Introduction
NYS OMH operates more than 4500 facilities, including 1300 psychiatrist facilities in the New York State. It has its Headquarters based at Albany. It conducts mental health research with the goal of providing prevention, treatment and recovery. Furthermore, it provides state operated inpatient and outpatient mental health support and services to residents of the state of New York.
Its major obligation is to secure its own Information systems and information resources collected or created as part of its ongoing business. IT is requisite to guarantee security of data and protection of confidential information belonging to different clients and patients. So, one of its important undertakings is security of data to ensure Privacy of clients and patients.
NYS OMH is a non – profit organization, which is a constituent of the Research Foundation for Mental Hygiene Inc. It aims at improving research and training. NYS OMH undertakes its activities using the latest IT available, this enables easy and fast communication between the field offices and the headquarters.
The state of New York has the largest multi faceted mental health system that serves over 700, 000 persons (NYS OMH, 2012). Thus, the information being handled by the organization is prone to breach due to enhancement of computer Technology.
Security breach is the violation of the set protocols, procedures, and processes by a third party. In organizations like NYS OMH, this kind of vice needs not be a factor so as to enable smooth operation of the organization and still be able to achieve its goals.
Types of Security Breach
In such an organization security, breach is not something that can just be written off. There are two kinds of security breach: Internal and External security breach, which can present as an electronic security breach (data security breach) and physical security breach.
Electronic security breach involves duplication of data through shared storage media like flash disks or interception of data on transmission by hackers without authorization for malicious purposes. On the other hand, physical security breach involves the loss of back up storage media, usually different types of hard disks.
Under internal security breach, there is the (Electronic Security Breach) IT security breach and the (Physical Security breach) physical theft of assets of the organization. It is classified as internal in the sense that an insider (employee) facilitates the occurrence of the security breach by leaking out confidential information about the company.
Figure 1: A line graph of security breach at NYS OMH in 3-month period for 2011
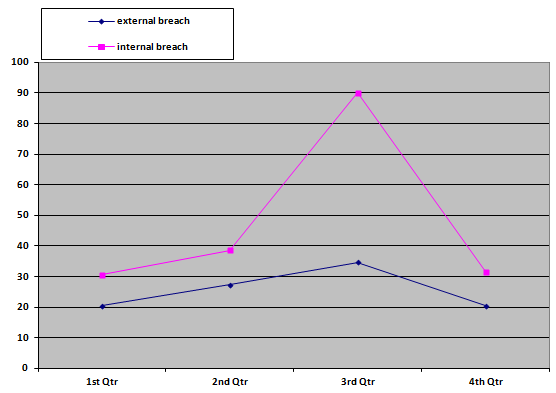
The above graph (Figure 1) shows the rate of security breach at NYS OMH for the past one year. From the graph, it can be concluded that internal security breach is more as compared to the external security breach.
Control and Management of Security Breach
External security breach involves hackers intercepting information for malicious purposes pass as an IT security breach. The theft of company’s asset without the help of an employee is a type of physical security breach from outsiders.
To avoid such kind of security breach, NYS OMH uses the following software / programs to try prevent the security breach, NYS OMH uses electronic applications, electronic mean to get, use, maintain and store personal health data and information (Jones, & Ashenden, 2005).
NYS OMH also uses the WORM (Write Once Read Only) program to prevent security breach. It has electronic and technology signatures. Its advantage is that it prevents tampering of data after creation of the initial files. NYS OMH also employs the virtual private network (VPN) to carry out networked transmissions.
VPN is used to make an encrypted network (ciphered network) and channels between the network and the user’s wireless device, hence hiding data and information transmission (Al–Hakim, 2007). Its advantage is that it is less costly and allows for network scalability (Mitchell, 2012; Shinder, 2001).
Other program the OMH employ encompasses use of firewall, which prevents unauthorized access to stored data and information. Use of anti – virus such as Norton and McAfee to prevent viruses and malicious software to corrupt stored data is method employed by the NYS OMH to prevent data security breach.
