Cyber Security Threat, its Nature, and Types
The term cyber threat is mainly used to describe information security issues. It is a crime aimed to steal information, damage data, or ruin digital life. Cyber security threats can take such forms as phishing, spying, DoS attacks, data breaches, cyber fraud, politically motivated attacks, and so forth. Not all malicious cyber actions can be considered cyberwar. Some cyberattacks are aimed to harm individuals, steal their personal information, or disrupt intellectual property. Others make part of cyberwarfare and are defined by Aboul Enein (2017, 16) as “the use of force to cause damage or destruction for a political purpose by states or political groups.” This presentation will discuss cyber security threats, their impact on UAE international security, and ways to address them.
Imranuddin (2017, 30) distinguishes the following types of cybercrime:
- Hacking. This type of cyber offense involves impinging upon and changing software or hardware which is not protected adequately by creators.
- Data breach. It means that some critical information is stolen from a system without permission. Data breaches can happen to both large and small organizations.
Cyber Threats in United Arab Emirates
The issue of cyber threats has been a point of multiple concerns in the UAE recently. In 2018, the UAE government and private sector were the subject of a total of 230 cyber attacks, as The National UAE reports (“More Than 200 Cyber Attacks So Far This Year,” 2019). The described statistics is quite troubling, even given the global trends. Specifically, the 2019 reports mention 80,000 cyber attacks per day in 2018 (“The Ultimate List of Cyber Security Statistics for 2019,” 2020). Therefore, immediate measures are overdue so that cybercrime could be addressed in the UAE.
Common Cybercrimes in the UAE
Currently, several types of cybercrimes appear to be prevalent in the UAE environment. Among these, financial fraud is the most frequently committed one (“The Rise of Cybercrime in Dubai and UAE,” 2015). Financial fraud poses the greatest threat to cybersecurity in the UAE since, in most cases, the threat causing a rise in cybercrime rates comes from within organizations (“The Rise of Cybercrime in Dubai and UAE,” 2015). Therefore, the level of cybersecurity needs to be updated to protect UAE organizations from malicious intents of some of its less trustworthy staff.
As far as the types of attacks that the UAE owners of online data have to face on a daily basis, one should mention ransomware and adware. According to the 2015 data, AdWare.Win32.BetterSurf.b was the most notorious ransomware in 2014, having infected more than 1,228,000 computers (“The Rise of Cybercrime in Dubai and UAE,” 2015).
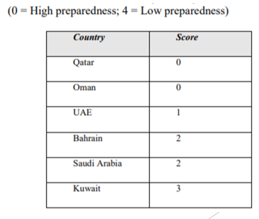
Preparedness of the Middle East countries for cyberattacks
In general, the Middle East countries demonstrate different levels of preparedness for cyberattacks, with the UAE being among the most prepared ones (Chandra et al. 2019).
Laws that ensure cyber security in the UAE
When speaking about the UAE governmental methods of addressing cyber threats, it is crucial to mention its cyber legislation. There are two primary laws that ensure cyber security in the UAE. They include Federal Law No. 1 of 2006 that governs transactions and e-commerce and Federal Law No. 5 issued in 2012 and aimed to assist in combatting cyber security. The latter has changed the definition of a privacy breach, expanded the list of offenses and penalties (Imranuddin 2017).
According to the law No. 5, any unpermitted access to websites or data is considered an offense charged under liability standards. Penalties are applied if anyone tries to access websites, systems, or sensitive data without authorization. Disruptors might be deported or committed to prison. The law controls the policy connected with international communication and data technologies. It also enacts penalties for other cyber violations such as spreading pornography, insulting religious traditions, casting aspersions on public officials, falsifying documents, stealing passwords, pin codes, and other financial data (Imranuddin 2017).
Cybercrime Threat Analysis
National Interest Scale
With the rise in attention to the problems of cybersecurity, the perception of the subject matter as the issue of the national interest has grown substantially. Therefore, on the national interest scale, the concern of cybersecurity and the reduction in the levels of cybercrime can be regarded as quite high. Indeed, given the 2006 and 2012 regulations that the UAE government established as the means of protecting its citizens, the extent of national interest toward the problem has grown. However, with no additions to the current regulations despite the time passed since their adoption, the national interest rates may reduce, which will contribute to a rise in the level of threat.
