Introduction
Every single corporation or organization that deals with the Internet software connection has its data with serious or sealed information hidden from the outside views. Software security and protection are currently issues nowadays, considering emerging cases of diverse malicious attacks and cybercrimes. Without proper online protection, online businesses might face several problems, such as trojan attacks, hacker intervention, and bug meddling in a company arrangement. To avoid and eliminate possible online malfunction, organizations implement diverse software, so-called shields, and programs to facilitate their information data security. Within a wide variety of tools, corporations resort to Firewall protection, a device that designs itself as a number one trustworthy cyber spy.
Firewall
A firewall is considered to be a software “wall” that detects and identifies all alleged cybercriminal attacks in a company network or intel. As computers with internet access are vulnerable and susceptible to various cyber threats, organization participants, represented by IT specialists and experts, usher in and devise new protective approaches liable for information safety. Liu and Ri (2020) stated that VPN (Virtual Private Network) is a widely deployed technology that allows internal users to roam and build their encrypted tunnel by means of Firewall protection. According to Li et al. (2021), “the embedded Firewall can distribute the intrusion prevention function to individual PC, notebook, and server in the network. Embedded firewalls distributed throughout the corporate network allow users to easily access information without exposing network resources to potential illegal intruders” (p.2).
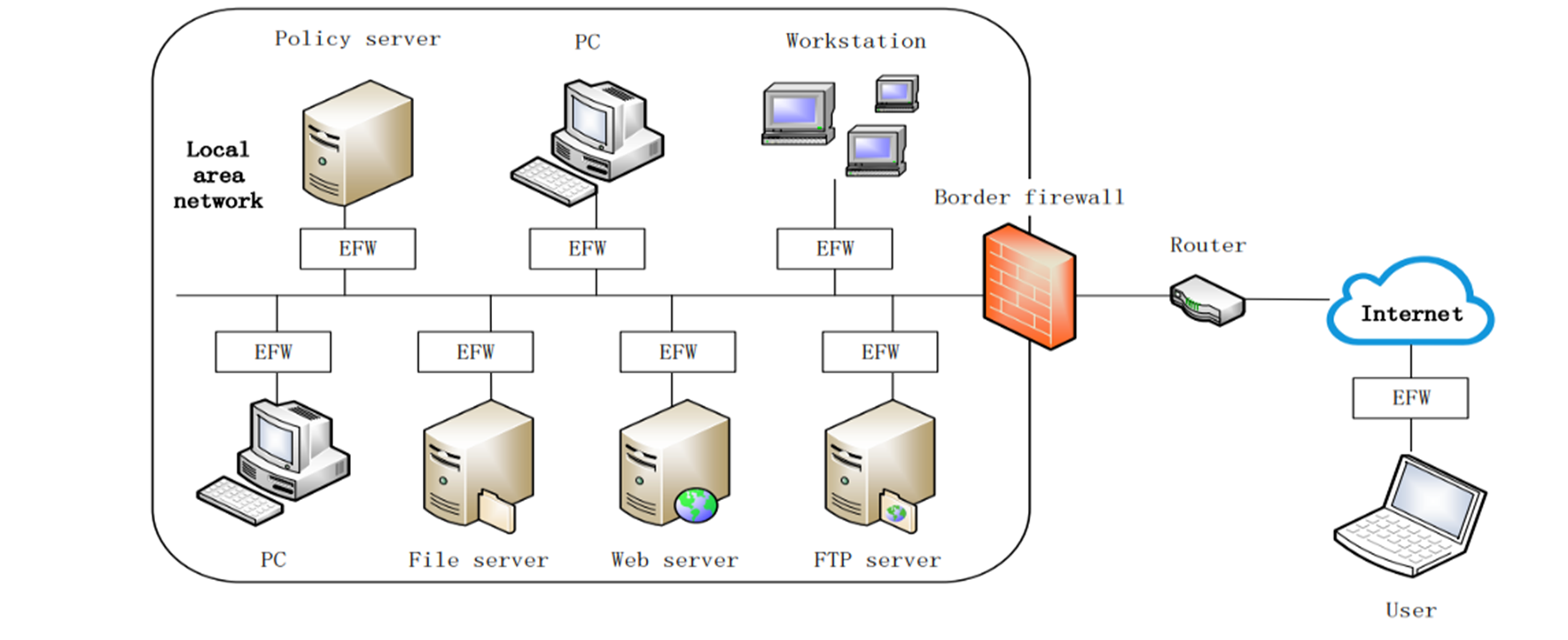
In Figure 1, the overall firewall mechanism is depicted clearly. A firewall operates as a protective shield that might prevent hackers from probing and combing a company data network. While there is a great expanse of upsides of this cyber contraption, there can be drawbacks as well. Realizing both benefits and downsides, companies might input this technology into their organizational processes with a few side-effects and consequences for their own business.
