Executive Summary
Due to the expanding market and improvements in technology, Cistern Security Systems (CSS) has been forced to hire more staff, most of whom are drawn from the local population. It has also been found out that the new staff is inexperienced on matters relating to the latest technologies in the security systems. This anomaly was discovered two months ago when we won a contract to fix CCTV surveillance cameras. The staff could not complete the task and the company had to hire staff from other firms, besides, the project was delayed and CSS had to pay a hefty fine as per the agreement.
The report aims to analyze the potential risk posed by inexperienced personnel on the performance of Cistern Security Systems. The main factors that contributed to such a scenario were difficulties to attract international experts, limited local knowledge and poor planning. A risk situation was modelled to describe the main factors that led to the risk situation. The proposed mitigation measures that CSS came up with included proactive forecasting, local recruitment workshops, training centres, and competitive pay packages. The team used the following tools to test the efficacy of the proposals: power field, severity and occurrence matrix, system approach and Hood Schools of Thoughts. The uncertainty level of the risk is level 2. The firm also used Porter’s FIT theory to analyze the feasibility of the mitigation measures.
Overview of the Risk Situation
Cistern Security Systems (CSS), one of the leading providers of security solutions, has undergone major expansion in the last seven years, this has included expanding operations into overseas markets, adopting modern security platforms, and venturing into other security services such as internet data security and tracking of goods in transit. During this period of rapid expansion, the company has strived to hire the most qualified staff in its technical and sales teams, whether from the local Saudi market or expatriates to meet the growing job demands (Brown 1995).
CSS has continually recruited new staff with the realization that the success of any organization depends largely on its staff. However, the company has been operating on a shoestring budget and has not been able to attract the most qualified staff while some of the most qualified personnel have been lured by better deals from other firms. Consequently, the firm has had to hire less qualified staff with no prior experience and retrain them through field experiences.
However, the nature of services that CSS has recently ventured into requires a thorough knowledge of security operations that require both knowledge and experience. This situation has created a crisis in the company since only a small percentage of the staff can perform their roles satisfactorily. At times, the temporary staff has been hired to assist in the operations and other instances, CSS has had to sublet contracts that it won.
This paper will analyze the staff “short of talent” risk that has a huge drawback on the performance and success of the organization, especially in undertaking projects that require expertise, experience and precision. Security operations are quite complex and sensitive and any flaw could cost the company millions of dollars in the form of contract fines, loss of contract and legal fees. Besides, the image of the company will be tarnished and once this happens, winning public confidence would be a daunting task that could take years.
Several reasons have led to a shortage of experienced and qualified staff in installing CCTV surveillance cameras and other security solutions as outlined below:
- In the early 2000s, the demand for personnel in security firms was low due to the small number of security firms that were operating in Saudi Arabia at the time, this caused several young experts to seek employment in other sectors. This was coupled by fact that security personnel were paid poorly as compared to other sectors such as oil drilling, above all, many people despised security jobs as they were considered ‘low-class’ (McCahill 2002).
- During the late-1990s and early 2000s, there was an increase in global demand for individuals who were highly qualified in security systems. This increase in demand was caused by an increase in general crime fears among people in developed nations, especially Europe. These opportunities attracted qualified personnel from Saudi Arabia as the pay-packages were better. This depleted the country of qualified and experienced individuals.
- Frequent political upheavals and threats of terrorism have discouraged expatriates from taking up job opportunities in Saudi Arabia.
- Poor forecasting & planning by the Labor Office. Had CSS known that there was a shortage of personnel and that their demand would increase in the late 2000s and early 2011, the firm would have started recruiting and hiring the security experts several years back to give young employees enough time to develop their skills. These early preparations would have prevented a shortage of experienced staff (Tse 2005).
- The final cause of qualified and experienced staff in Cistern Security Systems stems from the small operating budget. The organization continues to face competition for qualified staff from more-established firms such as STESA, Allcom, Abr Aman AFSTS, and IBD-Tech. All of these companies pay better than CSS and attract highly experienced staff from the company (Norris & Armstrong 1999).
Characteristics of the Risk Situation
The workforce risk shall be analyzed in regards to two major characteristics, i.e. frequency of occurrence and severity of the loss.
As CSS is expanding, it is facing competition for security system experts from other firms, this has forced it to hire less qualified and inexperienced staff and retrain them through on-field experiences. This implies that staff inexperience will be much pronounced in the first few months. However, due to the intricate nature of some security system operations, such as CCTV installation, fresh employees may encounter several difficulties for a longer time. Thus, the frequency of workforce risk is considered high (Carrera 2008).
