Introduction
Background
The rapid adoption of digital solutions is exposing schools to the cyber-security threat, which is currently the biggest concern that these institutions face as they make a complete shift from the analog to the digital data management systems (Chishti & Puschmann, 2018). According to a K-12 Cybersecurity Resource Center (2021) report, a staggering 1,180 incidents have been reported since 2016.
A recent Cyber Security of UK institutions found that cyber breaches and malicious attacks were prevalent in both business and education organizations in the last 12 months (Ipsos Synovate, 2020). As technology becomes central to the overall running of educational institutions, it is important to examine the new threat in order to find effective ways of addressing it (Christiansen & Piekarz, 2019).
Nature of Cyberattacks
According to a recent K-12 Cybersecurity Resource Center (2021) report, there has been a dramatic rise in frequent and severe K-12 cyber-attacks in educational institutions. The most prevalent cases involve unauthorized disclosures or breaches, ransomware, Denial of Service (DoS), phishing, hacking, and other attacks that are increasingly becoming severe and frequent. Techno-savvy criminals have perfected the strategy of illegally accessing sensitive data belonging to students, lecturers, specific administrators, or the institution at large with malicious intentions (Grieco et al., 2019).
Cybercriminals have been trying to hack into databases of such institutions with the aim of stealing the formula and selling it to other institutions around the world (Tallón-Ballesteros & Chen, 2020). Such intellectual property theft is a major concern to these institutions. Hacking may be targeted at manipulating information in the database of a learning institution. The financial department is always the leading target of these cybercriminals. Their goal is always to steal from the institution using different strategies (Berman et al., 2019).
Some criminal-minded students may hack the system and update their payment details with the goal of defrauding the institution. A hacker may target a student’s portal and manipulate data in various ways. Ransomware attacks are also increasingly becoming common, and they often target lecturers and administrators (Erendor & Öztarsu, 2020). Other major threats include Trojans, botnets, wiper attacks, and Distributed Denial of Service.
The Problem
Rapid digitization that has been witnessed in various learning institutions in the Kingdom of Saudi Arabia and around the world over the past decade has exacerbated the problem of cyber-attacks. The problem is that despite the serious danger that cyber insecurity poses to these educational institutions, they do not have the option of moving back from digital to analog data management systems (Nguyen & Reddi, 2020). These institutions have to continue using digital data systems because of the technological changes that have been taking place in the recent past. They have to learn how to manage the threat and operate secure digital platforms that protect learners, teachers, administrators, and institutions.
Factors Exacerbating Cyber Insecurity
Limited budget is a serious challenge that limits the ability of these institutions to fight cybercrime effectively. According to Williams and McDonald (2018), most of these educational institutions cannot afford to set aside a significant amount of their resources to fight cybercrime as they rely hugely on government funding and school fees. The income goes to the payment of staff, purchasing of consumables needed in the institution, and paying other bills. As such, setting aside a significant amount of money to install some of the latest software and pay for highly qualified experts is an issue. In addition, the country still lacks legislation that can help in prosecuting those who steal or manipulate data from these institutions (Kumar, 2020).
Cybercriminals may be prosecuted for a misdemeanor, which is a minor offense that cannot deter such actions in the country. The few cyber-security policies that have been enacted do not classify learning institutions as major victims of such attacks. As such, they have not been given priority when defining means and strategies for fighting cybercrime in the country. The cyber-security threat has worsened the tendency of students and staff to use personal devices such as personal computers, iPads, tablets, or smartphones to access these sensitive databases. Criminals take advantage of these security gaps to access information that they need (Nguyen & Reddi, 2020). Thus, it is necessary to find ways of addressing the problem to ensure that these institutions are protected.
Clear Statement of Aim
It is evident that learning institutions in the country and around the world are faced with serious cyber-security threats. As explained above, the problem cannot be solved by walking back technology and reverting to the analog approach to managing data. Instead, stakeholders have to find ways of ensuring that these educational institutions operate without being adversely exposed to cyber insecurity. The aim of this study is to investigate cyber-security threats that these institutions face and develop solutions that they can embrace to ensure that their data is protected from any form of attack.
