The information revolution and ‘cyber crime’
Understanding Cyber crime
Ajala (2007, p.1) stated that the development of internet has changed the entire communication system and it has replaced the traditional mailing and telecommunication system due to availability of global broadcasting capability. Ajala (2007, p.1) further added that internet has broaden the business scope and secured investment by developing communication between business persons of different region. However, Ajala also mentioned that the risk of internet fraud as it is one of the most powerful information tools, which help the criminals to gather knowledge about the victim.
However, the criminals get the opportunity to use personal information in order to undermine the credibility and to destroy the image of the innocent person to be benefited economically or for other purpose. According to the view of Algarni (2011, p.1), Saudi Arabia has experienced huge problem with the issue of internet fraud and other forms of cybercrime but most of the case they would not like to take any legal steps or disclose the crisis with others. In this context, the aim of this literature review is to describe the problem of internet fraud and response of the police in Riyadh with theoretical framework.
However, many scholars have already researched on this problem to assess the extent to which it can create disturbance for the ordinary internet users, and they try to provide possible solution to the policy makers and programmers to protect this crime but no effective solution has published yet, which can practically stop the criminals. As a result, the scholars have also defined the term in many ways, for example, Algarni (2011, p.1) stated that this crime includes the use of computers and the internet as a tool to perform illegal activities, while ITC (2009, p.19) defined the term “Cybercrime” as an illegal or illicit computer-mediated functions.
On the other hand, ITC (2009, p.19) reported that criminals can also take all the information of other computers though the victim is in different country; as a result, the concept of privacy could destroy both in personal and higher level. However, Algarni (2011, p.1) also pointed out that cybercrime is the threat for the society as it increases viewers of hard-core pornography, which destroys public morals. In addition, the victims may financially affected because this crime has adverse impact on intellectual property of the victims while the hackers access the online business, credit card security system and others function.
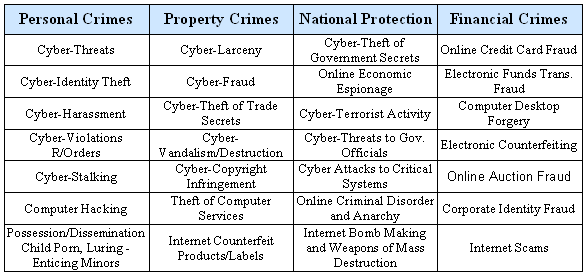
Classification Cybercrime
- Financial crimes/frauds and theft: Ajala (2007, p.2) stated that financial loses occur when criminals cheat the users, take the information of credit cards in unfair means and use it accordingly, misuse personal information to theft, involve with money laundering, and other related crimes. However, Ajala (2007, p.2) described internet fraud as privative gain or advantage by changing input in an illegal way, taking output dishonestly, making unlawful amendments to gather information about the victims’ banking details with personal information, and modifying and abusing programs. However, financial fraud is the one of the most common scenarios among all kinds of internet fraud cybercrime because this is the easiest process to victimize the people economically (Ajala 2007; Wall 2005; ITC 2009; and Cashell, Jackson, & Jickling, 2004).
- Hacking or Illegal Access: Ajala (2007, p.1) described that hacking is intentionally gaining an unauthorized access to the computer system and ITC (2009) stated that it is oldest form of cybercrime particularly breaking the password to access password-protected websites and circumventing password defense on the PC are the most common practice in the world. They further added that the hackers hacked the computer and other websites with different motivation or intension; as a result, the extent of damages is not equal in every case. Some hackers or groups act maliciously to victimize ordinary users or influential government agencies, but most of the damages occurred for nuisance attacks. As a result, victims suffer pecuniary loses, for instance, BBC reported that ‘love-bug’ virus crippled as a minimum 45.0 million PCs in all over the world and caused severe financial damage of the victims (Ajala, 2007). On the other hand, hacking in harsh nature known as “hacktivism” cause serious damages, for example, cyber attacks on Airforce, Yahoo, Google, and other important sources like NASA’s computer system not only cause financial loses but also can misuse important information;
- Online gambling: there are numerous websites offering online gambling but many of these sites used for money laundering;
- Cyber pornography: many pornographic websites those can destroy public morals particularly children’s morals. There are laws to protect child pornography and store such materials as these pornographic sites is allowed to access for the adults but not for children and the visitors need to maintain some procedures to visit these sites (Wortley & Smallbone, 2006). However, there is no specific rule to verify the age of the users, for instance, websites initially states if you are under 18, please exit this page as this sites for adults; therefore, people of all age can visit without any barrier by clicking enter button;
- Intellectual property crimes: This crime includes software privacy, infringement of copyright act, violation of trademark laws, and so on;
- Internet harassment: This is the process for harassing users by making insulting and racially aggravated comments or directing obscenities towards others in terms of faith, nationality, and sexual orientation.
Cyber security against Cybercrime
ITC (2009, p.14) pointed out that cybersecurity has a significant contribution to advance information technology, and Internet services as cybersecurity and protecting critical information infrastructures are crucial factors to the IT world in terms of national security, personal welfare, and economic growth. However, ITC (2009, p.14) further stated that it is important to enact new laws in order to protect the IT sector from the criminals as national security and privacy is depended on the implementation of the laws. In this circumstance, the improvement of the security system can be possible by developing co-operation between programmers and organizations; for example, programmers must try to protect the website using their talent and the employers must be aware how to use their website safely.
On the other hand, the programmers emphasized more on the consciousness of the users to avoid the risks though formulation and execution of a national framework and policy for cybersecurity has potential impact on the entire protection system. At the same time, it is also important to implement advance technology and to provide proper education to ensure security of the users along with fight against the activities of the criminals. However, the scholars identified that it is a global problem; therefore, it should require to have unified strategy to protect the world from this challenge. ITC (2009, p.14) argued that the WSIS acknowledged the genuine and major risks posed by insufficient cybersecurity and the proliferation of internet fraud, as a result, WSIS provided guidelines and implementation plan in the paragraph 108 – 110.
However, this plan provides the multi-stakeholder implementation procedure consistent with eleven action lines and allocates responsibilities to assist to implement these different activities along with developing confidence and security in the exercise of ICTs, therefore, the ITU Secretary General introduced a global framework known as GCA (Global Cybersecurity Agenda) to develop cooperation in international level response to the rising challenges. At this stage, GCA included seven key strategic objectives in order to fight against cybercrime by an integrated method, such as, legal method, technical measures, organizational charts, capacity building, global collaboration, etc.
GCA further addressed that collaboration of seven objectives is significant factor as implementation of single objective would not be able to stop cybercrime. For instance, technical measures can help to reduce crime but it cannot give ultimate solution, so legal measures need to apply to give justice to the victims while modern technology would assist to investigate the case. On the other hand, organizational charts concentrate on the prevention of critical information, detection, and response to the crisis, while capacity building spotlight on elaborating policies to build capacity mechanisms to increase awareness, and international cooperation muse on international cooperation, conversation and harmonization in case of cyber-threats.
However, GCA suggested that legal measures have emphasized the advance of the legislative provisions with technological adaptation consistent with the nature of the crime because to investigate different types of cybercrime need different types of technical tools and the punishment level should different considering the extent of damages. In addition, ITC (2009, p.15) reported that the law enforcement agencies require the essential and different instruments to investigate Internet fraud besides substantive criminal law provisions, which is also subject of new challenges, for example, perpetrators can commit crime from any location of the world and take preventive actions to disguise their identity.
Economic Impact of Cybercrime
Cashell, Jackson & Jickling (2004) stated that cybercrime has major impact on the stock market and ITC (2009, p.63) reported that Internet crimes is one of the most crucial causes of economic damage in modern era. ITC (2009, p.63) further stated that many scholars have conducted survey to assess the economic impact though there is a doubt regarding the findings of the survey reports or accuracy of the statistics because most of the time victims are reluctant to file a case.
Overview of the Results of Some Surveys
In 2007, the Computer Security Institute (CSI) had conducted a research in the US and interviewed to the police, policy makers, organizations, and financial institutions to measure the economic impact of cybercrime and the response of security agencies particularly polices to prevent such crime (ITC, 2009, p.63). However, this survey report identified that the economic impact of cybercrime was reduced from 2002 to 2006, but loses from criminal activities have increased dramatically after that period in this country. At the same time, the aggregate loses of the respondents in the US from internet theft was accounted of $66.90 million, which is ten times grater than the economic loses of 2001.
On the other hand, FBI also conducted Computer Crime Survey consistent with Computer Security Institute survey, where FBI estimated that net loses of the respondents from cybercrime was only $21.70 million, but the overall loses of the country was more than $67.0 billion in 2005, which is really alarming to the corporate world and small companies. It is important to mention that the aggregate impact from different survey reports show different amount though the researchers estimated the impact for the segmented problems, for instance, Computer Economics Malware Reported that the hackers design malicious software, which caused huge financial loses (more than $17.50 billion in 2004).
Problems connected to Internet Fraud Statistics
Different results of survey reports have already created confusion and raised question on the reliability of the net loses to the readers, and affected persons. In addition, the results of these reports identified that the aggrieved persons are not willing to report their problems and the police are not co-operating to help the affected persons though low enforcement agencies try to aware people if any offence commit. However, Cashell, Jackson & Jickling (2004) suggested that the users should report to the police as soon as offence committed in order to discourage possible attacks in the future and enact effective legislation considering the nature of the crime. However, many researchers have tried to calculate actual loses from direct and indirect sources but they got no formula to estimate real loses due to hazardous software and other activities of cybercriminals. In this situation, many organizations engaged their efforts to innovate products to reduce cybercrime like many malicious software damages hardware and software of the computer and create financial loses.
The limits of the sovereign state (theoretical discourses on crime control in late modernity)
The Limits of the Sovereign State
In a number of instances, sovereign states has inflicted by a range of limitations over its rights to policing over offences of internet fraud. These limitations occur for a number of reasons. For example, when the United Kingdom decided to be the member state of the European Union, its parliamentary sovereignty was destroyed. It is important to argue that the United Kingdom had no written constitution – its parliament was sovereign and it preserved all rights of leading the state as well as making all laws. However, as it went on to be a member nation of the European Union, the Commission and the European Court of Justice suggested the country that all its legislations, judgments, rules, and guidelines prevailed the laws and rules laid down by the UK parliament together with the precedent judgments made by the House of Lords itself.
These seriously hampered the parliamentary sovereignty of the country and damaged the Principles of Parliamentary Sovereignty laid down by Sir A. V. Dicey. This consequently led to the conclusion that the laws of the European Union will always dominate over the laws of the UK – as a result, today, all laws of the country, including the laws of policing over offences of internet fraud, are prevailed by the European Union. According to Crawford and Lister (2003) for the country, this imposes a great limitation over the sovereignty of the state.
