In this modern technology era, cryptographic keys and digital certificates are mostly applied as a means of developing trust between two or more organizations that share data over a network. The paper focuses on the process of issuing and managing digital certificates, discussing the weaknesses and vulnerabilities of different methods and the issues with revoking certificates, and possible remedies. The number of businesses and people that utilize online services is growing daily necessitating the need for digital certificates.
The Process of Issuing and Managing Digital Certificate
Digital Certificate
Digital certificates have a public key to be licensed, information recognizing the entity that owns this public key, metadata associated with the digital certificate, and the public key digital signature developed by a certifier. Public Key Infrastructure (PKI) leverages all three types of encryption to offer and manage digital certificates, which may be client-based or server-based. The major roles of PKI are distribution, validation, and revocation of a digital certificate (Danquah & Kwabena-Adade, 2020). If server and client certificates are employed together, they offer mutual validation and encryption.
Digital Certificate Issuing
Certification Authorities (CAs) issue digital certificates and Organizational Registration Authorities (ORAs) authenticate the certificate holder’s identity before the certificate is issued to them. An institution can function as a CA, ORA, or both of them in the process of issuing the certificate. CAs can be public like Thawte or VeriSign or private and be managed internally. Any person off the street cannot just request and get a certification, for example, at www.ebay.com; they should demonstrate that they have the power to do it. CA performs the authentication and may involve industry research records, emails sent to the domain contacts, and similar approaches (Winnard et al., 2018). Further, they are applied in other contexts such as offline and online to offer cryptographic privacy and security.
Certificate Trust Chain
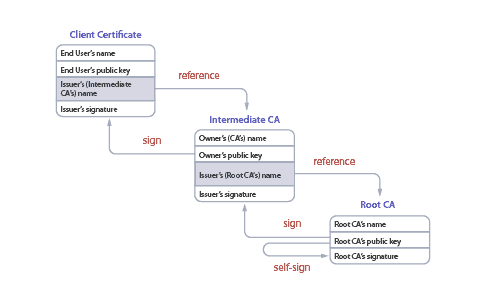
Ways of using digital certificates
Digital certificates may be applied in the following ways: debit and credit cards utilize chip-embedded digital certificates that link banks and merchants to guarantee that the transactions carried out are authentic and secure. Digital payment firms utilize digital certificates to validate their kiosks, automated teller machines (ATMs), and POS (point-of-sale) equipment in the field with the central service within their data center. They are utilized in a secure email to recognize one user to another and can be employed for electronic document signing (Danquah & Kwabena-Adade, 2020). Further, computer hardware producers embed digital certificates into cable modems to assist in averting broadband service theft via gadget cloning.
Types of digital certificates
Web browsers and web servers utilize three forms of digital certificates to validate over the internet. They are applied to connect a web server for a domain to an organization or an individual that owns it. They are termed the SSL certificates and these include domain validated (DV) SSL, Organization-Validated (OV) SSL, and Extended Validation (EV) SSL. The exact criteria and approaches CAs adhere to offer these forms of SSL certificates for web domains are changing because the CA sector adapts to new applications and conditions. The benefits of a digital certificate comprise privacy, ease of use, flexibility, and cost-effectiveness (Radif, 2018). Nonetheless, some of the limitations of using digital certificates are security, slow performance, management, and integration.
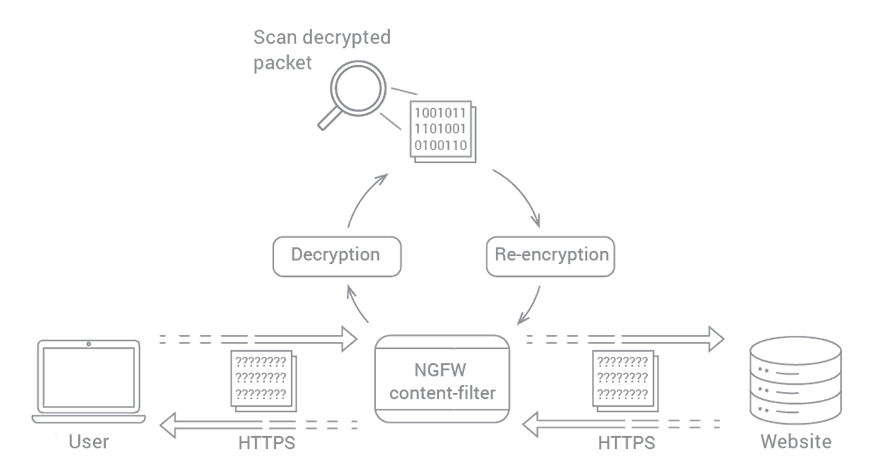
The SSL Inspecting the Use of PKI
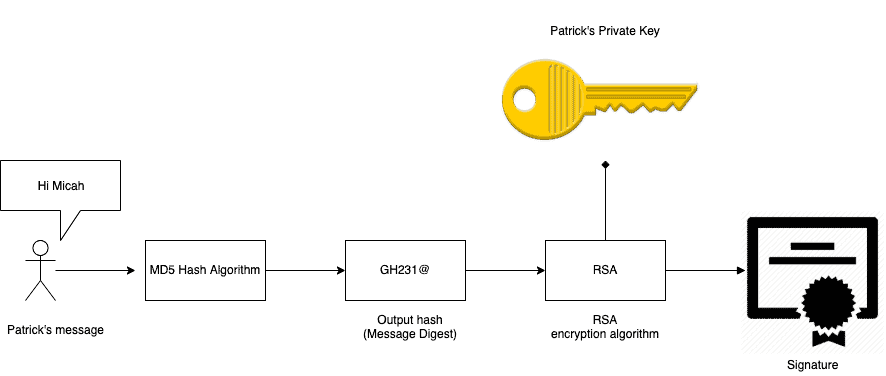
Digital Signature Process Illustration
Digital Signatures’ Weaknesses
Digital signatures like other electronic products have certain shortcomings that go along with their use. These comprise expiry, they depend on technology that it was based on like other technological products. With these modern fast technological improvements, most of these technological products have a limited shelf life. Certificates are another limitation because for one to effectively utilize digital signatures, both recipients and senders should purchase digital certificates at a cost from authenticated certification agencies. Further, entities need to have software to work with these digital certificates. Hence, recipients and senders have to purchase validation software at a fee. In addition, the law creates another challenge because, in some countries and states, laws concerning technology and cyber-based issues are non-existent or weak. Trading in these areas becomes a risk for entities using digitally signed documents (Radif, 2018). Lastly, compatibility which there are several digital signature criteria, and many of them are incompatible with one another and it obscures the sharing of digitally signed documents.
