Introduction
Due to the advancement in information and communication technology, there has been an increased need for privacy when passing on confidential information. Johnson & Jajodia (1998, p. 26) state that as the number of data exchanged on the internet increases, so does the need for information security to prevent illegal access and use. Moreover, the broadcasting and publishing technologies require ways of concealing their information (p. 26).
Current research approaches have focused on concealing information using steganography, among other methods like watermarking, copyright protection for digital media (Johnson & Jajodia 1998, p.26). However, this paper focuses on hiding information via steganography in digital media. According to Petitcolas et al. (1999, p.1062), Steganography is widely used in digital communication to ensure privacy and confidentiality since it’s difficult for hackers to trace and track the hidden communication.
Overview of steganography
Provos and Honeyman point out that steganography has been existent since the reign of the Greek empire and in Greek; the word means covered writing. Several ways were used to hide information throughout history like the Greeks used wax-covered tablets where they wrote messages (Provos and Honeyman 2003, p. 32-33). They scraped off the wax from a tablet and wrote the message then they were covered with wax to seal off the message.
A story of a slave was recorded by a Greek historian where the slave’s head was used to pass on hidden information which was tattooed on the skull after shaving. When the hair grew, the slave went to the recipient of the message who shaved the head to expose the hidden message (Petitcolas et al. 1999, p.1065). At the time of the Boer War, Lord Robert Baden-Powell was a scout for the British embedded maps that marked certain positions of enemies into butterflies’ drawings.
It’s also recorded that invisible inks were used by Axis and Allied spies to convey messages. The ink contained urine or fruit juice which exposed the hidden message when heated or put under ultraviolet light (Provos and Honeyman 2003, p. 33). With the invention of modern computers and software in the mid-90s, the older techniques of concealing messages inside other messages and images gained more popularity igniting a transformation in such methods of hiding information.
Cryptography and steganography are methods used in secret communication but they differ. In cryptography, contents of the secret data are hidden from unauthorized access but steganography hides even the existence of the message itself (Kessler 2004). An analysis by Johnson & Jajodia indicates that steganography and cryptography are both good ways of securing confidential information but can all be compromised (1998, p. 28).
Therefore these two methods can be combined for a better outcome where a message is encrypted and then hidden using steganography. Provos and Honeyman (2003, p. 33) give fingerprinting and watermarking as other methods related to steganography which are majorly involved in academic property protection. In watermarking, a signature is a hidden message in objects that denote ownership or the source of documents. In contrast, fingerprinting uses different, special marks implanted in distinct copies of the carrier objects which are distributed to customers (Provos and Honeyman 2003, p. 34-35). In these methods, the hidden information within files may be known to the public which is contrary to steganography.
According to Bender et al., when one is passing private and confidential information, then steganography is the best method to be used. He explains that intelligence agencies can exchange extremely confidential information through image steganographic software (2000, p. 547-548). This technique is very vital in the storage of information that is confidential especially top secrets in big institutions where information is on steganographic hard disk partitions (Schneier 2000). This is secure and invisible for a long time allowing access only to the owners.
Though it seems to be a brilliant means for exchanging confidential information in a hidden manner, steganography is also used in ways that are a threat to national security (Schneier 2000). The ability to conceal a message in a computer has turned out to be a communication method used by al-Qaeda to covertly convey their plans of attack to their member terrorist cells. Bender et al. (2000, p. 546-548) state that messages can be passed on to organizations, and with a covert operator within, instructions and missions can be forwarded secretly for the operator to execute.
Furthermore, hidden information via steganography can infect computer networks and even demolish a vital infrastructure system (Schneier 2000). The technique is used to hide malicious programs which threaten computers and network systems in large organizations. Information concerning illegal deals like drug trafficking, money laundering, the distribution of child pornography, and insider trading can be hidden using steganography (Kessler 2004). In such inappropriate usage, steganalysis techniques are needed to detect and destroy such communication.
Steganography techniques used in images
Digital images are the common carrier files for secret messages due to their popularity on the internet and there are several steganographic techniques applied during information hiding within images. Before embedding information in an image, the size of the image must be measured against the message to be transmitted (Petitcolas et al. 1999, p.1063). According to (Bender et al. 2000, p. 550), a cover-image (original image) holds the secret message becoming a stego-image and these images are so identical that the human eye does not perceive the concealed information as shown in the figures below.