When it comes to Saudi Arabia, the concern over the limitation of the sovereign state lies behind the fact that the country has always controlled by the Shari’ah law, and still today, it cannot think of being running devoid of this law. It is unfortunate that the Shari’ah law has not covered any areas as far as cyber crime or internet fraud is concerned, and neither to the arguments of policing over these crimes. As a result, a sovereign state like the Kingdom of Saudi Arabia needed to face a limitation when it comes to crime control.
In context, internet hoax and other types of cyber crimes have turn out to be an increasing alarm today in KSA; a large number of changing of online sham comes into view in a highly conservative community like the KSA; nevertheless, a substantial number of sufferers of online shams still do not think about telling their occurrences to law-enforcement organizations. This, in a large number of instances, occurs as a resultant effect of the common observation that cyber crime is never ever a punishable transgression in the societies of KSA – this carries to the front the lawful instruments for prevention of online swindles. Even before a few days, KSA did not have any precise and explicit legislation intended to deal with online cheats, PC generated unlawful acts, web hacking acts, or other types of fiddles like online credit card deceives.
However, in Feb 2007, as a consequent effect of rising strain on the Saudi government by a range of worried groups about the limitation of the sovereign state to prevent internet frauds and stop the hacks, credit card cheats, and other computer-generated crimes caused the legislators to configure a new legislation (anti cyber crime act) and explanations for cyber crimes. This legislation has soon examined by a huge number of legal professionals very carefully and later, permitted by the Council of Ministers of Saudi Arabia (Algarni, 2011). Numerous experts and legal professionals of the KSA including the legal and regulation enforcing segments together with lawyers, solicitors, advocates, and barristers have appreciated the passing of the new legislation as an important footstep on the way to defending Saudi Arabian conservative cultures from the rising danger of online cheats and other illegal conducts carried out in the modern globe.
Interpretations of crime in late modernity
Criminological speculations have customized through significant methods to the organizational situations of late modernity, or situations where offences are high and the inadequate efficiency of laws have extensively recognized; the most essential feature of this progress is the modification in the regulation’s focus away from speculations of communal scarcity to justifications implied in terms of societal control and its shortfalls. ‘Control’ is the crucial phrase of the latest challenges relating to communal, personal, and conditional control together with criminology, which has, otherwise fairly contrasted these days to share this general trouble-space; it is possible to observe this easily by considering ‘the recent criminology of daily life’ and their clashing corresponding item, the ‘criminology of the others’ (Garland, 2011).
Some people suggests that criminals are no different from other persons, as crime ‘is very human’ and ‘ordinary people’ do ‘ordinary crimes’; moreover, criminals characteristically show no particular inspiration and no unusual or unexpected temperament – they simply react, with the benchmark scales of consistency, to the combination of inducements and joysticks concerned in explicit circumstances (Garland, 1999). The main changeable issue in amplifying offences is consequently the degree to which the necessary activities of communal life do or do not assist offence measures by frequently inserting folks in wrong state of affairs; in the words of economists, offence is a supply side incident, and an outcome of the construction and release of opportunities to execute offences
Fundamentals of Crime Control
It is important to note that Gelsthorpe (2004) has proposed an exhaustive and perceptive chronological and intellectual explanation of in what ways the control of offences and its improvements has observed in the late 20th century, which have specifically personalized and rejoined to the contemporary planet together with its political and social standards. Moreover, some studies swivels regarding the concept that the improvement of approaches of control by considering it in terms of penalties and control as a traditional adjustment to ‘latest modernity’ and the complimentary marketplace has necessary connections with the societal traditions and political affairs which arose to govern the United States and the United Kingdom during the decade of 1980s.
The crime control perception of criminal justice emphasizes to the crime prevention by the utilization of restrictions; in this context, as per this perception, while the judicial structure run powerfully, probable offenders have dissuaded from performing offences, and those who executed unlawful activities have detained, trailed, and penalized with the view that the activities will not replicated. Some researches on these issues argue that offence rates get high, as offenders do not apprehend of being trapped and chastised to an extent that is sufficient to prevent them from executing offences repeatedly; additionally, the advocates of the crime control perception articulates on safeguard of society rather than procedural rights or rehabilitation of the offender. According to Anon (2011), in general, such perception concentrates on the sufferers and emphasizes on prevention of offences by means of definite and strict sentence.
Insecurity, Risk, and Surveillance
According to Owen (2007), contemporary livelihood and the adjustment of communities to with such activities have built an earth where detainees are not the merely those who breathe inside iron-cages of rationality; on the individualized eagerness for market autonomies and personal liberty, people have deserted societal connections, which embrace people together. The consequential feel of uncertainty has led to encompass behaviors and guidelines that would have seemed extremely oppressive before thirty years; these comprise shopping in guarded surroundings, staying in house rather than coming out; the appearance of anxiety, resulting from collapse of relations, society and ethical principles, extensive apprehension regarding offence and hostility; and a disquiet for the upcoming years.
Some people suggest that these are indications of the instability, which features late modernity; fear about financial uncertainty and individual security have led to a way of life where, as per several researcher, electorates in many parts of the world including the United Kingdom and United States permit politicians to catch a rising number of criminals behind the bars. As a resultant effect, they pass more and more ruthless legislations, and inflict a rising number of severe protections on conducts, which has formerly confronted by people in the name of freedom; under such a tradition, for the countries criminal justice structure has come to be considered as inadequacy in its capability to prevent offence and convey safety.
In reaction to the quandary, present societal rules and welfare state resolutions professed to be unsuccessful and have substituted with subsequence; in addition, there has been the materialization of criminology of the precarious situation while others discuss about offence by means of the words of conflict and resistance – societal resolutions have given way to financial resolutions. Welfares and criminology, with its centre of attention upon communal dispossession, has dislodged by a new criminology that emphasizes on preference and prevention -offence prevention has observed as a difficulty of severe deterrents, danger organization, and circumstantial engineering, other than an exertion of societal integrity or personal modification; moreover, old welfare principles of assistance, advice, and helps have discarded.
Diminishing offence rates and scrutinizing individual activities with electronic-technologies has guided a condition where customers have positioned underneath the gape of electronic-inspection and everyone has supervised as a probable surveillance item; the rising exploitation of information technology has amplified the prospective for rigorous and wide-ranging types of surveillance and as an outcome the corrosion of individual confidentiality.
The uncertain nature of late modern life triggers the hastening fear of communities together with prevention and offence management in general; it is important to argue that not merely the offence patterns that have transformed – in fact, civilization has transformed as well, and this alteration has in turn redesigned theories of criminology and communal guidelines. As the idiosyncratic model of communal, financial and traditional affairs that materialized in last quarter of twentieth century, late modernity has carried with it uncertainties and prevention inconveniences; all these played a vital function in determining varying reactions to offence; consequently, it is exemplary of current Western-culture that the actualities recognized in neo-liberal order offers the assurances of fleeing criminality. Now, criminals has not considered as ordinary folks who require of concern and assistance and has rather considered as blamable and unworthy as a great number of hazards has to be controlled; as per specialists, the treatment of criminals is now emblazoned in a scaffold of danger and personal guard rather than one of communal wellbeing and right.
Challenges to the state-sponsored policing of cyber crime
Broadhurst (2006) stated that state-sponsored policing in many countries including developed countries are not capable to react successfully to protect netcrime or arrest renowned cyber criminals. According to the view of Collier & Spaul (1992), there are mainly four factors hampering the investigation process of Internet fraud or cybercrime, such as, knowledge, capability and competence of the investigators, vague term of the definition of the internet crimes, lack of evidence, insufficient provisions and jurisdiction to convict the criminals. However, Stanley (1986) further addressed that reliable statistical data related with cybercrime, rapid expansion of the crime, adaptation of innovative technology and ideas to commit internet fraud and cybercrime, lack of training facilities of the state sponsored police, and advancement of new system. Broadhurst (2006) pointed that effective response of the police is a difficult issue considering limitation of the regulation in many cases.
In addition, there are no particular groups those commit the crime rather millions of people all over the world have engaged perpetrating cybercrime (Broadhurst, 2006, p.4). For example, 14 years old Chinese boy had created websites to misguides the people of Hong Kong by stating that the government decided to close port due to protect SARS epidemic, therefore, the supply chain management system of the supermarkets adversely affected until government declared the news as sham. In this case, the boy was arrested and convicted only for one year, which was very short period considering the consequence of the extent of the damage. Broadhurst (2006, p.5) stated that argued that there are few cases where the criminals arrested for their activities though law enforcement agencies have no imperfection of their duties.
Many scholars like Collier & Spaul (1992) and Broadhurst (2006, p.5) have addressed that jurisdiction is one of the most significant challenge for the policy as national police force have no right to arrest the criminals from foreign countries, for instance, Saudi Arabian police have no right to arrest cyber criminals from China. As a result, it is important to develop co-relation and cooperation between all countries and it should require enacting unified law for all over the world, which will help the state sponsored police to arrest criminals and respond appropriately to reduce cybercrime. However, the new challenge was forensic experts tasked with the process of investigating cybercrime related with bespoke code design, and they identified that high extent use of encryption and access protection create and increase challenge of extracting evidence from PCs and servers (Broadhurst, 2006, p.5). The law enforcement agencies failed to take appropriate step most of the cases because victims are reluctant to report about the offences or they cannot recognise the actual criminal (Collier & Spaul (1992) and (Broadhurst, 2006, p.5).
On other hand, Ajala (2007, p.4) and Broadhurst (2006, p.6) further added that victims are not aware about crime and sometimes they cannot measure the extent of damages particularly in case of virus attacks. In addition, availability of hacking software makes it easy for the ordinary people to break the security codes, even if, children to old age people would like to hack other websites just from the curiosity. In this circumstance, the ordinary people engaged with severe fraud related with telecommunications theft, information to use credit cards of others, damage in the networking system, creation of new virus, and decode personal information of victims. Therefore, the state sponsored police of well-developed countries always upgrading their security system and aware ordinary people to develop their moral values and social behavior. Nevertheless, the police of developing countries are performing with their oldest technology and they have not sufficient training to adjust themselves with new forms of cybercrimes. In addition, state sponsored police of developing countries cannot realize the nature of the crime or mass people have also engaged with this crime and police are unwilling to arrest under or over aged people because of their good faith on them.
