Introduction
Background of Study
Technology has significantly improved organizational performance by making firms more efficient and connected with one another. In this regard, there is improved connectivity of organizational processes and the adoption of faster data processing techniques. However, as companies continue to reap the benefits of these changes, they are increasingly facing the possibility of losing important or valuable data to hackers through cyber theft.
Relative to this fact, Mukhopadhyay et al. (2019) say that the uptake of technology and the prominence of the Internet of Things (IoT), which is a network of objects that communicate with each other, has increasingly exposed companies to the threat of online attacks. Hackers and identity thieves are the most common set of criminals found online and they are ready to exploit weak security systems for criminal gains.
Hacking and identity theft are cyber-security issues that have affected many organizations because before most of them use computing devices to carry out their core tasks. Consequently, they are vulnerable to multiple levels of security threats, which can be launched from anonymous quarters. The record and history of online attacks have been well documented in reports, publications, and academic studies (McAfee, 2018; Dinger and Wade, 2019).
Most of them suggest that such attacks often lead to the loss of information, privacy, and funds, and may cause reputational damages to firms (McAfee, 2018; Dinger and Wade, 2019). Additionally, firms may be concerned that public awareness about such cyber threats may fundamentally undermine confidence in their businesses. Therefore, without the assurance that the devices are secure and that the data contained in them are protected, it is difficult for people to trust organizational systems.
In the context of this study, hacking will be used as a broader term involving different types of malicious activities affecting the integrity of data or information contained in a secure network system. For example, Carpenter et al. (2020) classify unlawful appropriation, embezzlement, espionage, and plagiarism as part of crimes involving hacking. The establishment of sham websites to carry out fraudulent activities and using spoofers to “trick” people into releasing sensitive data through phony email addresses are also categorized as crimes involving hacking (Levitin et al., 2018).
Contrary to popular belief, hacking does not only affect personal computers because large-scale operating systems, such as those owned by government agencies running water treatment and sanitation services or electric power lines could also be hacked (Bialas, 2016). This statement means that not only are individuals at risk of such attacks but corporations are equally affected.
Identity theft occurs in several ways, but the effects on victims are the same as those of hacking. This is because both of them can lead to reputational damage, loss of money, and the release of confidential information – outcomes that could affect financial and non-financial aspects of business performance. Various types of identity theft have been mentioned in the Information Communications Technology (ICT) field and they include financial identity theft, social security theft, medical identity theft, synthetic identity theft, child identity theft, tax identity theft, and criminal identity theft (Mukhopadhyay et al., 2019).
Although these multiple forms of crimes have the highest incidence of occurrence (Carpenter et al., 2020), the financial industry is the most commonly targeted industry for cyber-attacks because of its proclivity to the flow of resources in business (De Souza et al., 2020; McAfee, 2018; Dinger and Wade, 2019). Consequently, there is a need to set up robust security features to protect organizations from cyber-attacks. This paper investigates strategies that companies could use to better mitigate the risk of hacking and identity theft by enhancing the security of their information security networks.
Definition of Terms
- Internet of Things (IoT). This concept refers to a network of objects that communicate with each other through the internet to connect and exchange data. The network is designed to use sensors, software, and other technologies to communicate with various devices found within the network (Kim, Lim, and Lee, 2015).
- Digitization. This concept refers to the transformation of sounds, texts, or pictures into a digital format that can make it possible or managers to process data via their computers. The goal is to transform information into a computer-readable format, which can then be processed for further use.
- Cyber Security. This is a field in the ICT industry, which is focused on the protection of computing devices, such as computers and tablets, from malicious attacks. Common types of cyber security breaches include malware and Trojan attacks.
- Hackers. They are people who exploit network security weaknesses to launch attacks on computer systems. They would ordinarily do so to gain access to data that they would otherwise not have had or are not supposed to have. They use such information to steal funds, forge people’s identities and carry out fraudulent activities in the guise of being someone else. Therefore, when given access to secure network operation systems, hackers can alter or misrepresent the actual meaning of data or steal information, which could then be used to carry out fraudulent activities.
- COVID-19. An airborne respiratory illness caused by a virus. In late 2019, the disease was first reported in Wuhan, China, and it has since spread throughout the world with millions of people infected and thousands more losing their lives. Efforts are currently underway to develop a reliable vaccine to treat it.
- Biometrics. The use of physical characteristics to identify someone before giving them the authorization to access a secure network or a set of organizational systems. This type of security measure is an upgraded version of the old user-password model, which was prone to hacking some people could guess other people’s passwords and breach the system.
Research Questions and Objectives
The aim of this study is to discover how individuals within an organization can handle issues of identity theft to minimize risk to other organizations. Supporting this aim is a set of research objectives, which will guide further discussions in this paper. They are outlined below.
- To find out which information security tools are needed to develop secure network systems.
- To propose measures organizations can take to mitigate the risk of identity theft and hacking in the current business environment.
- To ascertain the extent that trust plays in developing secure networks.
These objectives are supported by the research questions below.
- RQ 1: What information security tools are needed to develop secure network systems?
- RQ 2: Which measures can organizations take to mitigate the risk of identity theft in the current business environment?
