The Capra Tek designed a personal security device meant to provide security by sending an alarm in case the customer is in danger. Capra Tek, a computer developing company, had higher chances of meeting the target customers by developing a comprehensive device that could be differentiated and provide customer value (Capra Tek, 2018). The personal security device had several features, including a wrist band of electrical contracts attached by a lead wire to a hand-held body containing a battery power source at a first voltage, a transformer to step the first voltage to a second discharge voltage, and a capacitor to store the discharge energy.
The device could detect danger and ensure that the send signal to the security agent for rescue. Several risks were assessed and mitigated during the development of the device, but the risk managers did not provide proper mitigation measures that could lead to the project’s success(Khan & Han, 2021, pg. 82). The lead wire connects the positive and negative terminals of the capacitor to the sequentially disposed of positive and negative electrical contacts on the wrist band, respectively.
Quantitative Risk Analysis
It uses provable data to examine the effects of risk in terms of cost overflows; scope slinks, resource depletion, and schedule interruptions. Qualitative risk analysis, on the other hand, tends to be subjective. It focuses on identifying risks to measure both the probability of a specific risk event happening during the project life span and its effect on the whole schedule should it occur(Davis & Bradley, 2015, pg. 162). The objective is to determine sternness. Outcomes are then documented in a risk assessment matrix to communicate unresolved risks to shareholders. Eventually, the drive is the same: the difference is that it takes a more logical, data-intensive method.
Quantitative risk analysis uses the available data to assess the effect of risks on cost, the scope of work, resources used and develop an interpretation of the results (Davis & Bradley, 2015, pg. 165). The quantitative risk analysis involved in developing a personal security device includes a tabulation of the risk register through risk identification, risk planning, assessment, and evaluation of the risks to provide recommendations. The planning of the analysis will flow systematically, as shown below:
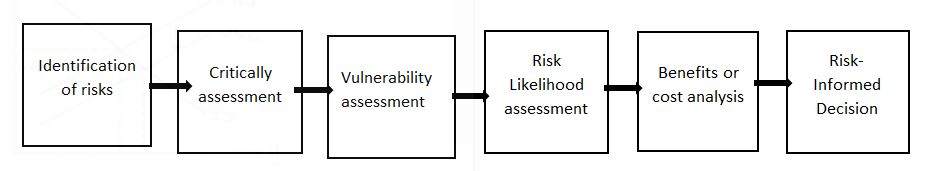
Risk Identification
The Capra Tek project had several risks that needed to be analyzed and the development of mitigation measures to help limit the project’s failure. According to the interviews held with the Capra Tek staff, the risks identified were identified concerning the new project (Capra Tek, 2018). The risks identified for critical analysis areas are in the table below.
Table 1. Selected Risk for Critical personal security device Risk Analysis
Consequence and Criticality Assessment
The assessment gives the losses or outcomes of the available risks in each category. Each risk scenario termed x was associated as an outcome of q. under the Capra Tek case, considering five loss dimensions as demonstrated in Table II. The subsequent events led to various outcomes, considered losses attributed to a single risk. Table II shows the outcome and the affected part for each risk, which measures the number of risks associated with the risk for all the shareholders within the company.
Table 2. Selected risk and its effect on shareholders
Considering the above losses definition for the personal security device project by the Capra Tek, it is definite that there are considerable risks that need mitigation measures (Ayyub, McGill, & Kiminskiy, 2020, pg. 793). The losses identified the potential losses, which means that if the company undertook the project without considering them, then there were higher chances of the project failure. Therefore, the formula for calculating the losses involves expressing loss (L) as a function of the risk attributed at a given scenario x, as shown below:
Lx=Fε|h(1−EM,ε)LMC,h(1−ER)…………..equation 1
Where Fε|h is the faultiness of the target element ε caused by risk type has a function of risk intensity. The equation was used to examine the losses for each element separately (CPNI, 2021 pg. 7). EM measures the resistance of the personal security device objective(s) to loss as a function of element damage, LMC,h is the maximum loss associated with risk h, and ER gives the effectiveness of the response to risk dependency.
Security Vulnerability Assessment
Security vulnerability assessment is the ability to assess them and determine the likelihood of the personal security device detecting danger and giving an alarm. According to Khan and Han (2021 pg. 85), personal security devices should be sensitive to monitor the environment, record any attack, and send an alert to the contact assigned. The product project was subjected to failure, which caused threats to various shareholders and customers.