Use of History
Using retrospective analysis to evaluate the current problem of cyberattacks , on will notice that the level of threat from cybercrime tends to increase as digital technologies become more complex. However, the existing UAE regulations have not been updated accordingly, which creates additional obstacles to improving the rates of cybersecurity. For instance, in 2011, the number of cyberattacks in the UAE amounted to 588; however, in 2020, the specified issue has risen to 70,000 for smartphones alone (Gulf Information Security Expo and Conference, 2020). In turn, the regulatory strategies have remained the same.
UAE and U.S.
The outlined information is quite troublesome, even though the threat of cyberattacks has become ubiquitous across the globe. Indeed, comparing the existing strategies for addressing cybercrime in the UAE to those of other countries, including those in Europe and the U.S., one will find similar concerns. For instance, in the U.S., the rise in reported cybercrimes (approximately 1,300 per day) and a total of more than $3.5 billion damage to organizations have shown the need for tougher cybercrime regulations and an enhanced framework for cybersecurity (Federal Bureau of Investigation, 2020).
Logical Fallacies in Addressing Cybersecurity Issues in the UAE
Likewise, the application of the analysis driven by the identification of common logical fallacies in the discourse will help to determine the nature and extent of the threat.
Ad Hominem
The ad hominem fallacy, which occurs most frequently when discussing the problem of cybersecurity, suggests that it is natural for people to make mistakes, including the errors that they make when managing online interactions (Butwick and Weiniger, 2019). Therefore, the specified assumption suggests that reinforcing cybersecurity further or trying to educate people in the issue of cybersecurity is pointless. The described sentiment is quite far from the truth; moreover, it prevents effective dissemination of knowledge about cybercrime prevention.
Onus Probandi
Another type of fallacy, onus probandi, or the burden of proof, is often used to reduce the impression of threat that the presence of cybersecurity issues entails. Namely, a range of sources of information fail to provide sufficient evidence to support their claims concerning high security rates of digital data, which leads to misinformation. The described issue occurs in the UAE setting quite often, with newspaper rarely shedding enough light on the problem of cybersecurity (Dederer and Singer, 2019).
The Ways to Address Cyber Security Threats in the UAE
Presently, the fine for cybercrime ranges from AED 250,000 to 500,000. At first glance, the price to pay is quite ample. However, the specified measure appears to be lacking efficiency due to the low effect of the legal repercussions. Although the fine is quite large, potential perpetrators do not face an incentive powerful enough to make them avoid cybercrimes (UAE Department of Justice, 2020). Therefore, extra repercussions, including a jail time, must be added to the list.
In addition, increasing the level of education among average users should be central to the mitigation of cybercrimes in the UAE. Although updating the existing regulations and reinforcing the security system will play a vital role in reducing the risks, it will also be essential to ensure that the human factor should not become a source of threat. Therefore, cybersecurity education should be made readily available to all users as a part of the national security program. The specified service should be advertised copiously on all possible platforms, especially social media sites.
Educational institutions, Society, and Industry
Educational institutions
UAE educational establishments play a pivotal role in strengthening cyber security. They aim to educate prospective cyber security employees that would protect the nation from any cyber threats. It is also crucial to cooperate with industry working groups to keep the knowledge up-to-date and useful. Cyber security should be included in special training programs and courses at universities. The UAE has already created several centers focused on cyber security research; for example, the Information Security Research Center at the Khalifa University (Chandra et al. 2019). The UAE has a vast number of long-term educational projects; one of them is to build a cyber security academy.
Society
UAE residents should be taught how to prevent and address possible cyber threats. The new generations should be aware of how to surf the Internet safely and protect their personal information. According to Chandra et al. (2019, 2808), in 2018, “the initiative “Cybersecurity Ambassador” was launched to build a secure e-culture, empowering Emirati students as ambassadors for cybersecurity to promote a secure electronic lifestyle in the UAE.”
