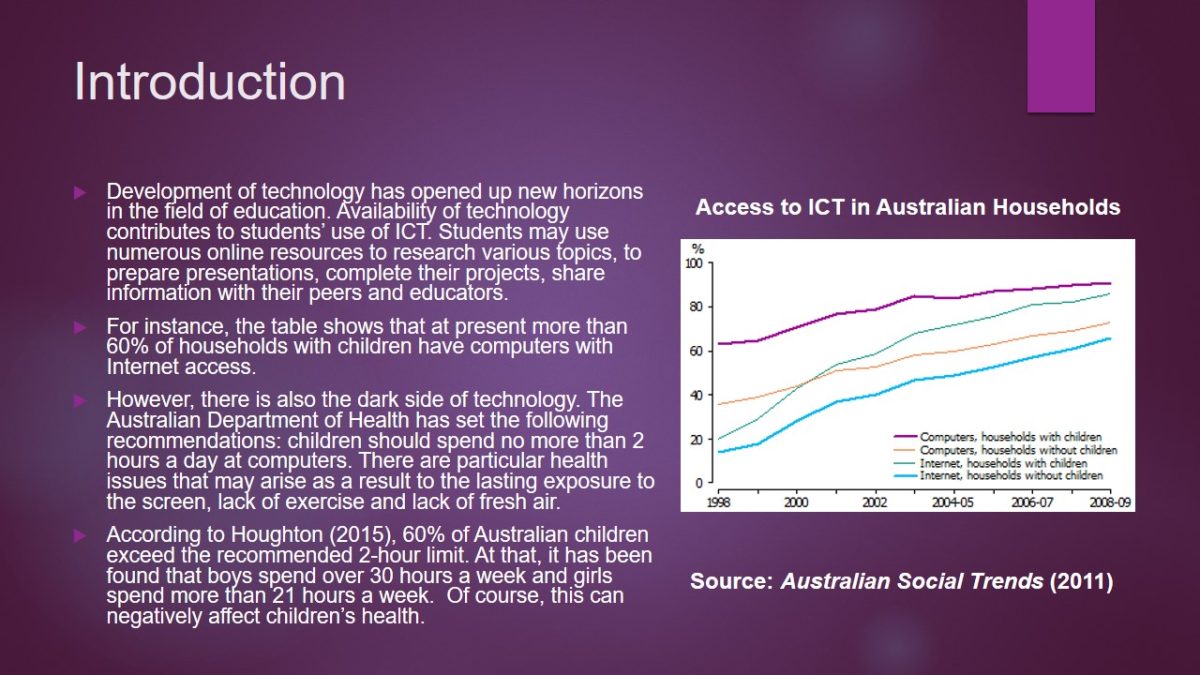
Introduction
Development of technology has opened up new horizons in the field of education. Availability of technology contributes to students’ use of ICT. Students may use numerous online resources to research various topics, to prepare presentations, complete their projects, share information with their peers and educators.
For instance, the table shows that at present more than 60% of households with children have computers with Internet access.
However, there is also the dark side of technology. The Australian Department of Health has set the following recommendations: children should spend no more than 2 hours a day at computers. There are particular health issues that may arise as a result to the lasting exposure to the screen, lack of exercise and lack of fresh air.
According to Houghton (2015), 60% of Australian children exceed the recommended 2-hour limit. At that, it has been found that boys spend over 30 hours a week and girls spend more than 21 hours a week. Of course, this can negatively affect children’s health.
