Introduction
Cybersecurity has become an important problem in today’s Internet networked world because of the increasing range of attacks perpetrated on the networks, making organizations such as DTL Power Corporation to develop countermeasures by training technical people with the skills necessary to respond to such threats effectively.
One training approach was through simulations that were done involving different groups at different levels to establish a range of issues related to Cyber-attacks.
This assessment report provides information about the roles the team members played to ensure business continuity planning, data encryption, emergency bypass policy, information privacy policy, load management, and training incentives (Wright, 2012).
Activities
Individual planning
Each team member was required to provide some support and play a significant role in the simulation exercise by contributing to the overall success of the simulation. In that context, the plan used as a framework for the hacking simulation activity for each member is discussed in the context as follows.
The hacker was prepared to make continuous and sophisticated attacks at the company’s network infrastructure and Cyberspace to increase the risk of loss of business continuity.
According to Agresti (2010), it was determined that a Distributed Denial-of-Service (DDoS) attack had occurred that was designed to cause financial loss by making the attacks known to the public.
The hacker contributed immensely to the disruption of the company’s services to the public to ensure disruptions occurred resulting into loss of business.
At the individual level, the preparation for the attacks involved putting in place the use of redundant primary disks to make the DDoS attacks successful.
The approach involved using primary disks that could make the movement of data through the restricted bandwidth difficult and impossible to deal with.
The procedure was implemented by the hacker who engaged in continuous tracking to determine the average usage of the disks by activating redundant disks to ensure that the primary disks were completely occupied and no memory space was available for additional use in service delivery.
The hacker had two backups for power redundancies, which is a common practice for setting up power systems to ensure sustained supply of power in case power disruptions happen.
In addition, two backup systems were used to ensure more power was available for use and in case of an emergency, two backup systems were deemed necessary to ensure sustained power supply (Agresti, 2010).
On the other hand, two backup power maintenance systems were made available for user’s data with two copies of the original data made available for comparison when the activity was over. The additional data backup was important to ensure sustained data availability in case the data was corrupted.
Policy review
Policy is an important element in Cyber security because it enables the organisation to set up strategies for combating Cyber-attacks that are relevant to the time the attacks occur and the level of technology development. Policy reviews were recommended to be revised on a 12 months cycle.
However, recommendations show that the 12 months are appropriate to investigate Cyber defenses and breaches to ensure sustained protection of the company’s critical resources.
In addition, it is a cost effective schedule because constant reviews are costly and sometimes could end up causing losses to the company (Assante & Tobey, 2011).
Business continuity planning
The protection of the company’s website was based on the DDoS protection binding strategy that was technically achieved by delaying the binding of the damage caused by the distributed denial-service attack.
The results include reduced employee morale, inability to provide the essential data availability services, and an interruption of customer services. The results were reduced customer and stakeholder confidence, which leads to loss of revenue, profits, and other related service delivery income.
To address the problem, the DTL Corporation must create a framework to protect its website and minimise the potential risk of being compromised by hackers using the DDoS attacks (Assante & Tobey, 2011).
However, to ameliorate the adverse effects of the DDoS attacks, the responsible team member put place business continuity measures that included the use of personal relationship management program to talk with the customers on the need to collaborate with the management to ensure service deliveries were made as required.
Collaboration was essential for each team member because of the contributions they made towards protecting the sensitive information assets of the company (Wright, 2012).
Load balancing
Load balancing was one the strategies that was used to protect the servers from the successful DDoS attacks. Load balancing was done to delay the DDoS binding to delay the movement of network traffic to protect the system and allow it to support its working capabilities.
In addition, by extending the network traffic using the load balancing program, it was possible to demonstrate how network traffic could flow smoothly through each resource used to make the system to work effectively (Assante & Tobey, 2011).
Data encryption
Data encryption is a technique that is widely accepted as an effective method of engaging hackers so that they do not find an easy way or access to protected data to comprise the integrity of the information system for unauthorized use.
The information stored in the company’s database was encrypted to create confidence in the customers on the security of the data.
However, some additional mechanisms were required to enforce data integrity and confidentiality by us of the SSL encryption to protect customer and company data against the threats from malware.