Objectives
- To assess the nature, magnitude, and frequency of cyber-attacks that target educational institutions in the country.
- To identify departments that are more vulnerable to these attacks in these institutions.
- To determine the impact of cyber-attacks on the normal operations and success of learning institutions in the country.
The Project Plan
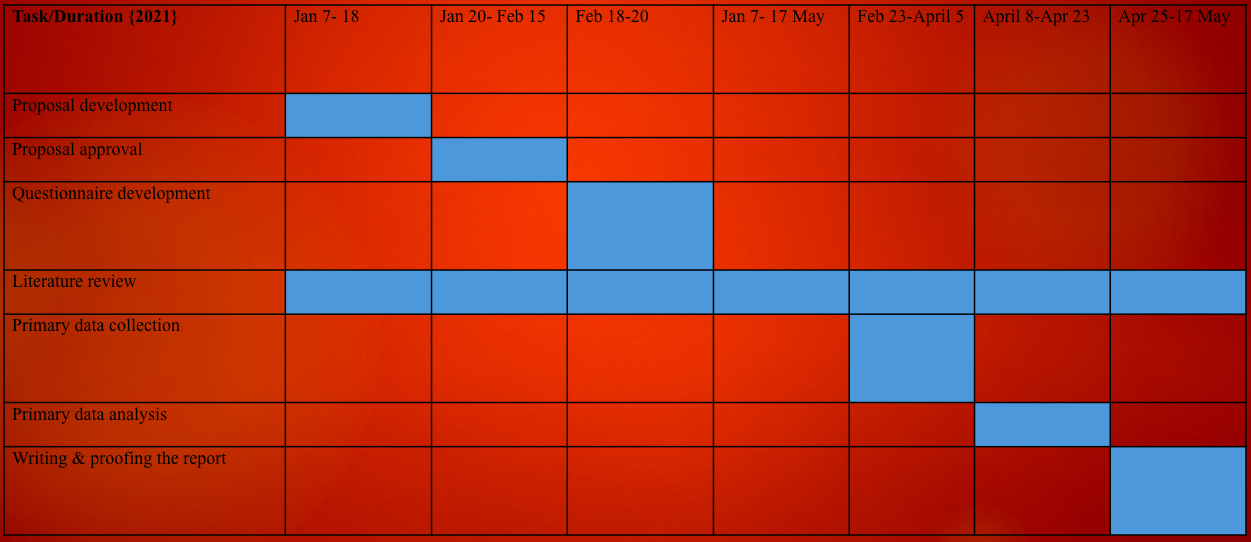
When conducting a research project, it is important to define in clear terms tasks specifications, and durations that they are supposed to take for them to be completed. The project plan helps in determining how each activity should be taken to enable the researcher to achieve the desired goals. In this section, the researcher defines these tasks and the duration that it will take to ensure that they are completed. The first task of developing the proposal was to take about 11 days, from January 7th to January 18th, 2021.
Proposal approval was expected to take about two weeks, from January 20th to February 15th, 2021. Questionnaire development took a relatively short period of two days, from 18th to 20th February 2021, because research questions had been defined. A review of the literature was a continuous process. From January 7th, 2021, when developing the proposal to April 25th, 2021, when writing the final report. Primary data collection took over six weeks, from February 23rd to April 5th, 2021.
Data analysis of primary data collected from these participants took about two weeks, from 8th to 23rd April 2021. Writing the report and proofing it, which was the last step, took about three weeks, from April 25th to May 17th, 2021. The completed report will then be delivered as per the regulations set by the school and within the time that was specified.
Literature Review
Overview
Based on the review of existing literature on cyber security in an educational institution, this review established that this topic had attracted a lot of attention from researchers and practitioners. This interest manifests in the growing literature on c cyber-attacks covered in this review. However, despite the existence of extensive research in this area, most of the studies focused on cyber-security threats to online learning. Topics such as severity, frequency, impacts, and solutions to this problem are adequately covered. Literature reviews and opinion briefs were common methodologies, but a few studies used structured questionnaires.
