Proposal Summary
This document presents an evaluation of the security systems at the United Arab Emirates (UAE) airports. The UAE has emerged as one of the leading trade and commerce centres of the Middle East. The country has neighbours such as Iran, Iraq, Syria, Afghanistan, and others which have seen increased militancy and terrorist activities. Therefore, airport security in the UAE must manage the latest challenges and threats to passengers, airport infrastructure and assets, and cargo.
The dissertation will use a mixed-method approach with primary and secondary research methods. Secondary methods will review the literature of airport security systems and the findings will be used to design a semi-structured interview instrument with open and closed-ended questions. Respondents for the interview include airport security managers who manage different departments and IT experts. Findings from the primary research will be triangulated with secondary research outcomes, and the results will help to make recommendations for airport security improvements in the UAE.
Topic of Literature Review
This section reviews the literature on airport security, societal changes, technology upgrades, and the new threats that airports face. The findings will help with developing an understanding of the subject and with creating the semi-structured interview instrument.
Research Background
The UAE is at the centre of Middle East trade and commerce, serving as the hub for many multinational oil corporations and a large number of Western luxury and retail brands. The Arab state has 21 airports catering to the high volume of passenger and cargo traffic. These include airports at Abu Dhabi, Al Ain, Mustafa, Al Futaisi, and many more. In 2017, Dubai alone processed more than 88.2 million passengers, and the total inward arrivals were more than 100 million (Saadi 2018).
Airfreight traffic cargo movement is high, and Abu Dhabi handled 800,000 tonnes of cargo in 2016. Airfreight traffic is projected to grow at a CAGR of 5.2 % between 2017 and 2021 (Rahman 2017). Airfreight is shipped in containers and it is possible to smuggle drugs and arms. Most of the passengers visiting for business, leisure and recreation, and for tourism. The assessment, however, is that some passengers may have illegal intentions such as smuggling of drugs, arms, and bullion. It is also possible that some passengers are affiliated with international terror organizations.
Ensuring safe passage for travellers is of prime importance and while the leading Middle East carriers have had very few incidents of accidents or other events, airlines consider only the number of incidents, accidents, hijackings, or bombings reported on their flights. Potential terrorists and illicit material may pass through these airports unchecked. The UAE, with its high growth rate, serves as a gateway to the Middle East, and it offers smugglers or terrorists a convenient way to enter the Middle East, Europe, or the Americas. Over the past several years, 93 fatal accidents have occurred with Middle East carriers, resulting in 4,692 deaths (Dudley 2016). These statistics are relative since they do not reveal the number of illegal goods and arms smuggled into and out of the UAE. The figure could be expected to reach very high volumes if all such violations were detected.
It appears that the UAE serves as a conduit for a large number of illegal transfers of arms and even nuclear weapons technology and equipment. It is possible that some of the weapons could be diverted and used in the US, Europe, or the UAE. While the UAE government denies responsibility and knowledge of such traffic, media reports indicate that such incidents happen (MEE Staff 2017).
According to Kaspersen (2016), airport security faces clear and present dangers and threats in several areas. These include cyber attacks on reservation and airport systems that can crash the system or cause aircraft accidents by disabling landing and navigation systems. Criminals are one step ahead of the security agencies and they use identity theft, impersonation, spoofing, and other hacking methods to help a terrorist with munitions board a flight.
Baggage and body scanning equipment detect metal objects, but plastic and liquid explosives in small quantities can be concealed and carried on aircraft and detonated. The use of drones and self-driving cars has allowed terrorists to reach the tarmac area. While face recognition software is available, it is slow and it cannot match millions of records from global databases. These trends indicate that airport security, which is overburdened with a large number of passengers, needs to develop adaptive systems that are fast and reliable.
Theory and Models
Several theories and models are available that can be applied to understand airport security. The ‘Concept of Operations’ model considers four interlinked usage scenarios. These are capacity planning, operational planning and design, airport performance, and security policy and planning (De Lange, Samoilovich, and Rhee 2013). The basic idea of this model is that an airport is a complex machine where all activities are interlinked. Security underlies all these activities, implying that each activity must be designed for functional capability and security considerations. This means that when capacity planning of the airport is conducted, with tasks such as aeroplanes landing, taking off, parking, and undergoing maintenance, security aspects should also be considered.