Therefore, the situation becomes out of control over the time, though many companies offer solution to the customers but practically ‘patch’ countermeasures have proved insufficient as most of the users failed to update or use the software proper way (Broadhurst, 2006, p.6). However, Wall (2005, p.10) noted that ‘law does not deal with trifles’, so, the aggravated people get no remedy due to the practice of de minimis principle, even if, they file a case because state sponsored police have deal with big issues of the nation. According to the observation of Wall (2005, p.10), state sponsored police ignored small issues such as the problem of spam is most common disturbance to the internet users but law enforcement agencies have taken no measures to stop such problems because spam is not creating any financial loses of the users, so there is no issue related with public interest.
However, Wall (2005, p.10) pointed out that this is not a small factors at all while poorest persons influenced by the spam messages like earn $750 daily from data entry job, and they expend at least %50- $90 to get this job and achieve the success in life, but practically state sponsored police have no concern to investigate this issue. At the same time, spam message is not only create problems of the poor people but it can cause of severe economic loses of original sellers or honest brokers who authentically seek to promote their products and services to the global market (Wall, 2005). In this context, the victims of cybercrime raised question considering the motivation of the state-sponsored policing system as the police forces show reluctance to deal with this issue. However, from the above discussion, it can be said that it should essential to arrange regular training programmed in order to motivate the police to realize the situation and to give knowledge about the latest activities of the cyber criminals because criminals always upgrading their system to perpetrate fraud and hide their identity to the police.
ITC (2009, p.107) stated that GCC countries including Saudi Arabia has already taken initiative to combat cybercrime maintaining international standards, for instance, GCC suggested in the conference in 2007 that they need to seek a joint approach to combat cybercrime. However, Wall (2005) stated that unified code or joint approach for global cyber offences would not be effective in many cases because of different socio-cultural, such as, the definition or nature of the differ country to country. As a result, it is possible that Saudi Arabian legislation defined an activity as a severe cyber offence but the US legislation considered that activity as a normal issue and this problem known as “ultra-social” problem. In this context, the US citizen perform this act and Saudi citizen adversely affects for such act, then the US police will take no action against that person but Saudi Arabian police will seek to take immediate action. In addition, the law enforcement agencies and government of developed countries give special attention on the upgrading the provision of legislation, therefore, they include the serious issues in the legislation (Wall, 2005).
For example, Saudi Arabian policy maker had not provided any attention on the phising and spam message; therefore, the people of this country experienced huge financial loses. On the other hand, Collier & Spaul (1992) rejected the view that well-developed countries defined the crime with consistent wording and they stated that section 1(1) of Criminal Damage Act 1971 only mentioned the word unlawful malicious damage of computer but it is not covering the test to measure dishonestly and when the act would be malicious. However, many people commit this crime without any intension to harm but their acts have significant impact on the society, then state sponsored police have to face problem to understand their responsibility.
Ajala (2007, p.3) stated that identify the criminals is another challenge to the police because the professional criminals never use their personal computer and they operate their function from cyber cafés where many people use same computer. However, Ajala (2007, p.3) pointed out that law enforcement agencies need enough time to locate the particular cyber cafés, and then they have to find out the actual criminals. In this situation, police failed to arrest them due to lack of sufficient knowledge as the criminals use many software and other preventive measures to save themselves from criminal liability by hiding their identity and information.
In addition, Collier & Spaul (1992) reported that 60% of total fraud occurred from the own organization due to lack of internal controlling system but the owner are not aware that it is one of the major internet fraud. From the above discussion, it can be concluded that there are many challenges those state sponsored police face regularly, such as, social difference, huge number of criminals, lack of regulatory provision, difficulties to understand the extent of damages, integration of latest software for hacking, jurisdiction of the criminals or territorial barriers, the practice of de minimis principle, and so on.
Symbolic Responses and The Creation of Police Cybercrime Units
Symbolic Responses
Collier & Spaul (1992) argued that it is difficult to measure the responses of the police since various researchers give different view in their study on the attitudes of police but most the them pointed out that cybercrime is comparatively new crime, which often results from the organization’s failure to defend itself effectively. However, Collier & Spaul (1992) further addressed that police has limited resources and knowledge to manage the ongoing situation. In addition, the have not sufficient equipment as well as training to use the equipment along with the provisions of minor penalties make reluctant the police not to provide immediate service.
Moreover, traditional police forces have no interest on cyber crime while they like to investigate on offences those may carry high sentence. The response of the police is not outstanding as they think cyber criminals are not typically public enemies and they suggest financial institutes has the option of deploying expert staff and equipment for managing internet fraud. In this circumstance, renowned international organizations have already recommended in the convention to save the world from complex threats of human security as well as State security; however, the Council of Europe’s Cyber-crime Convention 2011, and United Nations Convention against Transnational Organized Crime 2000 were the main influential sources of cyber crime acts. However, these conventions addressed the problem considering inhibit serious criminal networks, and suggested mutual assistance between nations (Broadhurst, 2006, p.12).
After terrorist attack in Twin tower and Pentagon in 9/11, international conventions influenced the law enforcement agencies to concentrate on the rising concern about the possible for misuse of ICT by terrorists (Broadhurst, 2006, p.12). However, the purpose of the conventions of United Nations and other international organizations is to protect terrorist attack by taking help of advance technology, because terrorists use computers, cellular and satellite telephones to make the plans, organize the activities of the group members, pass threats of bombing and communicate with one another (Broadhurst, 2006, p.6). At the same time, international organizations have realized the threat of terrorists using electronic or wire communication systems to perform criminal acts; therefore, the organizations have given importance on the cybercrime and guided the police force in the numerous articles. However, the response of international organizations have discussed below:
- Transnational Organized Crime (TOC) Convention: TOC Convention was one of the most important dimensions for the world of Information and communication technologies because it was the first international convention, which aimed to combat cybercrime, Internet fraud or terrorist activities using communication system. However, the representatives of one hundred and forty seven countries were participated convention in Italy and signed the recommendations, which also extend the provisions of the 1988 Vienna Convention in some cases. This convention defined the crime broadly and recommended 4 to 5 years sentence, and established a number of principles to broaden the concept international cooperation. However, this convention played a vital role in case of progressive development of international law and mutual assistance programs or responses between the nations. In addition, Broadhurst & Grabosky (2005) stated that TOC convention emphasis on the Asian countries because there is no potential law for the cybercrime and the response of law enforcement agencies and government is miserable in this zone comparing with international standards, for instance, there is huge gap in the KSA legislation as Saudi Arabian law based on Shari’ah law. Broadhurst & Grabosky (2005) stated Articles 5, 6, 8 and 23 of TOC Convention defined serious crime, Article 3(1) discussed ‘transnational’ crime, Article 3(2) described ‘substantial effects’ of transnational’ crime, Article 27 focused on police-to-police cooperation, Article 27(2) mentioned the cooperation between their law enforcement agencies, and Article 16 represented key step forward to incorporate existing bilateral treaty;
- The Council of Europe (CoE) Cyber-crime Convention: the organizers of this convention had mainly three goals, such as, present common definition of certain offences by harmonizing national laws, provide in general investigating power, and broaden the international cooperation. At the same time, this convention suggested that the government of the member states would incorporate the provisions of the recommendation to enforce in national law, for example, the law enforcement agencies of different countries will co-operate each other at the time of investigating crime and taking action against cyber criminals. However, Broadhurst & Grabosky (2005) stated that some provision of the recommendation has been criticized on different grounds by several associations, mainly those active in the protection of freedom of expression, but most of the provisions like computer related crime, offence connected with copyright infringement act were effective and praised to the scholars. According to the Broadhurst & Grabosky (2005), Title 3 seeks to control the application of information technology as a tool for the sexual orientation of children and acts of xenophobic nature because it corrupts the public morals particularly it negatively affect on the children’s values, therefore, they may create social disturbance in the future. However, Broadhurst & Grabosky (2005) and Wortley & Smallbone (2006) further addressed that as internet is the key way to distribute, the CoE Cyber-crime Convention enacted different regulation to control entire supply chain management of child pornography, and widen the concept of electronic invention, possession and distribution of this crime.
- The Organization for Economic and Cultural Development: Besides other international organization, OECD has been moved for the fight against internet crime and online security by balancing the activities of law enforcement agencies and international legislations;
- The International Criminal Police Organization: the purpose of Interpol is to help law enforcement organizations all over the globe, especially assists them by exchanging information, harmonizing joint operational functions of member states, and improving expertise, sharing technology, and using best practices to cover cyber crimes.
The Creation of Police Cybercrime Units
According to the Medford Police Department, the Police Cybercrime Units should responsible to train local police about Internet fraud and cybercrime investigations, to provide community-based Internet security Training to enable themselves to use ICT for their investigation as most of the state sponsored police have no educational background related with advance IT technology. HPC (2010) pointed out that the rationale behind establishment of Police Cybercrime Unit is to investigate the increasing number of cybercrimes those occur due to development of IT system; however, all modern people take the advantage of computer systems and criminals are no exception.
In addition, HPC (2011) stated that Police Cybercrime Units would use the existing resources along with new equipment and training to fight and prevent future cyber crimes, and attempts of terrorist attack, wide array of criminal activity including internet fraud and so on. However, the members of these units would be IT experts those are capable to identify criminals by using advance technology and train other staff to help combat cybercrime from global village. As Broadhurst & Grabosky (2005) stated that the cybercrime controlling system in Asian countries are not well developed, therefore, the policy makers of these countries particularly KSA should build up computer cybercrime units to deal with such crime in local area and cooperate to foreign law enforcement agencies. However, the KSA government should design Police Cybercrime Units considering the social cultural factors of each province because the people of Riyadh are more conservative and conscious with their rules and regulation whereas the people of other areas are more liberal than Riyadh.
However, the administrators should concentrate on the international standards to create such units and the legislation related with internet fraud should amend because many provisions have not consistent with global provisions and not covered the cybercrime issues due to strictly adapting shari’ah based laws. In addition, Constantin (2010) stated that Police Cybercrime Units could play vital role to save the Saudi Arabian women from the blackmailing by men; however, “Ha’ia” the religious police of KSA have more than 3500 employees protect the publication of the history or posting pictures as Islam prohibits unfair relationship and showing face. At the same time, Constantin (2010) stated that the police force of this units are more concerned with upholding religious laws, as a result, have monitored the social networking sites and other websites as men always try to earn money from women by using the photo of the women. Furthermore, the Medford Police Department have pointed out that Police Cybercrime Units should deal with following issues:
Adaptive Responses
Adaptive Response of Saudi Arabia
The changing pace of the technological advancements, coupled with the rising number of graduates in computer science and the number of programmers and web designers who specializes in C programming, C++ programming, HTML, java, and many other forms of site development means that the greater is the number of people who are able to cause augmentation in cyber crimes. This is the main reason of why, in today’s world, the number of hackers, internet frauds, and cheats are increasing causing in a consequent increase in the number of online crimes. In the pace of the late modernity, where every second developed society is able to defend all types of crimes, the fact that Saudi Arabia is a Muslim country and that it is bound to follow the Islamic Shari’ah law means that even being a rich nation, it will find obstacles towards developments.
