their focus from making physical attacks to using their cyber skills to manipulate data at the airports. These forms of security threat should be addressed effectively. The following recommendations should be considered by the local leaders in the aviation sector:
- Intelligence sharing is critical among the local, regional, and international airports. Once a threat is detected at one airport, it is important to alert other airports to enhance security.
- The management of the local airports needs to have disaster response and management teams that can help address emergencies that may arise within the airports.
- It is important to empower cabin crew so that they can have better skills to detect security threats and take appropriate actions as soon as possible. Passengers should also be encouraged to play active roles in intelligence gathering.
- Security team within the airports should be taken through regular training to equip them with skills that can enable them to fight varying threats to airport safety and security.
- It is necessary to embrace emerging technologies in screening of passengers and countering possible threats such as bomb explosions at the airports.
Appendices
Appendix 1: Research Questionnaire
Section A: Demographic Information
- Kindly state your nationality? (Tick as appropriate)
- French
- Non-French
- Kindly state your gender? (Tick as appropriate)
- Male
- Female
- Are you a member of any special interest group within the aviation sector?
- Yes (Kindly explain)______________________________
- No
Part B: Academic Background and Work Experience
- Kindly state the highest level of education you have achieved? (Tick as appropriate)
- High school graduate
- College diploma
- Undergraduate degree
- Master’s degree
- Doctorate degree
- Do you have additional professional qualifications other than your primary degree/diploma?
- Yes (Kindly explain)___________________________________________
- No
- How long have you been working in your current position of airport security officer/IT expert? (Kindly tick as appropriate)
- Under 2 years
- 2-5 years
- 5-10 years
- 11-20 years
- Over 20 years
Section C: Aviation Security Challenges and How They Can Be Managed
- Do you agree with the statement that security systems used by the local airports are effective in managing aviation security threats?
- Strongly agree
- Agree
- Not sure
- Disagree
- Strongly disagree
- What security systems are used by airports across the world? (Kindly explain)_______________________________________________
- Do you agree with the statement that airports in the UAE need to enhance their security systems beyond what they currently have?
- Strongly agree
- Agree
- Not sure
- Disagree
- Strongly disagree
- In what areas should security be enhanced at UAE airports? (Kindly explain)_____________________________________________
- Do you believe that the emerging technologies may be critical in addressing the current security threats in UAE’s aviation sector?
- Strongly agree
- Agree
- Not sure
- Disagree
- Strongly disagree
- What specific technologies and policies should UAE airports consider?_______________________________________________________
- Do you believe the local airport management authorities are doing enough to address the issue of aviation security in this 21st century?
- Strongly agree
- Agree
- Not sure
- Disagree
- Strongly disagree
Reference List
Abeyratne, R 2013, Regulation of air transport: the slumbering sentinels, Springer, Cham.
Abeyratne, R 2016, Competition and investment in air transport: legal and economic issues, Springer International Publishing, Cham.
Ali, A, Sagayan, V, Saeed, A, Ameen, H & Aziz, A 2015, ‘Age-invariant face recognition system using combined shape and texture features’, IET Biometrics, vol. 4, no. 2, pp. 98-115.
Alperen, M 2017, Foundations of homeland security: law and policy, John Wiley & Sons Inc, Hoboken, NJ.
Alsos, A, Eide, D & Madsen, L 2014, Handbook of research on innovation in tourism industries, Germany: McGraw Hill, Berlin.
Andersen, T 2013, Short introduction to strategic management, Cambridge University Press, Cambridge.
Baaghil, S 2015, The power of belonging: a marketing strategy for branding, 2nd edn, iUniverse, New York, NY.
Bendassolli, P 2013, ‘Theory building in qualitative research: reconsidering the problem of induction’, Qualitative Social Research, vol. 14, no. 1, pp. 25.
Bernard, H 2013, Social research methods: qualitative and quantitative approaches, SAGE Publications, Los Angeles, CA.
Bolman, L & Deal, T 2017, Reframing organizations: artistry, choice and leadership, Jossey-Bass & Pfeiffer Imprints, Hoboken, NJ.
Brennen, B 2013, Qualitative research methods for media studies, Oxford University Press, Oxford.
Bryman, A & Bell, E 2015, Business research methods, Oxford University Press, Oxford.
Card, A 2016, Applied meta-analysis for social science research, The Guilford Press, New York, NY.
Chin, L & Trimble, J 2014, Diversity and leadership, SAGE Publications, Thousand Oaks, CA.
Conyers, L & Kiyuna, A 2015, Cyber warfare sourcebook 2015, Lulu.Com, Raleigh, NC.
Cuervo-Cazurra, A, Inkpen, A, Musacchio, A & Ramaswamy, K 2014, Governments as owners: state-owned multinational companies, Journal of International Business Studies, vol. 45, no. 8, pp. 919–942.
Daft, R & Samson, D 2015, Fundamentals of management: Asia Pacific, 5th edn, Cengage Learning, London.
