Definition of TCP/IP
TCP/IP is an abbreviation for the Transmission Control Protocol/ Internet Protocol. TCP/IP is often regarded as a protocol matching set that was named subsequent to the pairing of dualistically essential protocols namely, IP and TCP. Thus, it can be defined as a primary communication element applicable through the internet.
It represents network protocol sets that offer support to networked computers to easily link up with the others. TCP/IP which is a universally known internet protocol suite is comprised of sets of layers whereby every layer is in charge of a specific network task while at the same time offering specific services to the upper layer. Internet Protocol Suite was first developed by the Defense Advanced Research Projects Agency (DARPA) in the fiscal 1970s.
Applications and uses of TCP/IP
Basically, TCP is commonly applicable during the transfer of data files and emails. The lower layer protocols of the TCP/IP functions at levels which are adjacent to the user and handles abstract data. IP and TCP became the initial protocols to be well-defined under the Internet Protocol Suite standard.
It is as a result of these protocols that the name of the protocol suite materialized. Conversely, the Transmission Protocol Control functions on the internet protocol suite known as the transport layer where it offers the networked computers with dependable facilities for communication. As a network protocol, IP is used to communicate data above packaged switch network. IP facilitates the transfer of diagrams founded on the IP network hosts addresses while operating on the protocol suite internet layer.
In the TCP/IP protocol pile, the highest level protocols are the application protocols. In fact, the application protocols are the visible user interface to the protocol suite of the TPC/IP and always communicate with other internet hosts applications. Each application protocol possesses features similar to others (Helmig n.p.). The features which exemplify their uses and applications are as follows:
TCP/IP protocols are applications transported and standardized with the products of TCP/IP or user written applications. The protocol suite for TCP/IP incorporates application protocols namely internet mailing system called Simple Mail transfer Protocols, and collaborative terminal telnet which allows admission into the remote internet hosts. These application protocols either use TCP or UDP as transport mechanisms. TCP offers connection oriented, reliable streams, flow control enabled and congestion friendly protocols.
As a peer to peer link leaning protocol, TCP has neither subordinate nor master correlations. Nevertheless, for communication purposes, the application normally draws on the server/client model. Servers are applications in TCP/IP which provide requisite services to the internet consumers.
Users only need to invoke customer application segment that in turn creates requests for specific services and send them to the application server segment via the transport vehicle, TCP/IP. The program (server) accepts requests, execute the requisite services and propel the outcomes back in form of reply.
Any server in the TCP/IP often handles multifaceted requesting customers and requests simultaneously (Panko 267). Therefore, it is apparent that TCP/IP has been widely used in server and clients models and in the provision of access to various other networks via gateway, bridge and router.
Standards for TCP and IP
TCP/IP has been widely recognized by users and developers alike due to its everlasting regeneration and integral openness. Similar facts hold true for the open communication network, internet. Nonetheless, such openness can certainly become helpful or harmful if there are no controls.
Even though there no general bodies which could govern the issuance of internet regulations and directives, there are mutual cooperation control. Under the organization and management of Internet Architecture Board (IAB), the Internet Society (ISOC) is mandated to standardize the internet community. From these organizations both TCP and IP are regarded as standards (Cisco Networking Academy 91). That is, the TCP as a standard is denoted by RFC 793 while IP is represented by RFC 791.
RFCs are numbered serially as they are issued. After a document is consigned an RFC number and issued, that number is certainly not reprocessed, even if the RFC is reviewed. In this respect, there has not been any question of having the most current versions of a specific RFC. Currently, RFCs are numbered up to 1609.
The term RFC is an incongruity. While most RFC biographers certainly will not mind if you give your views about the article, RFCs habitually are not actually demanding for any comments at all. In fact, they are descriptions or statements. There are three types of RFCs: Informational, which offers beneficial information; Experimental, which describes an experimental protocol and Standards Track, which stipulate Internet standards path protocol for the entire Internet community.
How TCP/IP protocol works
TCP/IP comprises of layers while each and every layer plays a significant role of carrying out some processes on the received data. After the operations have been performed, the data is passed to the advanced layers. Every protocol layer handles specific issues that are linked with data transmissions and at the same time rendering particular services to the developed layers.