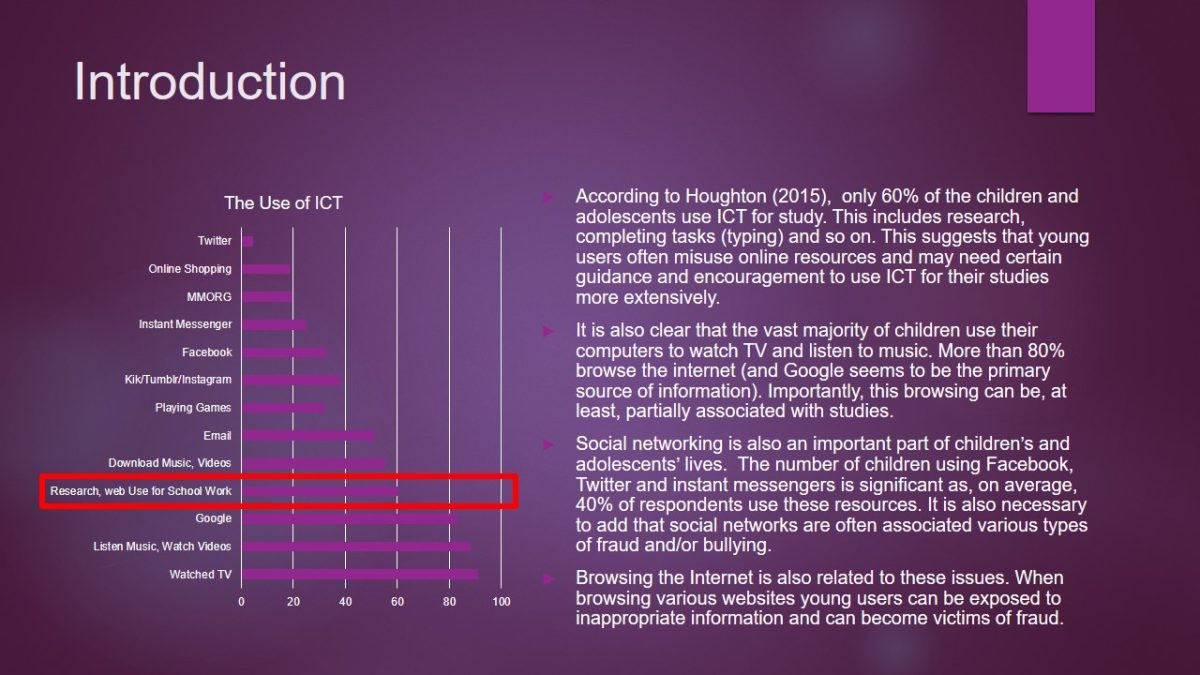
According to Houghton (2015), only 60% of the children and adolescents use ICT for study. This includes research, completing tasks (typing) and so on. This suggests that young users often misuse online resources and may need certain guidance and encouragement to use ICT for their studies more extensively.
It is also clear that the vast majority of children use their computers to watch TV and listen to music. More than 80% browse the internet (and Google seems to be the primary source of information). Importantly, this browsing can be, at least, partially associated with studies.
Social networking is also an important part of children’s and adolescents’ lives. The number of children using Facebook, Twitter and instant messengers is significant as, on average, 40% of respondents use these resources. It is also necessary to add that social networks are often associated various types of fraud and/or bullying.
Browsing the Internet is also related to these issues. When browsing various websites young users can be exposed to inappropriate information and can become victims of fraud.
Existing Threats
There are numerous undesirable outcomes of the use of ICT (Protecting personal information, 2015):
- Spam:
- It can be any type of information (usually advertisements). However, it can also be associated with various scams as scammers often try to find their victims sending spam messages to their emails. Apart from being a hazard, spam can be quite annoying.
- Cookies:
- The so-called cookies are certain tools that enable a website to save personal settings. Thus, personal information can be extracted with the help of cookies. This information can be used for fraud and other unlawful activities.
- Fraud:
- Fraud is associated with stealing information, money or other resources with the use of personal information.
- Identity theft:
- Identity theft is one of the types of fraud. It presupposes using personal information (and pretending to be someone else) to get some benefits (money, information and so on).
- Scams:
- Scams are often sent via email, or SMS and MMS. These include fake lotteries, phishing (messages that are claimed to be sent from reputable institutions asking some confirmations of or requests to reenter passwords, IDs and so on). The so-called Nigerian 419 scam when there is an email where a person offers the receiver to pay some (quite considerable) amount of money (for instance, to access a fortune) and in return the receive is promised to be paid some part of it.