Some images are large to be passed over a normal Internet link and need to be reduced to a file size that enables them to be displayed in a reasonable time. The image data are analyzed and condensed by mathematical formulas leading to smaller files through the process of compression (Johnson & Jajodia 1998, p.30). In lossy compression, the smaller file is produced by the deletion of excess image data from the original file. Those details that are too small to be detected by human eyes are removed resulting in an image similar to the original though not exactly a duplicate. Though a smaller image file is generated, part of the embedded message may be lost due to the removal of excess image data. The lossy technique is used in the Joint Photographic Experts Group (JPEG) image format (p.32).
Mathematical formulas are used to represent data instead of removing information from the original image in lossless compression. The integrity of the original image is intact and the decompressed image output is typically identical to the original image. Although the original image is not tampered with, the image is not reduced to a small file Graphical Interchange Format (GIF) and 8-bit BMP (a Microsoft Windows bitmap file) are image formats using lossless compression. These compression techniques define which steganographic algorithms to be applied (Provos and Honeyman 2003, p.40).
Johnson & Jajodia (1998, p.28) proposes two main categories of steganographic techniques used in images; image and transform domain. In the image domain technique, messages are implanted directly onto the intensity of the pixels, and the bit-wise technique is used during bit insertion and noise manipulation (p. 29). Lossless image formats are preferred in the image domain and the technique depends entirely on the image format. In the transform domain technique, the secret message is embedded in the image after image transformation, and in the process algorithms and image transforms are manipulated. Messages are more robust as they are hidden in the more significant parts of the cover image. As opposed to the image domain, the transform domain does not depend on the image format (p.29).
Image techniques entail original image distortion whereby image patterns are added to others (Petitcolas et al. 1999, p.1066). The Least Significant Bit (LSB) hides information concealed in images through the use of image-pixel bits which hide important beats of other images (Bailey and Curran 2006, p. 62). When creating a JPEG (Joint Photographic Experts Group) image, you need to have both the host image and the one to be hidden before selecting the number of bits to hide the secret image in. When many bits are used, they increase the clarity of the secret image but the host image deteriorates. Pixels from the two images are combined into a new image (p. 63). However, this technique makes it easy for attackers to discover and remove the hidden data (p. 63).
According to Bailey and Curran (2006, p. 60-70), transformation techniques are known to embed secret messages by “modulating coefficients in transform domain”. Direct Cosine Transformation (DCT) is a method of data concealing and the JPEG compression technique uses the DCT algorithm. The image is divided into eight by eight squares each of which is changed via a DCT (p. 73). The result is an array of 63 multidimensional coefficients. At the compression stage where data is lost, a quantizer rounds the small insignificant coefficients to zero while larger ones end up losing their accuracy (p.74). A collection of updated coefficients are then compressed again by Huffman encoding scheme.
This method works well since a casual observer at the pixel values does not notice anything and the concealed data can be widely dispersed over the image making it more robust. Though it may not be easy to distort the data, the method is exposed to noise. Johnson & Jajodia (1998, p. 31) asserts that Wavelet Transformations are used at high compression levels in image techniques to produce more robustness of the hidden data which are very vital in watermarking. Many wavelets are taken when encoding an image and the high-frequency element in the image is stored independently from low-frequency parts allowing the low-frequency areas to be compressed due to their susceptibility (p.32).
Steganography techniques used invoice
In everyday life, communication goes on either via face to face or using media like telephones and email. In case a secret message is to be passed; these methods are not secure enough. Cases have been recorded where face-to-face deliberations have been intercepted by unauthorized people who use covert listening strategies. Moreover, telephone communications may also be captured by telephone tapping devices. Steganographic techniques have been applied in this field to ensure secure Internet-based communication. According to Mazurczyk and Lubacz (2010, p:153), Voice over Internet Protocol (VoIP) is a real-time system of communication that secures secret messages due to its instantaneity and it also maintains high-quality performance for its services.