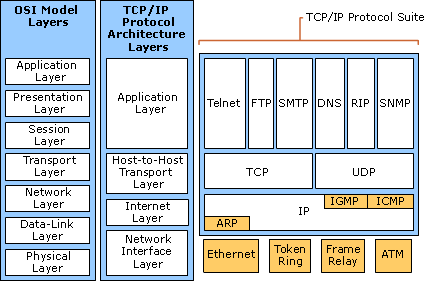
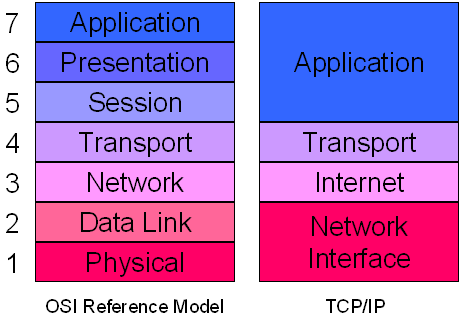
A detailed TCP/IP description is illustrated by the reference model in the appendices (Architecture diagram). The functioning of the protocol can be gauged via looking at the protocol layers of TCP/IP.
The protocol layers of TCP/IP
TCP/IP is actually sculpted into layers just like any other networking software. The layered sign gives rise to the protocol stack term, denoting the protocol suite layers. The TCP/IP protocol suite can be positioned using the stack protocol against other network systems including Open System Interconnection (OSI) and the System Network Architecture (SNA) model. The protocol stack divides the communiqué software’s into various layers.
Thus, allowing for the capacity to generate alternate implementation layers, simple code testing and implementation as well as division of labor. The implemented layers communicate with any other layer that falls either below or above through the abridged interface (“How TCP/IP Works” par.1). Layers in this regard offer services for any layer that falls right above it by utilizing services tendered by any layer that is underneath.
The four architectural layers that allow TCP/IP model to properly transmit data include transport, network, application and the internet layers.
Transport layer
This layer offers end to end transmission of data. This is possible as it can deliver data from a particular application to a specific distant peer. There is simultaneous support for several applications. TCP is the most applicable transport protocol layer. TCP allows for flow control, duplicate data suppression, link-oriented dependable data transfer and congestion control.
User Datagram Protocol is another component of the transport protocol layer. This protocol allows for unreliable, best effort and connectionless services. Any application that uses UDP as its transport protocol must therefore craft its specific control, end to end integrity and flow control. UDP is utilized by applications which can endure some data loss and require a quick transport mechanism.
Application layer
Programs using TCP/IP protocol to communicate offers this type of layer. It is an operator process associating with other processes normally under the unlike hosts. Notable examples of the application layer are the File Transfer Protocol (FTP) and Telnet. The interfaces amid the transport and application layers are well-defined by the number of sockets and ports.
Network interface layer
This layer is similarly referred to as data link layer. It is the interface that leads to the concrete network hardware. In fact, the interface might or might not offer dependable transfer and might consequently be stream or packet oriented. In this regard, TCP/IP protocol seems not to stipulate the protocols. However, it may use nearly several network interfaces that are accessible, particularly those that demonstrate IP layer flexibility. Examples include SNA, FDD, IEEE and ATM.
Internetwork layer
This layer is similarly dubbed as the network or internet layer as it offers virtual internet network images. The layer plays a critical role of shielding upper planes from the underneath physical system architecture.
In this layer, the IP is deemed as an imperative protocol. It does not accept any dependability from the subordinate layers given that it is a connectionless protocol. Functions such as error recovery, flow control and reliability are not proffered by the IP and must thus be offered at advanced levels (“How TCP/IP Works” par.4).
In summary, every layer is made of protocol sets that are bound to function at that particular layer level. The available network or connection layer protocols play the role of attaching the network nodes. The transport protocol layer manages the data packet transmission amidst the host destination network and the source. Conversely, the internet layer comprises of methods, specifications as well as protocols which are drawn on when transporting packet data through the established networks (Torres 2).
The uppermost TCP/IP layer is the application layer which unswervingly interacts and also connects with service applications. It is hence true that TCP/IP operates in each and every communication level situated within the network components. Sincerely, it emerges as the core and hub of the communication network.
Components: The required Hardware and software devices
The traceable components of the TCP/IP include: SYSTCPIP applicable in TCP/IP internal incident tracing; SYSTCPIS used to detect and trace the TCP/IP intrusion services; SYSTCPRT used in the protocol for OMPROUTE tracing; SYSTCPRE used in the TCP/IP to resolve tracings and SYSTCPDA applied in an IP package tracing.
The Serial Device Server is equally a TCP/IP protocol component. Other trace selections seem to be solely and habitually applied because of the advanced or IBM support personnel instructions (IBM par.1). However, SYSTCPDA packet trace is the most essentially applied component trace.