Cyberbullying
Cyberbullying is another serious threat. Abrahams and Johnson (2015) report that about 21% of Australians aged between 8 and 14 are victims of cyberbullying.
Victims of cyberbullying feel depressed, scared, anxious. Many victims commit suicide, as they cannot find the way out. Bullies can also feel depressed or uneasy about their deeds. Both bullies and their victims may need psychological assistance.

Existing Solutions
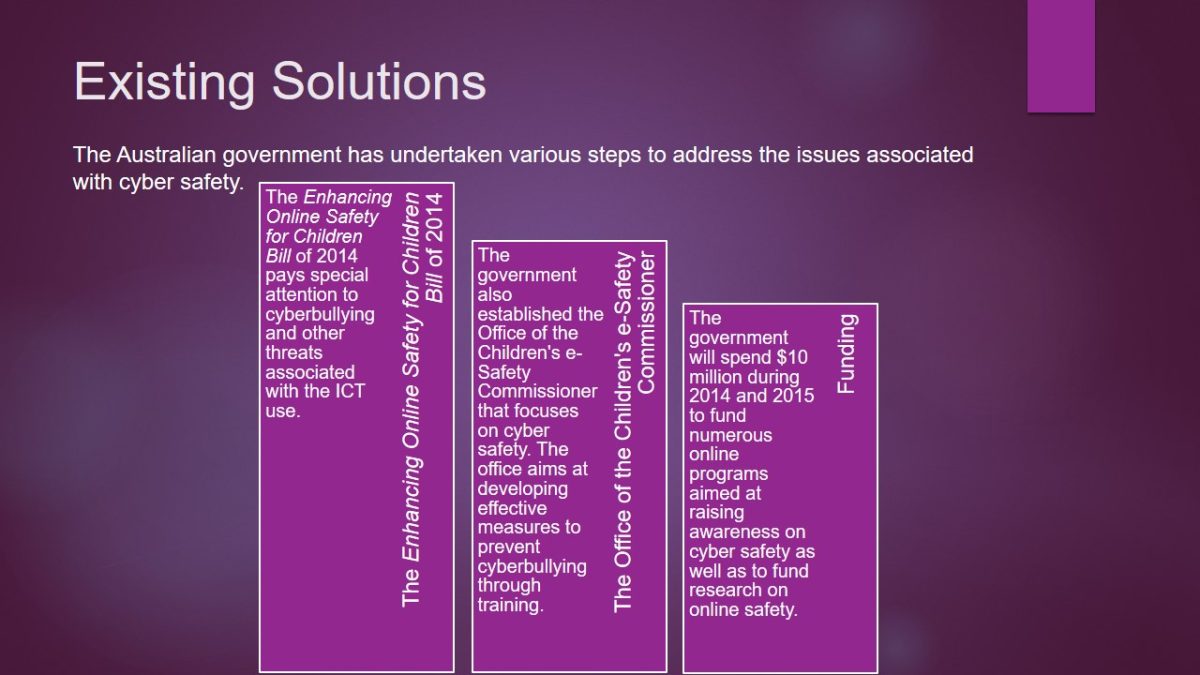
The Australian government has undertaken various steps to address the issues associated with cyber safety.
- The Enhancing Online Safety for Children Billof 2014
- The Enhancing Online Safety for Children Billof 2014 pays special attention to cyberbullying and other threats associated with the ICT use.
- The Office of the Children’s e-Safety Commissioner
- The government also established the Office of the Children’s e-Safety Commissioner that focuses on cyber safety. The office aims at developing effective measures to prevent cyberbullying through training.
- Funding
- The government will spend $10 million during 2014 and 2015 to fund numerous online programs aimed at raising awareness on cyber safety as well as to fund research on online safety.
Educators pay considerable attention to proper use of ICT:
- Proper ICT practices as a part of curriculum:
- Proper ICT practices have become a part of curriculum. At that, teachers educate students as well as their parents to use ICT effectively and safely.
- School policies in the sphere of responsible use of ICT:
- Schools’ codes of conduct contain considerable amount of information on online resources available to and helpful for students. The codes also touch upon responsible use of online resources (including information on responsible behavior online).