Without an appropriate and modern law that is able to secure citizens, development it bound to halt. For example, when the new generation of Saudi Arabia tries to match up with the technological advancements with the Western world, and develop websites for different purposes, or even governments develop differ governmental site for the benefits of the ordinary folks, the hacker come out the distort the sites. Even people who use online payment systems and credit cards in the country have no security as people can easily take away all money and there will be no law to stop them or punish them.
Moreover, many problems related to privacy of women in Saudi Arabia and use of internet frauds exist that can damage the reputation of such a conservative country. In such conditions, even after causing so much of damages to the ordinary people, governmental secret data, privacy of women, as well as internet frauds, when there is no way, by which the online offenders could get sufficiently punished means that the country will have to face more and more of such offences in future. This is a great hamper for the development of the country in terms of technology as whenever it goes forward with some advancement; the online criminals distort all its efforts. In addition, the duty of the state and the government is to ensure the security of the ordinary people and safeguard them from all types of potential hazard that can cause harms to their privacy, important and secret information, and even can endanger lives.
This was the cause of why question of passing a highly modernized law arose in an effort to adaptive response of Saudi Arabia (Algarni, 2011). Enacting this law was not only the headache of the political personalities or the people who were connected with it, including the legislators, but also, the concern and the sense of relief for those hundreds of thousands of Saudi Arabians who suffered with online criminal activities for days and still were facing the trouble with their privacy in general. On the other hand, owing to the fact that the act was appropriate with the locals customs and were not harmful to the religious beliefs of the ordinary folks means that the impact of this law will be long lasting in the society as a whole (Algarni, 2011).
The reality that Saudi Arabia has ruled and directed so far by the Muslim Shari’ah based law needs to address the idea that a long enduring and highly sensitive and useful assessment is necessary to propose a summary of Shari’ah’s universal standpoint about deceitful and misleading conducts, to scrutinize whether it presents a foundation for rapid-action on online crimes. This has trailed by means of reconsidering the evaluation of the “Anti-Cyber Crime Act” that has enacted in current times to deal with online crimes in addition to many other different types of illegal happenings concerning information technology and other IT enabled services that seems to be an apprehension for Saudi Arabians in general terms.
Even than, some other legislations, which were took into account (and which carried some specific significance) in context to the question of online crimes in the Kingdom of Saudi Arabia has also inspected by the experts with a high level of care to appraise the point to which every piece of the legislations tackled important features of cyber crimes. It is important to argue that this new law, even though has established to take care of a contemporary event, it has mostly organized and formatted on the fundamental philosophies of Muslim society and the Shari’ah law because article Seven of the Basic System of Governance initiated by the emperor Fahad restated Muslim Shari’ah as the basis of the monarchy.
The Anti-Cyber Crime Act
Subjected to the Council of Ministers declaration and permitted pursuant to the Royal Decree, the Anti-Cyber Crime Act is Saudi’s foremost regulations intended to fight against rising dangers of cyber offences, and before the preface of this law, verdicts in cyber offence cases shown on the General Courts (that has regulated by Shari’ah law) was left for the judge’s forethought. In short, the Act encompasses 16 articles; Article I shows descriptions of the expressions used in the ensuing articles; whereas the purposes required by the implementation of the law has set out in Article II, which argues that it intends to generate authoritarian principles to warfare IT, PC and online offences by identifying the applicable offences and penalizing manners. This article also considers upholding IT protection, defending the rights linked to lawful use of PCs and networks, guarding social-interest, ethics, and standards, and improving and defending the country’s economy; whereas articles 3 to 13 has troubled with recognizing punitive cyber offences and stating sentences for those; conversely, the remaining articles describe the responsibilities of the organizations executing the legislation.
To argue deliberately, the Anti-Cyber Crime Act has not particularly characterized any cyber crimes; nevertheless, the extensive characterization of computer-generated offences as given in Clause VIII of Article I evidently covered computer-generated offences or cheats as any other wrongdoings, which the legislation has been formed to deal with (Royal Decree, 2007). More specifically, as written in Clause VIII of Article I, an internet based fraudulent activity can be any illegal work, which has carried out using a PC, internet or other apparatus of IT or other; in addition, by describing internet frauds in such expansive terms, the Act gives a protection from any new internet frauds, which may materialize in future. It is essential to add that the precise declaration of merely a number of infringements with reference to cyber criminal doings in the legislation may give the impression to generate several perplexities by the way, since it may entail that the legislation is not comprehensive for every single types of computer-generated crimes; the particularly declared infringements are while an individual:
- Acquire other’s belongings by himself/herself or for any third person by an IT-network, any PC, or other devices for large funds or any coupon or accepting these coupons using a deceitful method or a false-identity or impression if such activities have indicated to swindle the sufferer or damage the peace of daily lives of the Saudi communities
- Utilizes any IT-network, any PC, or any other comparable technological machines to enter illegitimately/dishonestly into bank accounts/credit cards/financial data/private accounts on social networking sites or similar private records, in order to exploit some such records to get hold of private data, finances, or cashes and exploit it for her/his own purposes with intentions of theft or other criminal activities
According to AlBosaily and Morris (2011), this leads to a flaw in the legislation and unlocks the access for explanations that may often be false; the flaw of the proposed regulation with reference to online crimes has accentuated in reassessment accomplished by KSA’s CITC to measure to what extent the matter of shams, presently, has dealt with through present rules. As stated by Algarni (2011), most importantly, it is essential to argue that the issue of spam mails has not completely taken care of in the recently propagated Anti-Cyber Crime law. There also some arguments that suggest that the Anti-Cyber Crime law, which, although, has formed by the a long period of hard work by the concerned officials, legal experts (including professionals like lawyers, solicitors, advocates, and barristers), legislators, and the political personalities, is, to some extent, too narrow to deal with some broader range of cyber crimes.
Even though there had been broad discussions, courses of actions, and hard works by all concerned officials, the narrower side of the proposed law will come into sight as it will put into practice, and after a number of different cased have handled. To illustrate this idea, CITC stated that when the law forbids some forms of substances in e-mails, it does not clearly deal with the question of unwanted mercantile mails, which is another variety of spam mail; the law thus was unsuccessful to characterize spam and mercantile ads clearly, together with the type of permission needed, and necessity for justifiable mailing. Spam-mails symbolize a main displeasure and danger to online functions, especially for the users of mailing services, such as Google mail, yahoo mail, AOL, and so on; for example, in the KSA itself, it has observed that in the above stated mailing services, spam has used for malevolent reasons comprising phishing, virus dissemination, and deception.
If it has considered that the statement provided by the Communication and Information Technology Commission (CITC) is true, than it is important to argue that a huge gap still exists that has not addressed in the Anti-Cyber Crime law, and which, if remained untreated, could pose a great threat for ordinary people. If this happens to be true in turn, then the whole effort provided by the concerns organizations, experts, and legislators will not necessarily have any impact over the cheats associated with spam mail. This would means that without sufficient means of punishments, this online cheats will continue to use their capabilities to use electronic mailing facilities and cheats people as they did previously.
According to Check Point (2011), like many other forms of online crimes, conducting cheat by means of electronic mails is another big trouble that can ruin thousands of lived by making them fools and consequently, for example, taking away all their money. This is known as phishing – distributing electronic messages to ordinary people by untruly asserting to be a recognized lawful venture in a challenge to swindle him/her to providing confidential data, which would utilize for individual thievery; these messages indicates the person to go to websites where they will repost private data (like pass words of credit-cards, social-securities, and bank-account-numbers).
As stated by Lotsofknowledge (2011), expert hackers construct carbon copies of well-known websites with the intention of swindling ordinary people into taking a log in, then subsequently, with the person’s pass word, these online criminals could log into the person’s original private account and result all forms of troubles, like theft or using the account to conduct other crimes. Although modern technological advancements has bought many conveniences, but, in some instances, online criminals would attempt to obtain unjust benefit of circumstances; for illustration, the most well-known deception engages a replica website of PayPal – with the account data of normal men or women, criminals could clear the account’s money, or perform further multifaceted frauds in disguise of his/her personality.
This shows the fact that still a vast area of the most popular forms of cyber crime has not addressed Anti-Cyber Crime Act. Therefore, many chances exists in the Muslim communities of Saudi Arabia that despite of having so highly motivations regarding ethical practices and sensible behavior, their people, in near future will have to face more of the same types of nuisance by means of phishing from either the cyber criminals in their own country or of any other developed nation. In such circumstances, it remains the matter of the big question of how, after revising, reassessing, re-evaluating, re-checking, and reviewing the Anti-Cyber Crime Act for so many times by the legal experts, professionals, and legislators from the highest level of the Kingdom of Saudi Arabia, still such a big gap remained within the law.
There are concerns that more and more criminals, from now on, try to phish online by fooling around Saudi Arabians by utilizing this major gap in law. Therefore, much of the nuisances have existence in the society that people would need to suffer from even after passing such a wonderful act. However, a proper step from the part of the Saudi Arabian government, concerned officials, and political personalities can resolve the matter once again – as they will only have to come up with some few amendments and additions in the legislation. With this new amendments and additions in the legislation (which will be including especial indication as to spam electronic mails and phishing activities), the law will further enrich for more suitable working in defending crime.
At this stage of the paper, it is important to argue that the Anti-Cyber Crime Act imposes a range of different punishments and penalties for a range of different online criminal activities; data protection, in addition, is also included in the law – the Saudi Arabian law inflicts numerous sentencing that relate to data protection and privacy, comprising the following:
- Penalty of five hundred thousand Saudi Arabian Riyal (around one hundred thirty thousand US Dollars) and/ or up to 1 year’s jail for persons who break off information, which has sent out by an information system, devoid of any permission.
- Penalty of two million Saudi Arabian Riyal (around five hundred thirty thousand US Dollars) and/ or up to 3 years’ jail for persons who illegitimately entered bank accounts or credit card data or data relating to the possession of securities of ordinary men or women of Saudi Arabia.
- Penalty of three million Saudi Arabian Riyal (around eight hundred thousand US Dollars) and/ or up to 4 years’ jail for persons who illegitimately entered computer-systems to remove, expunge, demolish, disclose, spoil, change or even reallocate private data of ordinary men or women of Saudi Arabia.