- RQ 3: How relevant is the role of trust in developing secure networks?
Justification of the Study
Digitization is a revolution that has occurred in business circles and created vulnerabilities in organizational systems by replacing old systems of operation with new and better ones. The process predisposes people to security threats, which accompany the change. While these threats can be attributed to digitization, it is inherently difficult for companies to stop the automation process because it portends several major benefits to their operations, such as faster communication and the mass storage of data (Mukhopadhyay et al., 2019). Due to the potential for these changes to improve organizational competitiveness, firms have to think of ways to improve their security systems as opposed to slowing the pace of digitization.
Stemming from the nature of the investigations presented in this report, the findings of this study will have practical implications for businesses that have digitized their processes. For example, they can be used to improve the integrity of existing network security systems by providing unique and more sophisticated ways of preventing cyber-crime. Consequently, firms will be in a position to exploit the advantages brought by digitization without worrying about the threat it poses to businesses.
The findings of this study will also contribute towards expanding the body of literature on internet security systems because expert views form a reliable source of invaluable data relating to how companies can bolster their systems to have a more effective response to cyber-threats. Besides, suggestions for improving existing systems will be availed to provide empirical support in identifying areas that need further investigation. Consequently, scholars will be in a better position of identifying key gaps in the literature that need further investigation.
Literature Review
This chapter will highlight what other scholars have written about the research topic. The review will be skewed towards analyzing research materials relating to cyber security and organizational preparedness to manage the threats linked to it. The criterion for selecting articles to be reviewed in this analysis will be based on the year of publication and relevance to the research topic. In line with this selection criterion, research evidence that has not been published within the last ten years will be omitted from the review, while those that were published in 2010 will be included in it.
Theoretical Support
The actor-network theory will be used as the main theoretical foundation of this study. As its name suggests, it traces its roots to the ICT field with a primary focus on the digital data transfer process. The theory explains the relationship between people and innate objects by arguing that the two are involved in a constantly changing environment (Oliveira et al., 2019). Stated differently, the theory presupposes that the relationship between man and innate objects is “fluid” to the extent that it is characterized by a shifting network of interactions.
Therefore, there is an existing interrelationship among all factors involved because all the factors that influence these relationships are subject to the same forces of change. Therefore, the actor-network theory suggests that no external factors are involved in understanding the nature of these relationships and no such interactions exist outside of the forces that commonly act on them.
The actor-network theory has been used to appreciate the complexity of human relationships and their primary environment. From an organizational perspective, it is deemed useful in appreciating the complexity of corporate processes and the role that technology has played in improving coordination among departments or between different interrelated departments or agencies (Grommé, 2018).
Broadly, the actor-network theory can be used to understand how social effects are generalized and how they emanate from interactions with known networks. This statement is relevant in explaining how the actor-network theory is important in understanding how technology is changing social relationships and interactions among different sectors of the population and business agencies.
Based on the key characteristics of the actor-network theory highlighted above and its important role in explaining how technology is changing the business environment, the model has received immense support from known scholars, such as Bruno Latour, John Law, and Michael Callon (Grommé, 2018; McAfee, 2018; Dinger and Wade, 2019; Sun et al., 2018). They are some of the major proponents of this theory and they argue that the universal transmission of data is essential in supporting the growth of economies around the world (Oliveira et al., 2019).
This response helps to assess the threat level posed by hackers because they are also part of the “human element” involved in the broader networking system. Overall, the justification for the use of the actor-network theory as the main theoretical framework in this study is founded in its efficacy in providing a strong theoretical foundation for sampling the views of experts in the ICT field and analyzing their views on network security by providing a conceptual tool for synthesizing their findings.
Issues in Cyber Theft
Privacy violations are common in most organizational security systems because of the sensitivity of the data they contain. For example, hackers can use another person’s credit card to withdraw or transfer funds without consent and avoid detection or apprehension from police. Therefore, their activities can go unnoticed for a long time. However, the impact of their actions is still felt and researchers have tried to quantify losses that organizations accrue because of such attacks. In 2017 alone, it is estimated that organizations around the world lost billions from such crimes (Aydos, Vural, and Tekerek, 2019).
Collectively, they have not only affected organizational performance but also damaged the integrity of their organizational processes by eroding the confidence customers have in such enterprises, particularly with reference to the management of private information (Lutz, Hoffmann, and Ranzini, 2020). Some of these network breaches could have far-reaching implications on an organization’s systems, processes and procedures because one security breach could affect multiple stakeholders at the same time.
Issues in cyber theft can be interrogated using the information security triad, which encompasses aspects of confidentiality, integrity, and availability of data as the main pillars of a strong network security system. Figure 2.1 below explains the nature of interrelationships among the three main tenets of the model.
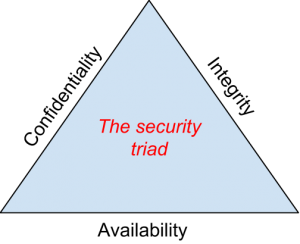
As highlighted in figure 2.1 above, the security triad should contain aspects of confidentiality, integrity, and availability of data. The concept of confidentiality speaks to the need to protect information from unauthorized access, but at the same time, it encourages people to share it only among authorized personnel (He, Devine, and Zhuang, 2018). This statement means that the principle of confidentiality in developing secure networks dissuades people who have no authority to access data from obtaining it or learning anything from it.
