Introduction
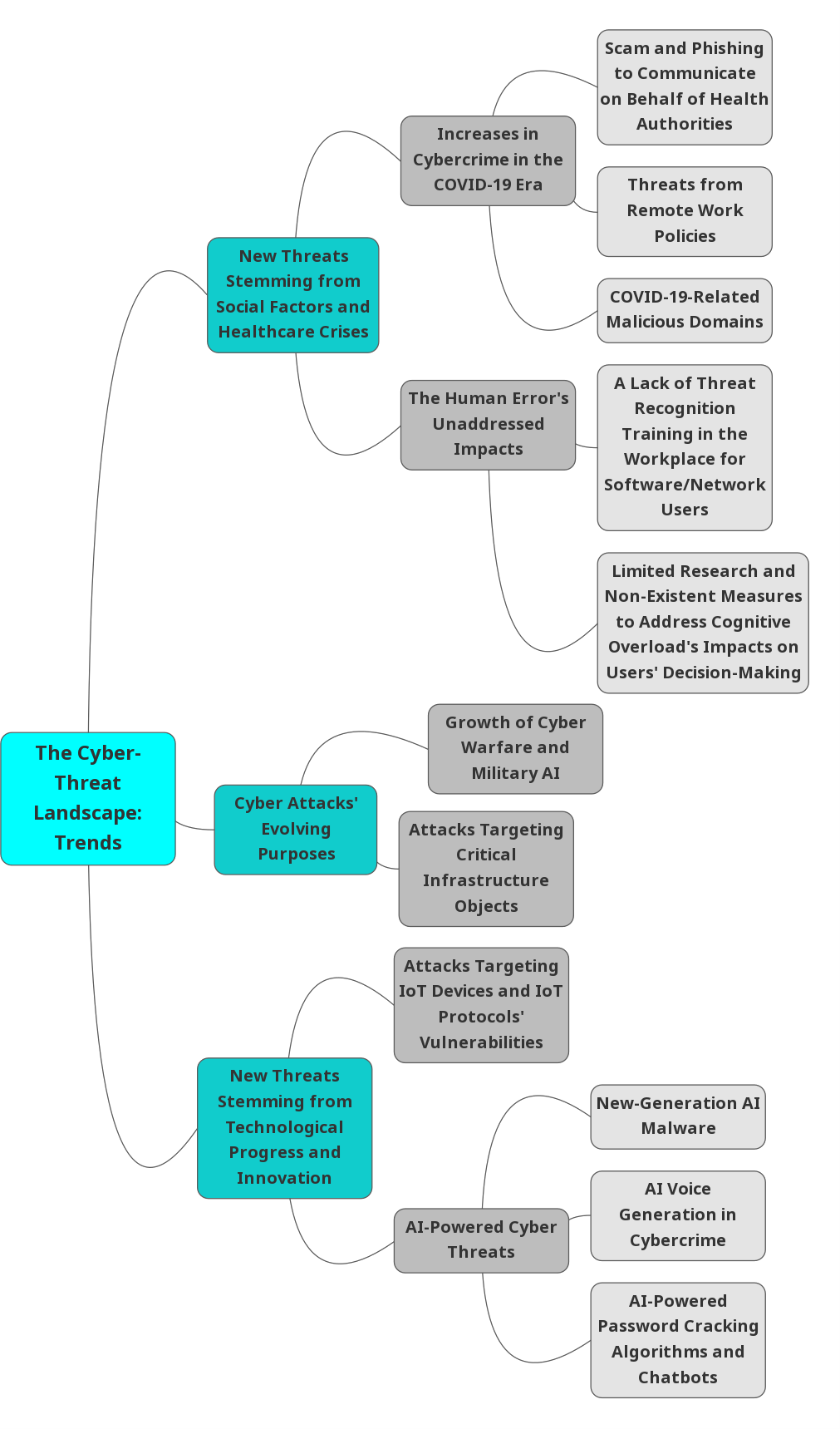
As a complex term, the cyber-threat landscape pertains to the full scope of risks and malicious acts in cyberspace that already take place or keep emerging. New tendencies and types of threats can result from diverse sources, ranging from external socio-economic challenges to the incorporation of the most recent technology into attack methodologies. This chapter reviews trends in the threat landscape, including human mistakes, crisis events, the growth of artificial intelligence (AI) and the Internet of Things (IoT), and the evolution of cyber-attacks in terms of purposes.