- School policies in the sphere of online safety:
- Schools’ codes of conduct also include guidelines in the sphere of online safety. This includes data on hazards and ways to avoid them, as well as information on preventing bullying or responding to it properly.
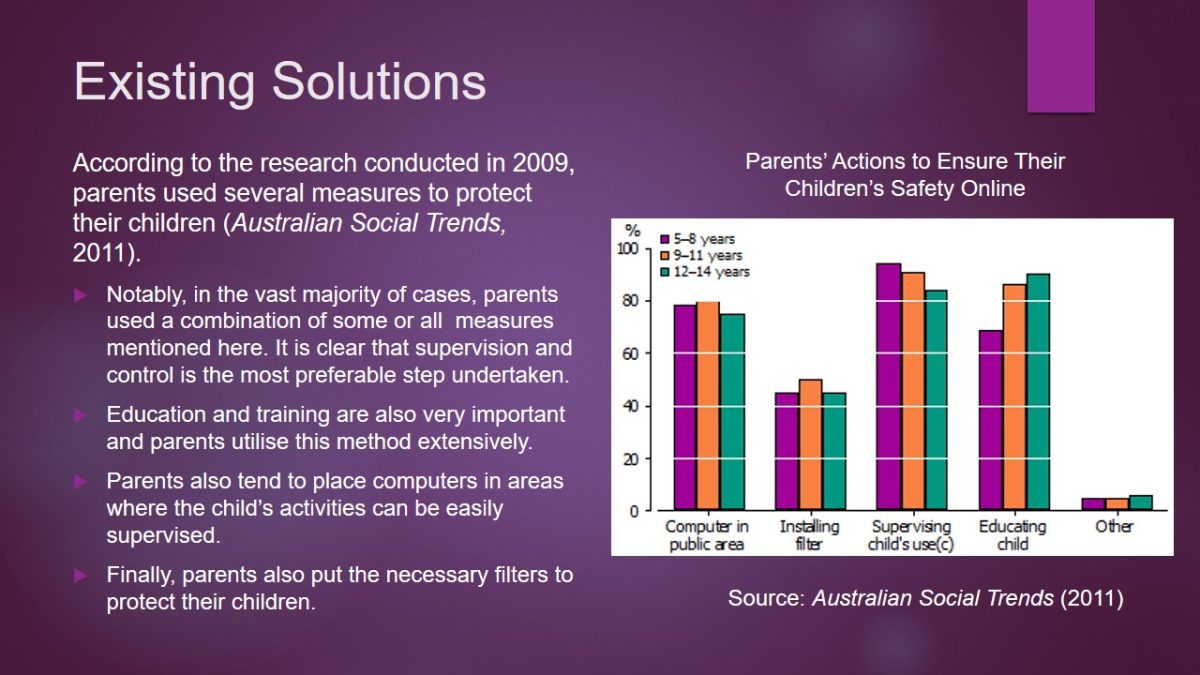
According to the research conducted in 2009, parents used several measures to protect their children (Australian Social Trends, 2011).
- Notably, in the vast majority of cases, parents used a combination of some or all measures mentioned here. It is clear that supervision and control is the most preferable step undertaken.
- Education and training are also very important and parents utilise this method extensively.
- Parents also tend to place computers in areas where the child’s activities can be easily supervised.
- Finally, parents also put the necessary filters to protect their children.
It is also necessary to mention such brilliant websites as:
- Cybersmart.
- Stay Smart Online.
- eSmartSchools.
These websites provide diverse and helpful information for students who want to know more about effective and safe use of ICT. Of course, educators actively refer to these resources in terms of the ICT training. At the same time, students are encouraged to use these resources in a variety of settings.