For example, researchers note that, in some jurisdictions, governments require education institutions to protect personal information relating to students by making such information confidential and only accessible to a few people. Consequently, most institutions have set up network security systems that prevent unauthorized persons from accessing information relating to students’ grades and identifying markers.
Integrity is the second concept in the internet security triad and it refers to the need to prevent alteration of data within the network security infrastructure. Therefore, the goal of maintaining high levels of information security is enshrined in the need to have safeguarded data to represent what is intended. This statement is similar to human relationships whereby people of high integrity have a higher moral standing because their followers believe in their truthfulness.
Subject to the goals of maintaining the integrity of data and information systems, researchers have pointed out that organizations can suffer security breaches stemming from malicious intentions by a person within or outside the organization to alter information stored in the network security system (Lavorgna, 2019). Thus, researchers underscore the importance of building strong network security systems of high integrity to safeguard data from being corrupted because of these problems.
Information availability is the last tenet of the information triad highlighted in figure 2.1 above. It refers to the ability of anyone to change information in a company’s network security system. Researchers suggest that the timeliness of information access is a significant point to consider in this assessment because some industries value the need to receive prompt information better than others who do not consider promptness as an important consideration in their work (Kim, Lim, and Lee, 2015).
For example, a marketer could easily be willing to get the sales data of the day’s operations the following day, but a stock trader may require such information promptly to make a profitable trade. Therefore, some companies can significantly experience operational disruption when their systems are not working while others may not be affected in the same fashion.
For example, Amazon may experience significant losses if its website is down for a few minutes but a government agency may not be significantly impacted by such an occurrence because it does not provide services outside of the business hours guidelines. This statement suggests that issues in cyber theft may vary across industries or even organizations.
Risk Factors Enabling Cyber Theft
Since cyber-crime is a broad problem affecting different organizations, researchers have taken the time to investigate key factors facilitating the occurrence of cyber-crime. Analysts have pointed out that one of the main risk factors supporting cyber-crime is the ease in the availability of private information through social media accounts, which can be used to hack private systems (Bossong & Wagner, 2017). The major problem associated with this type of system is the difficulty in identifying such breaches when they occur, thereby giving hackers a lot of room to attack because of the general slow response in detecting breaches (Ratten, 2019).
At the same time, failing to secure the physical infrastructure of computers may also encourage criminals to physically destroy or damage computers, thereby leading to the same outcome (Elhabashy et al., 2019). Research evidence further suggests that most of these breaches involve closely linked systems that are usually operated by people or corporate departments, which know each other (Bossong & Wagner, 2017). The sophistication of this system increases the complexity of addressing or mitigating an attack when it happens or detecting its existence in the first place.
Risk Management Strategies
The importance of developing risk management strategies to address the threat of a cyber-attack stems from the need for companies to have clear and measurable goals for managing such risks. Many researchers have proposed a variety of strategies for developing a robust risk management strategy for preventing hacking, but there is consensus that availing adequate resources to all players in the Internet of Things (IoT) is one of the most important steps to take in accomplishing this goal (Halima, Islam, and Mohammad, 2018; Ratten, 2019; Bossong & Wagner, 2017).
The need for undertaking effective organizational planning and developing robust evaluation systems have also been highlighted as additional strategies that corporations could take to improve their risk management strategies (Halima, Islam, and Mohammad, 2018; Ratten, 2019). However, the nature of the recommendations proposed is commensurate to the type of industry involved and the market that which a business operates.
Computer scientists have been at the forefront in championing the adoption of new strategies to address the growing threat of cyber-attacks, but their views are mostly skewed towards emphasizing the need to adopt sufficient data analytical tools to address the problem. Particularly, they have highlighted the reliability of such techniques to detect security breaches and monitoring networks (Patterson et al., 2017). Their recommendations are consistent with the views of Hu et al. (2017), which suggest that when systems are regularly updated, it becomes increasingly difficult for hackers to launch an attack.
Additional evidence suggests that even if they succeed in creating a security breach, such systems should enable authorities to detect it early. Part of the defense strategy adopted by organizations to mitigate against such a crisis is the need to set up an anti-virus and anti-malware software that would allow companies to detect, shutdown, or report security threats and breaches when they occur (Vučković et al., 2018). Most organizations have this type of system and constantly update their employees’ computers with the latest software needed to protect the system from attacks.
Some of the recommendations highlighted above also involve physically protecting the hardware infrastructure of network security systems by hiring guards to evaluate people who seek to gain access to premises that house sensitive data. These measures are intended to make it difficult for hackers to tamper with existing network infrastructure by preventing them from getting physical access to secured premises.
Thus, risk management strategies can be physical or virtual based on the extent that which they affect an organization’s systems. However, most works of literature focus on virtual protection through software and such-like tools, but the evidence also suggests that physical constraints could be as effective.