Advantages of Firewall
Monitor traffic or packet filter
A premier liability of a firewall is to monitor the traffic information going through a server. All information presents in the form of packets, some parts of these packets can include malicious threats or viruses. To prevent their intervention into a network, Firewall uses a packet filter. The firewall investigates and inspects hazardous meddling and threats in software by means of this filter. In case a Firewall detects them, it eradicates them or blocks them, thus guaranteeing the further functional process without malfunctions and system crashes.
Protection against Trojans
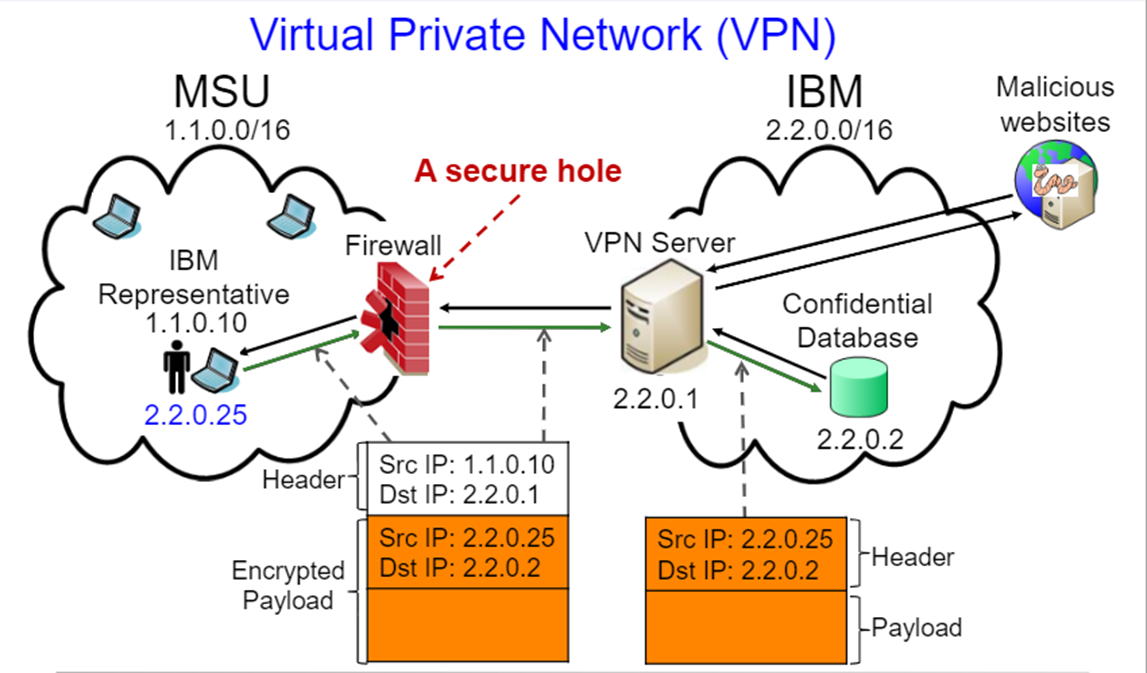
Malware stands for malicious software; cyber programs in the form of trojan or bugs trespass a company network space to steal a hacked software. Obviously, Trojans are very dangerous and invisible. They travel in a network space without clear signs of their presence as they collect or probe information a company operates. In Figure 3, it is seen the way a Firewall interacts with possible hazardous threats. In this illustration, MSU stands for Million Service Units, while IBM stands for International Business Machines. It is evident, that MSU and IBM are intrinsically linked, as they are significant components of every single software. As depicted, outside malicious websites are blocked with a Firewall; they cannot travel into a confidential database.
