R/3 System
The operation of monitoring the R/3 system performance and usage requires specific transactions to be carried out. The four transactions used for this purpose include ST03, ST06, STAT, and STUN. Thus, ST03 allows monitoring of the system performance, SAP statistics, and workload. ST06 is responsible for monitoring the operating system. STAT transaction deals with monitoring and controlling the local transaction statistics. Finally, STUN monitors the menu performance in the R/3 system.
The role of a Basis Administrator in an organization implementing an R/3 system is crucial as it is the Basis Administrator who runs the system, introduces it to the organization and all its employees, provides logging information to every particular employee, and monitors how R/3 system is used. As well, the Basis Administrator is responsible for R/3 system maintenance, data collection, and transactions and performance analysis.
R/3 Transport System
The main concepts behind R/3 transport systems include connection server, TCP/IP, Firewall, FTP, Local Area Network (LAN), Telnet, X.25, and IPX. These processes allow the connection between the homogeneous and heterogeneous R/3 systems and are administered by two basic transport protocols – TCP/IP and FTP. TCP/IP is the protocol providing communication opportunities to the organization’s clients and servers. The file transfer protocol (FTP) is the tool of file exchange between servers and R/3 systems connected.
Gateway is a communicational network used in R/3 systems as a protocol converter and translator. Thus, the role of the gateway is to provide communications opportunities for the computer resources that operate with different protocols. Being equipped with a router and a switcher, a gateway receives protocols from a source, converts them into the necessary format, and forwards the set of protocols to the intended source.
R/3 System Instances
The operation of any SAP system on the whole and R/3 in particular, is based on the performance of instances. Central and dialog instances are two basic instance types. The major differences between the two include the fact that central instance is unique for a system, while there might be numerous dialog instances in this system, and the point that the central instance consists of hardware and software, while dialog instance is a set of processes to facilitate the central instance performance.
The crucial role in setting instances and creating a database as a whole is attributed to the basis administrator. This person is responsible for instances’ creation and he/she is the only person entitled to create central and/or dialog instances. There are three stages in which an administrator can alter the properties of instances. For this, the administrator needs to open the instance database through SQL and RESETLOGS, delete the unnecessary data or the whole instance, and create the new instance.
EPR System
Seemingly, the most fitting approach to building an ERP system is the integration method according to which the ERP should comprise data from databases and modules considering the functioning of as many areas of the organization’s activity as possible. Therefore, an effective ERP should include data on at least the organization’s production process, financial performance, warehousing, customer relations, and supply chain management. The major issues associated with ERP building include the system’s potential incompleteness and lack of software and hardware resources to compensate for the drawback. These issues can be solved by putting more emphasis on IT development in the organizational strategy and increasing ERP development funding.
The local and domain installation procedures for ERP systems, as well as for other SAP, can be compared to the location of the server. The local installation is easier, but it is connected with the difficulty of authorization in case if some other system elements are installed on the domain server. The latter, in its turn, is the common server that unites numerous locals, but the transition from the local to the domain installation involves creating a homogeneous copy of the system on either of the servers and introducing this copy to the relocated, local, or domain, server.
To install an R/3 system, the basis administrator should work on three major accounts that include the operating system, the database, and the application. The operating system is the software package that enables the computer hardware to perform applications hosted at the computer. The conventional scheme of the operating system is the following: hardware – operating system – application – user. The application is the very function of the operating system, while the database is the complex of data concerning the applications carried out by the operating system. The improper functioning of the operating system, the database, and the application makes the installation of the ERP system impossible.
Message Server
Although message serves and gateways both deals with handling information, the main difference between them is that message servers only receive and forward messages through the application program interface (API), while gateways can convert messages and protocols to the format needed for the protocol to be received by a system using other protocols. At the same time, a message server is a part of a gateway, as a message server receives messages and the gateway converts the protocols to forward them through the message server again to another system.
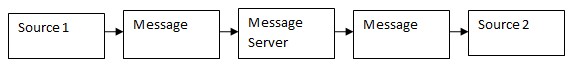
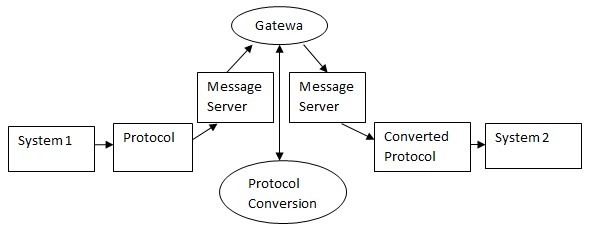
The connectivity between the message server and the gateway is checked by the quality of protocol conversion, as in case of the lacking connectivity the gateway could not receive the necessary message and respectively convert its protocol. Logs also help in checking this connectivity as they record the data about operations performed by the servers in the worms of single weblogs or parted access, error, and referrer logs.
The instance number serves as a sequential number of the form of the instance in the row of the applications conducted and requests for a page or another network resource. The instance number is based on the software client-server model, as both client and server roles are played by software programs in this case. For example, the Internet browser is the client software, while the website that is requested through this browser is the server software.
Load Balancing Monitoring (Administrator Functions and End Users Services)
Every part of the ERP, i. e. operating system, database, and application, like R/3 for example, is subjected to a particular workload, whose control is vital for optimal load balancing and resource utilization. Thus, to monitor the load balancing of the operating system, it is necessary to install a load balancer and monitor the performance of nods as for their workload. A timely reduction of the workload is necessary to retain the balance.
To monitor the load balancing of the database it is necessary to first establish the database goals and workload standards. Next, the use of the load balancer installed on the computer might be rather beneficial. Finally, it is the task of the administrator to notice the database overload and clear it to enable the database to store the next portion of data.