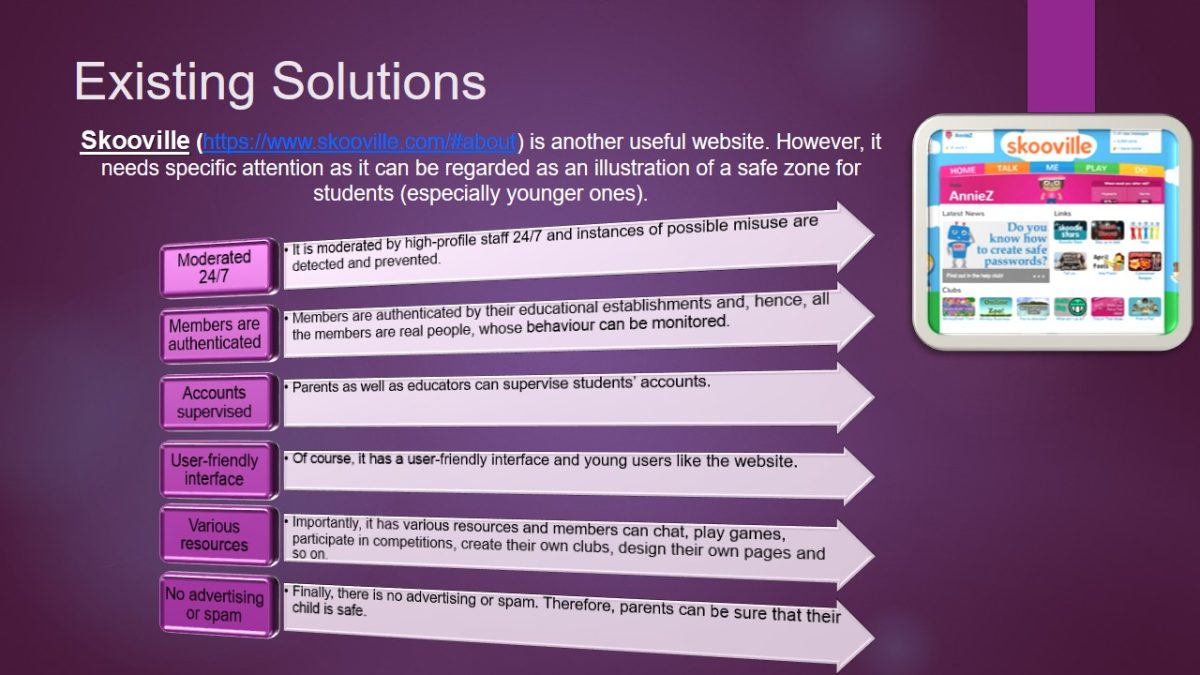
Skooville is another useful website. However, it needs specific attention as it can be regarded as an illustration of a safe zone for students (especially younger ones).
- Moderated 24/7:
- It is moderated by high-profile staff 24/7 and instances of possible misuse are detected and prevented.
- Members are authenticated:
- Members are authenticated by their educational establishments and, hence, all the members are real people, whose behaviour can be monitored.
- Accounts supervised:
- Parents as well as educators can supervise students’ accounts.
- User-friendly interface:
- Of course, it has a user-friendly interface and young users like the website.
- Various resources:
- Importantly, it has various resources and members can chat, play games, participate in competitions, create their own clubs, design their own pages and so on.
- No advertising or spam:
- Finally, there is no advertising or spam. Therefore, parents can be sure that their child is safe.
There are numerous benefits of such websites. Keep away from harmful resources
- First, they keep children away from harmful resources or resources they cannot work effectively with.
- These website keep children safe as there is no harmful or inappropriate information.
- They also teach how to use online resources responsibly and safely.