DeLange, R, Samoilovich, I, & VanDer, B 2013, ‘Virtual queuing at airport security lanes’, European Journal of Operational Research, vol. 225, no. 1, pp. 153-165.
Drabek,T 2014, ‘Emergency managers as community change agents: an expanded vision of the profession’, Journal of Emergency Management, vol. 12, no. 1, pp. 14-21.
Earley, C & Mosakowski, E 2016, HBR’s 10 must reads on managing across cultures, Harvard Business Review Press, Boston, MA.
Eriksson, P & Kovalainen, A 2015, Qualitative methods in business research: a practical guide to social research, Sage, London
Executive Office of the President, 2014, Budget of the United States government, analytical perspective, U S Government Printing Office, Washington, DC.
Fowler, F 2013, Survey research methods, SAGE Publications, Thousand Oaks, CA.
Fraga, S 2016, ‘Methodological and ethical challenges in violence research’, Porto Biomedical Journal, vol. 1, no. 2, pp. 77-80.
Gitterman, A 2014, Handbook of social work practice with vulnerable and resilient populations, Columbia University Press, New York, NY.
Gooderham, P, Grøogaard, B & Nordhaug, O, 2013, International management: theory and practice, Edward Elgar, Cheltenham.
Haddow, G, Bullock, J & Coppola, D 2014, Introduction to emergency management, Butterworth-Heinemann, Waltham, MA.
Hair, J 2015, Essentials of business research methods, ME Sharpe, London.
Hamner, M, Stovall, S, Taha, M & Brahimi, C 2015, Emergency management and disaster response utilizing public-private partnerships, Information Science Reference Hershey, PA.
Harrison, D & Sharpley, R 2017, Mass tourism in a small world, CABI, Boston, MA.
Hays-Thomas, R 2017 Managing workplace diversity and inclusion: a psychological perspective, Taylor & Francis Group, New York, NY.
Heng, Y 2015, Managing global risks in the urban age: Singapore and the making of a global city, Ashngate Publishing, New York, NY.
Hensel, N 2016, The defense industrial base: strategies for a changing world, Routledge, London.
Hewson, C, Vogel, C & Laurent, D 2016, Internet research methods, Sage, Los Angeles, CA.
Hoijtink, M 2017, ‘Governing in the space of the seam: airport security after the liquid bomb plot’, International Political Sociology, vol. 11, no. 3, pp. 308-326
Holz, M 2016, Suggestions for cultural diversity management in companies: derived from international students’ expectations in Germany and the USA, Anchor Academic Publishing, New York, NY.
Howson, P 2017, Due diligence: the critical stage in mergers and acquisitions, Routledge, London.
Hyndman, D & Hyndman, W 2016, Natural hazards and disasters, Cengage Learning, Boston, MA.
International Civil Aviation Organisation, 2016, Security at airports: ACI policy and recommended practices handbook, 8th edn, International Civil Aviation Organisation, Montreal.
Johnstone, R 2015, Protecting transportation: implementing security policies and programs, Elsevier Ltd., Oxford.
Kahan, J 2015, ‘Emergency management and homeland security: exploring the relationship’, Journal of Emergency Management, vol. 13, no. 6, pp. 483-498.
Kahlke, R 2014, ‘Generic qualitative approaches: pitfalls and benefits of methodological mixology’, International Journal of Qualitative Methods, vol. 13, no. 1, pp. 37-52.
Kaplan, F 2016, Dark territory: the secret history of cyber war, Simon Schuster, London.
Katz, J 2015, ‘A theory of qualitative methodology: the social system of analytic fieldwork’, African Review of Social Sciences Methodology, vol. 1, no. 2, pp. 131-146.
Kazda, A & Caves, R 2015, Airport design and operation, Emerald, Bingley.
Laroche, L & Yang, C 2014, Danger and opportunity: bridging cultural diversity for competitive advantage, Taylor & Francies Group, London.
Maktoum M 2017, Reflections on happiness & positivity, Explorer Publishing, Dubai.
Margulies, P 2017, ‘Global cyber-security, surveillance, and privacy: the Obama administration’s conflicted legacy’, Indiana Journal of Global Legal Studies, vol. 24, no. 2, pp. 459-496.
Marschan-Piekkari, R, Welch, D & Welch, L 2014, Language in international business: the multilingual reality of global business expansion, Edward Elgar, Cheltenham.
Maszka, J 2017, Al-shabaab and Boko Haram: guerrilla insurgency or strategic terrorism, World Scientific, London.
McHoes, M & Flynn, M 2017, Understanding operating systems, Cengage Learning, Boston, MA.
McLoughlin, D & Aaker, D 2014, Strategic market management: Global perspectives, Wiley, Hoboken, NJ.
McNabb, D 2015, Research methods for political science: quantitative and qualitative methods, M.E. Sharpe, New York, NY.
Meifert, M, Ulrich, D & Potter, L 2013, Strategic human resource development: a journey in eight stages, Springer, Dordrecht.