Other Legislations Controlling Online Crimes in the Saudi Arabia
The Anti-Cyber Crime Act is not the mere regulation in kingdom, which has regarded as applicable to the question of online crimes; two other types of regulations enclose essentials directing a number of features of online crimes and, consequently, could appear, together with the Anti-Cyber Crime Act, as an authoritarian scaffold for overbearing these online crimes in KSA’s Muslim communities. These two are the Anti Commercial Fraud Law and the Electronic Transactions Act; however, the degree to which each of these two regulations handles such online crimes has observed in the lower sections of this paper.
Facts Concerning the Anti Commercial Fraud Law and the Implications
As per the Anti Commercial Fraud act, each trader have to perform his/her business action or operations by means of outstanding attentiveness, keeping away from terms or contracts, which consist any sort of swindling, deceptive, or fraudulent things causing harm to the ordinary customers. This legislation provides the Ministry of Commerce (MOC) with the major liability for handling all types of customer-related commercial deceits; enactment of this legislation, i.e., the discovery and examination of infringements of the legislation and its statutes are chiefly the accountability of MOC; moreover, it assigns the MOMRA the job of observing the termination dates of foods in the market. As for the enactment of the legislation, six committees, dispersed throughout diverse areas in the Saudi Arabia, has set up; in addition to this, a nodal committee, known as the National Commission for Consumer Protection, took the escort and is accountable for directing the a range of committees, arranging and scrutinizing the implementation, and organizing customer fortification consciousness schemes.
As per the act, financial fines, closing off the firm, incarceration, and recompense could affect any person who assists, supports or frankly performs swindling, deception, hoaxing, faking or fussing customers concerning the depiction or advert of any product (that is lying about the product and misinforming or trying to ruse the Saudi Arabian customers). In such conditions, it appears that while someone is trying to handle infringements concerning the substance of the communication in deceitful and misinforming online adverts, the act would be the apposite orientation to settle on whether the substance of the communication is unlawful and accordingly summon conducts on the foundation of authorizations offered through the legislation for safeguarding customers’ interests.
Facts Concerning the Electronic Transactions Act and the Propositions
The purpose of the Electronic Transactions Act is to lay down combined authoritarian principles to rationalize utilization of online dealings and signs, and to develop poise in the reliability and strength of online dealings, signs, and accounts; it also ask to ease practice of online dealings nationally and globally in grounds like online-based administration, deals, drugs, schooling and payments. With intended courses of action, it has proposed to eradicate obstructions in utilizing online dealings or sign, whilst during the similar occasion avoiding exploitation of online dealings or signs and interrelated deceptions; moreover, provided the nature of the act, there are appropriate provisions against precise types of deceptions.
According to article twenty-nine of the legislation, for example, it has stated that safety against disguises (pretence under any other individual’s name), counterfeit of online signs or digital-certificates, on top of unlawful admission to other’s computer-systems for the intention of mistreating these official documents, has strictly prohibited in the Kingdom of Saudi Arabia. Article 30 dictates that anybody who executes any of the breaches designated above will be subject to a fine not beyond SAR 5000000 or 5 years’ jail or even both punishments; the conclusion, the article goes on to declare, may contain elimination of the hardware systems, software utilized in the breach and annulment or deferral of the service stipulation license.
Distributed Security
Distributed security is basically an approach for ensuring online security. Thus, a number of sophisticated technologies are used for realizing such pattern of security problem and alternative solutions involving different cryptographs, authentication and access control. All of those aspects are necessary to prevent online fraud in Saudi Arabia (Microsoft, 2011).
Security services: According to the projected purposes, distributed security offers the following services:
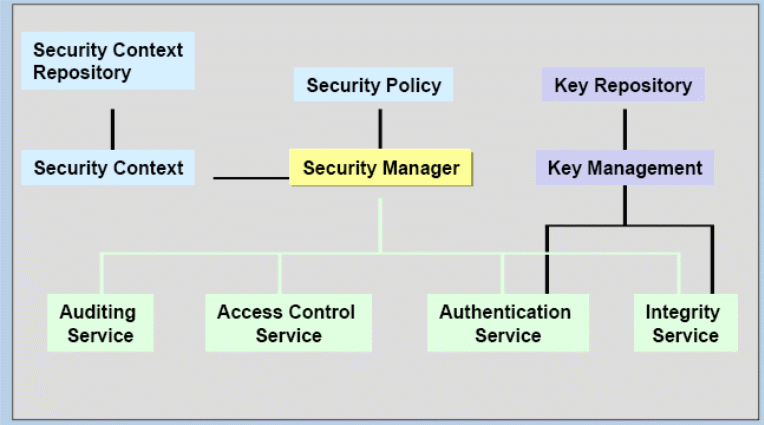
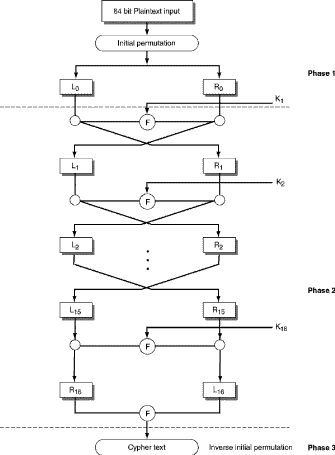
Structural development: As mentioned before, the basic structure of distributed security covers three arenas. Cryptography and digital signatures are first concerns where encryption is the most integral point of communication. Encryption is the process of encoding data in such way through which it is difficult for an eavesdropper for easy reading. Here, encryption algorithm is comparatively secure if it is not possible for systematic analysis to break. Encryption commonly takes two forms regarding public and private- key encryption. DES or Data Encryption Standard is implemented for ensuring confidentiality of the key that can be increased by key size. There are three phased of DES named as initial permutation, shifting and inverse permutation (Microsoft, 2011). The functioning flowchart of all those phases are shown below-
Security can also be magnified through the implementation of Triple DES that uses 64- bit keys. After, two common techniques are applied for digital documentation purpose. Digital signature is the one technique, which is a message digest and implements a protected 128 bits long hash module. This digest has largest benefit as the third party, like- any hacker or internet fraud would not able to know about private key as an essential tool for computing perfect value of digest. Asymmetric encryption is also called public key encryption with the functioning of both private and public key. RSA is the most common form of this kind of key that entails three stages as private and public key determination, message encryption and decryption (Ericsson, 2004). Delivering authentication is the second step of distributed environment. Authenticating or confirming user ID is the initial task here. There are three measures of doing so regarding the usage of user password, key and retina or fingerprints (Microsoft, 2011). There are also some relevant issues about which the distributed system must be concerned for preventing fraud, such as:
- Eavesdropping.
- Multiple password management.
- Reply.
- Trust etc.
Additionally, various types of certificate lists are also used for ensuring different forms of authentication as one-way, two- way and three- way authentication. Certificate distribution center is a crucial component of distributed system because if it crashes, the overall distribution may be affected. Kerberos V.5 is the most ancient authentication technology, which is used for offering a reliable third- party authentication service. In lieu of all areas inducement in the distributed process integrated by complexity in utilization of ID and passwords, Kerberos holds only one main database for preserving authenticated information which is also known as KDBM or Kerberos Database Management System (Microsoft, 2011).
Once distributed systems are formed for permitting open informational flow among each and every adjusted organism to the channel, a distributed operating module should offer access control for ensuring proper information sharing facility. Here, more reliance is posed on various hardware devices along with the accomplishment of firewall. Such firewall is used for protecting security threats and may take two basic dimensions as packet- filtering gateways and proxy services. A packet- filtering gateway induces an engineer for security with the consideration of internal and external flow of information throughout that firewall. Proxy service performs as an insider client’s service to exterior world. Two forms of proxy services can be used regarding application- level and circuit- level gateway proxy services. There are also multiple firewall architectures, such as, bastion host, filtering host and filtering subnet architecture. Bastion host is useful for mapping information among various networks where system abusing is the major problem. Filtering host uses the previous host along with proxy services where the router performs like a screen by delivering packet- filtering functions. Finally, filtering subnet is the most secured architecture than other two with one proxy- service and two packet- filtering firewalls (Microsoft, 2011).
Advanced security: Along with the traditional approaches, distributed security system can be further sophisticated through the integration of reputation, auditing and cryptography regarding the related parties, contributors or other parties. All of those modules are helpful to enable the server for delivering integrated services, which can also assist the users to become safer from attacks (Szabo, 2003). Various approaches used for this issue are discussed below-
Lamport order: In an asynchronous network, this order can be successfully used for solving the ordering problem (Szabo, 2003).
Composition of fair total order: – The previous approach may create ambiguities in some cases which can be solved by implementing this approach that functions through the ways below:
- Multiparty secure computation: It is the protocol for producing practical equipments between two or more parties. Here, any party is allowed to compute regarding its personal input and output of such computation. Each party can also keep high confidentiality in its input (Szabo, 2003).
- Threshold Cryptography: It is another version of the previous approach where only one key is used for encryption although all the parties have a common key to decrypt (Szabo, 2003).
- Natural broadcasts: Broadcasts that utilize radiation or sound from variety of sources, like- satellite, pulsars or radio towers may encounter a number of problems regarding the structure and attack. Natural broadcasts can solve those problems through the application of logical broadcast protocols. Secure time- stamping is one of the most common types of such protocols which are considered as the technique for one party accompanied by a secret document or more than one party for delivering confidential messages, for entrusting each other and third parties an indefensible time-stamp. Point- to- point communications can be the subject of malicious attacks that can be prevented through logical broadcasting. There are four distinguished characteristics of such logical network involving reliable ordering, reliability, fairness and casualty preservation (Szabo, 2003).
Byzantine- resilient replication: – This approach is widely used for delivering security and the generated services are also termed as “intrusion tolerant” since the service is able to protect attack as well as fraudulency up to T servers. Various techniques are implemented here, like- fair coin tossing and threshold cryptography. Moreover, Byzantine- resilient replicated library can also be used for applying internet services accompanied by distributed confidence in the CORBA process. It can also be used for increasing trust in data integration and calculations. This program involves blacklist updating facility which can assist authority as a user to notice unreliability. As a result, the attack become discloses and further, the client can remove it from the server (Szabo, 2003).
Implementations: – For providing a public service, a number of factors need to be considered regarding trusts as name mapping, key identification or name addressing. All of such purposes can be better meet with the implementation of replicated service. Along with property rights, some other centralized services can be re- applied with sophisticated integrity and trust throughout Byzantine approach, such as, digital cash and Domain Name System or DNS (Szabo, 2003).
Policy conformance
A large- volume and flexible validation is possible in the development of distributed policy through the integration of specific architecture and decomposition algorithm. ODESSA is one of such kinds of modern technique that has the core goal of verifying the infrastructural condition in terms of overall policy standard followed by the demonstration as data log rules. It uses an evaluation protocol throughout four components as monitoring agents, verifiers, predicate group and resilience (Ericsson, 2002).