Security policy and planning is based on probabilistic risk assessment in which different scenarios of security incidents are simulated for each activity area. Capacity planning is done by adopting one of several models such as the deterministic queue model, Markov model, stochastic queue model, hierarchical control theory, and others.
Technology is available to detect suspicious objects, people, and events. It is important that security systems become a central part of the activity management, and it should not be considered as a mere extension of it (Shafieezadeh, Cha, and Ellingwood 2015). One of the major models used in designing airports in the agent-based model. This model helps to define flows in all operational areas such as ticketing, gates, baggage security, restaurants, immigration, and others. Figure 1 illustrates the flows in an airport.
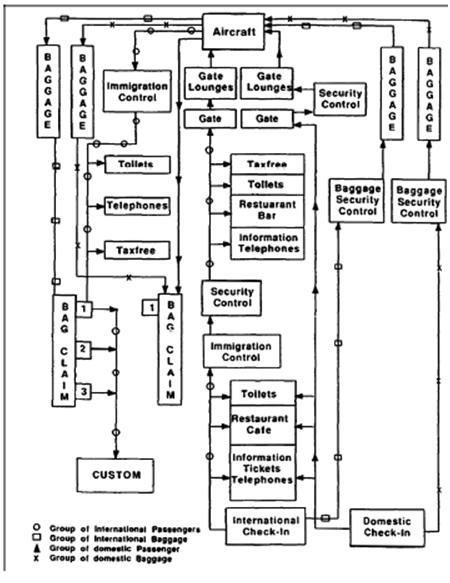
An important factor while designing airport security systems is to understand the peak load time. Some airports see the highest number of aircraft landing and taking off during the early and late hours. Queues will be longer at such times and all services including security will experience the maximum load. Airport security needs to be in its maximum state of readiness at this peak time (Wu and Mengersen 2013).
New Threats and Trends in Airport Security
Airports and aircraft have seen a large number of threats, attacks, hijackings, and bombings by suicide bombers or through bombs placed in cargo. These threats are only a part of the overall threats that airports face. Some of the threats are laser illumination, where powerful green and blue hand-held or tripod-mounted lasers are pointed at the cockpit, blinding pilots. More than 200 such attacks occur every day in the US. These attacks are carried out when a plane is landing, vulnerable time, and helicopters also face these attacks. The windscreen goes opaque and there is a high risk of accident (Esler 2016).
Although passengers are checked for drugs and other banned materials, insiders pose a greater threat. These insiders include catering and baggage handling crews, maintenance and cleaning staff, temporary staff, and cabin crew that have access to the tarmac and the aircraft. Verification and monitoring of contract staff is a major issue. Other threats that need to be considered are aircraft bombing through passengers, baggage, and cargo; armed attacks; leave-behind devices; vehicle-borne improvised explosive devices; cockpit doors; passenger screening and profiling; and many others.
In recent years, drones have come to pose a great threat since these devices are manually operated and they are not expensive. They can be fitted with radio-controlled bombs and made to fly near an aircraft or into its path and then detonated. While threats and attacks have been around for many decades, the methods for delivering the threats have changed (Price and Forrest 2016). Liquid bombs or explosives made from fluids and gases can escape detection by standard airport scanners, creating a dangerous security threat (Hoijtink 2017).
Societal Changes
With the introduction of budget airlines and tours, the number of passengers has grown tremendously. As noted in section 2.1, with more than 100 million passenger inflows, screening and verifying passengers becomes very difficult. People have become ‘mobile’ and air travel has become convenient. As a result, the load on airports and security has increased, while funding for airport security has not seen a proportionate rise. Many airports in the US use facial recognition, fingerprint, and iris identification systems, where the face of a passenger is scanned and compared with database records. Success depends on matching photographs in the database with the passenger being processed. If a male passenger has grown a beard or mustache, then the system can fail. These systems are useful and their accuracy can increase when very fast matching is possible and the databases of airport systems from different countries are linked (Ali et al. 2015).