Literature Review
Trends Related to Social Factors and Healthcare Crises
The COVID-19-related growth of cybercrime represents a prominent trend in the threat landscape. The disease pandemic has stimulated an increase in online service utilization, widening the ill-intentioned parties’ opportunities for implementing social engineering and revealing common audience’s digital hygiene knowledge deficiencies (Alsharif et al., 2022; (Chokhonelidze et al., 2020). As per the International Criminal Police Organization, phishing and scamming have grown in prevalence in over 65% of its 195 member states, with cybercrime agents seeking to misrepresent themselves as healthcare authorities or vaccine researchers (Alexander & Jaffer, 2021). The malicious domain registration rate experienced a six-time increase during only the initial two months of the pandemic, revealing fraudsters’ prompt adaptation to social realia and nations’ most prevalent fears (Alexander & Jaffer, 2021; Chokhonelidze et al., 2020). The reports of COVID-19-related scam attempts have been intense, including robotic calls for identity theft, vaccine sales ads, the offers of disease relief payments in exchange for users’ financial data, and so on (Alexander & Jaffer, 2021; Alsharif et al., 2022). Internet users can be acquainted with suspicious offers, but mass panic and the fear of uncertainty enable fraudsters to succeed.
Another critical trend is the intensification of external cybersecurity risks resulting from COVID-19-induced remote work. Businesses’ increased implementation of work-from-home policies has given rise to implementing shadow/unsanctioned IT, decreasing IT departments’ control over devices and software used for work completion, as well as sensitive data transfer processes (Alexander & Jaffer, 2021; Chokhonelidze et al., 2020). The normalization of telework has popularized software solutions for remote access, enabling cybercrime actors to benefit from such programs’ security-related deficiencies and resulting in heightened attacks against Microsoft Remote Desktop and Citrix Workspace (Alexander & Jaffer, 2021; Chokhonelidze et al., 2020). Common software users’ cyber hygiene deficiencies become a crucial challenge in this regard.
As the threat landscape keeps evolving due to technological progress, the human factor’s role as a contributor to successful cyber attacks and breaches also increases, calling for this role’s recognition and massive action to increase common users’ cybersecurity literacy. In business contexts, access to the latest and more complex IT solutions informs organizations’ competitive advantage maximization strategies, but human users’ increased susceptibility to security-compromising mistakes remains underestimated (Alsharif et al., 2022; Djenna et al., 2021; Nobles, 2018). Based on empirical and field research, human users’ flawed decision-making is
found to cause 80%-86% of cyber-security incidents, and IT systems’ increasing complexity might make keeping track of security in multiple applications exhausting and challenging (Nobles, 2018). This creates an urgent need for implementing cybersecurity policies and training ubiquitously.
The popularity of IoT ecosystems that are susceptible to interception in the healthcare field brings the human error problem and education to the forefront. As Djenna et al. (2021) highlight, IoT users’ insufficient cybersecurity awareness/informedness and limited critical thinking maximize their susceptibility to social engineering endeavors, making users the weakest part of organizational cybersecurity chains. As the Verizon agency’s global data breach research suggests, within the last five years, social engineering tactics’ popularity has increased to be represented in more than 40% of all breach incidents (Nobles, 2018). According to investigations into end-users decision-making factors in cybersecurity, matters suggest an increased reliance on individual values and knowledge, which results from weak or non-existent cybersecurity education at the organizational level (Alsharif et al., 2022; Nobles, 2018). The presence and quality of IoT end-user education cause the exacerbation of the existing threat landscape.
Trends Linked to Technological Growth and Innovation
Like many prominent fields that could benefit humanity and protect cybersecurity, AI is becoming malicious actors’ helpful resource, causing AI-based applications’ increasing role in the global cyber-threat landscape. AI-powered malware first appeared in 2018, with the emergence of IBM’s experimental DeepLocker tool preventing the attack payload from detection (Kaloudi & Li, 2020; Thanh & Zelinka, 2019). Hypothetically, malicious software developers can implement AI by using four sets of techniques, including smart evasion of detection by anti-malware solutions and AI-powered autonomous software that is yet to be developed (Thanh & Zelinka, 2019). Adversarial attacks to interfere with AI systems’ prediction accuracy and swarm algorithm development/implementation to create malware capable of learning and evolving are other trends (Thanh & Zelinka, 2019). Other novel threats coming from AI are represented by voice imitation opportunities, such as the Lyrebird voice cloning algorithm, password-focused cyber attacks that would be possible using PassGAN or similar techniques, and chatbot weaponization to facilitate stealing personal information (Kaloudi & Li, 2020; Thanh & Zelinka, 2019). The promise of AI applications for malicious actors is, therefore, enormous.
With IoT’s development, attacks on IoT systems have shaped another tendency in the threat landscape. As per Symantec Corporation’s estimates, IoT devices that are recently installed take up to 120 seconds to be scanned and detected by hacking groups using network vulnerability assessment techniques (Nobles, 2018). IoT protocol-related vulnerabilities have been demonstrated in researcher-organized attacks on IoT smart lighting systems, IoT-enabled wireless lock solutions, and entire smart home systems (Kaloudi & Li, 2020; Pour et al., 2019). Cyber attacks on IoT devices, according to an investigation by Pour et al. (2019), are already prominent, with compromised appliances found in manufacturing facilities, factory automation infrastructure objects, and healthcare facilities.