Security- oriented rules and regulations
In distributed purpose, several security measures have been adopted by Saudi government in terms of distinguished rules and regulations for preventing online fraudulency. One such regulation is that, every internet café user must submit ID cards for recording his/ her name and ID number. Online logging into and logging out time are also traced by the café for at least six months so that it can submit this record to the authorities in response to such request. Such decision has been made since authorities have noticed that cyber cafes were not following proposed rules. Additionally, some personnel were assumed to have connections to terrorism that were caught in a cyber café of Madinah (Qusti, 2003). Thus, some common distributed security standards imposed on cyber café by Saudi authorities are as following:
- User acknowledgement about the fines and punishments for breaking up of security.
- Restriction of using internet under the age of 18 except some especial purposes.
- Liability of open places for the inability of recognizing personnel responsible for dishonoring security rules or abusing security instrument.
- Accomplishment of Islamic rules and government regulations while utilizing internet completely for positive issues.
- Utilization of Islamic Shariah breaking materials, informational exchange related materials challenging Islamic or governmental laws, usage of public security threatening materials and usage of crime supportive materials etc. are strictly prohibited.
According to many social science researchers, Saudi legal authorities should change its attitude of enforcement of law from reaction and penalty to more preventive approaches by strengthening community policing in the internet world. Initially, development of cybercrime protective regulations should be induced with individuals and corporations. As a result, both parties would become conscious enough to identify the potential threats and then install essential tools and equipments to protect threat, lessen their belief on unknown e- mail and the like. However, all the time, it would not possible to suggest the specific tools by the authority while it is necessary for all kinds of users to invert the common protective and sanction technique. By this way, a single person’s desire of law obligation becomes his/ her liability to escape from being a sufferer (Science Daily, 2009).
Potential challenges
There are several problems in designing and implementing online distributed security (Ericsson, 2004), such as:
- Adjustment of multiple phases;
- Accomplishment of diversified environment with numerous software and hardware.
- Adjustment of multiple protective solutions for ensuring security against distinguished malfunctions;
- Potential errors and inconsistency in managing systems especially by manual handling program.
Preventative Policing
Sorell (2008) has spotted out preventive policing as an activity conducted by police forces with an aim to recognize and put off an explicit offence (comprising cyber offences) or a form of misdemeanor; “preventive policing” may also comprise “exceptional investigation procedures”, together with furtive surveillance; it is important to argue that such courses of action bears palpable ethical dilemmas. If preventive policing is any act performed by law enforcement agencies with a goal to find out and avert some sorts of transgressions; then generally interpreted, it should not bear particular ethical risks; for instance, municipal police association with societal bodies and NGOs accountable for opposing fundamentalism possess an apparent job in stopping violence in societies known to restrain militia.
Collaboration with neighborhood in order to fabricate trust may be the basis for police receiving dependable information about explicit threats; it may also afford opportunities for societal organizations to sensitize police to heavy-handedness in their operations or biased manners; another instance of straightforward preventive policing is a strategy of tackling small crime forcefully within a society recognized as containing radicals. This strategy demonstrates that the law enforcement agencies has attentions in offences against parts of a collaborative society, and not simply in the recognition of criminals inside it; it can also aid the deterrence of more grave offences; however, neither strategy need to engross interruption, disregard for societal practices, or shams; of course, it carries what is well-known as diplomatic-risks.
Police can not be legislatures of the country who are expected to win confidence of societies holding radicals, and they may articulate and perform things that cause felony, but the dangers that face any interaction between groups in tension with one another exists during cooperation period; the ethical risks of not going in for societal association may be significantly worse. On the other hand, some ethical dilemmas of the notion of preventive policing may augment invasive actions, where the rate of frauds might increase, and the argument for aiming folks for enquiries appears to be laying on unfairness, or even, in another way, on typecasts which may construct excessively immense sample of inhabitants as probable “criminals” for comparatively unusual felony. Conversely, it is notable that “special investigation techniques” are amid the transporters of hazards on this phase, but a new and dissimilar basis of danger is the utilization of inadequate evidence based forensic tests, particularly profiling; the paper would focus on these matter on the later segments; but next, it would continue with special investigation techniques.
Special Investigation Techniques in Context of Saudi Arabia
So far, special investigation techniques has utilized in the jurisdictions of the EU member countries which comprised surreptitious bugging, wire tapping, electronic message interruption, individual and webcam observation of prospective criminals in common areas, and supervision in tavern quarters and confidential habitations. What fastens these ideas jointly is that they have performed devoid of the awareness of the folks investigated, and occasionally engage sham; the exercise of these methods characteristically necessitates permission by a top ranked police officer, an arbitrator, or a chamber of judicial benches, or more rarely a government minister.
The further invasive the method, the superior the lawful impediments that classically rise in the way of the law enforcement forces utilizing it, and the further is number of sovereign bureaucrats who will have to give the approval; usually, the collection of biometric data, whether explicitly or in secret, has regarded as predominantly interfering, because it is uniquely identifiable. As argued by Khan (2010), Saudi Arabia has recently created and initiated a latest appraisal to fight crimes, which has currently reassured by the Kingdom’s high-level officers from the Bureau of Investigation and Prosecution in Riyadh; Mohsen Al Munif (a BIP-analyst), suggested that the nation is undergoing the procedure of forming scientific-research over offences throughout KSA to enhance legal system. Concerning the formation of the special investigation techniques, Al Munif argued that the country is continuing to encourage countering the crimes through the initiation of a range of diverse methods encompassing the diffusion of sacred discussion on violence (divine proclamations) through TV Medias, Print Medias, and radio services together with prayer zones.
An Acceptable Structure of Special Investigation Method
Sorell (2008) has spotted out that the cabinets of different minister in a wide range of countries all across the world was able to come up with some groundbreaking success in terms of efficiently delineating an acceptable and lawful scaffold for exercising of the special investigation techniques stated above in this paper. Following this, the Kingdom Saudi Arabia has currently received many suggestions from the part of the intellectuals in the country to construct the special investigation techniques in such a way that increases and enhances the ability and competency of the country in crime-control.
It is arguable that although the Saudi Arabian government has adopted the idea of special investigation techniques in its legal system for the assistance of the policing segment, but, in fact, a matter of controversy is present of whether the framework of the entire system is of high standards where the interests of a proper judicial system will be uphold. The “common standards” of this scaffold presume (but do not state), the non-interventionist idea to the design of administration that is in the constitution of nations together with the organizations of co-related bodies; following the citation of the common standards and the boundaries on preventative policing copied from them, the conversation will generate clear the thought behind the non-interventionist idea.
Ethical Dilemmas of Preventive Policing In Counter Terrorism
The counter terrorism strategy has formulated in 2005; out of its 4 filaments (stop, chase, defend and retort) merely two possess an undeviating association with law enforcement (and policing); possibly astonishingly, the “stop” filament is not principally a policing based responsibility. This has troubled with tackling the grounds of fundamentalism amid the public and inhabitants of the jurisdictions of major countries, and those related to its functioning are probable to be NGOs, together with applicable social-groups; the “retort” filament would deal with repercussions of catastrophes, and will logically put service into organizations connected to mending infrastructure, or food-deliveries, and health-services. The “chase” and “defend” filaments have concerns with policing; the “defend” section has designed mostly to deal with safeguarding national boundaries against the entrance of criminals, and IT based infrastructural amenities from substantial and cyber attack; on the other hand, “chase” is the filament, which comes after pertaining itself with the detention and trial of those accountable for cyber attacks.
Administrative rationalizations of this filament, nevertheless, does not openly differentiate amid examinations that aim terror-suspects prior to a offence has conducted, and examinations intended at recognizing, detaining and condemning those guilty for terror-attacks post-facto; however, both in counter terrorism and in examination of prearranged offence, a use for police operations that discovers and tests the intentions of suspects are present. Such maneuvers more often engross the police forces and other law enforcement agencies in top-secret observations, and usually in undisclosed permeation of illicit gang members with a vision to identify plots for importation of illegal-drugs or traffic in immigrants; maneuvers alongside these lines frequently terminate in arrests before an attack, or in interferences that interrupt the completion of a crime.
Apart from KSA, even in modern countries like the UK, ethical dilemmas are present in preventative policing; Emily (2009) has identified a number of ethical dilemmas; e.g., in UK, from 2007, while two terror-attacks had fruitfully disillusioned, the number of Black people clogged under this power has raised by 322%, and by Asians 277% whilst white people merely by 185%. Such practices, by no means, will fall under the notion of “just and impartial judicial system and preventative policing framework”, rather, the practice put forward by the police forces of the UK, seems to be completely racist, and in favor of the UK citizens with an adverse threat even over ordinary foreigners from African or Asian origin.
From ‘grand theory’ to the policing of internet fraud in Saudi Arabia
Grand Theories of Criminology
Akers and Sellers (2004) mentioned that the grand theories of criminology are the basic tools that that contribute to comprehend and give explanation the real life assist to working with criminal justice system. The theories put forward the readers to learning the things are right and wrong, and the application of good or bad by providing clarification of crime both in micro and macro level of the society. The grand theories of criminology also facilitates to analyzing human behavior, their criminal mentality to commence crime violating social justice and performing delinquent acts, while the theory aimed to social application and policy suggestion for a better human civilization.
Akers and Sellers (2004) also added that the philosophers of enlightenment era like Cesare Beccaria in 1761 had provided the most influential classical theory of criminology, which argued that the crime occurs while the benefits prevail over the costs of happening crime and individuals perform such action to uphold self-interest or personal benefits for not to having any effectual punishments. Beccaria also pointed that the crime is a personal choice if self-motivation individuals by violating the law and order of the society where they belongs while social contract theory of Rousseau has enacted. Cullen and Agnew (2003) pointed out that the Stafford and Warr introduced the Rational Choice Deterrence theory that argued crime as a selection of an individual prejudiced by the costs and benefits judging with individual’s rationality that permits due to serious punishment for comparatively less offence. The offender is well known about the cost of crime and further expected to be deterred if its punishments are certain and immediate that may argue to commence lesser offence or prevent serious injury.
Akers and Sellers (2004) explained that the Positivism theory or the biological theory of crimes stated that it caused due to biological deficiencies among the individuals while afterwards researchers put emphasis on psychological and sociological influential factors as a driving force of criminal offence. This theory permits that crimes are occurred due to genetically determined factors those are inborn defects and irregularity of an individual where the person has no influence to motivate, such theory of criminology may inspire social unrest and pointed as a defense for the criminal lawyers of modern era.
