Project Scope Statement
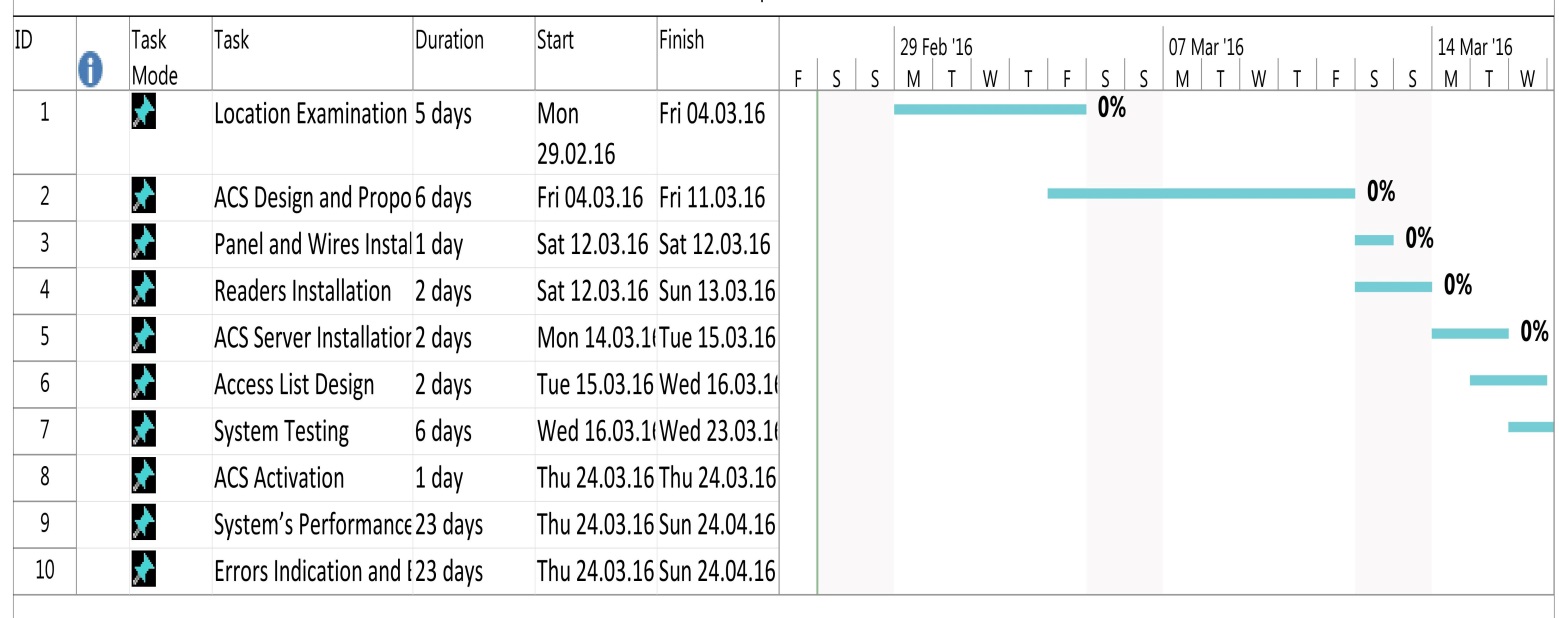
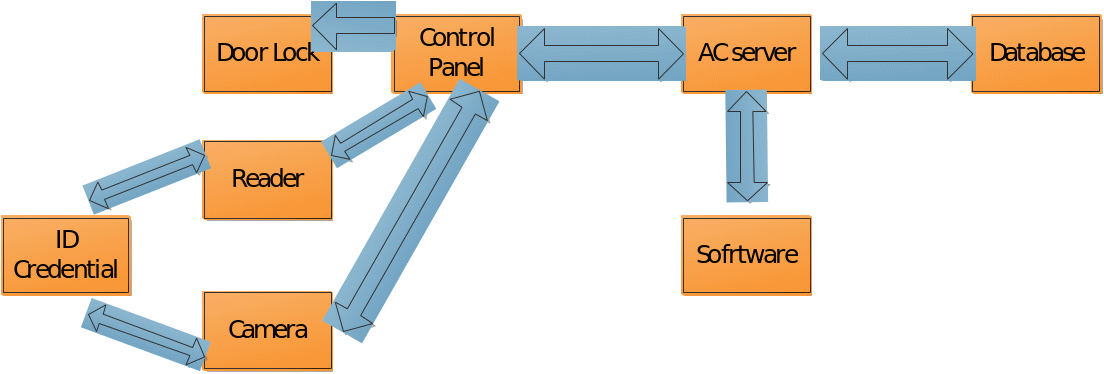
The project at hand provides a detailed description of the implementation process of an access control system (ACS) into a college dormitory. The project was designed by the members of the local Information Security Team to improve the security in the building and guarantee that the flaws of people entering it are properly controlled. The system is developed with due consideration of the location’s specificity, its size, and the existing identification system. The project provides an explicit explanation of the implementation stages and the essential equipment. The Gantt chart and the System Diagram are included to provide a clear idea of the procedure’s course.
Major Tasks
Preparation
Location Examination
It is essential to examine the dormitory area to define the appropriate locations for readers and cameras.
ACS Design and Proposal for Management
It is necessary to create the visual design of the dormitory’s interior and exterior areas. At this stage, it is also critical to assure the general compatibility of the current security system and its updated version. Finally, one should prepare a detailed report for the management providing a detailed cost evaluation.
Installation
Panel and Wires Installation
First, it is necessary to install the main control panel and the essential wires.
Readers Installation
As long as the wires and the panels are installed, one needs to install readers on the walls both interior and exterior, and on the doors.
Configuration
ACS Server (Software) Installation, Its Connection to Camera and Readers
The ACS server should be installed in such a way that it can control the main database. The camera and the readers should be properly connected to the server to assure the relevant comparison of the credentials received from the card and the Access List.
Access List Design
As long as the college already has students’ IDs in file, it is necessary to import this file to the server so that an Access List can be designed.
Execution
System Testing
The primary system testing is to be carried out on the staff before the full deployment of the system.
ACS Activation
The system can be activated as soon as it has passed a series test runs and all the students have been informed on the changes in the ACS.
Post-Employment Analysis
System’s Performance Monitoring
It is critical to carry out the monitoring of the system’s performance regularly and collect the relevant feedback.
Errors indication and elimination
All the errors indicated in the course of monitoring should be eliminated timely to maintain consistent security in the building.