Critical Analysis
The article by Adel et al. (2019) provides a clear picture of e-learning and its growing adoption in higher education institutions. The authors conduct a comprehensive review of existing literature on the online education approach, which helps readers understand the nature, trends, advantages, and limitations of e-learning. This source is relevant to the research because its content helped to provide a strong background to the study. However, the article lacks depth because very few sources are included, and most of them are not current.
In their journal article, Aliyu et al. (2020) advanced a more comprehensive, internet-based framework for analyzing and assessing security vulnerabilities and potential threats in online systems. This study is relevant to the research project because it details an array of cyber threats to educational institutions. Furthermore, the article offers metrics that educational institutions can utilize to measure their competency or maturity in relation to online learning adoption. Besides that, the authors propose a security assessment model, which, unlike other conventional frameworks, incorporates relevant regulations. The major limitation of this study is the lack of primary data.
In this journal article, Coleman and Reeder (2018) provide a nuanced discussion of major reasons why educational institutions need to invest more resources in improving the security and integrity of their information communication systems. The authors draw on a wide range of literature and empirical evidence to support their arguments. In addition, it integrates old and current literature which helps capture current issues and debates on cyber security in learning institutions. However, the authors rely heavily on secondary data and personal opinions, which weaken the validity and reliability of their arguments.
Muniandy et al. (2017) conducted an empirical investigation to examine the current state of cyber security behavior of college and university students in Malaysia. The researchers explored how the learners use passwords and their knowledge about key attacks such as phishing, malware, internet-based scamming, and social engineering. Unlike previous studies, this study employed a structured questionnaire to gather primary data from the participants. Analysis of the collected data revealed that a majority of the learners exhibited unsatisfactory knowledge levels across all five security threats. The use of a structured data collection tool enhanced the validity and reliability of the research results. Furthermore, this instrument enables the researcher to recruit a large sample, which also enhances the overall trustworthiness of the study. However, the rigidity, structured, and non-participatory nature of this tool did not allow the investigators to gain a nuanced understanding of the research problem.
Methodology
Overview of Research Methodology
Limited studies have narrowed down to how local educational institutions in the Kingdom of Saudi Arabia are affected by the problem of constant cyber-attacks. Therefore, this study examined how these institutions are affected by this problem to find ways of developing local solutions. As such, collecting primary data from local stakeholders in the education sector was essential. This chapter explains how participants (subjects) were identified, sampled, and involved in the process of collecting data. The chapter also explains the instrument used in the process of collecting data, the procedure, and the statistical analysis that was conducted to help in answering the research questions. The chapter ends by explaining the challenges faced and ethical considerations that the researcher observed.
Subjects
The researcher had to collect data from stakeholders in the education sector who could explain the cyber-security threats that they have encountered in their normal operations. The researcher used a stratified sampling method to select 50 participants. The first group was the administrators responsible for ensuring that these institutions were running smoothly. The second group was the teachers who are currently using cyberspace and other modern technologies to facilitate the learning process. The third group was learners who are currently using information technology to enable them to acquire new knowledge. The researcher selected two institutions of higher learning to facilitate the process of collecting data from these three groups of respondents.
Instrumentation
It was necessary to develop an instrument to facilitate the process of collecting data from the sampled participants. A questionnaire helps to harmonize the collected data and ensures that every participant is given the same question that can then be used to facilitate the analysis (Politano et al., 2018). It also eliminates cases where a researcher forgets to ask critical questions needed to respond to the main research questions. The researcher developed a questionnaire with three sections. The first part of the questionnaire focused on the demographical factors of the respondents. The second part of the document focused on the experience and academic qualifications of the participants. The last section of the instruments focused on specific issues related to cyber-security threats to educational institutions within the country.