Hacker prevention
Hacker intrusion is a significant phenomenon in the IT security sphere. Hackers long for vulnerable computers in order to perform illegal activities such as stealing information or breaking a network. In case hackers find susceptible devices, they penetrate them to implement their malicious, spreading viruses. A firewall is the best solution to prevent such penetrations. They can cause irreversible consequences for a network space and all information repositories that keep all pertinent company information.
Host access
Most networks have their hosts with secret information, which is hidden from outside people or cybercriminals. Users insert a special valid security mode to hide or seal host information and prevent entrance into these hosts. A firewall can enforce this security and provide access only to participants who have the right to enter this system, as privacy is one of the profound elements of Firewall security. Moreover, every user has their domain name service, where only this very user can enter inserting their personal account data. A firewall service can guarantee that a user’s IP address might be invisible for hackers to intrude.
Disadvantages of Firewall
Cost
Firewall services are not free as they have constant investments and pay to use net protection. As a rule, a firewall is expensive to protect all hosts and domains. Besides, implementing this service into a network space requires first-hand counseling of IT experts who can guarantee appropriate protection of different company data. Not all average users can afford this tool; only prosperous and profitable companies and organizations can invest in this security program for their performance and arrangement without oncoming hacker attacks.
Users Restrictions
A Firewall is a personalized tool for one user; it cannot be used by all company members. It does not provide an organization with multiple access, as one domain belongs to one user only. It implies that the overall organizational processes of a company can be affected, as all mechanisms are slowed down. All entrances into a host are authorized by one person who can do only certain operations. Sometimes, employees resort to the usage of so-called “backdoor” exploits so as not to get access to all hosts. As a rule, this practice might entail a malfunction of the whole security platform, as it might alert on invalid and insecure logging.
Malware Attacks
Although a Firewall service is in charge of protection and security, it faces several severe attacks by hackers, whose operating systems are better performed. This kind of malware program can pass through a company system to extract its files. A mindset says that it is better to have an anti-malware protection tool combined with a Firewall to eradicate all possible threats and risks. All uploaded software, anti-malware services, and security devices might limit an organization’s performance due to its overloaded adjustment and possible malfunctions.
Complex Operations
A Firewall is made, primarily for small businesses, but it is not devised for large corporations and organizations. Firewalls require a set of concrete stuff teams for each host to operate and maintain in large corporations. A group of users monitors the performance of a Firewall to protect a network space from outside cybercriminals. This form of separate work might slow down a company’s process, which can entail losing other opportunities.
Conclusion
Diverse organizations pay much attention to their data and information security level, as their developments, analysis, and statistics include the complex work and maintenance of these very companies. This secret information cannot be stolen, as this information is a credible image of all processes undertaken in a company. These encrypted details are a company property that cannot be passed to competitors. For this very reason, various corporations use anti-malware security programs to save the company’s future and its participants. A Firewall is treated to be one of the most efficient and trustworthy devices used widely and intentionally.
References
Li, Y., & Zhang, X., Jia, B. (2021). The design of hardware firewall based on Acorn RISC Machine. In IOP Conference Series: Earth and Environmental Science. IOP Publishing ,692(2), -022038.
Liu A.X., Li R. (2021). Collaborative enforcement of firewall policies in Virtual Private Networks. algorithms for data and computation privacy. Springer Publishing. General Press.