Introduction
Proper network architecture can enhance security and efficiency as crucial factors in communication. In design, the network’s configuration and protocols must provide prompt and effective user identification and permission (Troia et al., 2020). The network architecture and services employ the Open Systems Interconnection (OSI) model as most network topologies. This paper aims to simulate an entire IP network and investigate its performance under different network conditions using the Riverbed Modeler (OPNET) simulator. The objective is to examine the effect of routing protocols on network performance. The network operations are investigated by creating a simplified version of the London Metropolitan Area Network (MAN) network, which directly links all the Swiss universities. In network architecture implementation, networking expenditures, such as those associated with infrastructure, hardware, and software, as well as operations, support, and service, may be significantly improved with proper network architecture.
A Literature Review on WAN Performance Optimization
Engineers must consider several factors in network architecture design while creating a network. The implementation must factor everything from security and disaster recovery to network speed, usability, dependability, and redundancy. In design assessment, a network’s effectiveness can be gauged by measurement, modeling, or simulation, including the application of OPNET. Several protocols must function in concert for data to be sent effectively, reliably, and securely via a network. Establishing a route between any two devices in the network and allowing data exchange between the network’s gateways are two of the most crucial variables determining network operation (Nurelmadina et al., 2021). In a Wide Area Network (WAN), routers can interact via gateway protocols, which depend on the network’s configuration.
Wide Area Network Architecture
The WAN architecture is implemented as a grouping of interconnected telecommunications networks dispersed over a broad geographic region. The WAN provides the networks for cities and countries, allowing the component networks to communicate. In design and implementation, WAN types may be divided into switched WAN and point-to-point WAN, which are the two main kinds (Nurelmadina et al., 2021). In addition, there are five types of WAN based on the technology used to support them. A shared networking architecture connects several component LANs in a switched WAN network. In network design, the primary responsibility of the technicians is to ensure optimized operations that provide efficiency and security in communication.
Performance Optimization in Backbone Networks
With the surge in popularity of cloud computing, businesses face significant WAN optimization control difficulties, such as ensuring excellent Quality of Experience (QoE). The QoE is configured to enhance communications as a service by lowering round trip time (RTT), signal loss, and jitters in the system. The implementation requires handling jitter and packet loss while overcoming any delays during transmission. However, there are concerns that since traditional WAN optimization techniques are only intended to minimize bandwidth usage, the technologies are of little use in addressing these issues. The positive aspect of the advancements is that the Cloud provides businesses with network optimization technologies.
Eliminating Latency
In the past, Multiprotocol Label Switching (MPLS) gave businesses pricey yet low-latency communication between facilities. In such circumstances, facilities are connected at the bare minimum required capacity. WAN optimization tools have been developed to address this issue, allowing users to maximize the use of MPLS bandwidth. However, the utility of WAN optimization equipment was diminished by the transition to a mobile-first, cloud-first company. Branch offices must transfer traffic back to the secured Network gateway in the servers since there are more resources in software as a Service (SaaS) cloud systems. There were compromises with WAN based on appliances and VPN based on the Internet as a replacement to MPLS.
Compensating for System’s Packet Loss and Jitter
While connection availability, packet loss, and jitter are often encountered WAN performance issues in the final mile, latency is predominantly a concern in the intermediate mile connections. Utilizing a variety of network optimization methods, such as packet loss mitigation, active link utilization, and brownout mitigation, the Cloud enables WANs to alleviate these last mile issues (Nurelmadina et al., 2021). Cloud SaaS decreases the time it takes to find and recover dropped packets by segmenting the network to mitigate packet loss. The Cloud replicates transmissions across network communication for all or some apps when connections are too unreliable.
In WAN optimizations, the cloud-supported networks integrate and control multiple Internet connections in active link utilization, routing traffic on both lines concurrently. Customers can aggregate bandwidth for production usage using active-active rather than having idle backup lines. The approach can enhance brownout mitigation by automatically detecting packet loss changes and switching traffic to an alternative channel as they occur. Traffic is automatically switched back to primary connections when packet loss rates drop below predetermined criteria.
OPNET Simulator
The simulation used in this study to assess the handover effectiveness across a transmission model specified as vehicle speed is OPNET modeler 14.5simulator. A visual interface (GUI) is provided by the OPNET Modeler simulation environment, allowing researchers and practitioners to investigate and assess various technologies, applications, and interfaces via wired and wireless systems. In this project, the OPNET modeler uses a hierarchical method to model network connectivity and is object-oriented.