Possible Ways to Improve the Situation
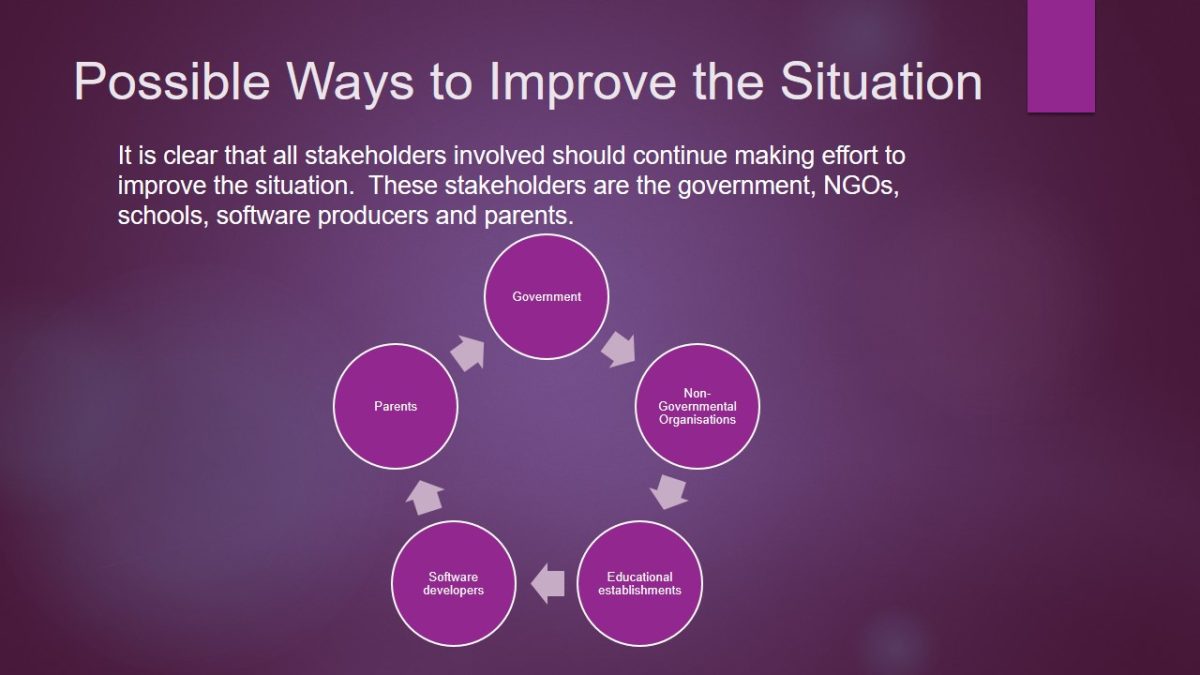
It is clear that all stakeholders involved should continue making effort to improve the situation. These stakeholders are the government, NGOs, schools, software producers and parents.
- Parents;
- Government;
- Non-Governmental Organisations;
- Educational establishments;
- Software developers.
Government
Of course, the Australian government should make sure that the existing policies are updated and effective.
Governmental agencies should implement numerous surveys and researches to reveal the gaps in the policies and provide the necessary recommendations to improve them. The research should address such areas as outcomes of policies, efficiency of funding, new trends and hazards, new opportunities, students’ use of ICT and so on.
It is also important for governmental agencies to collaborate with non-governmental organisations, software developers, commercial companies and educators. This collaboration presupposes sharing information, work on projects and so on. This collaboration may also involve provision of some benefits or certain tax relieve to organisations that develop safe websites or contribute to development of safety software.
The government should also develop proper sanctions to those software producers that do not pay the necessary attention to online safety and responsibility.

Non-Governmental Organisations
- Training and education:
- Non-governmental organisations should take an active part in training and education of young Internet users. These organisations should launch various projects involving educators, officials, parents and students.
- Implementation of research and surveys:
- NGOs should also implement further research on the matter as this will enable officials to address the existing gaps and make the cyber world safer.
- Contribution to development of safe websites:
- Many NGOs are involved in development of various websites and, hence, they can also develop safe websites for students’ use (something similar to Skooville).
- Sharing information with other stakehold:
- Finally, these organisations should also provide data to the government, schools and so on to make sure that all the stakeholders are well-informed.
Educational establishments
Schools should be the most active participants in the process. Of course, the primary goal of these establishments is to teach and train students, so schools should provide efficient training of students when it comes to online safety and responsible behaviour. (Focus on education and training in the sphere of online safety and responsible behaviour).
Furthermore, all educational establishments should make sure that they have codes of conduct that address the issues associated with online safety. These codes of conduct should be updated regularly. (Updating codes of conduct).