Threats from Advanced Computing
Advances in computing have made airports a connected world where almost all transactions and events are managed through computer networks, leading to increased cyber attacks or malfunctions. A recent incident in May 2017 with British Airways saw 800 flights grounded (Scott and Trimarchi 2017). Assets such as air traffic control systems, passenger screening and ticketing systems, cargo handling stations, and many other airport security systems and databases are under threat of attack. Attackers can be hackers with a profit motive, terrorists, insiders or contract workers and airline staff, disgruntled employees, organized crime syndicates, ransomware hackers, and several other types. If the cyber system is made highly secure, then data flow suffers. Many airports in the US and Europe have developed interconnected systems that try to reduce vulnerabilities (Johnson et al. 2016).
Airport Security Policies
The European Commission has established a common EU aviation security policy and regime. This policy covers all operational and functional aspects, supply chain and logistics, passenger processing, baggage handling, all types of aircraft, and all other areas related to airport security. As an example, it specifies if toothpaste, gels, and perfumes are considered liquids. However, the policy does not specify performance parameters and technical specifications of the security system apparatus. While the policy is extensive, implementation, and auditing of the security policy are not always accurate. As a result, security threat events occur often, and each time the security system fails in identifying the threat before it occurs (European Commission 2018).
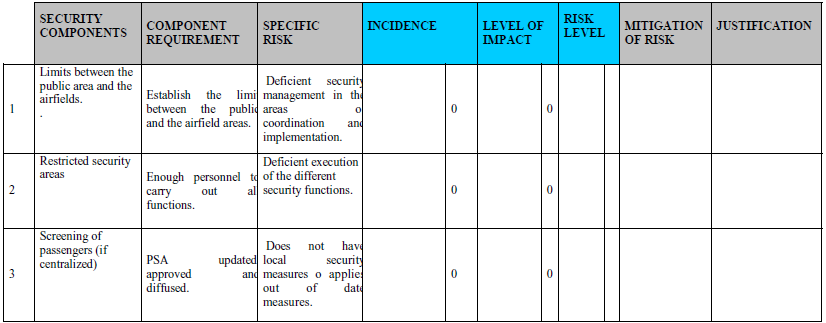
A risk assessment matrix helps security management to assess terror groups, organized crime, anti-system groups, social conflicts, radicals and religious sects, and other threats by creating a profile of the group. This profile details information such as leadership, will and means, infrastructure and funding, sympathizers, and combat mechanisms. Threat levels are assigned such as low, medium, and high (International Civil Aviation Organization 2018). It is important to construct a risk assessment matrix at the required level of detail, update it when required, and follow risk mitigation methods. Fig 2.2 illustrates a sample risk assessment matrix.
Variables From the Review
The review has brought out several variables from different categories. A partial list of these variables is presented in Table 2.1 and the list will be expanded in the dissertation. These variables will be tested in the research.
Table 2.1 Partial List of Variables.
Objectives
The research objectives framed are:
- Evaluate the threats that airports face and methods adopted by the UAE to recognize and address them.
- Evaluate the extent of readiness of UAE airport security to handle major incidents.
- Identify methods used by international airports in the US and Europe and the extent to which UAE airport security systems match them.
- Make recommendations to fill gaps between international and UAE security systems.
Project Outcomes
The expected project outcomes are that gaps and shortcomings in UAE airport security systems and their ability to identify new threats and methods to fill these gaps will be documented. Recommendations to fill these gaps will be made and when these recommendations are implemented, airport security will improve.
Why are you interested in the project?
The UAE has become the central hub of aviation for the Middle East. UAE airports serve as a conduit for agents of trade, commerce, and tourism. While UAE airports have not witnessed any major security incidents, any major event could damage the brand’s reputation for safety. Therefore, airport security must be the best in the world and ensure safe passage. This project will help to increase airport security and maintain the image of our airports.
What are the key questions the project attempts to answer?