Summary
In this chapter, the evidence relating to measures adopted and proposed by companies to mitigate against cyber threats seems to focus more on generic aspects of data management without a specific focus on the organization involved or the type of threat under assessment. Few scholars have also explained the human element of internet security systems, which is trust. It is integral in building robust network security systems but it could also be a source of weakness as seen by the actions of hackers who are people that exploit system weaknesses to benefit themselves.
Methodology
In this chapter, the strategies and techniques adopted by the researcher to answer the study questions will be highlighted and explained. In line with this goal, key sections of this chapter highlight the research approach, design, data collection methods, sampling strategy, and ethical implications of the investigation because of the use of human subjects in research.
Research Method and Design
Two main types of research methods are used in academic studies: qualitative and quantitative. The qualitative technique involves the collection of subjective data, while the quantitative technique focuses on the collection and dissemination of standard and measurable data (Strokes, 2017). Therefore, the information collected using the quantitative approach often involves the process of gathering numerical data that can be quantified. Comparatively, the qualitative research method is used to collect data, which cannot be easily quantifiable. In this regard, it offers researchers an opportunity to collect in-depth information from respondents.
This characteristic of the qualitative research approach highlights its suitability for the current study because the researcher intends to give in-depth information about the topic under investigation. Furthermore, the qualitative research methodology aligns with the theoretical framework of the study, which is predicated on the use of the actor-network theory, which highlights the intersection between social interactions and technology as a complex process that cannot be explored using numerical data alone.
Data Collection Procedure
The data collected in this study were retrieved after interviewing 13 respondents who worked as security systems administrators in five internet security companies located in Abu Dhabi. The interviews happened via telephone calls and Zoom. Specifically, seven of the respondents were interviewed via Zoom, while six of them chose to give their views via telephone conversations. The respondents selected the platform to undertake the interviews based on their familiarity with Zoom or mobile phone communication.
Similarly, their availability to perform a face-to-face (Zoom) or oral conversation informed their decision on whether to choose either of the two interview methods. Therefore, the selection of the interviewing platform was purely at the discretion of the respondents. The interviews followed an open format with lead-in questions as follows:
- Have you or your coworkers been victims of identity theft in the past? If so, how did those incidents take place?
- Has your organization been hacked in the past? If so, what outcomes did the security breaches create for it?
- Is identity theft a significant concern for you when designing security systems at your organization?
- What strategies do you use to protect the organization from hacking or identity theft?
The informants were sampled using the snowball method because the researcher intended to get specialized personnel who could not be reached using other sampling methods. The snowball technique involves identifying an initial contact who later introduces a researcher to other people who are willing to participate in a study (Strokes, 2017). The participants were informed in advance about the purpose and method of the study and assured that their privacy and anonymity would be observed. The information gathered using this technique was later analyzed using the thematic and coding method, which identifies unique themes emerging from the interviews.
Reliability and Validity
The reliability and validity of a research process address the integrity of its findings. The two concepts are related but different in the sense that the reliability of a study refers to its consistency, while its validity relates to the accuracy of the measures involved (Mallette and Duke, 2020).
To safeguard the reliability of the information presented in this report, the researcher compared the primary research findings with secondary research to find out if there were significant areas of deviation or convergence of opinions. If there are significant disparities in findings, such information was flagged down and investigated further. To safeguard the reliability of the findings, the results presented in this study were investigated across time and compared with pre-existing data.
Comparatively, to safeguard the validity of the findings, the researcher checked how well the findings of the study compared to well-established theories and more importantly the actor-network theory outlined in chapter 2 of this paper. Similarly, the researcher compared the findings of this paper to other measures of the same concept. Subject to the steps outlined above and that are aimed at safeguarding the reliability and validity of findings, it is important to point out the assumptions made by Strokes (2017), which suggest that a valid measurement is reliable. In other words, a test that produces accurate results is often easily reproduced.
Ethical Considerations
The use of human subjects in research attracts many ethical considerations. Relative to this fact, Ballin (2020) says that confidentiality, anonymity, and prioritizing the interests of the respondents in research should be the guiding factors in ethical evaluations of research investigations. Based on this statement, the above-mentioned factors were integrated in the overall ethical protocol followed in this study.
First, the informants took part in the study voluntarily, meaning that the researcher did not coerce or give them financial incentives to take part in the study. Secondly, all the information provided by the informants was presented anonymously to protect them from receiving backlash for giving honest opinions. All the data obtained from the study was also stored safely using a password and only accessible to the researcher.
Limitations of the Study
It is important to understand the limitations of this study because they highlight characteristics of the design that may affect the interpretation of findings. The first limitation is that the pieces of information presented in this study are indicative, meaning that they do not represent the situation in any one given organization; instead, it appeals to general security network issues affecting systems globally. Therefore, there are constraints on the generalization of data which should be factored in when interpreting the findings of this study.
Research Findings, Analysis, and Discussions
This chapter highlights the findings generated from the study after implementing the research techniques highlighted in chapter three above. To recap, the researcher collected primary data from the respondents using interviews as the main data collection technique. Thirteen respondents gave their views on the research issue and their findings are highlighted below.
