Attack Analysis
The possibilities of the Internet today can be considered almost limitless because, with the help of the global network, a large number of operations are performed daily, and people around the world enjoy these benefits. However, the Internet is not always used for peaceful purposes. With the development of technologies and the improvement of programming systems, there have become more frequent cases of so-called hacker attacks, which are a real problem for many large companies.
The scenario of such attacks is often similar: cybercriminals hack into secret databases and other private information that is usually not publicly displayed and place stolen data on the network. Over time, it has become more difficult to fight such criminals as new ways of circumventing defense systems and antivirus databases were invented.
Thus, one of the most famous cases in the world, which related to the hacking of important information, was the attack on the database of the world-famous online store eBay. According to some sources, it was included in the list of the most severe attacks in the history of the Internet. Therefore, it is necessary to find out what the perpetrators were guided by, what result this attack entailed, and what measures could have been taken to prevent the leakage of important data.
Summary of the Attack
The case under investigation occurred in the summer of 2014 when one of the most popular trading platforms on the Internet was attacked by virtual intruders (Meyer, 2017). According to Meyer (2017), “the company had 145 million user accounts compromised” (p. 11). Such a large number of affected people could not go unnoticed, and the eBay case received a significant public response.
Despite the fact that the attack did not touch on important financial information, for example, essential data about payment cards of clients, personal data of many users was stolen. In this regard, users of the online store had to urgently change their private information including passwords and logins, and delete old accounts in order to avoid hacking. The fact is that clients’ personal pages do not contain vital payment information. However, such personal data as volume and history of purchases, as well as some other information, were contained in their accounts. Therefore, the attack was primarily related to the theft of not financial but private user data.
The damage to the reputation of eBay was significant. The company representatives tried to do everything possible to compensate for the damage done to their customers. However, the authority of the online store as the largest site for the sale of goods was significantly spoiled, and its management had to experience much criticism of its address, which came from angry shop users. Because of the fact that this hacking attack has become one of the most public in the history of the Internet, it is still an example for many other large online trading corporations. Therefore, the events of 2014 were discussed very actively, and today, eBay is putting much more effort than before to protect its data.
Analysis of Hackers’ Activities
The activities of people who hacked user information and abducted passwords and access codes were organized professionally enough. It is worth noting that the protection of eBay was not absolutely useless, and for some time, the firewall was protected. Nevertheless, cybercriminals managed to circumvent this protection and successfully commit their crime. The following Figure 1 will show what exactly happened to the Internet store, and what threat its customers had to experience:
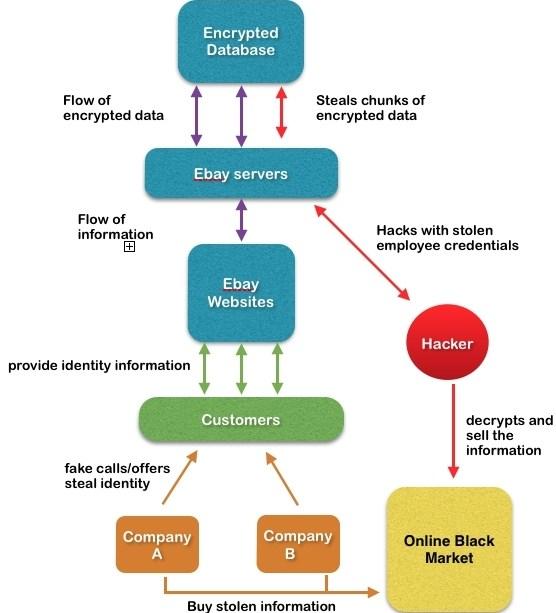
According to Figure 1, it can be concluded that customers could have been a rather serious risk if the target of the hackers had been to attack for the purpose of stealing and using certain information. It is hard to suppose what the motives of cybercriminals were and what they wanted to achieve. Perhaps, their actions were aimed at undermining the authority of the company.