VoIP is a group of products that facilitate communication over a data network in which voice is a key feature. Due to it being cheap with advanced digital features, the VoIP technique has been preferred to the public switched telephone network (PSTN) (p. 154). VoIP – based steganography is easily achieved since the continuing chat of VoIP itself can hide secret messages. This is because, in a VoIP channel, the voice data are known to be the only data carried. Furthermore, eavesdroppers are not able to detect abnormity in a short VoIP due to insufficient time of exposure (p.154).
The steganographic techniques used like the least-significant-bits (LSBs) steganography, must ensure the security of the information irrespective of how complex the specific speech codec may be. LSB steganography is widely used due to its high capacity and security. A method used to convey secret speeches was proposed by Huang et al. (2009) which relied on information hiding in VoIP systems. In this process, secret speeches were compressed, and then their binary bits were filled into LSBs of the cover speech codec with G.711. However, most of the steganographic techniques could be easily detected by the steganalysis algorithm because of the non-uniform distribution of LSBs of the cover speech in binary bits of the secret messages (Petitcolas et al. 1999).
According to Petitcolas et al (1999), secret messages needed to be encrypted before embedding to secure them. Unfortunately, traditional encryptions could not be used for real-time steganography over VoIP since they are time-consuming. Therefore an m-sequence-based model for VoIP is preferred where the m-sequence encrypts secret messages before the LSBs substitution and here, the statistical steganalysis algorithm cannot detect it. Moreover, an appropriate synchronization mechanism is used in this model based on protocol steganography that securely transmits secret data in real-time (Huang et al. 2009).
Huang et al. (2009) propose effective VoIP-based steganography, in which there must be an embedding and restituting algorithm as well as synchronization. This implies that the secret message has to be securely embedded into VoIP streams and restituted. The sender and receiver have to agree on when and where the secret data will be implanted into VoIP streams. In fig.1 below, it’s assumed that the sender (Alice) intends to convey a secret message to the receiver (Bob) during their conversation through the VoIP system. An embedding algorithm is used by Alice to embed the secret data into the voice and the secret data are retrieved by Bob using a restituting algorithm when he receives the voice.
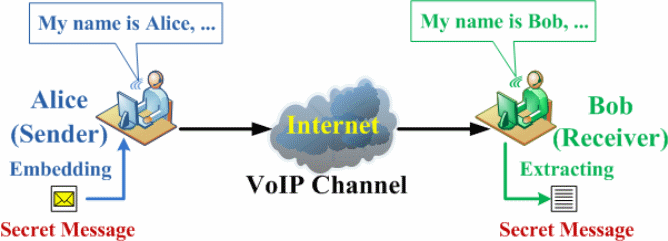
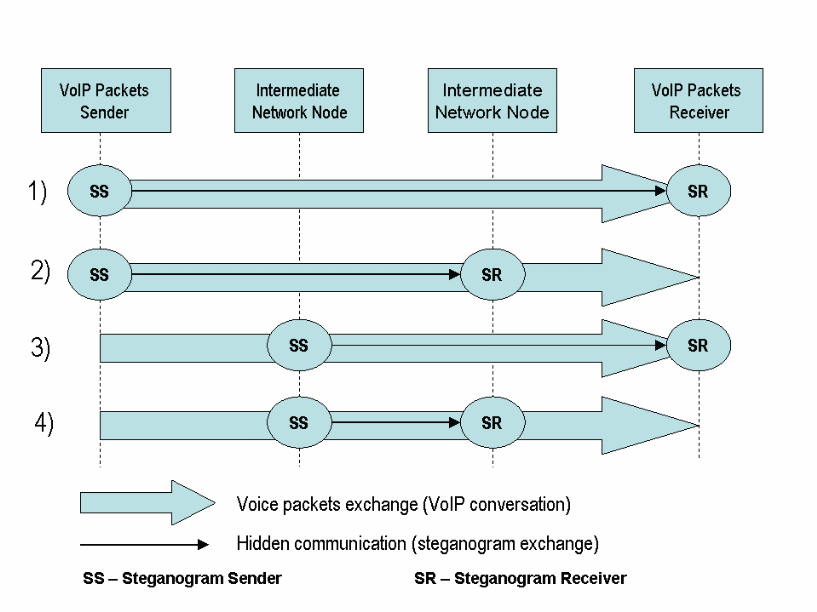
For VoIP systems, information can be hidden during communication in several ways as shown in Figure two below (Mazurczyk and Lubacz 2010). In the first case (2), stereograms are concurrently exchanged in a VoIP conversation between the sender and the receiver and the concealed data path is similar to the talk path. In the following cases (2-4), the intermediate nodes result in the use of a part of the VoIP end-to-end path to hide information and in such a case, those communicating are unaware of the steganographic data switch.