Cyber Attacks’ Evolving Purposes: Warfare and Infrastructure
The growth of cyberwarfare has been expanding the threat landscape in terms of attacks’ purposes. Cyberwarfare, along with cybercrime’s various types, keeps becoming more complex, which results from cyberspace’s properties as a business field, including high transparency, weak entry barriers, and anonymization methods (Li & Liu, 2021; Thornton & Miron, 2020).
Prominent political actors keep developing cyber capabilities for active and protective military operations, with AI’s role in warfare creating division (Thornton & Miron, 2020). In opposition to the United States, the United Kingdom, and China, Russia’s authorities seek to center AI research around exploring its military applications, resulting in the AI-using Sukhoi S-70 drone (Li & Liu, 2021; Thornton & Miron, 2020). AI is envisioned to facilitate malware planting and give rise to large-scale misinformation and fake news generation applications, thus taking war propaganda strategies to the next level (Li & Liu, 2021; Thornton & Miron, 2020). AI-enabled warfare remains an emerging trend at the intersection of technological and geopolitical factors.
The cyber-threat landscape keeps changing, reflecting the rapid growth of criminal parties’ knowledge of critical infrastructures’ security-related vulnerabilities. In 2015 or even earlier, healthcare services and public services, which are among the critical sectors, became the first and fourth most targeted industries in the context of cybercrime, respectively (Chokhonelidze et al., 2020; Nobles, 2018). With a five-fold increase in cyber attack incidence against the World Health Organization alone, healthcare agencies are facing even more threats compared to financially attractive targets, such as banking and manufacturing services (Chokhonelidze et al., 2020; Nobles, 2018). Considering the amount of sensitive data the sectors work with, successful attacks’ consequences can be disruptive in the long term.
Discussion: Challenges and Opportunities
Notably, the aforementioned trends reveal a series of challenges for academic researchers and practitioners in the cybersecurity field. Regarding the existing challenges, as the cyber-security landscape keeps evolving, attack prevention techniques and cybersecurity application development are not enough to address threats in their entirety. Specifically, the human factor’s status as an unaddressed barrier to security can potentially undermine security systems’ work, requiring effective solutions to spread security-related awareness and literacy on a global scale. Researching human-related vulnerabilities concerning “human nature” and investing in employee cybersecurity education should be emphasized (Alsharif et al., 2022, p. 1153).
Remembering the COVID-19-related increases in cybercrime against individuals and organizational actors, cybersecurity education for the common audience should emphasize fraudsters’ increasing activities during nationwide crises affecting people and businesses economically and in terms of health. IoT protection remains a separate challenge, requiring IoT operators to engage in concerted work and secure data-sharing initiatives while also emphasizing methods for reducing darknet traffic peculiar to IoT systems (Pour et al., 2019). With that in mind, the recent threat landscape presents various unresolved issues to explore.
Nevertheless, the trend-related information also reveals significant opportunities for cybersecurity professionals. There are emerging threats, including AI-enabled warfare and smart self-teaching malicious software. Both have not reached their full potential yet and remain highly speculative at the moment, enabling researchers to begin preventive work proactively. The recognition of such trends enables security solution developers to predict the ill-intentioned parties’ preferred ways of thinking and design ways for curbing and detecting more complex malicious activities.
Annotated Bibliography
Djenna, A., Harous, S., & Saidouni, D. E. (2021). Internet of Things meets Internet of Threats: New concern Cyber security issues of critical cyber infrastructure. Applied Sciences, 11(10), 1-30. Web.
According to the source, new trends in the cyber-threat landscape are inseparable from the emergence of IoT and IoT-based infrastructures. The growing number of IoT-connected appliances and devices, including Smart Health applications, creates more intense risks of cyber-attacks against healthcare information management systems and cyber-physical systems (CPS). Due to organizations’ increased reliance on non-physical informational assets utilizing IoT or global networks, cyber-attacks have become far more aggressive and methodologically complex.
The source’s relevance to the chapter’s topic stems from their thematic proximity. Trends in the cyber-threat landscape pertain to factors, innovations, or changes that alter the scope of data-related security threats. IoT’s popularization in various fields, including healthcare, enables the malevolent parties to instrumentalize IoT’s technological imperfections for their purposes, so the article helps characterize the current threat landscape.
Kaloudi, N., & Li, J. (2020). The AI-based cyber threat landscape: A survey. ACM Computing Surveys (CSUR), 53(1), 1-34. Web.