Research Procedure
The process of collecting data from the sampled participants started with seeking permission from the management of the two institutions before contacting individual participants. After that, the researcher reached out to individual respondents to obtain their informed consent. The goal of this study was explained to them, and they were informed of the reason why they were selected. Only those who agreed to be part of this study were engaged in the process of collecting data. The researchers emailed questionnaires to these participants. The email explained how they were expected to respond to the questions. The researchers made a follow-up with every respondent to remind them that the document had been emailed to them and that they were expected to email back the filled questionnaire. The process of collecting primary data took two weeks.
Statistical Analysis
When primary data had been collected from the participant, it had to be processed to help in responding to the research questions. According to Mallette and Duke (2020), one can use qualitative, quantitative, or mixed-method to process primary data. The choice of the method depends on the nature of the questions that have to be answered. In this study, statistical analysis was the most appropriate method of answering questions. The quantitative method used structured questions, and the participants were instructed to select answers that best responded to each of the questions asked. Data obtained from the participants were coded into an excel spreadsheet. The software was then used for the computation and generation of various outputs depending on the nature of the question that had to be answered.
Challenges Faced and Ethical Considerations
The process of collecting primary data was affected by some challenges which are worth discussing at this stage of the report. One of the major challenges was the inability to physically interact with the participants because of the COVID-19 restrictions. Face-to-face interviews were the most preferred approach for collecting primary data and could not be used in this investigation due to COVID-related restrictions. The researcher had to rely on online platforms to gather the needed data. When conducting this study, the researchers were keen on observing ethical considerations. Consistent with Baron and McNeal (2019), the researcher ensured that the identity of those who took part in the study remained anonymous. Instead of using their actual names, they were assigned codes from Participant 1 to Participant 50. The researchers obtained informed consent from each participant before they could start answering the questions. All forms of plagiarism were avoided, and information obtained from secondary sources was referenced accordingly using American Psychological Association (APA) seventh edition style.
Results and Findings
Nature and Magnitude of Cyber-Attacks
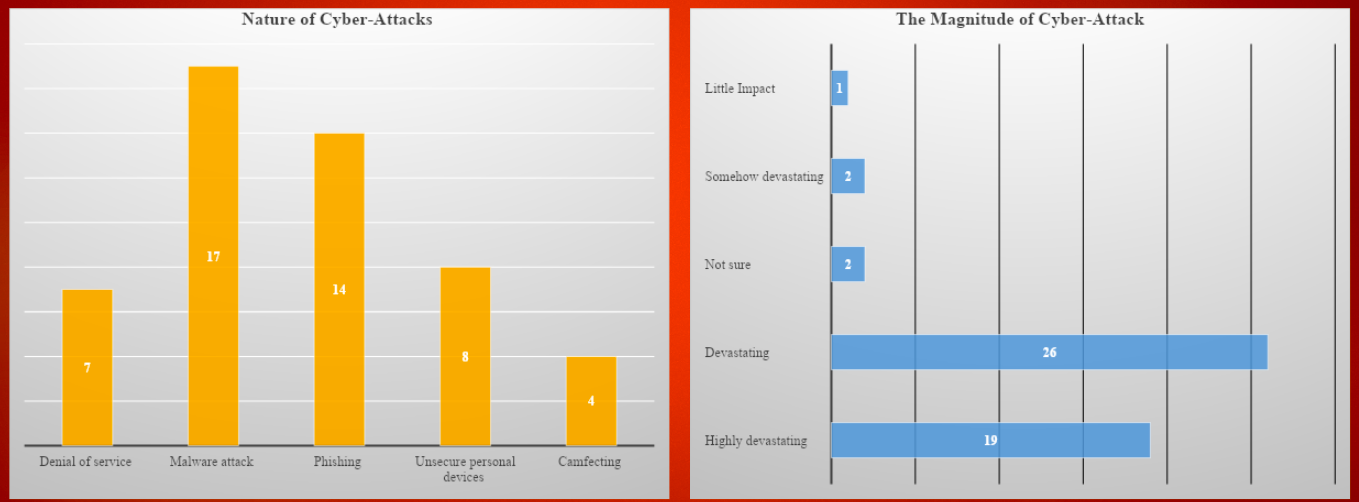
Malware attack is the most common cyber-attack at these institutions. It affected all the stakeholders, irrespective of their department. Phishing was the second-most common form of cyber-attack at these organizations. The respondents identified unsecured personal devices as another common problem. Denial of service (D-o-s) and camfecting were the other challenges that these respondents identified. The findings of this study confirmed the high perverse nature of cyber-security threats in the existing literature. An overwhelming majority (94%) of the participants believe that cyber-attacks have a devastating impact on the normal operations of these educational institutions. 38% of the respondents (19 out of 50) stated that cyber-attacks have a highly devastating impact. Another 52% of the respondents (26 out of 50) stated that the impact is devastating, while 4% believed that it is somehow devastating.