Risk Likelihood Assessment
The risk likelihood assessment provides the rate at which risks occur per year. The risk likelihood schedule gives the forecasted cases of security device failure, attacks, and legal losses due to court cases presented by clients or third parties (Davis & Bradley, 2015, pg. 158). The risk profile below gives how the project would cause risks if no mitigation measures were initiated.
Cost-Benefit Analysis
The analysis adopted was the monte Carlo Simulation analysis, whereby the project’s cost is estimated and the project results forecasted to understand its viability (Muthén & Muthén, 2009 pg. 469). The below graph shows the cost of the project and its probabilities. The graphs aid in making decisions since the cost with a higher probability will be used as the effective cost for the project.
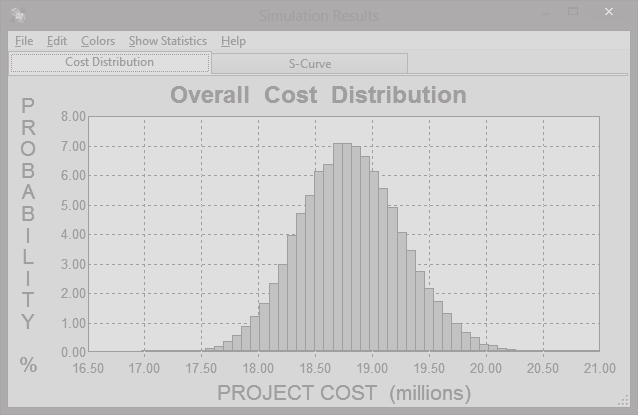
The above graph shows that the project was worth to be undertaken but cautions to be in place since there are many risks associated with the project. The graph shows that the project cost of $ 19 million is more likely to be completed. Therefore, managers for the personal security device should be using the amount. A higher value increases risks during forecasting while a low value also increases risks; hence, a good project will range in the optimum value.
Risk-Informed Decisions
A project of high risks, like the personal security device, involves active use of resources, experts, and planned time for effective implementation of the project.
Audit Risk Analysis
The audit risk analysis involves reviewing the risks, setting a plan, and initiating proper internal controls that could mitigate future risks. The analysis for the Capra Tek shows that the decision to undertake the project was not given proper timing (Capra Tek, 2018). Some of the risks involved include failure to allocate proper human resources for the project, inability to train the staff, non-involvement of all project committees before undertaking the project, and ensuring proper working of the device.
The risks could be mitigated through proper monitoring of projects to ensure all projects are complete before initiating new ones and accurate allocation of resources, time, and vendors for the entire project. The new projects should also involve proper testing before launching the product and incorporate all the conditions required to function better (Capra Tek, 2018). In addition, the project would require stage testing to enhance higher performance, which would make it, particularly since it is the only means to deal with and handle high-risk projects. The audit report for higher-risk projects would also be shared with all employees to understand what is required to avoid any project failure. The risks identified in the reports will be prioritized for the next project face.
Vital Preparations For Higher Risk Project Management
Higher-risk projects require preparations to avoid failure. Some of the preparation for the higher risk projects include the accurate estimation of the time and cost of the project. Any project requires proper estimation and time duration to undertake the project. Therefore, before starting any project, it is better to estimate the cost by use of experts and the time required for the project to be complete. Other preparations include the resources.
Higher-risk projects require adequate resources, which include financial and human resources. Every manager should ensure capable human resources for the project to be undertaken. There should also be the required financial requirements for the project. The last preparation is the vendors for the project. The availabilities of all vendors and the skills for the project are critical since it determines its success. Proper utilization of these preparations reduces the probability of project failure in society and business organizations.
References
Meritt, J. W. (2020). Method for quantitative risk analysis. Journal of risk and management system.
Ayyub, B. M., McGill, L. W., & Kiminskiy, M. (2020). Critical asset and portfolio risk analysis: an all-hazards framework. Wiley online library, 789-801.
Capra Tek. (2018). Audit risk analysis. Capra Tek.
Capra Tek. (2018). Quantitative risk analysis. Capra Tek.
CPNI. (2021). Personell secuirity risk assessement. UK: Center for the Protection of the National Infrustructure.
Davis, R. E., & Bradley, G. (2015). Quantitative analysis of information security risk: quantitative decision-making for business analysis. Journal of information security risk, 154-167.
Khan, K. M., & Han, J. (2021). Assessing security properties of software components: a software engineer’s perspective. Research Gate, 78-89.
Muthén, E., & Muthén, T. (2009). Example: Monte Carlo simulation studies. Risk and Management (pp. 465-479). Chicago.