Here, each team member collaborated effectively by contributing their skills and knowledge on the best data encryption algorithms to use to encrypt data for security reasons.
It was established that each team member has specialist technical expertise on the use of encryption algorithms and the best solution was arrives at after evaluating the performance of each algorithm (Assante & Tobey, 2011).
One of the approaches that were used to increase integrity and confidentiality was the use of secure data encryption algorithms that could be developed by the company.
In addition, it was recommended that the company use minimum resources on training the staff on information security programs such as how to enforce privacy using different tools, policies, and algorithms.
Information privacy policy
The information privacy policy was an important asset for the company to use for the protection of data according to the recommended data protection act to ensure minimum standards for data protection were observed.
In computer investigations and Cyberspace employee most have to upgrade their skill by training in order to continue with their career (Assante & Tobey, 2011).
There are number of organization recently proving the certification programs for computer forensics and before engaging in a certificate program make sure to research the requirements, cost and acceptability in the chosen area of employment.
Also, the Federal government still in under threat; therefore, funding should be provide in order to protect the Cyber incidents and trained the worker who can take care Cyber threats.
Incentives
When creating incentives programs the conforming to the usual affection for employers is to provide training bonus and maximum amount of spending on training promotion and evaluation.
DTL Power Corporation require to update, revision and implement the innovation through the emergency bypass policy by spending with a maximum amount of money and the violations of typical separation of duties protocol will be warrant through the restriction and violation of damage involve with fines.
Briefing report
In making the simulation to work, it was important to ensure that different measures were in place to ensure that the DDoS attacks could not successfully compromise the website or the company’s network.
The core elements that were integrated into the protection mechanism were to disable the company’s ability to provide access to its services using remote communication methods. Here, the risk to the type of attacks that could be minimized includes DDoS attacks.
However, to ensure business continuity, it was crucial to provide the middle level management with remote access capabilities to the company’s information assets or systems because it provided the management with the ability to reduce the vulnerabilities to Cyber-attacks.
Business continuity assurance
However, a critical analysis revealed that business continuity was not assured because of the increases in the downtime that occurred because of the network isolation techniques that were employed to isolate and assess the network for vulnerabilities and threats.
In addition, the loss of business continuity stemmed from the strategy of isolating the network to minimise the risk of attacks or minimise the effects of the attack. However, loss occurred because the network isolation policy was contributing to the detriment of the operational functionality of the network.
On the other hand, the company’s management beliefs that disabling the operating system (OS) and the database ports and its associated services could minimise the level of vulnerabilities of attack on the systems.
On the other hand, the management of the company has placed its trust to protect its resources against brute force attacks by creating a password change policy which requires that each user changes the password regularly to avoid hackers guessing passwords.
However, the policy to allow for password changes for every 45 days provides the hackers enough time to conduct intrusion attacks and to brute force the passwords.
Gradually, it was established that DTL Power views the increase in budgetary allocations could lead to loss and reduce profits if the company invested significant amount of money in implementing the technical measures to protect its network from Cyber-attacks.
However, a more widely accepted strategy was to use more financial resources in establishing strong customer relations development to increase their confidence towards the organisation.
Controls
The type of controls recommended for use to protect the resources include delaying the binding, a technical method that allows the technician to conduct a TCP splicing that could allow controlled flow of traffic within the company’s systems’ network to detect and deter malicious attacks.
Load balancing could be achieved by spreading the workload to different servers and ensuring that no one server was overloaded using the HTTP protocol. By making the distribution of the services offered by the server, it could be possible to counter the DDoS threat.
On the other hand, the use of a firewall was deemed necessary to filter the incoming web traffic and block suspicious traffic to ensure effective auditing of the attacks or attempted attacks at the network.
DTL Company settled on an additional system protection technology by using an intrusion detection and prevention system, with the aim of the ability to monitor the flow of traffic into and out of the system that might be malicious.
In addition, a log management system could provide a summary of programs that were allowed access into the network or the programs that were rejected to understand the level of threats intending to attack the system.