In their review, the authors seek to problematize AI-based applications’ recent growth as a factor in the current cyber-threat landscape and summarize the concept of AI-powered threats to cybersecurity. Based on the analysis of eleven scholarly studies of AI-empowered attacks, the researchers distinguish between diverse categories of threats from AI. These include AI-powered malware, AI voice generation, AI-based password crackers, chatbots, and so on.
The article is directly relevant to the chapter due to providing a detailed overview of recent AI-related cybersecurity threats. A combination of these existing and emerging threats reveals the role of increasingly complex AI applications as a multidimensional trend. This information will supplement a review of novel cybersecurity threats.
Li, Y., & Liu, Q. (2021). A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments. EnergyReports, 7, 8176-8186. Web.
The source contains a detailed overview of the cyber attack and cyber threat terms. It also clarifies the conceptual relationship between crime, warfare, and attacks in the context of cyber threats. Based on current tendencies, including the intensification of hardware/software production and governments’ increasing digitalization, the article problematizes cyber warfare’s growth. It features a multi-element classification of threats according to the actor/facilitating factor, including organized hacker groups, individual hackers, terrorist organizations, foreign geopolitical rivals, and intraorganizational/internal threats.
The article’s relevance stems from shedding light on the evolution of cyber threats in terms of purpose and the increasing use of technological progress as a means of warfare. By researching how progress facilitates the expansion of threats from local criminal acts to large-scale attacks on entire governments, the study supports the recognition of trends linked with cyber attacks’ goals.
Alsharif, M., Mishra, S., & Alshehri, M. (2022). Impact of human vulnerabilities on cybersecurity. Computer Systems Science &Engineering, 40(3), 1153-1166. Web.
The source explores both technology’s and human error’s roles in the increasing number of cyber threats. It explains the current cyber-threat landscape concerning IoT applications’ easy identification by ill-intentioned parties. Another tendency pertains to increases in cybercrime against critical industries, including healthcare, finance, and public services. The article also reveals fileless malware’s contributions to today’s cybersecurity-related risks for organizational actors.
Regarding relevance, the source offers an overview of large-scale tendencies affecting the landscape rather than local challenges. It popularizes the recognition of threat-related trends that deal with psychological factors and the mismatch between the pace of innovation and common users’ ability to control safety. With this focus, the paper is supportive of the chapter’s topic.
Pour, M. S., Bou-Harb, E., Varma, K., Neshenko, N., Pados, D. A., & Choo, K. K. R. (2019). Comprehending the IoT cyber threat landscape: A data dimensionality reduction technique to infer and characterize Internet-scale IoT probing campaigns. Digital Investigation, 28, S40-S49. Web.
Regarding its empirical component, the study proposes an L1-PCA-based technique for reducing the dimensionality of data and uses network telescope data to explore IoT devices’ sources of security deficiencies. The analysis reveals thousands of compromised IoT-connected devices in multiple sectors, including Internet providers, telecommunication technology, and businesses/services. Such devices also exist in non-commercial services, including healthcare and public agencies. IoT’s vulnerability to cyber attacks is, therefore, highlighted as a novel source of threats.
In terms of relevance, the source sheds light on the implications of the increased utilization of IoT in various environments for cyber security. Moreover, the very paradigm of IoT is conceptualized as a source of the cyber-threat landscape’s diversification and evolution. Thus, the article supports the discussion of attacks targeting IoT as a crucial trend in the scope of digital security threats.
Conclusion
Finally, the trends of importance include intensified cyber-attacks to profit from the fear of COVID-19, remote work’s cybersecurity-related pitfalls, and human error’s exacerbation resulting from higher cognitive loads in working with more complex software. Technological advancement, including IoT’s popularization and critical infrastructures’ digitalization, also inform changes to the threat landscape, and the emerging trends pertain to AI-enabled warfare and malware. To adapt to this landscape, cybersecurity actors should advocate for ubiquitous cybersecurity literacy promotion, keep investigating IoT vulnerabilities and human thinking, and continue experimentation with AI to prepare for addressing its potential for cybercrime.
References
Alexander, K. B., & Jaffer, J. N. (2021). COVID-19 and the cyber challenge. The Cyber Defense Review, 6(2), 17-28. Web.
Chokhonelidze, G., Basilaia, G., & Kantaria, M. (2020). Cyber threats and attack vectors during COVID-19. International Journal for Research in Applied Science and Engineering Technology, 8(10), 814-817. Web.
Nobles, C. (2018). Botching human factors in cybersecurity in business organizations. HOLISTICA–Journal of Business and Public Administration, 9(3), 71-88. Web.
Thanh, C. T., & Zelinka, I. (2019). A survey on artificial intelligence in malware as next-generation threats. Mendel, 25(2), 27-34. Web.
Thornton, R., & Miron, M. (2020). Towards the third revolution in military affairs: The Russian military’s use of AI-enabled cyber warfare. The RUSI Journal, 165(3), 12-21. Web.