Frequency of Attacks and most Affected Departments
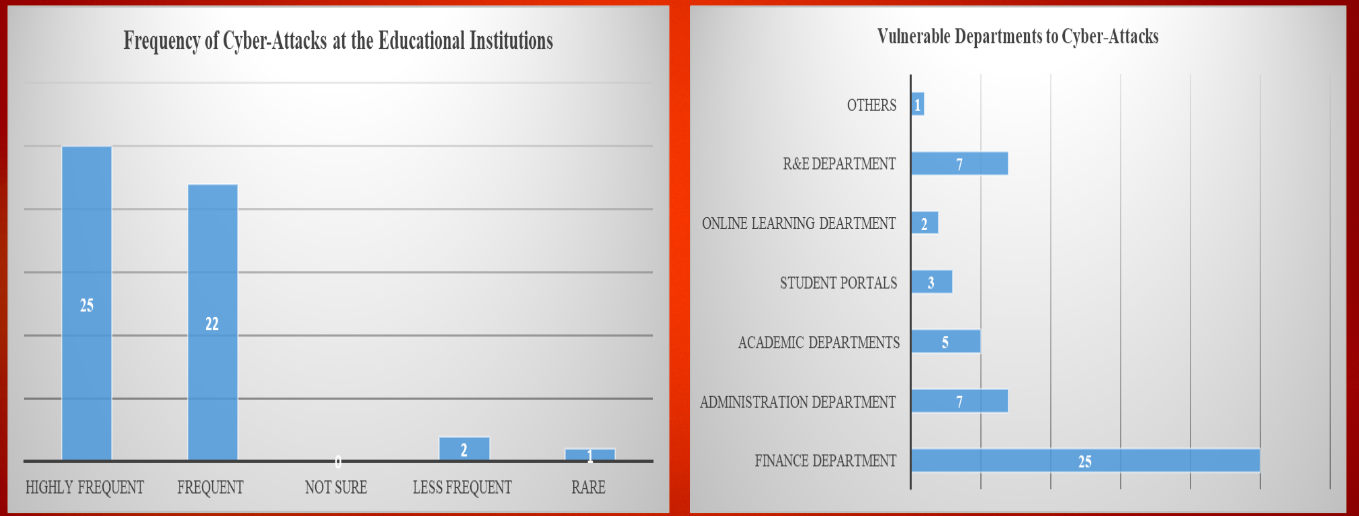
An overwhelming majority of the participants (94%) believe that these attacks are frequent at the selected institutions. 50%, 44%, and 4% of the respondents stated that these attacks are highly frequent, frequent, or less frequent, respectively. The finance department is the most vulnerable unit, with 50% of those interviewed identifying it as the most vulnerable department. The administration, research and extension, online learning, academic department, and students’ portals were also at great risk of cyber-attacks.