Need for Information Security and Trust in Systems
It is important to understand the need for information security and trust in organizational systems to comprehend the context in which companies design their internet security systems and measure the efficacy of such models in preventing identity theft and hacking. Relative to this fact, the respondents were asked to give their views about the real causes of cyber security threats and it was established that a plethora of reasons could be responsible for security breaches.
Consequently, there was the need for the respondents to give specifics on their perceived causes of such threats, and they were encouraged to focus on identity theft. Responding to this line of the probe, one of the respondents said,
The real causes of identity theft vary widely. You would be surprised that simply failing to discard documents containing personal information well is a risk factor. Think about it this way, there are thieves who sift through people’s trash to find documents that contain personal data. It starts from there, but more sophisticated causes of identity theft could be traced to weak security systems and …… I believe that is the focus of your study. You see… hi-tech levels of information security breaches can be linked to hacking corporate databases to get information about clients, particularly, the high-value ones.
Relative to the above statement, five of the respondents suggested that organizational security needs and trust in systems can be categorized into three key segments: confidentiality, integrity, and availability. Confidentiality was explained as the attempt by organizations to prevent unauthorized people from gaining access to information.
Comparatively, the concept of integrity was described as the attempt by organizations to change information in an authorized and organized manner. Lastly, the respondents said that the need for respecting information security and trust in organizational systems could be predicted by the concept of “data availability,” which refers to the unfettered access to information by authorized users. Relative to these findings, one of the respondents said that trust is often a key pillar of a company’s network security systems because only trusted workers are given premium access to data.
Information Security Tools Needed To Develop Secure Networks
It was important to get the views of the respondents regarding information security tools that organizations can use to improve the integrity, availability, and confidentiality of the information they receive. Broadly, the tools mentioned by the respondents can be regarded as part of a wider variety of equipment needed for developing information security policies among various organizations. Therefore, the view of the respondents sampled can be categorized into three groups.
Four respondents proposed the first one and it involved authentication. They acknowledged that most computer systems use people’s physical appearances to authenticate access but it is difficult to continue relying on this measure of authenticity because it is weak. One of the respondents gave an example of a thief who peeps over someone’s shoulder to see the PIN when withdrawing money at an Auto Teller Machine (ATM) machine. Thus, there is a need for a new level of authentication.
In line with the above statement, it was proposed that organizations should use different authentication tools to determine whether the people who want to access the system are indeed who they claim to be. When asked to further clarify on real measures that organizations can follow to actualize this objective, the respondents argued that most systems are based on authenticating people’s identities depending on what the system knows about them, have about them or know something that is uniquely associated with their identity. From these key bases of user authentication, most organizations require employees to input a name and password to gain access to their systems.
This view is consistent with those of other scholars who believe that the user and password model is the most commonly used method of authentication (Zhao et al., 2019; He, Huang and Yang, 2020; Lee, Jeon, and Lee, 2019). In this type of security design, authentication is completed based on the information that only the user knows, such as their identification names and password.
The user-password authentication process has been used in many organizational contexts of data management. However, as pointed out by one of the respondents, it is easy for hackers to compromise this type of system, thereby creating the need for a stronger method of control. Relative to this assertion, one of the respondents said,
I am personally not a big fan of the user-ID model, because identifying people based on what only they know has been problematic in the past…. in my experience. This is because when that password is stolen or gets lots, it becomes an automatic problem for the person because it means someone can use the same tools to gain unauthorized access into systems. For example, a hacker can use a lost physical credit card to launch an attack. Therefore, I would propose adopting a network security policy, which stems from identifying markers that are specific to one individual.
Biometric forms of identification fall within this group of network security systems because they use identifiable markers that are only uniquely associated with one user. For example, most of them use fingerprint technology, which is based on a unique identifiable marker (Choi, Lee, and Won, 2016). They also use eye scans and other complex methods of authentication to further protect their systems from unauthorized entry (Choi, Lee, and Won, 2016). These types of tools are aimed at improving authentication requirements to discourage hackers from launching an attack.
The second tool proposed by the respondents was access controls, which is concerned with the need for users to only access resources or data that is appropriate for their security clearance level. For example, in most security systems adopted by organizations today, the concept of access control is to categorize employees into different groups with the highest clearance given to people who can modify, delete or alter information.
One of the respondents gave more intricate details about this information tool by saying that it occurs in two forms: the access control list and the role-based access control format. The respondents said, in many organizations, two groups of users are often created based on their ability to take control of specific actions that can be initiated within the system. Mostly, this type of system is found in access control lists because each category of the user has specific actions they can take, such as reading, writing, or deleting data. Employees who do not have this type of access are not even aware that such information resources or data exist.
One of the respondents cautioned against the adoption of such a system because he noted that most organizations manage each information resource separately. A rigid model makes it difficult to remove a user who is plugged within a larger set of systems and controls information resources remotely. The same respondent also said that even though it was easy for most companies to manage and maintain ACL systems, it becomes difficult to achieve a high level of efficiency when the number of users increase. Relative to this statement, he said,
This problem creates a new level of access control, which is predicated on role assessment as the main basis for establishing information access security levels. In other words, the system is designed to allocate users with specific roles and then the same roles are assigned different levels of security clearance.