Cullen and Agnew (2003) argued that the Marxist theory has give details of both law and criminal justice along with focusing ahead to the splitting up involving the capitalist class as governing class and working class as suppresses class are pole apart due to irrevocable conflicts. The theory pointed out the society has been ruling by the bourgeois and the working class is the suppressed segment of the society where any demand to live worthily by the workers has considered as a crime by the ruling class. The capitalists control over the state power they are willing to make the working class powerless and the working class has been struggling to establish proletariats dictatorship, which would lead to the classless society and ensure proper justice and human rights.
Akers and Sellers (2004) argued that under the male controlled society the knowledge and wisdom supposed to be strong-minded with the understanding trained through the individual’s gender, ethic group, race, colour, and class, as the criminology under enemy control by masculine gender, the area has defectively organized by male’s viewpoints without integration of females. The activists of feminism disapprove of the male dominated theories of crime as developed to explain only male crime. The theory of feminism on criminology also argued that the males as a ruling class are enjoyed a great deal of opportunities to involve with numerous crime while they impose liability of crime females while the males have no justified answers to the discretionary of mail prevailed traditional theories.
Internet Fraud and Saudi Legislation
Algarni (2011) conducted a study in Saudi Arabia to identify to what extend the existing the Shari’ah based Islamic law of the kingdom would capable to protect cyber crime. Analyzing the Anti-Cyber Crime Law- 2007 and Electronic Transactions Law- 2007, he identified that the legislation of KSA (Kingdom of Saudi Arabia) on Internet fraud is an effort to materialize the legal system with international standards without any changing basic principles of Islamic radicalism but tried to enabling the law enforcement agencies and policing to encounter with the new forms of criminality and cyber-crime. The mentioned legislations identified the criminal offences all those are internationally recognized cyber crime such as violating data protection standards, pornography and property frauds, moreover adjoined Shari’ah law even women rights, freedom of speech and democracy all also criminal offence or cyber crime in Saudi Arabia. Thus, the Saudi Police has to spying on all those web contents those are concerned with the Anti-Cyber Crime Law- 2007 and Electronic Transactions Law- 2007.
Broadhurst (2006) pointed out that the government of Saudi Arabia has been keeping highest efforts to establish control over the news media and the internet contents those inspire democracy, women rights and free thinking including the contents against the Royal family, while police has to engage their supervisory efforts to protecting these progressive contents rather than real cyber crimes. In KSA in the name of cyber-crime, the government is imposing censorship on huge number of websites arguing them ‘against Shari’ah law’ but those are not really against the core values of Islam. However, the Saudi police have to well train to filtering and blocking progressive websites but the Medias under government controlled always rely on positive speeches to promotion of e-governance. While the core values of the internet is to introducing open access to the information, Saudi people have to go under censorship and highest care for not to caught by the police for cyber-crime even when they are gathering and sharing knowledge on the internet.
Policing Of Internet Fraud
DDGIS (2011) pointed out that the police forces of Saudi Arabia are well defined with latest technological development to ensure in homeland security of the kingdom by adopting electronic policing systems by using the Internet technology, GIS Systems, mobile system, and digital recording of audio and video with the close cooperation with British and US technology partners.
MapXL Inc (2011) explored that the Police of Saudi Arabia was established under the reign of first king Abulaziz and is liable to uphold peace and social order protecting all sorts of law violation within the kingdom, though it was not actually a well thought-out law enforcement agency at the opening. Along with the police, the Sheikhs of the ancestral ethic groups are also responsible to safeguarding the law and order situation, thus Saudi police closely work jointly with the tribal chiefs.
During sixties, there were significant changes to transform the police force in a standard and modern form by providing huge power and arms, Saudi police has empowered to sanction punishment even for civil law maters without going to the court. At the same time, the Saudi police have been treated as public security force, but it is authorized to call and deploy military anywhere as they needed. There are several wings of police in Saudi Arabia and each wing has its director general but still there is no official internet policing, though all wings of Saudi Police are well equipped with internet and modern technology to spying internet contents of the websites hosted in the kingdom. The Saudi police are highly capable to encounter with cyber crime in the kingdom and to stand against people to safeguarding the royal family’s anarchy.
Benson (2010) mentioned that the Brazilian representatives in the United Nations along with the support of China and Saudi Arabia proposed to establish Internet Policing globally to manage and administer the web contents those are harmful for the communities in the state power. To some extends UN (United Nations) officials are convinced to this proposal, but it has raised serious debates as there is no reasonable explanation to protecting the freedom of speech that the Internet technology contributed. The global civil society has demonstrating their protest for such dangerous proposal to protecting people’s voice and it may give birth of serious conflict among the people and the government of the democratic countries while there is no justification to engage any global governing body or policing to make conform with internet content. There is huge evidence of violating human rights by the Saudi police, BBC News (2011) reported that Saudi police has open faired upon the people while they were protesting against government and demanding democracy, for such notorious role, government increased 15% salary of police.
To encounter with the cyber-crime, the Saudi Act Anti-Cyber Crime Law- 2007 and Electronic Transactions Law- 2007 needed to be free fair and impartially address the on going cyber-crimes learning from the grass toot level and sharing ideas with development partners rather than safeguarding undemocratic monarchy. The Saudi police needed to learn the nature of internet frauds those are occurring in the kingdom like credit card fraud, signature verification fraud, and mail and wire fraud, financial institution frauds and addressing such issues would be real encounter with the cyber crime.
Overview of contemporary Saudi Arabia
In Saudi Arabian sites, which are related to the opposition political groups are filtered, some websites related to the human rights issues, and also religious writings or content, which appear to be offensive to Muslims. Pornographic and gay sites are strictly prohibited and in some cases, extremist bloggers have been arrested, and blogs and sites, which are contrary to the public opinion and / or against the religious views of the country operated by online activists, have been blocked.
Saudi Arabia is the place where the Holy Prophet Muhammad was born and from this place began the rise of Islam; moreover, in this place, the Saudis practice Islam very strictly and the people are very religious as well (BBC, 2008). Many people who try to bring about a change and reform towards modernization, but which might interfere with the conventional Islamic practices even risk being jailed; additionally, there are also no political parties as well as democracy is not the medium of selecting the leader. The authorities also monitor journalism and the journalists must filter their articles for not being dismissed or subject to government scrutiny. Moreover, the programs in the media and the television channels are also highly regulated and private television and radio stations are not allowed in the country.
Use of internet has gained popularity and blogging has become a means of communication (BBC, 2008) – there are about 2000 bloggers and almost half of them are women; the government tried to ban blogging, but it was not possible for long, and after some days, the ban was lifted with only sections of the blogging website being blocked.
Some activists also attempted to protest against these restrictions in an online campaign to support human rights in 2008; this was highly publicized and it was also broadcasted by the international media, such as CNN, Washington Post, and France.
The state-run Saudi Telecom Company (STC) from 1998 has provided telecommunication in Saudi Arabia. The telecom sector continued to grow with high revenues. However, the broadband penetration rate was much lower which was about one percent. Nonetheless, as advanced ICT projects are introduced this will gradually change. These projects include STC’s launch of a home fiber- optic service providing fast Internet speed reaching 100MB per second for its clients in the Kingdom.
As far as the Internet is concerned, it is considered the most comprehensive and largest source of information in the world. It consists of millions of smaller computer networks such as universities, research centers, private companies, governments, and military agencies. As a result of the expansion in the geographical area and increase in the number of people who use this new technology, “internet Cafés” started to spread all over the world. Internet cafés are originally defined as the places where one can have some coffees, drinks, and snacks while hooking up with the internet. These cafés were established to meet the needs of those who have neither regular subscription nor access to the internet through their business or home. They aimed to assist people to spend their spare time in developing their knowledge about computing in general and accessing the information on the superhighway.
Internet service in Saudi Arabia (SA) was introduced on 19 December 1998. In the beginning of the internet, service in KSA the service seemed to lag behind the needs of its users. The internet services in KSA was not satisfactory to the internet cafés users, due to the bad connection to the net and due to the humble machines that been used in those cafés. However, since then up until now, the internet service has been improved and gradually the users have become more satisfied in 2004. This is particularly so with respect to connection speed to the internet. Several steps have been taken to improve the internet services bandwidths and infrastructures at the beginning of its introduction to KSA. This improvement was caused in part by the introduction of new ways to connect to the net using a DSL technique. This technique made the speed of the connection to the internet become very high.
As a concern of fact, the Internet has become a popular medium for free mixing between the people of the society, which is not possible openly because there are many restraints on the interactions of males and females. Moreover, it has been seen that women also dominate the internet. Some Saudis say that by means of the internet many people has received a chance to act in a very conservative style publicly while involving in much more liberal behavior online.
The spread of internet cafés in SA is also growing. The users in the internet cafés are usually younger, singles, and students. The ratio of internet cafés users, especially in intermediate and secondary school level have increased. In addition, the usage of internet applications such as email, chat and so on has become ideal. For instance, the usage ratio of email has increased while the usage of chatting has been decreased. In addition, that the quality of the machines in the internet cafés has been increased.
The government’s Internet Services Unit (ISU), which is a department of the King Abdulaziz City for Science & Technology (KACST), has been in charge of supervising Internet services in Saudi Arabia and for continuing government censorship. The government of Saudi Arabia explicitly conducts all censorship of the use of Internet, which is clarified on a section of the ISU Web site. Accordingly, the government filters all kinds of websites related to pornography and some other sites are also made inaccessible to the citizens, which have been requested by the government security bodies. The censors depend on people who make requests to the block sites.
Recently in 2008, the government initiated new law regarding the use of technology. These laws include penalties of ten years in prison and a fine for Web site operators that advocate or support terrorism; three years and fine for financial v fine for those guilty of distributing pornography or other materials that violate public law, religious values, and social standards of the kingdom. Accomplices of the guilty parties and even those who are proven to have only intended to engage in unlawful IT acts can receive up to half of maximum punishments. Suppliers and distributors of the equipment for fixing Internet may also be held liable under the new law, including mangers of internet cafes whose provisions are used to send content that violates the morals of the country.
The new law has been applied in political as well as non-political cases. For instance, a man was found guilty of hacking a woman’s email account and he stole her photos, then the man proposed her and asked her to have an affair with him and if he declined, he threatened her to post the photos online. When this was found by the state, the court fined the young man 50,000 Saudi Riyal (approximately USD 13,000) and sentenced him to 22 months in jail and 200 lashes. In another scenario, the Saudi authorities refused to allow the residence permit of an Egyptian person who stayed in Saudi Arabia for many years only because he wrote critically about the Egyptian regime in Internet articles and newspapers. The Saudi authorities arrested another blogger because he wrote about political prisoners in Saudi Arabia and he was released after he was imprisoned for four months.