Impact of Cyber-Attack on Educational Institutions
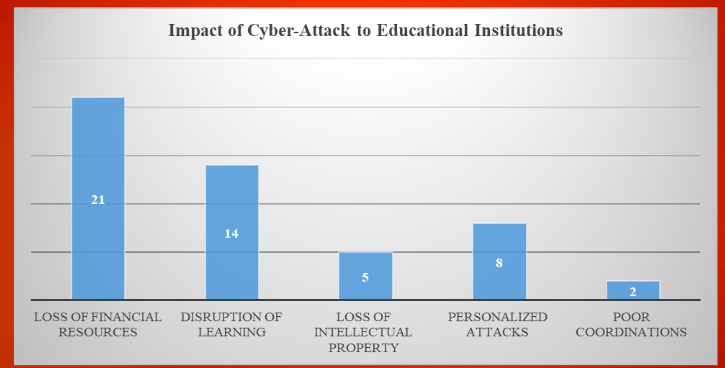
The biggest impact of these attacks is the loss of financial resources. This finding confirms previous research results showing that most of these cybercriminals are often targeting the finance departments of these organizations. There is also the massive disruption of learning when they attack digital instruments that are meant to facilitate the normal learning process. Personalized attacks on students, the teaching staff, and the non-academic staff may also disrupt the learning environment. Loss of intellectual property is another issue that institutions face when attacked. Some of the respondents felt that when there are such attacks, there would be poor coordination of activities, especially when the communication system is compromised.
Conclusion
Many learning institutions are transitioning from analog to digital data management systems. Online learning is becoming a dominant approach to education delivery due to its cost efficiencies and enhancing access to higher education. This trend is exacerbated by the COVID-19 containment measures. However, these impressive steps have been significantly affected by the continued cyber-attacks that these institutions face. Cyber-attack is a major threat to the success and normal operations of educational institutions. This investigation established that the institutions that were surveyed were not ready to deal with the threat associated with the new system. The attack has led to the loss of finances for these institutions, loss of intellectual property, cases of blackmail, and other forms of online harassment.
Recommendations
The management of educational institutions and policymakers in the country should find a way of addressing the problem of cyber-security threats in the country. They have to put in place policies and infrastructural systems that will ensure that sensitive data for these institutions remain as secure as possible. The following are the steps that they should consider to address this problem:
- Every education institution should have internal policies meant to minimize the capabilities of cybercriminals;
- They need to invest in emerging technologies meant to protect their databases;
- These institutions need to work closely with cyber-security experts to help in monitoring and managing these threats;
- The government should enact strict policies that can ensure that cyber criminals are severely punished to discourage such practices;
- The government should increase the financial allocations of educational institutions to enable them to fight cybercrime effectively.
Challenges and Future Research
The process of collecting primary data was affected by some challenges which are worth discussing at this stage of the report. One of the major challenges was the inability to physically interact with the participants because of the COVID-19 restrictions. Face-to-face interviews were the most preferred approach for collecting primary data and could not be used in this investigation due to COVID-related restrictions. Furthermore, the pandemic made it difficult to draw a large sample and some participants. As a result, the researcher had to rely on online platforms to gather the needed data. Further research should consider using large samples and studying multiple schools to compare findings. Future research should use face-to-face methods such as personal interviews to gain in-depth knowledge into the nature, frequency, and impact of cyber-attacks in educational institutions.
References
Adel, E., Elsawy, M., & Ahmed, S. (2019). E-Learning using the Blackboard system in light of the quality of education and cyber security. International Journal of Current Engineering and Technology, 9(1), 49-54.
Aliyu, A., Maglaras. L., He, Y., Yevseyeva, I., Boiten, E., Cook, A., & Janicke, H. (2020). A holistic cybersecurity maturity assessment framework for higher education institutions in the United Kingdom. Applied Sciences, 10(1), 1-15.
Coleman, C. D., & Reeder, E. (2018). Three reasons for improving cyber-security instruction and practice in schools. SITE, 26(30), 1020-1024.
Hasan, R. (2017). Protect a university website from the different types of outside attacks. Journal of Advanced Computing and Communication Technologies. 5(4), 109-114.
Muniandy, L., Muniandy, B., & Samsudin, Z. (2017). Cyber security behavior among higher education students in Malaysia. Journal of Information Assurance & Cyber security, 7(1), 1-12.
Nguyen, T., & Reddi, V. (2020). Deep reinforcement learning for cyber security. Cryptography and Security, 3(1), 1-11.