Seven of the respondents hailed this strategy and said it is justified for use in most organizations because it makes it possible for authorities to manage users and roles separately. It was also noted that doing so simplified administrative responsibilities and made it further possible to enhance the associated level of security.
Encryption is the last information technology tool proposed by the respondents. It is primarily focused on the transmission of data across network security systems. Particularly, it is designed to curb security threats that occur when hackers intercept information being transferred from one point of the information network system to another. This information technology tool focuses on the need to encrypt data, such that unauthorized persons cannot gain access to it. The process is often embedded in a computer program, which encodes the text that needs to be transmitted across communication platforms.
To further explain how this system works, one of the respondents said that the encryption process is automatically linked to the decryption phase, which started when a recipient receives encoded data. Therefore, for them to be able to read it, they need to decode it. However, for both processes to work effectively, it is important for concerned parties to agree on the encryption format to use, such that both of them have access to the information transferred. Stated differently, both parties should have an encryption key to allow each one of them to code or decode the messages.
The secondary research data gathered in this review also mentioned the need to have a common metric for coding and decoding data. However, they should stem from the process of symmetric key encryption, which has been deemed problematic by some researchers who believe that the presence of two sets of keys in equally different places makes it difficult for coordinated communication to happen (Chen, Wei, and Ma, 2015; Choi and Kwak, 2016).
Public encryption has also been mentioned in the extant literature as an alternative to the symmetric key encryption format (Zhao et al., 2015). It involves the design of two sets of keys: public and private to code and decodes information. For encryption to occur, the public key has to be accessed, while the encoded information will be accessed privately. Therefore, anyone who wishes to send a message using the public key can do so but the information generated has to be encrypted and accessed using a privately generated key. Therefore, public and private keys are needed to secure messages.
How to Mitigate the Risk of Identity Theft
When asked to state how the risk of identity theft can be minimized, the respondents alluded to the need to adopt a holistic approach to data assessment when building secure networks. When asked for specifics, one of the respondents highlighted the need to track people’s financial records and social activities.
This recommendation is consistent with the views of Laybats and Tredinnick (2016), which suggests that continuously checking the accuracy of personal data is one of the most effective ways of promptly dealing with any discrepancy that may arise from a security breach. Additionally, another respondent highlighted the need to use one’s social security number to keep track of changes to financial statements and other sensitive data.
Three of the respondents said that companies need to seek the help of third-party players in mitigating the effects of cyber theft. Relative to this assertion, one of the respondents said identity protection services could be used to mitigate the effects of cyber theft on companies. He added,
Typically, these third-party players equip their clients with information that would help them to safeguard their personal data.
Another respondent added that
These third parties can also help to monitor public and private records to alert their clients of any incidence or information breach. This strategy has been observed in companies that monitor credit reports because they give their clients status reports on the type of data to hold as well as any transaction changes they need to know about. I must also add that they are also useful in helping clients to resolve issues that may occur due to identity theft.
Additional evidence obtained from a review of the existing literature also supports the above-mentioned proposals with much of the suggestions indicating that these third parties could be governmental agencies and non-profit organizations that help people to get help when they have been attacked by a hacker (Chen, Wei, and Ma, 2015; Choi and Kwak, 2016; Laybats and Tredinnick, 2016). This type of help is often offered on websites and other online platforms of engagement where clients can get the tools and resources to better manage their data.
In response to identifying proposals to mitigate the risk of identity theft, one of the informants also said that adopting a multifactor authentication process would enable organizations to improve their network security levels. This strategy works by adopting two or more types of authentication processes to improve the level of risk preparedness because it would make it more difficult for a person to breach multiple layers of security in one attack.
To further support the adoption of this strategy, two of the respondents gave examples of the RSA SecurID Token, which generates new access codes periodically and within intervals of minutes or seconds. Organizations that have adopted this system require users to know their access PINs and still key in a security code that is generated by a login system. The respondents further remarked that this system offers a new layer of security, which works by generating the system code described above every few seconds. Therefore, a failed login attempt using a set of codes cannot be replicated in a new attempt because a new code will be generated in every instance a hacker attempts to gain entry into the system.
Four of the interviewees further supported the adoption of this system by giving the example of online banking, which requires users to not only input their passwords but also a mobile-generated code that is linked with the telephone numbers that they used during registration. Therefore, the basic assumption underlying the integrity and quality of the system is that even if a hacker were able to guess a bank user’s password, it would be difficult for them to be in possession of the user’s mobile phone at the time of log-in.
Backing up data was mentioned by all the respondents as one of the techniques that organizations should adopt to prevent themselves from cyber-attacks. This strategy was mentioned as the first line of defense that organizations have in defending themselves from attacks. Relative to this assertion, one of the interviewees said.
I cannot stress enough that backing up your files is an essential requirement in the administration of any network security system. You also need to know that no matter the extent or nature of proposals you hear about protecting network securities from cyber-attacks, they cannot be 100% certain that they will work. Therefore, we need to have a secure backup process to restore the system in case of an attack. This action will protect organizations from the risk of having to “start from scratch” when they lose valuable data.