TCP/IP Architecture
The name TCP/IP protocol suite comes from the notable two essential protocols namely the Internet Protocol (IP) and the Transmission Control Protocol (TCP). Internet Protocol Suite is the name that is often used. The architectural model for TCP/IP is comprised of internetworking, and the already discussed TCP/IP protocol layers and the applications.
Internetworking
TCP/IP was mainly designed to build networked interconnections dubbed as the internet or internetwork which offers global communication amenities over a diverse physical network. Such internetworks are beneficial in that they enable communication amid hosts located in diverse networks that are probably disjointed by large geographic areas. The phrases internet and internetwork emerged from the interconnected network phrase. Internet as used in TCP/IP has numerous network groups including local networks, commercial networks, backbones and regional networks.
These networks are usually limited in size based on the maximum geographic area that can be spanned by a given network, the total number of users belonging to the networks, and network applicability in some settings. Ethernet for instance, is integrally partial with respect to geographical scope. As a result, the capacity to hierarchically interconnect volumes of networks in organized fashions facilitates the communication between two hosts that belong to such internetwork (“How TCP/IP Works par.2).
TCP/IP internetworking also creates standardized communication mechanisms abstractions which are offered by each kind of network. All physical networks have their own dependent technological communication interfaces known as programming interfaces which offer primitive or primary communication functions. From its structural composition, it appears that TCP/IP proffers communication services running amid user applications and the programming physical network interface.
This independently supports joint interface applications devoid of the basic physical network. Therefore, it is apparent that the physical network architecture is concealed from both the application developer and the user. The application just requires the standardized communication abstraction code so as to purpose under any kind of operating platform and the physical network.
From the diagrams in the appendices, it is clear that any interconnection between two networks is only possible if the computers are attached to each of the available networks. This will ensure that packet data will be easily forwarded from a given network to another via a router. In most cases, the IP router term is applicable given that the routing purpose is a component of IP segment of the Transmission Protocol Control/ Internet Protocol suite.
This is well-illustrated by the protocol layers of the TCP/IP diagram, found in the appendix. However, to easily recognize the internetwork hosts, every host must be consigned an IP address (Helmig n.p.). If a host possess numerous networked interfaces or connectors such as routers, all interfaces ought to have inimitable IP addresses. Thus, the IP address is usually made of two components:
IP address = <host number> <network number>
Within the IP address, the network number segment distinguishes the network system inside the internet. The central authority plays the significant role of assigning the network number while ensuring that it is distinctive all through the internet. A segment of the IP address host number is assigned by an authority residing with the controlling organization which identifies the network number.
Strengths and weaknesses of the TCP/IP protocol
TCP/IP has numerous strengths and weaknesses. These are as explained below:
- TCP/IP Strengths: TCP/IP has the capacity to check errors, it can simultaneously transfer data and is considered very reliable, higher volumes of data can be held by the TCP/IP at once, it allows internetworking and has the capacity to establish connections amid various servers or computers.
- TCP/IP Weaknesses: The Transmission Control Protocol/Internet Protocol (TCP/IP) suite can occasionally be slow while the protocol has a very multifaceted structure or setup.
Conclusion
Generally, the Transmission Control Protocol/Internet Protocol (TCP/IP) suite has developed into a standard de-facto for computer communications in the current interacted universe. The permeating application of a particular network standard seems to have actually given rise to a far-fetched reliance on any application that is supported by the protocol. In the contemporary society, people utilize the Internet and the TCP/IP protocols not merely for information and entertainment, but equally in conducting everyday businesses.
Even though the protocol has manifold strengths and weaknesses, it plays the critical roles relating to gateway, routing, internetworking, bridging besides acting as a server and clients model. Hence, it is true that TCP/IP operates in each and every communication level situated within the network components. It emerges as the core and hub of the communication network.
Appendices
Works Cited
Cisco Networking Academy. IT Essentials: PC Hardware and Software Lab Manual. McKinney, TX: Cisco Press, 2010. Print.
Helmig, Johannes. “TCP/IP Basics”. 2002. Web.
How TCP/IP Works. 2003. Web.
IBM. “Tracing TCP/IP components”. IBM Corporation. 2010. Web.
Panko, Raymond and Panko, Julia. Business Data Networks and Telecommunications. New Delhi, India: Pearson Education, Limited, 2010. Print.
Torres, Gabriel. “How TCP/IP Protocol Works”. 2007. Web.