Thus, according to El-Kenawy, El-Desoky, and Sarhan (2014), eBay has always been one of the world’s largest online platforms, and the activities of competitors have always been aimed at reducing the popularity of this store. Also, a possible version of the reason for the attack may be an ordinary database hacking for entertainment purposes, thereby showing the creators of the security system that their product is unsafe and can easily be damaged. Regardless of the intent of the criminals, they managed to achieve what they aspired to: the eBay system was hacked, and the information of millions of user accounts was made available to strangers.
Hackers did not use the scheme of well-known DDoS attacks when many requests are made to one site with the purpose of its collapse. They used a more sophisticated method. Having hacked an information field of the online store, they gained access to essential information. Due to the fact that critical financial data were not stored in an attacked base, money was not stolen by the attackers. However, the reputational damage to eBay was enormous. According to Aggarwal, Arora, and Ghai (2014), millions of buyers on the Internet lost their password-protected data. This hacking attack was one of the most famous in the history of the Internet and has become a reason for discussion for a long time.
Perhaps, if the criminals had managed to steal the company’s money and buyers’ personal funds, eBay would have entirely ceased to exist and have received many lawsuits from dissatisfied customers. However, the theft was only informational, which, nevertheless, cannot be regarded as something positive. If specific measures had been taken timely, it would not have been so easy to hack the system and steal valuable information.
Approaches for Mitigating the Attack Vectors
One of the main reasons why hackers did not succeed in stealing valuable financial and other private data was that the information was stored in an encrypted form. Thus, in order to prevent unauthorized access to information, listening, and intercepting traffic, encryption is used. It is a method of converting data to maintain confidentiality.
The encryption process involves negotiating a particular key among users and using it on a particular website or another platform. The technical peculiarity of this method is that the attacker will not be able to access data without having a unique key that was used by users. Encryption can be symmetrical and asymmetric. In the course of symmetric encryption, one key is used that was previously known to two users. In asymmetric encryption, two keys are used: public and private. A public key is used to encrypt a message, and a secret key is necessary for decryption. Most online platforms, including eBay, use an asymmetric version of encryption. The simplest and most well-known option for such protection is as follows:
According to Figure 2, it is possible to note that a similar type of encryption is used on many online platforms. Also, it is possible to define a few more methods of how eBay IT employees could prevent the attack of 2014. In order to protect the system from a possible recurrence of such attacks, it is essential to adhere to appropriate preventive rules.
Restricted Access to the System
The ways to combat unauthorized access can be quite simple if they are properly implemented. The fundamental thing here is the reduction or complete elimination of hackers’ ability to gain access to the system through an unauthorized protocol. As an example, it is possible to consider avoiding hacker access to the server, which provides Web services to external users. Without access to this port, a hacker will not be able to attack it. As for the firewall, its main task is to prevent the simplest attempts of unauthorized access.
If the specialists of eBay’s IT department had been able to provide complete protection of its content in time to prevent unwanted access to the system, the 2014 case would not have happened. One person or group of people successfully took advantage of the fact that the online store did not have a sufficiently secure network, and it was not difficult to steal unprotected data. After the incident, it was decided to strengthen the protection of the network and check its protective protocols in order to exclude possible repetition of the attack. Nevertheless, the damage suffered by the corporation can hardly be forgotten.