Due to the advantages associated with VoIP, much research has been done on VoIP-based steganography. For instance, Mazurczyk and Lubacz (2010, p: 154) presented LACK ((Lost Audio PaCKets Steganography), a technique that uses lost audio packets that are intended for VoIP. The payload (information to be hidden) of some deliberately delayed packets that are unnoticed by eavesdroppers, conveys secret messages to the receiver. LACK is widely applied in IP telephony and it is because markedly delayed packets in communication protocols on media like Real-Time Transport Protocol (RTP) are discarded during the reconstruction of data at the receiving point since they are viewed as of no use (p. 155).
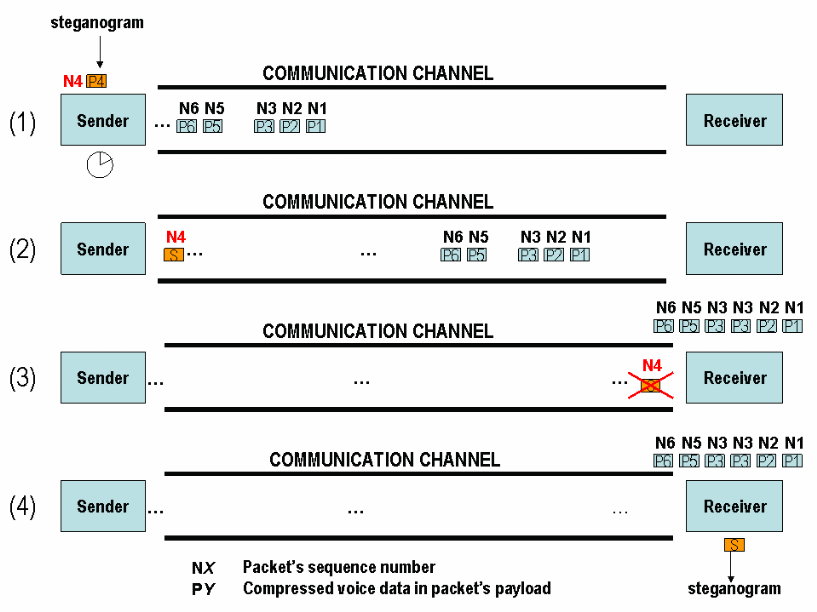
When using LACK, a few of the chosen audio packets are delayed deliberately at the transmitter point. Should the receiver view these delayed packets as extreme, they are ignored and the steganography used is unnoticed. The receivers aware of the steganography procedure get the secret message conveyed by the payload of the purposely late packets (Mazurczyk and Lubacz 2010: 159). Fig. three below illustrates four primary scenarios in which LACK is used.
In the first scenario (1), the voice payload of a packet chosen from the RTP stream is replaced with steganogram bits. Selected packets are delayed by a specific time and then passed through the channel of communication as seen in the next case (2). Scenario 3 shows that an extremely delayed packet is discarded by the receiver who is not aware of the hidden message at the receiver’s side. Should the receiver be aware of the steganographic technique, the payload is extracted from the delayed packet (scenario 4).
Virtual Local Area Networks (VLANs)
Local Area Networks (LAN), known as the simple network of computers in an area initially, refers to a single broadcast domain (Varadarajan 2006). Workstations are connected via hub/repeater which disseminates incoming information through the network. When two people send information concurrently, a collision occurs leading to loss of transmitted data. The hub/repeater propagates the collision throughout the network. A bridge/switch may be used to block the transmission of these collisions through the network. In contrast, a router does not allow the propagation of broadcasts and multicasts in a network. Therefore, a LAN segment is made up of hubs, repeaters, and workstations and may also be known as a collision domain as shown in figure 4 below (Varadarajan 2006).