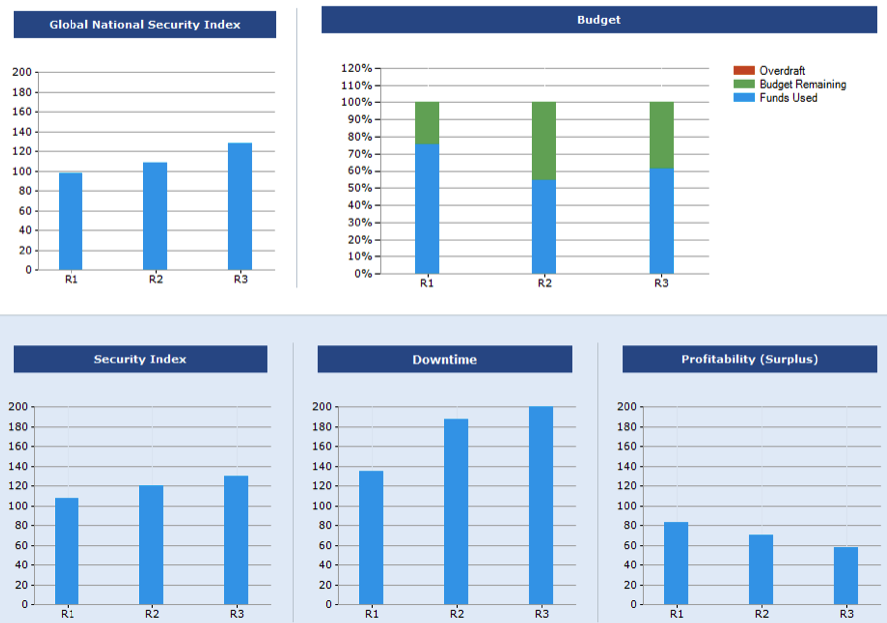
Table 1: Downtime effects report
The results in table 1 show an increase in downtime, security index, budget, and a significance decrease in the company’s profitability because of the poor implementation of Cyber security defenses.
Results for round 2 simulations
Introduction
The second simulations were done to investigate the attacks that happened affecting the networks and websites for both public and private institutions with DTL Power suffering a significant impact of the operations and service delivery of the company.
It was necessary to conduct vulnerability assessment of the DTL Power security controls and establish the most effective countermeasures to ensure that the weak points were established and the best security mechanisms to integrate into the information architecture of the company.
Here, the impact of the Cyber defenses of the company was audited and the results noted.
Team assessment report
An assessment report indicating the operational functionality of the company’s website and network protection shows that the strategy of reducing network access to reduce the risk of remote attacks was not an economically feasible.
The rationale for the argument was that discontinuity of service provision to the customers violated one of the IT triad of security and that is availability. Here the response to the attacks that were caused by a virus being transmitted on the Internet was unprofessional.
However, a professional application and use of the tools such as port blocking based on the type of virus and the target port number the virus uses to infect the systems could be used to re-mediate the problems.
Security controls
The strategies to counter the attacks that were recommended by the team members include patching the operating system with the most recent and up to date patches that are recommended and regularly provides by the company, using both the hardware and software firewalls and the universal threat management systems to filter and block malicious code, use of delayed binding or the TCP protocol at the appropriate layer, and careful use of the ISP to block any code that behaves maliciously.
In addition, it was necessary to train users of the information systems to avoid downloading programs or any email attachments that were suspected to be coming from suspicious sources.
The preventive measures include educating employees on how to encrypt data in transit, conduct a continuous risk management to discover the security holes and the risks data can be exposed to, use antivirus software from a reliable vendor to protect an scan computers for viruses and worms, and any other malware, and ensure mails are received or sent as per the policies of the company.
On the other hand, it is necessary to train workers on the procedures and policies necessary to enable them identify resources that are under the threats of Cyber-attacks.
In addition, it is necessary to train technical and mobile employees on the effective application of information security data standards irrespective of the tools or services they are getting from the company’s IT infrastructure (Ten, Liu & Manimaran, 2008).
Table 1
Profitability
The team convened to evaluate different strategies to improve the profitability of the company under the current DDoS threat landscape.