Centralized Key Management
The method that in many ways resembles standard encryption is centralized key management. Several important points are taken into account here, and the order of work should be in accordance with a certain algorithm and observance of a special chain. This order is displayed in the following scheme:
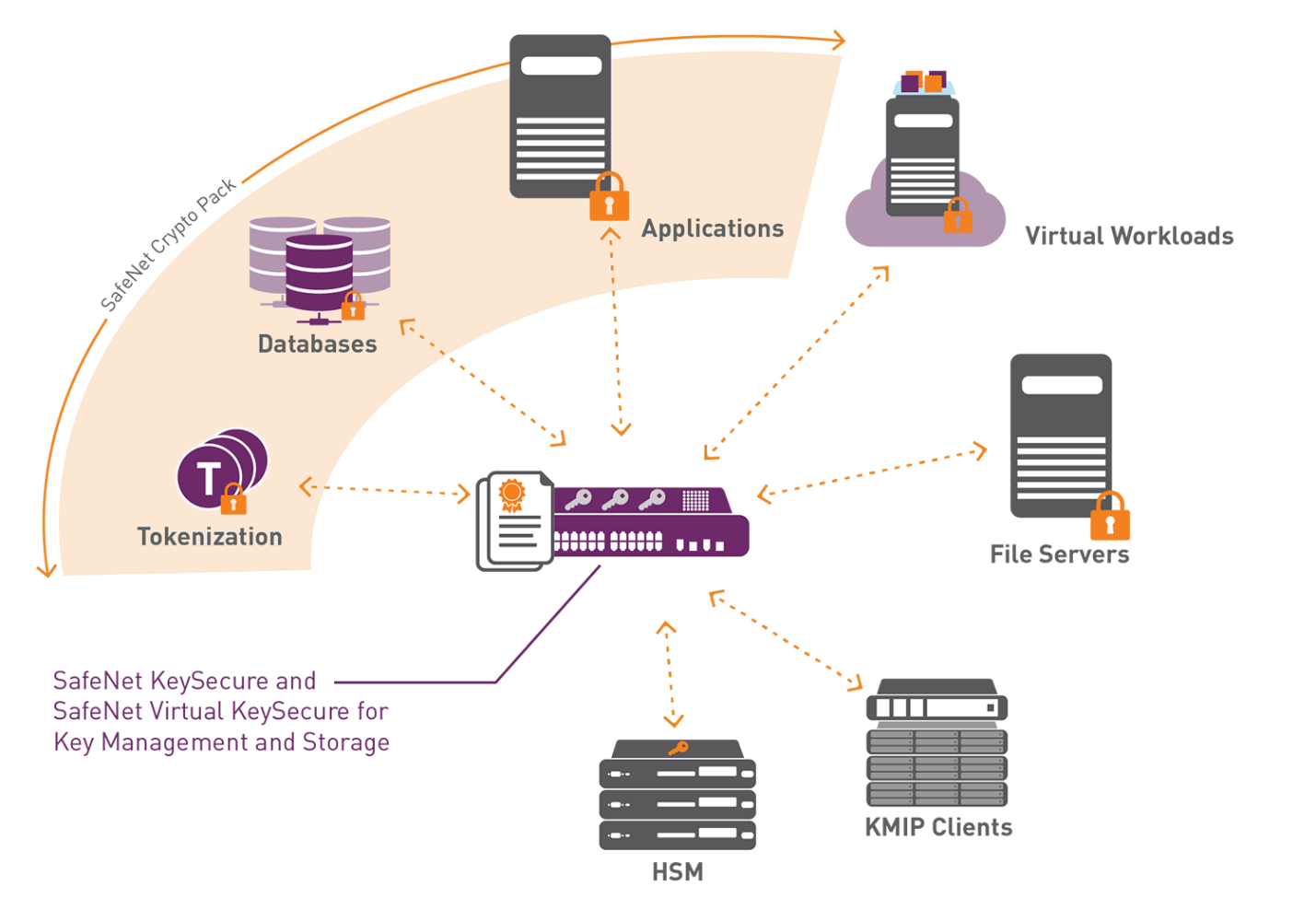
According to Figure 3, it is possible to see that all the objects in the database chain are managed by one key element. It is significant for the management of such a scheme to conform to all the standards of modern information protection. The more reliable and professional the central control apparatus will be organized, the more chances that this or that system will be entirely protected from hacker attacks. Accordingly, an insufficiently qualitative scheme can lead to the threat of data theft.