The secondary literature gathered in this study suggested that a robust backup plan should have four main components: a good understating of an organization’s resources, regular backup of data, offsite data storage, and the test of data restoration (Chen, Wei, and Ma, 2015; Choi and Kwak, 2016).
The last measure is proposed as a continuous process whereby organizations are required to occasionally perform drill backup data to make sure that they would actually work in an emergency setting. One of the respondents said that it was important for organizations to undertake their own internal evaluation systems to determine the effects of downtime on their businesses. In most cases, many organizations choose to have an off-site data restoration plan that protects a firm from experiencing the effects of data loss when a security attack happens on-site
Conclusion and Recommendations
Conclusion
The aim of this study has been to determine how individuals within an organization can handle identity theft and hacking issues to protect their network security systems. Three objectives guided the investigation and they were focused on identifying information security tools needed to develop secure systems, highlighting measures that organizations and take to mitigate the risk of identity theft, and understanding the relevance and role of trust in developing secure networks. Stemming from the need to meet these objectives, data was obtained from interviewees and secondary research data.
Based on the evidence gathered in this study, internet connectivity can pose significant security risks to organizations. Therefore, when a security breach happens, it may be difficult to detect such a risk early because billions of objects may be connected at the same time. The sophistication of hackers and the complexity of their strategies when planning and executing cyber attacks has further made it difficult for firms to effectively address the risk of internet security threats.
The evidence gathered in this report has additionally shown that the current internet security features adopted by most organizations is insufficient in protecting the physical infrastructure and private data associated with most of these enterprises. Therefore, companies should take the threat of cyber security seriously to encourage the development of a more elaborate framework for handing such risks within and outside the organizations.
Three tools were noted to be of critical importance to organizations that intend to develop robust and secure network systems: access control, authentication and encryption. Although these tools are purposefully different from one another and serve several functions, they help to identify different levels of security requirements needed to be assigned to different groups of employees in an organization.
In other words, the above-mentioned tools promote a layered system of information flow and security access system based on roles and tasks assigned to each employee. More of these discussions have been highlighted in this study as design features that organizations can exploit to promote the robustness of their systems. The same tools have been proposed as instruments for adapting organizational resources to different types of security needs.
They have also been mentioned as instruments for developing strategies for mitigating the risk of cyber threats, as seen through the development of backup systems and firewalls, which are commonly adopted tools of security engagement. Overall, the evidence gathered in this document also shows that the strategies proposed to address different types of security systems should be implemented promptly because the nature of security threats keeps changing and it is important for solutions to also change in the same manner
Recommendations
As highlighted in chapter three of this report, one of the limitations of this study was its indicative nature. This means that the findings cannot appeal to all organizations or industries because of their unique characteristics and needs. Thus, it is important to perform a contextualized review of information systems analysis in one industry or sector to have a better understanding of how some of the proposals highlighted in this document can be addressed.
The importance of doing context-specific research is premised on the understanding that each industry has its unique security needs and threats that can be effectively addressed in an investigation that focuses on such factors. Therefore, future research should be directed towards adopting a context-specific understanding of the research phenomenon. These recommendations should be adopted in the study because the objective of this research process was not only to discover new knowledge but also to propose practical recommendations that can be used in a sectoral context or organizational setting.
Social, economic, and political changes affecting the business environment have also forced managers to think of new ways of accomplishing organizational tasks by exploiting the opportunities brought by digitization. For example, the recent COVID-19 pandemic has seen firms encourage their employees to work from home and the preceding rapid digitization of organizational processes has enabled this to happen.
However, these changes and developments have only led to the creation of more problems for most companies because of the increased threat of cybercrime and the cost of preventing them. Therefore, to manage these developments, it is pertinent to have a broad strategy for addressing this threat since it is difficult for one company to effectively tackle this problem alone. Particularly, there is a need for all stakeholders to collaborate effectively and address the problem.
There is also a need to undertake a quantitative assessment of the research phenomenon because the current study is qualitative. This approach to data collection will ensure the collection of robust and holistic data relating to internet security systems because the qualitative information obtained is only representative of the views of a few experts in the field.
Additionally, the focus of this investigation has been on identity theft as one of the main security threats affecting organizations today. Therefore, it is important to investigate other aspects of security breaches such as the physical destruction of computer systems.
Reference List
Aydos, M., Vural, Y. and Tekerek, A. (2019) ‘Assessing risks and threats with layered approach to internet of things security’, Measurement and Control, 52(6), pp. 338-353.
Ballin, E. H. (2020) Advanced introduction to legal research methods. London: Edward Elgar Publishing.
Bialas, A. (2016) ‘Risk management in critical infrastructure-foundation for its sustainable work’, Sustainability, 8(3), p. 240.
Bossong, R. and Wagner, B. (2017) ‘A typology of cybersecurity and public-private partnerships in the context of the EU’, Crime, Law and Social Change, 67(3), 265-288.
Bourgeois, D. and Bourgeois, T. (2020) Information systems security. Web.
Carpenter, S. et al. (2017) ‘Expert sources in warnings may reduce the extent of identity disclosure in cyber contexts’, International Journal of Human-Computer Interaction, 33(3), 215-228.