The core elements that were suggested to be changed because of the inherent weaknesses that were identified in the assessment include policies on remote access, patch management, issuing of alerts, vendor software use, the privacy of information, and system analysis and development.
However, the most important areas covered include policy changes to CERT in Round 2 from the Breach Notification Policy from FBI/NSA in Round 1.
Impact of Cyber–defenses
As detailed in table 3, the Cyber defense applied on the information system of the company showed a significant increase in compliance, contribution to NSE, disaster readiness, popular sentiment, fair balancing of network load, an increase in internal security index, a reduction in the downtime experienced at the company network services, and an improvement of insurance security index (Wright, 2012).
The rationale for the achievements is because of the application of Cyber defenses, which include firewalls, antivirus software, regular operating systems updates, regular patches, and
Table 3: Cyber defense
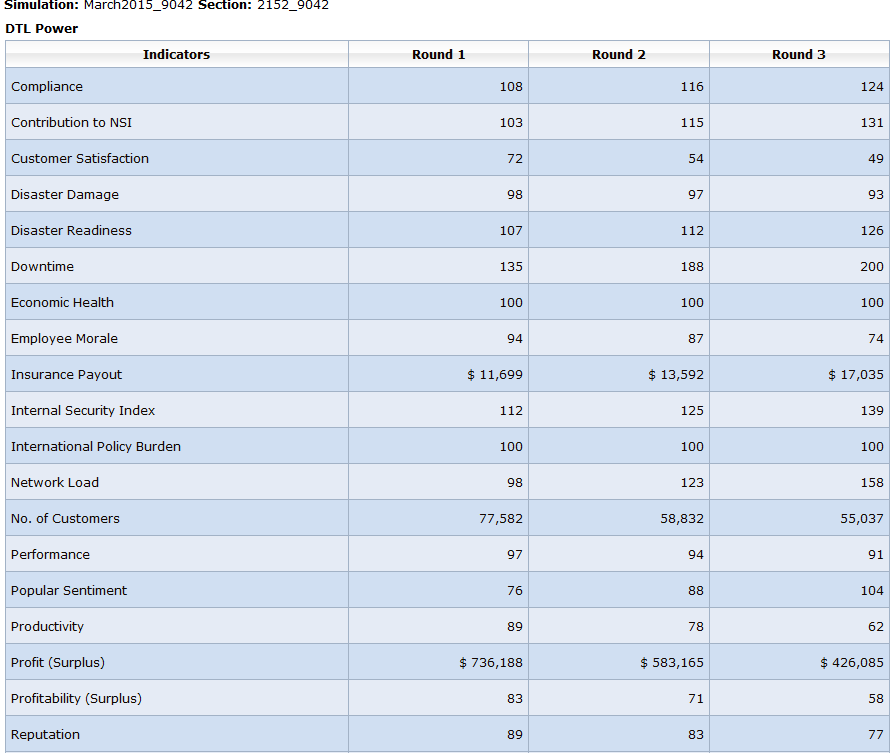
Conclusion
In conclusion, the simulation showed that there was a for the company to improve its Cyber defenses by implementing appropriate controls, which include firewalls, intrusion detection and prevention tools, universal threat management tools, antivirus software, and constant and constant updates, and regular patching of the operating system.
In addition, the study showed that training employees on the basic Cyber prevention skills were necessary to enable them prevent Cyber-attacks that are perpetrated though social engineering techniques and the spread of malware on the Internet.
In addition, the use of data encryption techniques such as algorithms, load balancing techniques, and other techniques underpins the successful implementation of controls to ensure profitability and operational efficiency of the controls.
References
Agresti, W. W. (2010). The four forces shaping cybersecurity. Computer, 43(2), 0101- 104.
Assante, M. J., & Tobey, D. H. (2011). Enhancing the cybersecurity workforce. IT professional, 13(1), 12-15
Ten, C. W., Liu, C. C., & Manimaran, G. (2008). Vulnerability assessment of cybersecurity for SCADA systems. Power Systems, IEEE Transactions on, 23(4), 1836-1846.
Wright, K. (2012). Cybersecurity roundtable: The enemy is unknown. Electric Light & Power, 90(2), pp. 28-31.