Design to Identify the Attack
There are many ways to take advantage of the vulnerability of a particular network. Hackers can use one or several exploits at the same time, incorrect settings for software components, or even a backdoor program installed in the operating system during the previous attack. Because of these measures, detecting a hacker attack is not the easiest task, especially for an inexperienced user. The data center infrastructure that was used in the eBay of 2014 was characterized by rather standard principles; all the software, server hardware, and monitoring systems were quite ordinary.
The control of security levels was carried out in accordance with a traditional scheme, and no special procedures were used. Therefore, it is necessary to formulate some outline and tips that could have helped an operator to identify whether the computers of eBay’s network could have been protected from the attack. Surely, it is impossible to claim that all these methods will give a full guarantee that a hacker attack would have been detected. However, if a specific system is about to be damaged, some of the following indicators can probably be seen.
High Outgoing Network Traffic
When using a common type of connection, it is possible to notice an unusually large amount of outgoing network traffic. In particular, it can be observed when computers from a certain group are connected to the Internet, but no activities are done. In this case, the risk that the network may have been hacked is high enough. Such a computer can be used for hidden spamming or the propagation of viruses. Those who participated in hacking the eBay company were not likely to take advantage of this type of vulnerability. Nevertheless, it is significant to remember about such a danger and timely prevent any potential breaking.
Increased Hard Drive Activity
If increased hard drive activity or suspicious files in root directories are noticed, it is a good reason to pay close attention to a protection system. Many hackers scan the information stored on the network in search of valuable documents or files that contain logins and passwords to bank payment centers or electronic payment systems like PayPal (How Hackers Hack PayPal Account in 2017 – Hack PayPal, 2017). Some viruses similarly search for disk files with email addresses, which are then used to send infected messages. Having noticed a significant activity of hard disks even when the computer is out of work and the emergence of suspicious names in public folders, it is possible to assume that the network is hacked, and the threat of theft is high.
A Number of Packets Stopped by a Personal Firewall
After determining the target (for example, the range of IP addresses of a company or home network), hackers usually start automatic scanners trying to use a set of various exploits to penetrate the system. When launching an installed firewall that is an indispensable tool in protecting against hacker attacks and noticing an unusually high number of stopped packets from the same address, it is possible to conclude that the network has been attacked.
Thus, if such a firewall reports the shutdown of these packages, the network is most likely safe. However, much depends on which running services are open for access from the Internet. For example, a firewall might not be able to cope with an attack aimed at an FTP service. In this case, the solution to the problem is the complete temporary blocking of dangerous packets until the connection attempts are terminated. Most corporate firewalls have a similar function and are used to protect companies’ networks from various threats including data thefts.
Thus, the plan to protect the personal data of eBay’s users could have been developed in advance, and if all the appropriate measures were taken timely, unpleasant consequences probably could have been avoided. The system was not sufficiently protected, which caused considerable damage. After the case of 2014, the company’s management has undoubtedly revised the approach to protecting both valuable financial information and user data. Nevertheless, if the entire algorithm is not carefully considered and some sectors of the network remain vulnerable, it is impossible to speak of full protection. Only comprehensive control will help to achieve maximum security and prevent a repetition of the attack. Therefore, there is a need to discuss additional concepts related to the attack.
Comparison of the eBay Attack with Another Case
Certainly, the attack of 2014 on the eBay database was not the only major online crime. In the same year, network users learned about such a term as the Heartbleed bug. It was a virus similar in its purpose to eBay, but it affected not only local databases but also the security systems of other well-known platforms: Google, Facebook, etc. (Gujrathi, 2014). However, these two attacks had similarities in common since hackers who developed the Heartbleed bug could access the contents of the server’s memory, which at that time could contain private user data (Gujrathi, 2014). Therefore, the principle of their operation was similar. The bug was so famous that it even had its own logo. The activities that it performed when attacking various databases can be displayed in the following scheme:
The Heartbleed bug is a serious vulnerability that allows hackers to access the contents of the server memory, which can contain private data from users of various web services (Gujrathi, 2014). In addition, cybercriminals can also obtain digital keys used, for example, to encrypt correspondence and internal documents in a variety of companies.