Secondly, the complex nature of some security systems means that staff must have a working knowledge of these systems. Therefore, mistakes are more common and this increases financial losses. Besides, any mistakes arising from the inexperience of staff may cause delays in the completion of a contract, resulting in fines, and hiring temporary staff to work on contracts (Tsoukala 2007). This further drives up financial losses. Therefore, the severity of the loss is considered high as well.
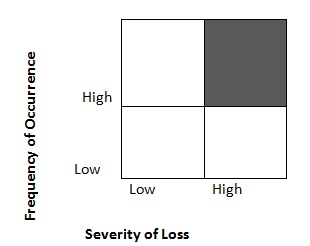
From the matrix table in Fig. 1, it is evident that the severity of loss and frequency of occurrence is high, hence an organization should strive to avoid the risk. However, in a situation similar to the one in our company, the risks should be eliminated and sufficient measures introduced to prevent their occurrences in the future, thereby reducing financial losses.
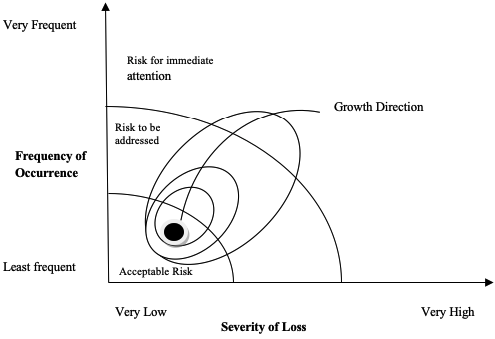
Figure 2 illustrates the growth dimension of the workforce risk over time. The inexperience of the personnel combined with the complexity of some security operations requires urgent attention and actions to reduce financial losses (Honess & Charman 1992).
The System Model
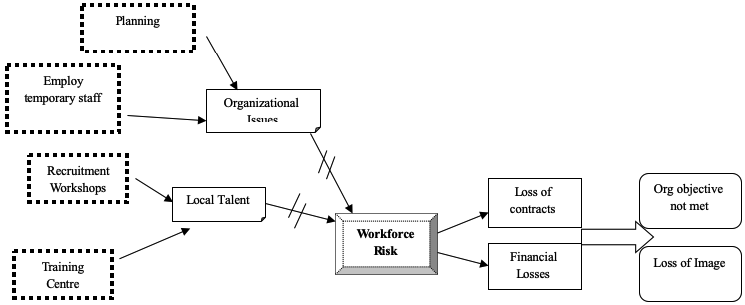
It is imperative that a holistic view of the risk situation is considered and the factors that caused it assessed. A system model shows all the major factors that led to the risk situation and illustrates the relationship between these factors as illustrated below:
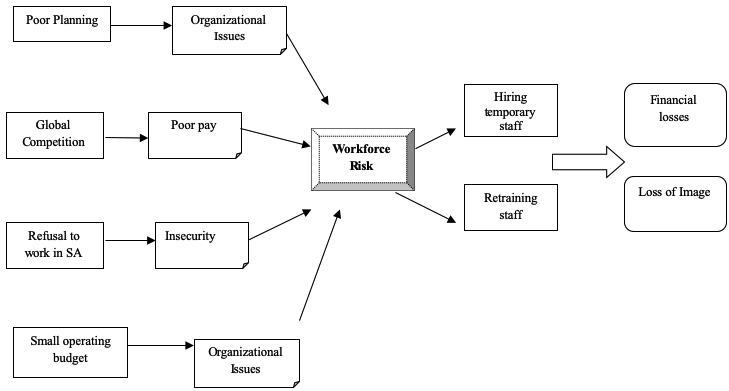
The System Model is shown in Fig. 3 illustrates the factors that caused CSS to hire inexperienced personnel and the factors that led to this anomaly. It can be seen that most of the problems were because of organizational inefficiencies (Lyon 2001). The concept of a power field can enable us to understand the environment in which the organization operates.
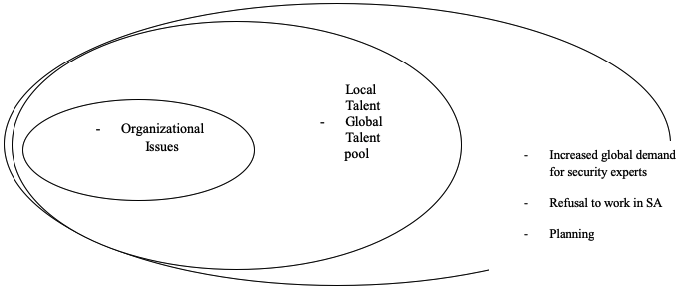
The Power Field Plot gives the most effective mitigation measures that can be used by CSS on factors that are under its influence. The organization cannot reverse the fact that most experienced staff are close to the retiring age, or that people are refusing to work in Saudi Arabia due to security concerns. These factors have forced CS to opt for a younger, less experienced workforce that, instead, has turned out to be a liability (Balzacq 2006).