It is also necessary to monitor students’ accounts and their behaviour online. This can be carried out through school websites and school social networks. (Monitoring students’ online behaviour (focus on detection of such issues as cyberbullying and so on)).
Finally, educational establishments should also make sure that software they have is reliable and appropriate. Schools should contribute to development of proper software that will meet particular requirements and will be consistent with the school’s code of conduct. (Development of corresponding software).

Software developers
- Be responsible:
- In the first place, software developers should be responsible. They should understand that their products can be potentially harmful. These companies (as well as individuals) should try to enhance cyber safety.
- Collaborate with other stakeholders:
- Software developers should also participate in various projects and share information with the government, or other stakeholders. Of course, this does not mean that companies have to reveal their commercial secrets of confidential information. However, it could be favourable if software developers detected harmful software and informed the stakeholders about their findings. This would enhance online safety.
- Be full of initiative:
- Finally, these companies should be full of initiative to really make a difference and make the cyber world safe for children and young users.

Parents
- Be cautious:
- Of course, parents should remember that they are responsible for their children’s safety, first and foremost. They cannot rely on the government or educators and do nothing. Therefore, parents should remain cautious and supervise their child’s use of ICT.
- Be responsible:
- The measures mentioned above should be utilised in the future as well. Hence, parents should install filters, monitor their children’s activity, educate and train them, address educators to share ideas on online safety.
- Be active:
- Parents should always remember that their children need guidance and training. They should also understand that educators cannot foresee all hazardous situations and if a parent detects a potential hazard, he/she should address educators who will be able to react correspondingly.

Apart from governmental efforts and activities of educators and officials, each person can remain safe. Each user should remember about major rules when using the Internet. Particular actions to undertake are as follows:
- Students as well as their parents and teachers should:
- Disclose financial information on reliable and secure websites only (these can be governmental (.gov) or educational (.edu) websites, or these can be websites of well-known companies).
- Read carefully privacy policies (when registering or downloading anything, it is crucial to read all the privacy policies carefully and if there is something suspicious or unwanted (for example, you should agree to share your personal information with third parties), you should refrain from using this website).
- Use spam filters. This easy step can significantly reduce the amount of spam bombarding emails.
- Have a specific email for registrations. It can also be a good idea to have a particular email for registration as it will secure personal information that can be extracted from an account.
- Select your password and login carefully. Of course, it is crucial to make sure that the password is not easy to guess. It is inappropriate to use own name or a name of a close one, date of birth, or any other information that can be easily traced.
- Users should not:
- Answer emails asking to provide your passwords or personal information. Banks or any reputable companies do not address clients (especially via email) asking them to provide a password or any personal information. It is better to call to the bank or the company asking why the information is needed.
- Users should not allow the use of their personal information. Of course, it is important to make sure that personal data will not be used by third parties.

Conclusion
In conclusion, it is necessary to note that online safety remains one of the major priorities of the Australian government, educators as well as many individuals.
Technology is available to the vast majority of Australians and children are especially vulnerable as the cyber world contains numerous hazards. Various scams, frauds as well as cyberbullying still pose significant threats to proper development of Australian children.
It is also important to add that the Australian government as well as other stakeholders have undertaken numerous efficient steps to address the issue. There are effective policies and projects, various organisations contribute to development of software to ensure online safety. Educators train young users to use the Internet safely and effectively.
However, it is crucial to continue working in the same direction. The world is changing and the cyber world is not becoming much safer in spite of the effort made. Of course, there will still be scams and harmful software. Hence, education and training (as well as individual responsibility) are the most effective measures to utilise when addressing issues associated with online safety.

Reference List
Abrahams, N., & Johnson, D. (2015). Cyberbullying and why we need an e-safety commissioner.The Sydney Morning Herald. Web.
Australian social trends. (2011). Web.
Houghton, S., Hunter, S.C., Rosenberg, M., Wood, L., Zadow, C., Martin, K., & Shilton, T. (2015). Virtually impossible: Limiting Australian children and adolescents daily screen based media use. BMC Public Health, 15(5), 1-11.
Protecting personal information. (2015). Web.