The research question proposed is “How effective are UAE airport security systems in identifying and preventing security violations, and what measures can be adopted to improve them?”
- What is the status of air security at UAE reports and how it can be enhanced?
- What are the possible risks that UAE airports face?
- What security systems are used by airports across the world?
- In what areas should security be enhanced at UAE airports?
- What specific technologies and policies should UAE airports consider?
What Research Methods do you intend to use?
The intention is to use secondary and primary research methods. The secondary research will use a literature review to obtain information about current air security threats and the methods used by Western airports to manage them. Based on these inputs, a semi-structured interview instrument will be designed. Respondents for the instruments will be airport security officers from various UAE airports and IT experts. Their responses will be analyzed using keyword associations, and the results will be triangulated with the literature review. Conclusions and recommendations will be drawn from these studies. Details of the research methods are described in the following sections. The Research Onion Framework suggested by Saunders, Lewis, and Thornhill (2015) is used in this study. The framework is illustrated as follows.
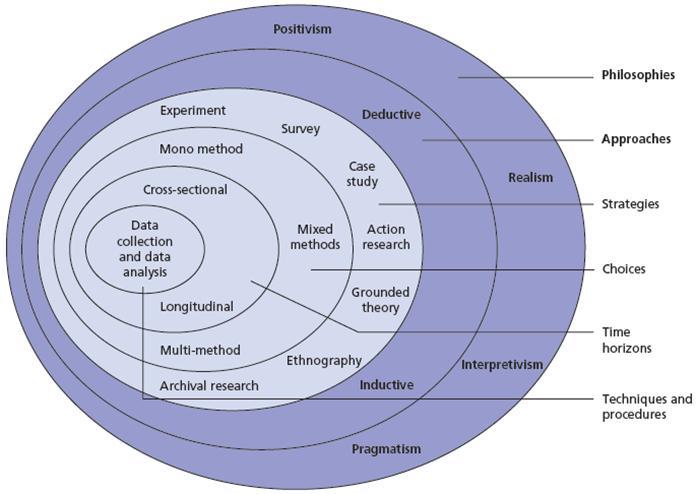
Research philosophy: Research philosophy is about the development of knowledge, its nature, and its relation to the world. Several research philosophies are available, including positivism, realism, interpretivism, and pragmatism. For this research, the interpretive philosophy has been selected, as interpretive research matches the goals of understanding security threat events and the behavior of actors, and identifying multiple causes and effects. In this research, the objective is to find trends in airport security, assess if the UAE follows them, and make recommendations. Along with secondary research, primary research is planned. Interpretive research will help to analyze and interpret the results, cross-reference findings with the literature, and conclude.
Research approach: Research approaches include deductive and inductive types. A deductive or top-down approach is used to form a theory and hypothesis, collecting and testing data to prove the theory. An inductive or a bottom-up approach is about collecting and analyzing data to draw observations and then forming conclusions. This research uses the inductive approach since we do not already know the trends in aviation security or the gaps in UAE airport security. The inductive approach will be appropriate for gathering and analyzing data, interpreting the results, comparing them to existing literature, and drawing conclusions (Bryman and Bell 2015).
Research Strategy: The research method defines the methods and processes used to collect and analyze data. Section 3 presented the research objectives and section 6 listed the key questions. The research strategy focuses on meeting these objectives. The plan is to use a semi-structured instrument to obtain answers to the questions. This method is used along with interpretive and inductive methods. The reason for using a semi-structured instrument is that it allows open and closed-ended questions to be posed to respondents, who can provide answers as per their understanding of the issue. Thus a diversity of opinions and views can be obtained (Hair 2015).
In this research, the theme of airport security has many factors, and each respondent will have personal views about the importance and strength of the dimensions. The survey instrument will help in capturing different perspectives. The survey instrument will have closed and open-ended questions. These questions will be based on the variables listed in Table 2. A partial list of closed-ended questions is given in Table 7.1, and these questions will be detailed in the dissertation.
Table 7.1 Partial List of Closed-Ended Questions.