Proposed Mitigation Measures
The risk mitigation measure considered in this paper is aimed at avoiding or preventing employee-based risks from occurring in the future. Since CSS has already hired inexperienced employees, they cannot sack them according to since this is prohibited by the Saudi labour laws. This leaves the company with the option of enrolling these employees through intensive training programs to improve their expertise.
Mitigation of the organizational issues
Proactive Forecasting and Planning: CSS needs to make forecasts accurately for its future operations. The forecasts need to centre on the expected growth and attempt to relate this to the number of staff required.
Mitigation of the local talent factor
- Recruitment Workshops: CSS can visit local universities and technical colleges to encourage young people to specialize in the security systems as well as provide these fresh graduates with lucrative offers to allure them to joining the organization.
- Training Centers: The organization should build a real-time training centre where the inexperienced personnel can get hands-on training that will expedite their learning curve in an environment where training mistakes will not be costly. Also, the organization should provide its inexperienced personnel with detailed procedures and guidelines of the operation to eliminate the risk of mistakes and improvisation (Cazemier 2000).
Unintended Effects and Secondary Mitigation Measures
Implementation of these mitigation measures reduces risks arising from the limitations of the workforce. However, new unplanned effects may arise from these measures as shown below:
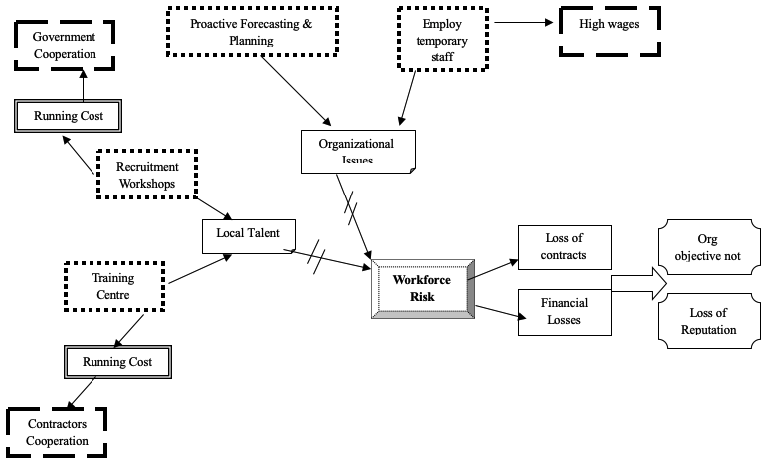
From the figure above, the preliminary set of mitigation measures have brought in a new set of problems, these include:
- Operation costs of the recruitment exercise. Since the exercise will be done in conjunction with the local universities and technical colleges, the expenses will be substantially reduced.
- Costs of running the training centres: the staff will pay part of the money used for their training, and to prevent ‘poaching’ from other firms, the retrained staff will sign a five-year contract with the company.
- Higher wages paid to temporary staff: they will be employed temporarily while the rest of the staff are in training, although they will cost the company a substantial amount, the long-term benefits of the training program will exceed the costs.
Effectiveness & Sustainability of the Risk Mitigation Measures
Several theories that can be used to reduce workplace risks have been postulated. However, each one of these theories requires an assessment before they are implemented, this is because the implementation costs can exceed the expected benefits (Ericson & Haggerty 1997). Since operations at CSS require specialized skills, and any mistake can prove costly to the company economically and in terms of image loss, it must proactively ensure that staff have the right expertise.
The designs doctrine can be used to illustrate the advantages of having the right skills at all employment levels. The organization must ensure that the workforce is trained on the latest technologies in security systems (Bon van 2004). However, before the training commences, CSS should consider the effects that may arise and calculate their magnitude so that they can be minimized.
The residual uncertainty level of the organization must be determined so that its future performance can be evaluated. The residual uncertainty is defined as the improbability that remains after the best possible assessment of the company has been performed (Courtney, Kirkland & Viguerie 1997). The company’s growth prospects can be evaluated so that future resource requirements can be estimated, this can help in averting the debacle witnessed at CSS. The organization’s future growth will be affected by factors such as economic performance and competitor’s strategies. Consequently, the residual uncertainty level is level 2 “alternative futures”.