Molinsky, A 2013, Global dexterity: how to adapt your behavior across cultures without losing yourself in the process, Harvard Business Review Press, Boston, MA.
Mor-Barak, M 2014, Managing diversity: toward a globally inclusive workplace, SAGE Publishing, Los Angeles, CA.
Muḥammad, J 2017, European intelligence services in the face of the “Islamic State” cells: flabbiness of the European intelligence services, AlMaktab AlAraby LilMaaref, Cairo.
Neal, Z 2016, Handbook of applied system science, Taylor & Francis Group, London, UK.
Nemeth, C 2016, Homeland security: an introduction to principles and practice, CRC Press, New York, NY.
Nestor, P & Schutt, R 2014, Research methods in psychology: investigating human behavior, SAGE Publications, Thousand Oaks, CA.
Nevin, M 2016, The strategic alliance handbook: a practitioners guide to business-to-business collaborations, Routledge, London.
Notarnicola, N 2015, Global inclusion: changing companies strategies to innovate and compete introduction, Franco Angeli, Milan.
Örtenblad, A 2016, Research handbook on corporate social responsibility in context, Edward Elgar Publishing, Northampton.
Ozbilgin, M 2015, Global diversity management, Palgrave Macmillan, London.
Parhizgar, K 2013, Multicultural behavior and global business environments, Taylor & Francies Group, New York, NY.
Percy, W, Kostere, K & Kostere, S 2015, ‘Generic qualitative research in psychology’, The Qualitative Report, vol. 20, no. 2, pp. 76-85.
Pierre, E & Jackson, A 2014, ‘Qualitative data analysis after coding’, Qualitative Inquiry, vol. 20, no. 6, pp. 715-719.
Price, J & Forrest, J 2016, Practical aviation security: predicting and preventing future threats, Butterworth-Heinemann, London.
Reis, H & Judd, C 2014, Handbook of research methods in social and personality psychology, Cambridge University Press, Cambridge, UK.
Robinson, C 2014, ‘Sampling in interview-based qualitative research: a theoretical and practical guide’, Qualitative Research in Psychology, vol. 11, no. 1, pp. 25-41.
Rossi, F 2014, EU legal framework for safeguarding air passenger rights, Springer, Cham.
Rothaermel, F 2013, Strategic management: concepts, McGraw-Hill Irwin, New York, NY.
Sales, M 2017, Air cargo management: air freight and the global supply chain, 2nd edn, Routledge, London.
Saunders, M, Lewis, P & Thornhill, A 2015, Research methods for business student, 7th edn, Pearson, London.
Schellwies, L 2015, Multicultural team effectiveness: emotional intelligence as success factor, Anchor Academic Publishing, Hamburg.
Scott, B & Trimarchi, A 2017, ‘The digital aviation industry: a balancing act between cyber security and European consumer protection’, Air and Space Law, vol. 42, no. 4, pp. 443-462.
Shafieezadeh, A, Cha, J & Ellingwood, B 2015, ‘A decision framework for managing risk to airports from terrorist attack’, Risk analysis, vol. 35, no. 2, pp. 292-306.
Smith, M 2014, Europe’s common security and defence policy: capacity building, experimental learning, and institutional change, Cambridge University Press, Cambridge.
Stahl, G, Tung, R, Kostova, T & Zellmer-Bruhn, M 2016, ‘Widening the lens: rethinking distance, diversity, and foreignness in international business research through positive organizational scholarship’, Journal of International Business Studies, vol. 47, no. 6, pp. 621–630.
Sylves, R 2015, Disaster policy and politics: emergency management and homeland security, Sage, Los Angeles, CA.
Taneja, N 2016, Designing future-oriented airline businesses, Taylor & Francis Group, New York, NY.
Tracy, S 2013, Qualitative research methods: collecting evidence, crafting analysis, communicating impact, Wiley-Blackwell, Chichester, UK.
Triana, M 2017, Managing diversity in organizations: a global perspective, Taylor & Francis Group, London.
Ulmer, R, Sellnow, T & Seeger, M 2015, Effective crisis communication: Moving from crisis to opportunity, SAGE, Los Angeles, CA.
Walker, J 2016, Oman, UAE & Arabian peninsula, Victoria Lonely Planet, Footscray.
Wu, P & Mengersen, K 2013, A review of models and model usage scenarios for an airport complex system’, Transportation Research, vol. 47, no. 1, pp. 124-140.
Wukich, C 2015, ‘Social media use in emergency management’, Journal of Emergency Management, vol. 13, no. 4, pp. 8-15.
Yanow, D & Schwartz-Shea, P 2014, Interpretation and method: empirical research methods and the interpretive turn, M.E. Sharpe, London.
Yip, G & McKern, B 2016, China’s next strategic advantage: from imitation to innovation, The MIT Press, Cambridge, MA.
Yuen, S 2015, ‘Becoming a cyber power: China’s cyber-security upgrade and its consequences’, China Perspectives, vol. 2, no. 102, pp. 53-58.