Responses to the questions will be analyzed by using a 5-point Likert scale. Scores will be calculated for each question and response by assigning a numerical value such as Strongly Disagree 1, Disagree 2, Neither Agree nor Disagree 3, Agree 4, and Strongly Agree 5. Table 7.2 presents a partial list of open-ended questions (Eriksson and Kovalainen 2015).
Table 7.2 Partial List of Semi-Structured Questions.
Keywords from each respondent for each question will be extracted and added to a keyword list of all respondents for each answer. These will be analyzed by using keyword analysis with cross-references to secondary literature.
What primary and/or secondary data sources do you intend to use?
Secondary data sources are books, journals, and reliable websites. Information will be accessed from multiple sources and arranged as per their significance and usefulness. These will be analyzed to draw out key observations.
Primary data sources are airport security managers in the UAE and if possible from major airports in Europe. A sample size of 10 is considered. These respondents will be contacted personally and a request for an appointment will be made, and the questions will be administered personally. If a face-to-face meeting is not possible, then they will be contacted by email or telephone, and the questions will be mailed to them. A mail will be sent, requesting them to complete the instrument. Responses will be collected and analyzed.
List of References
Ali, A.S.O., Sagayan., V, Saeed, A.M., Ameen, H., and Aziz, A. (2015) ‘Age-Invariant Face Recognition System Using Combined Shape and Texture Features.’ IET Biometrics 4, (2) 98-115.
Bryman, A., and Bell, E. (2015) Business Research Methods. Oxford: Oxford University Press.
De Lange, R., Samoilovich, I., and Van Der Rhee, B., (2013) ‘Virtual Queuing at Airport Security Lanes.’ European Journal of Operational Research 225, (1) 153-165.
Dudley, M. (2016) Which is the Safest Airline in The Middle East? Web.
Eriksson, P., and Kovalainen, A. (2015) Qualitative Methods in Business Research: A Practical Guide to Social Research. London: Sage
Esler, D. (2016) The risk of laser attacks on pilots is real and growing. Web.
European Commission (2018) Aviation Security Policy. Web.
Hair, J.F. (2015) Essentials of Business Research Methods. London: ME Sharpe.
Hoijtink, M. (2017) ‘Governing in the Space of the “Seam”: Airport Security after the Liquid Bomb Plot.’ International Political Sociology 11, (3) 308-326.
International Civil Aviation Organization (2018) Manual and Threat Assessment and Risks Management Methodology. Web.
Johnson, C., Shreeve, M., Sirko, P., Delain, O., Ruhlmann, O., Vautier, E., Graham, B., and Meloni, M.T. (2016) Defending European Airports: Cyber-Physical Threat Analysis in Total Airport Management. In: 11th International Conference on System Safety and Cyber Security (SSCS 2016), London, UK. 2016.
Kaspersen, A. (2016) Four threats to Aviation Security – and Four Responses. Web.
MEE Staff (2017)Did the US know about Illegal UAE Arms Shipments to Libya? Web.
Price, J., and Forrest, J. (2016) Practical Aviation Security: Predicting and Preventing Future Threats. London: Butterworth-Heinemann.
Rahman, M. (2017) What will Drive UAE Logistics Sector Growth? Web.
Saadi, D. (2018)Dubai International Handles 88.2m Passengers in 2017, Retains Top Rank. Web.
Saunders, M., Lewis, P., and Thornhill, A. (2015) 7th Edn. Research Methods for Business Students. London: Pearson.
Scott, B.I., and Trimarchi, A. (2017) ‘The Digital Aviation Industry: A Balancing Act Between Cybersecurity and European Consumer Protection.’ Air and Space Law 42, (4) 443-462.
Shafieezadeh, A., Cha, E.J., and Ellingwood, B.R. (2015) ‘A Decision Framework for Managing Risk to Airports from Terrorist Attack.’ Risk analysis 35, (2) 292-306.
Wu, P., and Mengersen, K. (2013) ‘A Review of Models and Model Usage Scenarios for an Airport Complex System.’ Transportation Research Part A: Policy and Practice 47, 124-140.