The key factors that will determine the success of the mitigation measures are:
- The organization’s ability to efficiently and accurately analyze the security systems’ market to plan for the required personnel.
- The commitment of the inexperienced personnel to learning and improvement because all the training activities will not succeed unless the employees are willing to develop and learn from their mistakes.
- They hired consultants’ willingness to be active in both training and job operations.
For the organization to sustain a competitive advantage over its competitors, it needs to achieve strategic positioning and order fit (Porter 1996). Positioning establishes how and what activities the company performs, and how these activities relate to each other. CSS should take a needs-based positioning to serve its customers where it can supply all components of security systems that it sells. For example, when it is installing CCTVs, it should be able to supply the cameras, hard drives, display screens, and back-up devices (Fyfe & Bannister 1996).
The risk mitigation measures should reduce the initial uncertainty of the risk situation to be sustainable. The mitigation measures should reinforce each other to minimize the risk and thus the third-order fit “optimization of effort” is the most suitable here, the model is shown below:
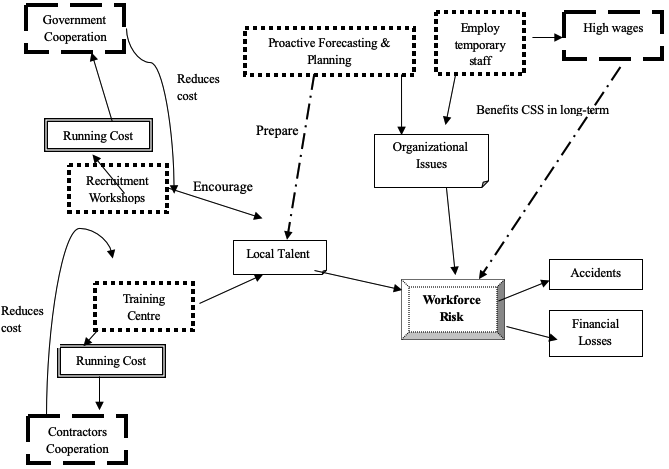
The figure above illustrates how the initial sets of mitigation measures and secondary effects will reduce the risks related to inexperienced personnel.
Conclusion
Classification of risks can be done concerning their frequency of occurrence and severity of a loss. This case study enables one to evaluate risk situations in organizations, the exercise involved tracing risk situations from the sources, mitigation measures, and secondary mitigation measures, and finally the analysis of the efficacy of the mitigation measures. Several models were used during the case study that enabled CSS to solve the workforce risk situation, however, it should be noted that not all organizations can employ these models to solve risk situations. This system approach greatly depends on the perception of the analyst and thus it is subjective. The analysis introduced several tools that analyze the effectiveness of the proposed mitigation measures.
References
Balzacq, T. (2006), Security versus Freedom, Aldershot: Ashgate.
Bon van, J. (2004). IT-Service management: Introduction to basic operations of ITIL. Amsterdam: Van Haren Publishing.
Brown, B. (1995). CCTV in Town Centres: Three Case Studies. Police Research Group, Crime Detection and Prevention Series, Paper No.68, London: Home Office Police Department.
Carrera. S. (2008). Security and our Freedom, Aldershot: Ashgate.
Cazemier, J. (2000). Security Management, Stationery Office. London: Sage.
Courtney, H. Kirkland, J. and Viguerie, P. (1997). Strategy Under Uncertainty. Harvard Business Review, Nov-Dec 67-79.
Ericson, R. &. Haggerty, K. (1997). Policing the Risk Society. Oxford: Oxford University Press.
Fyfe. R. and Bannister. J. (1996). City watching: closed circuit television in public spaces. Area 28(1): 37-46.
Honess, T. and Charman. E. (1992). Closed Circuit Television in Public Places: Its Acceptability and Perceived Effectiveness. Home Office Police Research Group, Crime Prevention Unit Series, Paper no 35, London: Home Office.
Lyon, D. (2001). Surveillance Society, Buckingham: Open University Press.
McCahill, M. (2002). The Surveillance Web: The Rise of Visual Surveillance in an English City. Cullhompton: Willan Press.
Norris, C. &. Armstrong. G. (1999). The Maximum Surveillance Society: The Rise of CCTV. Oxford: Berg.
Porter, M. (1996). What is Strategy? Harvard Business Review, Nov-Dec 61-78.
Tse, D. (2005). Security in Modern Business: security assessment model for information security Practices. Hong Kong: University of Hong Kong.
Tsoukala. A. (2007). Terror, Insecurity and Liberty, London: Routledge.