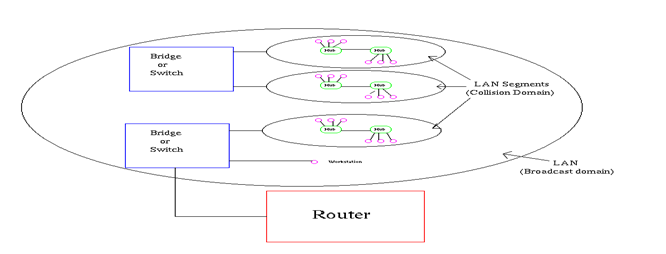
According to Varadarajan (2006), the physical link of workstations, hubs, and switches determines the creation of broadcast and collision domains in a certain LAN meaning that all users on A LAN are to be located in one area. Information broadcast on one LAN reaches other users on that LAN but a router prevents broadcasts departing from a LAN. Compared to a switch and a bridge, a router takes longer to process incoming data.
This motivated the development of Virtual Local Area Networks (VLANs) to replace the use of routers in containing broadcast traffic (Varadarajan 2006). VLANs enable a network manager to come up with several broadcast domains by logically dividing a LAN hence the workstations do not have to be in the same physical location. The broadcast domains can be defined in the absence of routers in VLANs (Varadarajan 2006). According to Varadarajan (2006), bridging software can instead be employed to elicit the stations of work that may be included in the broadcast domain. However, communication between two VLANs is via routers (Varadarajan 2006). Figure 5 below shows a sample VLAN in physical and logical views.
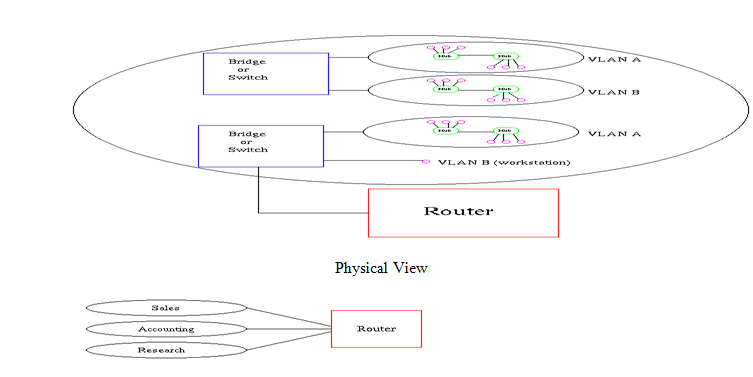
VLANs are used in networks with a lot of broadcasts and multicasts to evade sending such traffic to needless destinations. A broadcast domain of ten users, where traffic is intended for five users, places five on a separate domain to avoid it reaching unintended users (Varadarajan 2006). The latency of routers increases as the volume of traffic increases because they need further processing of incoming traffic which compromises performance. Varadarajan, (2006) proposes that when VLANs are used, few routers are needed because broadcast domains are generated using switches. Workgroups consisting of members from different departments formed periodically can communicate via VLANs where broadcasts and multicasts are contained within instead of moving them physically together (Varadarajan 2006).
VLANs reduce network costs incurred in LAN due to changes of users in LAN as well as reconfiguration of devices. Reconfiguration of routers in VLAN is not needed in the case of the movement of a user. Private and confidential data broadcast on a network may be propagated to only the intended users on a VLAN limiting chances of unauthorized access from outside to the secret data. Therefore VLANs ensure security for sensitive data and in case of an invasion, they inform the network manager (Varadarajan 2006).
Current issues in Steganography, Digital Watermarking, and Digital Copyright
Provos and Honeyman (2003, p. 35) state that steganographic techniques are vital to the greater achievement of the mushrooming multi-billion dollar digital media supply industry. However, the industry lacks advanced technology that ensures completely no illegal copying of copyrighted digital items. Moreover, with no development and acceptance of digital Watermarking technologies, there is no proof of possession of a digital product.