This vulnerability allows an attacker to gain access to sixty-four kilobytes of server RAM and perform attacks many times until the data is completely lost. It means that not only logins and passwords are subject to leakage but also the cookie data that web servers and sites use to track user actions and simplify authorization. According to Gujrathi (2014), periodic attacks can give access to more serious information, such as private encryption keys used by the site to block traffic. When using this key, an attacker can replace the original site and steal a variety of types of personal data, such as credit card numbers or private correspondence.
Accordingly, this vulnerability also carries a certain danger for personal data, and its mechanism of action has something in common with the case of eBay in 2014. In particular, the Heartbleed bug is dangerous when it comes to passwords; in 2014, many customers of the online shop also were theft. Therefore, in both cases, the problem is associated with the need to ensure full protection of access to passwords and other important information that can be used by cybercriminals.
Measures to Prevent Attack Repetition
Despite the fact that after the events of 2014, the management of eBay took appropriate measures to protect the data of its customers and ensure more efficient security, there is always a risk of attack. Technologies never stand still, and new viruses and other malicious software appear regularly. Hackers can create some other threats that will be able to circumvent existing firewalls and harm content.
In order for this case not to happen again, IT professionals of the eBay company should pay specific attention to the protection of customers’ personal data and, in particular, to password encryption. There is a high probability that attackers will want to repeat the attack since this online store is one of the largest and most famous on the Internet, and access to information about its customers can bring cybercriminals considerable profit.
Thus, system administrators should regularly monitor the amount of outgoing traffic and in case of any violations or unusual situations, it is necessary to immediately take measures and block any suspicious activity. Also, it is essential not to allow third parties to the database where all important information is stored. It can happen that even a person working inside the organization can turn out to be a criminal and steal passwords and other information about clients. In order to avoid it, it is necessary to allow only those professionals who are directly involved in the IT department and do everything possible to ensure that unauthorized persons do not have unrestricted access to network information.
The management of eBay probably has taken all necessary measures since the attack of 2014. Nevertheless, it is always significant to ensure control as the hacker threat can be in any form: stealing passwords, blocking information, breaking the site, etc. Therefore, the higher the security of the system is, the less likely that cybercriminals will be able to crack it.
Conclusion
Thus, according to the information studied, it is possible to claim that eBay has undergone one of the most famous hacker attacks in the history of the Internet. The reason for the leakage of customer personal data is not enough high level of system protection. The threat could have been prevented if appropriate measures had been taken timely. Cybercriminals acted on a rather famous pattern. Despite the fact that customers did not lose their money, the reputation of the online store was broken. In order to avoid such an attack in the future, it is essential to provide enhanced database protection and monitor any suspicious activity.
References
Aggarwal, P., Arora, P., & Ghai, R. (2014). Review on cybercrime and security. International Journal of Research in Engineering and Applied Sciences, 2(1), 48-51.
The case of eBay data theft and potential threat to customers [Image]. (2014). Web.
The damage that the Heartbleed bug caused [Image]. (2014). Web.
Gujrathi, S. (2014). Heartbleed bug: AnOpenSSL heartbeat vulnerability. International Journal of Computer Science and Engineering, 2(5), 61-64.
El-Kenawy, E. S. M. T., El-Desoky, A. I., & Sarhan, A. M. (2014). Bidder strategy system for online auction trust measurement. International Journal of Computer Science Issues (IJCSI), 11(5), 76-82.
How hackers hack PayPal account in 2017 – Hack PayPal. (2017). Web.
The login page of eBay [Image]. (2017). Web.
Meyer, C. (2017). Submitted to the Department of Technology Systems. Web.
The system of centralized cryptographic key management [Image]. Web.