Vulnerabilities
Susceptibilities in illegal digital certificates permit Spoofing
Using vulnerability management tools such as AVDS is the standard approach for this vulnerability discovery. The main shortcoming of VA in discovering this susceptibility is associated with setting a proper network scan frequency and scope. It is critical that the broadest array of hosts possible are scanned and this scanning is carried out often (Radif, 2018). It is recommended weekly and should be made possible, affordable, and easy.
Testing of penetration for the vulnerability
The vulnerabilities in illegal digital certificates permit spoofing is prone to false positive reports in many vulnerability evaluation solutions. This issue can be removed using AVDS as it used behavior-based testing. In other VA tools, a security consultant can propose authentication by direct observation (Winnard et al., 2018). The ideal is having pretesting accuracy and the cope and frequency possibilities of VA solutions and must be accompanied by AVDS.
Updates of Security on Vulnerabilities in Illegal Digital Certificates Permit Spoofing
In the existing updates on the susceptibility, please one should look out at www.securiteam,com if it is one of the most often found susceptibilities, there is enough information concerning mitigation online and a good reason to have it corrected. In addition, hackers are aware that it is often found susceptible; therefore, its detection and repair are of significance (Radif, 2018). Hence, any networks that are present and lack mitigation create an avenue for attackers.
Certificate Revocation
According to the best practices, it is required that whenever a certificate status is maintained, it should be checked if one needs to rely on the certificate. Failure to do this, a revoked certificate can be inaccurately acknowledged as valid. It implies that for the application of a PKI efficiently and effectively, one needs to have access to existing CRLs. The presence of a CRL means the need for a person or an organization to enforce policy and revoke certificates seemed to go against the operational policy. However, if a certificate has been revoked mistakenly, substantial issues may arise (Danquah & Kwabena-Adade, 2020). A certificate must be revoked instantly if its private key reveals signs of being interfered with or compromised. The Certificate Revocation List (CRL) stores certificates that have been revoked. The Online Certificate Status Protocol (OCSP) is the recent and complex approach to discovering revoked certificates. In this case, a client may send the certificate that appears compromised to the CA (Winnard et al., 2018). Upon receiving the certificate, the CA will then return the certificate status and revoked, good, or unknown.
Possible Remedies
Revoked certificates cannot be reactivated in the future as is for disabled certificates. However, the possible remedies to avert certificate revocation and inconveniences. These include import certificates where one has control of all the certificates. Change certificate PIN to permit one to alter the operations PIN assigned to a certificate. Further, one can temporarily disable a certificate and re-enable it without having to revoke it (Fecha, 2021). Lastly, one can employ the management of user permissions and configurations.
References
Danquah, P., & Kwabena-Adade, H. (2020). Public key infrastructure: An enhanced validation framework. Journal of Information Security, 11(04), 241-260. Web.
Fecha, M. E. (2021). Revoked digital certificate: What to do in these cases? Ivnosys Solutions. Web.
Radif, M. (2018). Vulnerability and Exploitation of Digital Certificates. New Trends in Computing, Communication, and Information Technology (NTCCIT), 3(2), 1-18.
Raphaely, E. (2022). Public key infrastructure: Explained. SecureW2. Web.
Winnard, K., Bussche, M. V., Choi, W., Rossi, D., & Redbooks, I. (2018). Managing digital certificates across the enterprise (7th ed.). IBM Redbooks.