Industry
Since the UAE has been subject to numerous cyberattacks in recent years, it has become evident that it is critical to invest into high-capacity, reliable technologies. Moreover, it is crucial to teach personnel how to observe safety and use technologies correctly. Training on cyber security can help mitigate possible risks and even increase efficiency and productivity. As described by Chandra et al. (2019, 2807), “UAE organizations can enhance their IT security and make attacks difficult merely by addressing some essential vulnerabilities that include obsolete and unsupported software, weak passwords, unpatched systems, and weaknesses in configuration management.” It is also vital to enhance the collaboration between international and national entities. In this way, many innovative technologies can be implemented into private enterprises to improve their safety and security.
To conclude, the UAE is one of the most promising and highly developed Middle East countries. Unfortunately, it is often subject to cyber security threats and attacks. The state implements a number of efficient measures to strengthen its cybercrime defenses.
Since the UAE has been subject to numerous cyberattacks in recent years, it has become evident that it is critical to invest into high-capacity, reliable technologies. Moreover, it is crucial to teach personnel how to observe safety and use technologies correctly. Training on cyber security can help mitigate possible risks and even increase efficiency and productivity. As described by Chandra et al. (2019, 2807), “UAE organizations can enhance their IT security and make attacks difficult merely by addressing some essential vulnerabilities that include obsolete and unsupported software, weak passwords, unpatched systems, and weaknesses in configuration management.” It is also vital to enhance the collaboration between international and national entities. In this way, many innovative technologies can be implemented into private enterprises to improve their safety and security.
To conclude, the UAE is one of the most promising and highly developed Middle East countries. Unfortunately, it is often subject to cyber security threats and attacks. The state implements a number of efficient measures to strengthen its cybercrime defenses.
Conclusion
To outline the findings, one will need the tools such as the national interest scale. The specified analytical tool allows gauging the extent of threat when considering the existing statistical information. Namely, according to the recent facts concerning the rate of cybercrimes identification, the UAE cybersecurity has been improved significantly. However, when examining the statistics on cybercrime prevention, one will admit that the specified issue represents a serious gap in the UAE cybersecurity strategy.
In addition, looking back at the analysis performed above, one should mention that the historical analysis and the introduction of logical fallacies have contributed significantly to the understanding of what affects the rise in cybersecurity risks in the UAE. Namely, the historical assessment has shown the gaps in the development of cybersecurity strategies in the UAE. In turn, the application of the logical fallacies to the case has shown why a significant number of people tend to overlook obvious security concerns when using digital technology.
References
Aboul Enein, Sameh. 2017. Cybersecurity Challenges in the Middle East. Geneva: Geneva Papers.
Butwick, A. J., & Weiniger, C. F. 2019. “Combatting Myths and Misinformation about Obstetric Anesthesia.” International Journal of Obstetric Anesthesia, 40: 1-3.
Chandra, Geetanjali Ramesh, Bhoopesh Kumar Sharma, and Iman Ali Liquat. 2019. “UAE’s Strategy Towards Most Cyber Resilient Nation.” International Journal of Innovative Technology and Exploring Engineering (IJITEE), 8(12): 2803-2809.
Dederer, H. G., and Singer, T. 2019. “Adverse Cyber Operations: Causality, Attribution, Evidence, and Due Diligence.” International Law Studies, 95 (1): 14.
Imranuddin, Mohammed. 2017. “A Study of Cyber Laws in the United Arab Emirates.” PhD diss., Rochester Institute of Technology.
Aboul Enein, Sameh. 2017. Cybersecurity Challenges in the Middle East. Geneva: Geneva Papers.
Butwick, A. J., & Weiniger, C. F. 2019. “Combatting Myths and Misinformation about Obstetric Anesthesia.” International Journal of Obstetric Anesthesia, 40: 1-3.
Chandra, Geetanjali Ramesh, Bhoopesh Kumar Sharma, and Iman Ali Liquat. 2019. “UAE’s Strategy Towards Most Cyber Resilient Nation.” International Journal of Innovative Technology and Exploring Engineering (IJITEE), 8(12): 2803-2809.
Dederer, H. G., and Singer, T. 2019. “Adverse Cyber Operations: Causality, Attribution, Evidence, and Due Diligence.” International Law Studies, 95 (1): 14.
Imranuddin, Mohammed. 2017. “A Study of Cyber Laws in the United Arab Emirates.” PhD diss., Rochester Institute of Technology.