Building a Network Model
This section creates a simplified version of the London MAN network, directly linking all Swiss universities. It will create a streamlined version of the London MAN network. The network is designed to connect all Swiss universities directly via a WAN. OPNET offers a complete toolkit and user interface for the construction and design of topologies. The network community’s agreement on the outcomes’ reliability is another benefit of adopting OPNET. In the simulations, the realistic analyses of performance metrics and the efficacy of wireless network design methodologies are made possible by OPNET. The Swiss campus networks are operated at a data rate of 11 Mbps in scenario one and a maximum throughput of 1 Mbps in scenario 2.
Justifications for the Designs
In the design, the MAN is implemented as a common connection point for devices that link workstations in an area with many buildings, like in London. By design, the size of a MAN is more than that of a LAN but less than that of a WAN. The London MANs, for instance, connect many interconnected local area nodes. MANs are implemented as bigger than LANs but lesser than WANs that directly connect users in the larger institution’s branches over massive geographic distances. The MAN provides support for the WAN by delivering high-speed carriers, such as fiber optic connections, which can be used to transmit data quickly. In the model, a wider range of transmission methods is becoming accessible with the introduction of cordless devices and subsequent networking systems.
Links
Three routing protocols are selected, including Routing Information Protocol (RIP), Interior Gateway Protocol (IGRP), and Open Shortest Path First (OSPF). In the designs, one of the purposes of building the network models is to simulate its performance and thus identify potential performance-affecting issues. The transmission lines and switching devices comprise the WAN network design subnet, which has two separate components. Transmission lines, consisting of copper wire, optical fiber, or radio connections, transport information between equipment.
In implementing WAN architecture, the network has many transmission lines, each connecting two routers. To communicate with each other, the signal must go via another router, two router units that do not connect via a transmission line. Packets are delivered from one router to another through the intermediate routers. It is received at each of those routers, kept there until the necessary output line is available, and then transferred to the receiving terminal. In the models assessed in Figure 2, an Interior Gateway Protocol, the OSPF protocol is implemented as a series of IP network topologies used to redistribute IP routing data across a single Autonomous System (AS) in an IP address (Okonkwo and Emmanuel 2020). In the design, the link-state routing OSPF system allows routers to communicate topological details with their immediate neighbors. Every router in the AS has access to the topology data, giving every router in the AS a comprehensive understanding of the topology of the AS.
Routers
The hop count is the primary statistic in the distance vector protocol known as the Routing Information Protocol (RIP). RIP specifies how routers should exchange information while transferring traffic between a collection of linked local area networks (LANs). The ease of configuring and implementing RIP is its most significant benefit. In general, there are no loops. The fundamental purpose of the distance-vector technique outlined earlier in this section and how messages are employed to accomplish it are the two key areas where we uncover significant problems with RIP. The architecture has four major issues: counting to infinite loops in the routing, tiny infinity, and delayed convergence.
Applications Running
Verifying network information dissemination will restrict users’ access to the network. The number of users is limited to some level, which is good for the network’s efficient functioning. Since there are several methods for restricting access, approved software may be deployed between the sender and receiver to grant authorized visitors access to the system. Users can access information with fair equality of opportunity through communication systems. In the designs, each user’s rights are correctly assigned by the network information manager, who should also provide audit information on system access.
Traffic Generated
Based on the traffic generated, the user show the need for emphasis on network architecture, and redundancy is intended to provide network operations with double assurance. In such network models, it makes use of a redundant dual-core architecture. Dual network redundancy spanning layers and connections is a feature of computer networks. As a result, it provides a backup for the internet infrastructure irrespective of where the issue arises. Core switches and servers in network infrastructure often use redundant designs. Links can still be opened, and application platforms can function normally when a problem arises. Consequently, computer networking dependability will be efficiently secured.