The monitoring of the load balancing in applications like the R/3 system is also a challenging task in which a load balancer is a necessary tool. As well, the application load balancing can be monitored by the basis administrator whose responsibility is to collect the applications’ performance data and to carry out the timely maintenance of the operating systems on the whole and applications in particular.
Performance and Sizing
In using the SAP systems, metrics play an important role in finding out how optimally and correctly the resources of the ERP system are used. Memory use should be monitored as it allows understanding the system potential and current workload. The metrics of disk performance are mostly focused on disk response time and the speed of applications’ conduct. The metrics of the CPU and network bandwidth also evidence the power and the working potential for the SAP system by providing data about the maximum allowed workload and processing capacity.
The recent developments in ERP interfacing are mainly connected with introducing a more computerized approach to ERP building. If formerly ERPs were the attempts of companies to control all spheres of their activities, nowadays ERP development is a highly computerized process, which also involves higher costs as a result of third party vendors’ activities. The latter consists in buying and reselling goods or services to smaller companies. Computer technology and internet hosting are two industries affected by third-party vendors to the greatest extent.
ERP System Administrator Transactions
In the process of work, system administrators use the set of transactions that include SU01, ST02, SM50, RZ10, DB02, and SECR. The transaction SU01 can be used for the administrator authorization and the creation of a new system user. ST02 fulfills the functions of identifying the SAP system buffer performance statistics. SM50 transaction allows seeing and managing the work processes in the system and reducing or increasing the workload based on the data. Further on, RZ10 allows editing the instance profile by clicking the extended maintenance and change buttons in it. DB02 is another statistical transaction that allows seeing the database history, applications record, and current storage capacity. Finally, SECR transaction is concerned with security and environment audit matters. Accordingly, it is transaction SM50 that would allow modifying the threshold value for disk usage percentage for an alert monitor.
ERP Metrics
Oracle is one of the central instances in the ERP system. It has over 250 metrics but Data Buffer Hit Ratio Alert, Redo Log Space Requests Alert, Shared Pool Contention Alert seem to be crucial in its performance. Data Buffer Hit Ratio Alert reports the cases of the system hit ratio falling below the standard, Redo Log Space Requests Alert allows log space requests increase and system capacity development and Shared Pool Contention Alert allows avoiding the multitask locks requests in which tasks request locks that other tasks are currently using.
The traditional means of enforcing security into an ERP system include the use of firewalls, means of detecting intrusions, and VPNs. However, recent ERP developments attribute more attention to personalized and distinguished ERP access. For example, currently, ERP access by secure login and password is preferred by organizations together with delimiting the areas of their ERP that the employees of a particular department can, or cannot, access.
R/3 System Security
R/3 System Security elements consider the operating system, the database, and the application as the most important aspects of security:
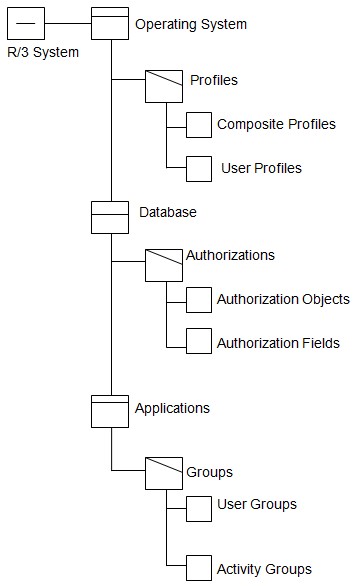
Thus, it is obvious that operating systems are protected by profiles; the databases have authorizations as their protection means, while applications are protected by the division of their variety into user groups and activity groups.
Client-server Models Comparison
The historical development of client-server models is characterized by three major stages. First, sockets, and latter secure sockets (or SSL) were used for clients to request data and servers to provide it. Second, encryption and encoding were introduced. Third, currently, client-server models operate with the ERP-dictated HTML and URL programming languages that allow referring to the server content without the need to provide its instance number.
The future of ERP is reportedly bright due to the addition of the four new architecture elements to it including the individual elements coverage, wider applicability, greater functionality, and better utilization of the Internet opportunities. These four elements allow ERP to develop into a more modern and applicable SAP system.
User and Activity Groups
User groups serve the function of dividing the users of the networking resources according to their preferences, recorded application requests, and other factors. The major role of the activity groups is to sort out the activities, or applications, that the servers might carry out to have greater control and processing capacity over those grouped activities.
The transaction code SU53 is used to display check values and authorization values. For example, if a user does not have access to a certain area of an ERP, the consideration of authorization error messages might reveal the unsanctioned access to those areas by the unauthorized user.
The process of detecting the actual set of transactions for a given period involves the calculation and the analysis of the typed transaction codes for this very period. The basic method for a systems administrator to find out the actual number of dialog steps performed during a transaction is to analyze the situation in the context of the administrator’s knowledge of the average dialog steps’ number required for a particular transaction.
The method to allocate a particular resource to a user is to follow the steps that include analysis of the resource necessity for the user, pre-allocating of the resource, and final allocation of the resource. Only systems administrators can allocate resources to users as they possess resource existence, management, and operational authority.
Setting the ERP System Disaster Recovery Plan
The most significant concern about an ERP disaster recovery plan is the presence of at least two standby application servers. Next, the remote servers should display an increase in application rates at the time of disaster. Finally, manual work should be eliminated or minimized. A systems administrator should always be aware that recovering from a disaster the ERP should display data consistency and be protected from intrusions.
The batch work process deals with transferring the set of data to the database, while the dialog work process fulfills the requests of active users for carrying out dialog steps. Only one batch work process is possible at a server, while dialog processes are proportionate to the number of dialog steps executed. Therefore, dialog work processes are more effective in respect of resources and processing capacity. To further improve the system efficiency, suitable system files might be modified or archived to achieve load balancing for all the elements of the system.