Chen, L., Wei, F. and Ma, C. (2015) ‘A secure user authentication scheme against smart-card loss attack for wireless sensor networks using symmetric key techniques’, International Journal of Distributed Sensor Networks, 7(2), pp. 1-10.
Choi, S. and Kwak, J. (2016) ‘Enhanced SDIoT security framework models’, International Journal of Distributed Sensor Networks, 5(1), pp. 1-10.
Choi, Y., Lee, Y. and Won, D. (2016) ‘Security improvement on biometric based authentication scheme for wireless sensor networks using fuzzy extraction’, International Journal of Distributed Sensor Networks, 11(3), pp. 345-451.
De Souza, M. A. et al. (2020) ‘Detection and identification of energy theft in advanced metering infrastructures’, Electric Power Systems Research, 9(3), p. 182.
Dinger, M. and Wade, J. T. (2019) ‘The strategic problem of information security and data breaches’, The Coastal Business Journal, 17(1), 1-25.
Elhabashy, A. E. et al. (2019) ‘A cyber-physical attack taxonomy for production systems: a quality control perspective’, Journal of Intelligent Manufacturing, 30(6), 2489-2504.
Grommé, F. (2018) ‘Actor-network theory and crime studies: explorations in science and technology’, Technology and Culture, 59(1), pp. 201-202.
Halima, I. K., Islam, S. and Mohammad, A. R. (2018) ‘An integrated cyber security risk management approach for a cyber-physical system’, Applied Sciences, 8(6), pp. 1-10.
He, M., Devine, L. and Zhuang, J. (2018) ‘Perspectives on cybersecurity information sharing among multiple stakeholders using a decision-theoretic approach’, Risk Analysis, 38(2), pp. 215-225.
He, S., Huang, J. and Yang, P. (2020) ‘Build with intrinsic security: trusted autonomy security system’, International Journal of Distributed Sensor Networks, 9(1), pp. 1-10.
Hu, Z. et al. (2017) ‘Method for cyberincidents network-centric monitoring in critical information infrastructure’, International Journal of Computer Network and Information Security, 9(6), p. 30.
Kim, H., Lim, J. and Lee, K. (2015) ‘A study of K-ISMS fault analysis for constructing secure internet of things service’, International Journal of Distributed Sensor Networks, 4(2), pp. 1-10.
Lavorgna, A. (2019) ‘Cyber-organised crime: a case of moral panic?’, Trends in Organized Crime, 22(4), pp. 357-374.
Laybats, C. and Tredinnick, L. (2016) ‘Information security’, Business Information Review, 33(2), pp. 76-80.
Lee, S., Jeon, S. and Lee, B. (2019) ‘Security controls for employees’ satisfaction: perspective of controls framework’, SAGE Open, 5(2), pp. 112-139.
Levitin, G., Xing, L. and Huang, H. Z. (2018) ‘Security of separated data in cloud systems with competing attack detection and data theft processes’, Risk Analysis, 39(4), pp. 846-858.
Louchez, A. and Rosner, G. L. (2016) Internet of things security – the case for systemic resilience. Web.
Lutz, C., Hoffmann, C. P. and Ranzini, G. (2020) ‘Data capitalism and the user: an exploration of privacy cynicism in Germany’, New Media and Society, 22(7), pp. 1168-1187.
Mallette, M. H. and Duke, N. K. (2020) Literacy research methodologies. 3rd edn. New York: Guilford Publications.
McAfee. (2018) The economic impact of cybercrime: no slowing down. Web.
Mukhopadhyay, A. et al. (2019) ‘Cyber risk assessment and mitigation (cram) framework using logit and probit models for cyber insurance’, Information Systems Frontiers, 21(5), pp. 997-1018.
Oliveira, M. et al. (2019) ‘Actor-network theory: opening the black box of the reasons for the involvement of researchers in the technology transfer process’, Journal of Innovation Management, 6(4), pp. 49-72.
Patterson, N., Hobbs, M. and Zhu, T. (2017) ‘A cyber-threat analytic model for autonomous detection of virtual property theft’, Information and Computer Security, 25(4), pp. 358-381.
Ratten, V. (2019) ‘The effect of cybercrime on open innovation policies in technology firms’, Information Technology and People, 32(5), pp. 1301-1317.
Strokes, P. (2017) Research methods. London: Macmillan International Higher Education.
Sun, Q. et al. (2018) ‘Improving the security and quality of real-time multimedia transmission in cyber-physical-social systems’, International Journal of Distributed Sensor Networks, 6(1), pp. 10-19.
Vučković, Z. et al. (2018) ‘Analyzing of e-commerce user behavior to detect identity theft’, Statistical Mechanics and Its Applications, 1(5) pp. 331-335.
Zhao, H. et al. (2015) ‘Securing body sensor networks with biometric methods: a new key negotiation method and a key sampling method for linear interpolation encryption’, International Journal of Distributed Sensor Networks, 7(1) pp. 998-1123.
Zhao, Y. et al. (2019) ‘Security-enhanced three-factor remote user authentication scheme based on Chebyshev chaotic maps’, International Journal of Distributed Sensor Networks, 4(2), pp. 1-11.