Schneier (2000) reports of a case where the entertainment industry failed to prevent the illegal digital media copying witnessed a few years ago when the DeCSS program was released on the internet. This program which was created principally for playing DVDs on Linux systems permitted the copying of DVDs. Furthermore, the trial for custody and circulation of this software was eliminated by a California Appeals Court and this has been a big blow to the movie industry as it struggles to guard copyrighted works (Schneier 2000).
The process of digital watermarking preserves the quality of the product and proves its ownership. For digital watermarks to be effective business tools, they must be robust and tamper-proof (Provos and Honeyman 2003, p. 34-35). The digital rights protection industry has created business opportunities with companies like Digimarc which is a chief developer of digital watermarking technologies. Digimarc gives tools like a small mouse-like device used to scan images and establish whether it’s original or a copies. Moreover, tools like Epson’s “Image Authentication System” (IAS) verify images right from when they are captured in a standard JPEG file via digital cameras (Kessler 2004). Though it does not guard against copying, it helps detect interference directly from the source and confirms the original owner.
Web-based images can be protected by the Java script from Java Script Planet and when a cursor is moved over the protected image, a copyright-protected or similar image is produced (Provos and Honeyman 2003, p.44). Other programs support quick image encryption and decryption like SecurityPlus bySoftbyte labs and Cryptapix by Briggs Software. Those with the right to view hidden images are not able to access them due to encryption. Many copyright industries’ willingness to disseminate their works through the internet to make them available heavily relies on their ability to combat unauthorized copying as well as distribution activities that occur often through digitally networked settings (Johnson & Jajodia 1998, p. 33).
Conclusion
In this paper, I explored the issue of steganography in current digital media in terms of steganography techniques used in images, steganography techniques used in voice, virtual local area networks (VLANs), and the current issues in steganography, digital watermarking, and digital copyright. According to Kessler, the use and application of covert communication through digital steganography techniques as well as their derivatives continue to develop and increase at an alarming rate since there is a lot of information being exchanged on the internet whose owners need protection from unauthorized access and use (Kessler 2004).
From the above essay, it is evident that steganography plays a significant role in current digital media. In the modern use of steganography, the internet has acted as a link to many steganography tools and whose application continues to develop and become more sophisticated with technology (Bailey and Curran (2006, p. 78). As steganography continues to develop and become widespread in use in this modern computer era, so does the development of steganalysis techniques aimed at detecting hidden information. Many steganography techniques are not robust enough to counter attackers and steganalysis which call for evaluation and development of new methods (Peticolas et al. 1999, p.1078).
List of References
Bailey, K., and Curran, K. (2006) “An Evaluation of Image-Based Steganography Methods”, Multimedia Tools and Applications, 30 (1): 55-88.
Bender, W., Butera, W., Gruhl, D., Hwang, R., Paiz, F.J., and Pogreb, S. (2000) “Applications for Data Hiding”, IBM Systems Journal, 39 (4): 547-568.
Huang, Y., Ke Zhou, R., Jiang, H., Jin-Liu G., and Dan-Feng, R. (2009) “An M-Sequence BasedSteganography Model for Voice over IP”, Proceedings of the 44th IEEE: International Conference on Communications, 3(2):1–5.
Johnson, J., and Jajodia, S. (1998) “Exploring Steganography: Seeing the Unseen”, IEEE Computer, 31(2): 26-34.
Kessler, G. C. (2004) “An Overview of Steganography for the Computer Forensics Examiner”, Forensic Communications, 41(7): 34-43.
Mazurczyk, W., and Lubacz, J. (2010) “LACK – a VoIP Steganographic Method”, Journal of Telecommunication Systems, 45 (2):153–163.
Petitcolas, F., Anderson, R., and Kuhn, M. (1999) “Information Hiding – A Survey”, Proceedings of the IEEE, 87(7): 1062-1078.
Provos, N., and Honeyman, P. (2003) “Hide and Seek: An Introduction to Steganography”, IEEE Security and Privacy, 01(3): 32-44.
Schneier, B. (2000) Secrets & Lies: Digital Security in a Networked World, Toronto: John Wiley & Sons Publishers.
Varadarajan, S. (2006) Virtual Local Area Networks. Web.