Investigation and Analysis of Simulations
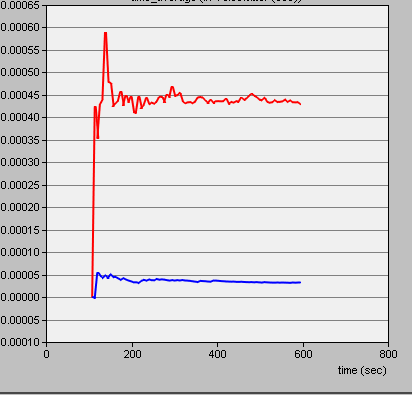
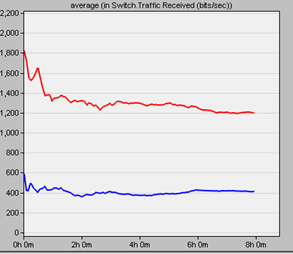
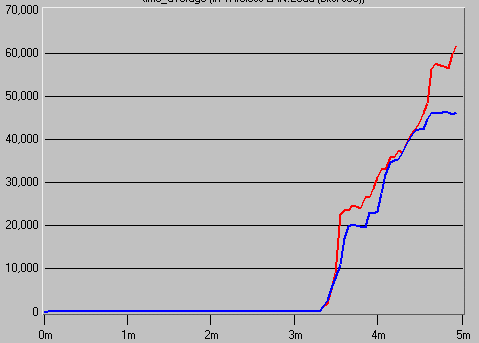
Under ordinary conditions, the Routing Information Protocol (RIP) is blue. In scenario 2, Node Failure Conditions, red in figures 1, 2, and 3 for rates of traffic sent, traffic received, delay, packet loss, and jitter show a difference in performance. The simulations in Figures 1, 2, and 3 show scenario one at 1024kbit at 11 Mbps and scenario two at 1024000kbit at 1 Mbps.
Routing Information Protocol
The distance vector protocol implemented as the RIP employs hop count as its design’s primary measurement. As in data rates in Figure 1, when transporting traffic between a linked collection of local area networks (LANs) within the institutions, the RIP specifies how routers should communicate information, significantly improving the data rates at 200 msec. The protocol via which routers may communicate about the topology of a network. Small-to medium-sized networks are frequently used as inner gateway protocols. The architecture of the RIP networking is built to allow for frequent network upgrades, broadcasting of entire routing tables, and updating of routing information.
Interior Gateway Protocol (IGRP)
In the design, the host network uses the IGRP as a proprietary distance vector routing protocol to exchange routing information. In Figure 2, the normal condition operations demonstrate data rates higher than the node failure scenario two but decline with loading. According to the plan, the IGRP controls the routing of data sent across linked routers in the network segment. The IGRP is capable of load balancing over connections with different costs. IGRP is a Cisco-developed routing technology that can only be used with Cisco routers. By default, IGRP will increase capacity traffic if there are many routes to the equally expensive destination.
Open Shortest Path First (OSPF)
In figure 3, the handover procedure is initiated along the planned route as the signal travels through the Swiss institutions. Every node suffered a delay because the coverage area for BS 1 and BS 2 is more significant. The waiting time for these two network components is longer than the delay BS 0, whose coverage is geared to interlink and open spaces from the different institutions’ LAN networks and experiences. The simulation’s delay parameter, often called the handover process, is intended to track how long it takes a mobile user to connect to and disconnect from every BS. The average value in the simulations results from the most minor and most significant values at each base station.
Conclusion
The Swiss campus scenario for a switched Ethernet network on a WAN network demonstrates a functional network architecture with redundancy. The campus facilities’ data exchange rates are depicted based on the idea that each contains unique domains and computers categorized as campus units, respectively. Network simulation considers a WAN situation with three Swiss campuses spread across several geographically diverse regions. Today, the Internet has ushered in an era of information in which everyone is connected in work and life. Large and small computer networks are experiencing information exchange and transmission as the Internet has been widely used. As in the efficiencies observed, the OSPF is the most recommended routing protocol. OSPF always uses the shortest path to forward packets, which causes traffic to increase. Although additional pathways are less crowded than the shortest path, OSPF consistently favors using the shortest route making the systems more resilient.
References
Nurelmadina, N., Hasan, M.K., Memon, I., Saeed, R.A., Zainol Ariffin, K.A., Ali, E.S., Mokhtar, R.A., Islam, S., Hossain, E. and Hassan, M.A. (2021) ‘A systematic review on cognitive radio in low power wide area network for industrial IoT applications’. Sustainability, 13(1), pp.338. Web.
Okonkwo, IJ, and Emmanuel, I.D., 2020 ‘Comparative study of EIGRP and OSPF protocols based on network convergence’, International Journal of Advanced Computer Science and Applications, 11(6), pp.39-45.
Troia, S., Zorello, L.M.M., Maralit, A.J. and Maier, G. (2020) ‘SD-WAN: an open-source implementation for enterprise networking services’, 22nd International Conference on Transparent Optical Networks, 2(1) pp. 1-4. Web.