Compliance policies and regulatory policies instituted by the state and federal government, ensures protection of patients’ information. Adherence to this policies and regulations is another form by which the organization to curb security threats to data and information.
Others strategies include intrusion-detection systems, authentication, upgrades and software patches and access point configurations (Appari, & Johnson, 2008). The adoption of Electronic Health Records (EHR) as envisioned by the government has ultimately reduced the threat posed by Electronic security breach.
Some of the regulatory practices employed by the NYS OMH include enactment of compliance policies and regulatory policies in NYS OMH in relevance to security of patient’s information.
Counter Measures
Countermeasures make a network more secure and therefore enhance security. Some of the countermeasures employed by NYS OMH are discussed below.
There are technical countermeasures, which play a very important role in security management. Furthermore, these measures ensure that patient’s data and information are accessed only by the authorized people (Fleming, 2009). Technical countermeasures include the use of hardware and software to offer protection to web application and networks.
These measures include public-key infrastructure, firewalls, virtual private networks, encryption, intrusion-detection systems, authentication, upgrades and software patches and access point configurations (Al -Hakim, 2007).
There is also Technical training as a preventive strategy adopted by NYS OMH, because of the fact that that most of the previous security breach occurred internally, and did not result from external factors. In addition, educational initiatives are important in ensuring that a cultural change is incorporated in the NYS OMH.
This has been summed up by high-level confidentiality policy to all personnel who have access to very sensitive information. These countermeasures can be classified as countermeasures from the social perspective (Hanover, 2012).
Analysis & Recommendations
Upon implementation of these countermeasures, cases of security breach have reduced though not been eliminated. Considering the Software employed by NYS OMH ,the level of Data security has been greatly improved. Yet, the organization has to acquire the very latest software to ensure total elimination of the vice (Hogan, 2010).
Now, upon considering the EHR and its implementation at NYS OMH incorporated important clauses, which encourage high penalties for persons who engage in security breach.
This fines range from $50,000 to $1, 500,000 depending on the serious of the crime (NYS OMH, 2010). OMH has a well-established Security Management Systems, which foster security on patients’ information. This has made its network secure from any viable security breach.
Considering regulations to be employed by the organization, NYS OMH should set up regulatory compliance policies, which can be supported by the confidentiality, and privacy policy. These policies would enhance the already existing protocols and security counter measures thus improving security in NYS OMH (Ko, & Dorantes, 2006).
Considering the recommendations for the countermeasures which include: public-key infrastructure, firewalls, virtual private networks, encryption, intrusion-detection systems, authentication, upgrades and software patches and access point configurations, security in NYS OMH has improved tremendously.
In addition, the employees undergo continuous training on importance of data security and confidentiality to reduce or eliminate internal security threat.
References
Al-Hakim, L. (2007). Web Mobile-Based Applications For Healthcare Management. Hershey, PA: IRM Press.
Appari, A., & Johnson, M. E. (2008). Information Security And Privacy In Healthcare: Current State Of Research. Hanover, NH: Dartmouth College.
Fleming, D. A. (2009). Ethics Conflicts In Rural Communities: Health Information Technology. Hanover. NH: Dartmouth College Press.
Hanover, J. (2012). 3 Massive Security Breaches In 3 Weeks: Taking A Closer Look. Web.
Hogan, M. F. (2010). NYS OMH Strategic Framework. Web.
Jones, A., & Ashenden, D. (2005). Risk Management For Computer Security: Protecting Your Network And Information Assets. Burlington, MA: Elsevier Butterworth-Heinemann.
Ko, M., & Dorantes, C. (2006). The Impact Of Information Security Breaches On Financial Performance Of The Breached Firms: An Empirical Investigation. Journal Of Information Technology Management, XVII, 13-22.
NYS OMH (2012). About OMH. Web.
NYS OMH. (2012a). Description of the Security Management System. Web.