On the other hand, the Saudi Arabia’s Human Rights Council also protested against the blocking of websites of Arab and international human rights organizations. The chair of the society mentioned that they know about the blocking of Web sites of Human Rights Watch, Reporters without Borders and the Arabic Network for Human Rights Information inside Saudi Arabia and also said that blocking these sites amounts to deprive Saudi Arabia of its rights as a member of the UN Human Rights Council.
In another situation in May 2009, some Saudi women journalists criticized a publication of an online newspaper of the country, Kul Al-Watan. The article stated that the character of the Saudi women largely deteriorated and that the women journalists depended on illegal affairs with newspaper bosses for their promotion. The women journalists accused the writer and the report for providing false information and asserted that the writer was taking advantage of the fact that online publications were not filtered in the country. After some days later, the Minister of Culture and Information said Saudi Arabia intends to enact laws, regulation, and legislation for newspapers and Internet Web sites. Under this regulation, the Saudi based Web sites will require official licenses from the government and the Minister stated that this law was enacted to prevent offensive articles in the newspapers and the Web sites. In Saudi Arabia, usage of internet even in the cyber cafes is strictly controlled. Recently, all internet cafes have been instructed to fix hidden cameras to catch those who continue immoral practices. The police said that some male and female youngsters become involved in immoral activities so they wanted to put an end to these practices online.
Finally, it is apparent that KSA publicly recognizes filtering of immoral substances and religiously sensitive material, but authorities also censor some political sites, which are explicitly against prevalent views of the country, and some sites, which are focused on human rights issues, because those human rights laws also are deemed to be against their strict interpretation of Sunni Islamic Laws. In addition, the state has initiated new surveillance measures at Internet cafés and has declared policies to start a system under which local sites will need to register with the authorities. The Saudis in many cases have tried to online activism, but the government have arrested many such online writers and banned their articles. A native human rights group has shown interest in challenging the government for filtering the sites related to human rights issues. On an overall, censorship of the internet in Saudi Arabia is used to prevent the widespread of immorality through the internet and in some cases to suppress opposition of the activist and retain an Islamic environment.
The Saudi Policing System
The Saudi policing system is quite complex and several forces are in place to keep its law and order into compliance with the Islamic Shari’ah. It is important to state that although, in recent times, the Saudi Arabian government is dealing with a few number cases where policing system in terms of cyber crimes has concerned, but in practice, the actions taken by the government to create online policing system is not sufficient to deal with wide-ranging cyber crimes. The government officials of the country seems more focused and concerned about some other forms of policing rather than online policing – which are known as the mutawas. However, at this state, the paper shall consider the newly adopted online policing system of the country, which although is not “comprehensive”, but quite realistic for internet shams.
According to the DDIT (2011), Developed Dimension for Information Technology
Ltd (DDIT) has finished the 1st large-scale operation of electronic-based policing systems in the KSA for the nation’s exceptional law-forces for freeway watch, which comprises transportable digital-recording of both audio/video (DVR) together with License Plate Recognition (LPR) reading both old/new KSA license-plates in both Arabic/English. Sheikh Al-Saedan (CEO), suggested that this scheme came due to 2 years progressing improvements and tests with numerous policing-organizations to guarantee that this was completely Arabic-compatible for users; the CEO also argued that this scheme was a triumph for KSA, which has led by awesome R&D to make this happen in the Saudi realm, whilst advantaging the country’s safety.
Mr. Imad (MD) stated that the scheme has concluded throughout the country in three points, originally in Riyadh-based section, in Western-Province, and ultimately in Eastern-Province; moreover, DDIT fitted more than hundred systems; however, now, its key precedence changed to persist with enhancing the freeway observation officials with the intention of increasing their abilities in this significant segment of the country. It is notable that such a modernized policing system will assist the kingdom to step toward a more enhanced technological advancement in terms of prevention of online crimes.
Being a conventional and conservative country, the Kingdom of Saudi Arabia has always been more conscious with the preservation of its religious values and principal for prevent all sorts of ill behaviors in the country by means of a Shari’ah based regulation. Whilst very small section of its policing system deals with cyber crimes, on the other hand a major part has concerns about social welfare and offence prevention.
Mapsofworld.com (2009) stated that the Saudi Arabian police are accountable for the preservation of peace and order throughout the country; the policing organizations in KSA has created under the decree of the 1st king, Abul Aziz but has not in actual fact an well-organized organization as it is on these days. In accumulation to the police force, the Shaykhs of the ethnic assemblies also shared the liability for the preservation of law and order; the King of Saudi Arabia approved this power for them – they even had the authority to rebuke criminal (who violate Islamic regulation) of the civil law.
The police force of Saudi Arabia has known as the Public Security Forces, and this force can look for help from the military forces in times they need; at about the commencement of the 1960s, major changes has made to modify the police forces – the steps integrated supplying the police man with walkie-talkie communication equipments as well as latest vans. Rising number of tribal people has employed in the Saudi Arabian police force and the forces has allocated all over the state, this policing people in the country has separated into 2 different allotments – which is the usual police safekeeping force and the other one is the exploratory police team. The next is accountable for management of examinations of illegal cases and deeds under the directorate of examinations; in fact, they have also known as the clandestine police team.
Another form of policing in KSA involves the mutawas, Alrabaa (2011) argues that sacred law enforcement teams in Saudi, who possess responsibilities to make sure that stringent devotion to conventional systems or behavior (in light of Al Koran or Islamic Shari’ah) has shown by all the citizens of the country; whereas criminals (including foreigners) will be arrested without any warrants. Although, such police forces interrelates very deeply to the religious values, principles, and morals of the country, and in many instances, preserves the interest of the society, whilst, the society, in turn, gain pleasure and contentment for the preservation of Islam by the mutawas, in a large number of circumstances, the issue of whether their action are “holy” remain questionable. Even though to many Saudi Arabian civilians, mutawas are by themselves religious devout, but in fact, behind the veil of their “holiness”, lies the secret evils or the modern day criminals.
The people, who are there to prevent crimes, are criminals by themselves. Alrabaa (2011) suggested many cases proving this, where a 28-year old hotel security-guard was killed for drinking beer; more horrifying is the story of Sina, the 25-year old Mongolian girl, who was tortured, detained, and brutally raped for not covering her face; moreover, Ahmed, a Bangladeshi private car driver was killed by not allowing to take diabetics medicine. His “crime” was that he was driving a car, which carried a woman, who belonged to the family that employed him; conversely, Marcus, a German, was arrested because he had a cross around his neck – the man has been in prison for three years until now. All this indicates the secret behind the “religious fellows” of the KSA.
Reference List
Ajala, E. B. (2007) Cybercafes, Cybercrime Detection and Prevention. Emerald Group Publishing Limited, 0741-9058.
Akers, R. L. & Sellers, C. S. (2004) Criminological Theory: Introduction, Evaluation, and Application. 4th ed. Los Angeles; Roxbury Publishing.
AlBosaily, A. & Morris, D. R. (2011) Data Protection Update 5 – Data Protection in the Kingdom of Saudi Arabia. Web.
Algarni, A. F. (2011) Is a Shari’ah-based Law Compatible with Cybercrime? An Inquiry into the Saudi Regulations on Internet Fraud. Journal of Law, Politics and Societies, 5(2).
Alrabaa, S. (2011) How the Mutawas (Morality Police) Keep the Saudi Society Clean from Vice. Web.
Anon (2011) Review of Fundamentals I: What Is Correctional Authority. Web.
BBC (2008) Country profile: Saudi Arabia. Web.
BBC News (2011) Saudi Arabia police open fire at protest in Qatif. Web.
Benson, J. (2010) UN considers establishing global internet police force to regulate the web. Web.
Broadhurst, R. (2006) Developments in the Global Law Enforcement of Cybercrime. Policing: An International Journal of Police Strategies and Management, 29 (2): 408-433.
Broadhurst, R. & Grabosky, P. (2005) Cyber-crime: the challenge in Asia. 2nd ed. Hong Kong University Press.
Cashell, B. Jackson, W. & Jickling, M. (2004) The Economic Impact of Cyber-Attacks. Web.
Check Point (2011) Phishing: Dangers of Internet Identity Theft. Web.
Collier, P. A. & Spaul, B. J. (1992) Problems in Policing Computer Crime. Policing and Society, 2(1). Web.
Constantin, L. (2010) New Saudi Cyber Crime Unit to Crack Down on Blackmail of Women. Web.
Cullen, F. T. and Agnew, R. (2003) Criminological Theory: Past to Present. 2nd ed. Los Angeles: Roxbury Publishing Company.
DDGIS (2011) New Technological Revolution in Homeland Security in Kingdom of Saudi Arabia. Web.
DDIT (2011) New Technological Revolution in Homeland Security in Kingdom of Saudi Arabia. Web.
Emily, G. (2009) The Problem with Preventative Policing. Web.
Ericsson (2002) Distributed Security Infrastructure.Web.
Ericsson. (2004) A New Distributed Security Model for Linux Clusters. Web.
Garland, D. (1999) The commonplace and the catastrophic: Interpretations of crime in late modernity. Theoretical Criminology, 3(3). Web.
Garland, D. (2011) Crime Control and Social Order. Web.
Gelsthorpe, L. (2004) Back to Basics in Crime Control: Weaving in Women. Critical Review of International Social and Political Philosophy, 7(2). Web.
HPC (2010) Police Cyber Crimes Unit (CCU). Web.
HPC (2011) Understanding Cybercrime: A Guide for Developing Countries. Web.
Khan, G. A. (2010) New measures to combat terrorism. Web.
Lotsofknowledge (2011) The Dangers of Phishing. Web.
Mapsofworld.com (2009) Saudi Arabia Police. Web.
MapXL Inc. (2011) Saudi Arabia Police.Web.
Microsoft (2011) Distributed Security. Web.
MPD (2011) Computer Crime Unit. Web.
Qusti. R. (2003) Internet Regulations Tightened. Web.
Royal Decree (2007) Anti-Cyber Crime Law. Web.
Science Daily (2009) Distributed Security: A New Sharing Approach to Online Security. Web.
Sorell, T. (2008) Deliverable 25. Moral Risks of Preventive Policing in Counter-Terrorism. Web.
Stanley P.M. (1986) Computer Crime Investigation and Investigators. Computers and Security, 5 (1).
Szabo. N. (2003) Advances in Distributed Security. Web.
Wall, D. (2005) Digital Realism and the Governance of Spam as Cybercrime. Web.
Wortley, R. & Smallbone, S. (2006) Child Pornography on the Internet. Web.