Introduction
Considering the current scenario of things in the world, it is not wrong for one to argue that, everything existing currently; globally, owes its origin from technology. This is because; technology drives every aspect of human life ranging from simple home cores, for example, cooking and washing, to the most complex technological innovations in communication systems. In addition, to a larger extent, the quality of life depends on the nature of technologies embraced by society. This is the case primarily because currently, even the nature of health systems depends primarily on technology; communication systems depend on it; time and program scheduling programs in all spheres of life depend on it; working systems depend on it; to some extent quality, education delivery depends on it. Hence, considering this and many more, for sure technological advancement forms the backbone of every aspect of life. On the other hand, although such innovations have many associated advantages, it is important to note that, like any other innovation effort, technology has its own disadvantages or associated negative impacts; the most affected being the information technology sector.
Communication is one of the most important elements of any human interaction process, which primarily depends on the nature of available communication systems. With many innovations in the information technology sector, communication systems have received a great boost; this being a sector that has had the biggest share of technological innovations. Such innovations are clear in the internet technology whereby, it plays an important role not only in communication but also in other sectors of life that endeavor to solve human problems, for example, space studies, education, and medicine. Individuals who utilize such innovations for goodwill can surely attest that such innovations have had great impacts on their daily lifestyles. Although that is the case, still there exists another class of individuals who have taken advantage of the much technological advancement in the information technology sector to defraud; perpetrate crime, hence, taking other individuals’ belongings unknowingly through “witty” procedures.
That is, currently, there exist many internet swindles, primary identity theft cases, which have caused many losses not only to individuals but also to ‘big” organizations or business units. It is important to note that, apart from monetary gains, the majority of defrauders also target other organizational information, which may be crucial to their personalized-egocentric needs (Barnes, 2010, p. 1). Therefore, compounding these factors, it is very essential for any individuals connected to the internet, or whose operations depend on the internet to ensure they safeguard their systems from defrauders using required programs. In addition, it is very important for individuals who use the internet as their main communication channel to critically scrutinize the nature of messages they receive before responding to invitations, which in most messages seem very pleasing at first sight. On the other hand, it becomes very crucial, for governments to put in place mechanisms of catching defrauders, through the implementation of appropriate reporting mechanisms. This paper will discuss concepts of identity theft via the internet whereby it will critically analyze how individuals perpetrate the crime, and how organizations or organizations can avoid being victims of the many scams that are all over the internet.
Internet Identity Theft
There exists a close correlation between the current rate of crime and technology. That is to say, many technological developments; more so in the information technology sector, have “given birth” to new forms of crimes, which previously never existed. This is because; currently the physical contact thieving process has undergone a transformation whereby, individuals can use internet communications to defraud anybody of anything they want through the use of their personal information. This to a larger extent has made it hard for most law enforcement agents to deal with some forms of crime; because of the un-availability of the physical presence of some crime perpetrators. In addition, because of a lack of knowledge by individuals on the nature of internet crimes, the majority of individuals discover that somebody has defrauded them when it is too late hence, making it hard to arrest and prosecute such crime perpetrators. This nature of crime involves primarily faking of identity whereby, an individual impersonates some organization’s identity or another individual identity for gaining purposes; primarily through cheating mechanisms. This form of crime is so complex and serious in that most innocent individuals suffer for offenses they never committed primarily because somebody else impersonated their identity. As reported in the Cnet news, with every dawn the rate of this form of crime keeps on increasing as more cases of identity defrauding occur daily in not only America but also in other parts of the world. For example, in the year 2005-2006, reported cases of the crime totaled fifteen million, which was a double-figure in the year 2003.
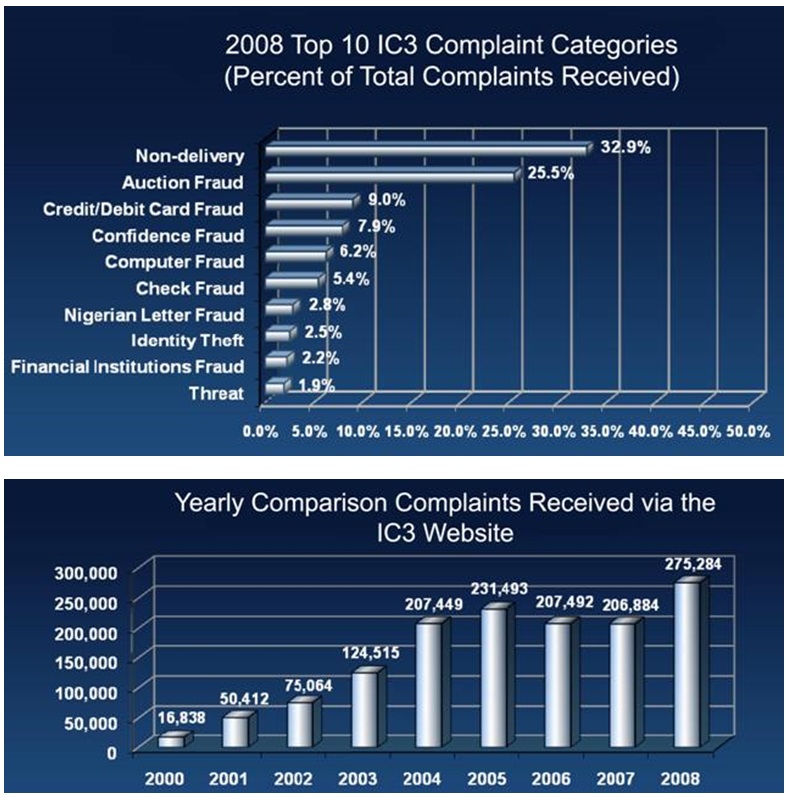
Monetary losses associated with this period amounted to almost $ 3,257 million in the year 2006, a figure that had doubled up from the figure reported in the previous year that is $1,408 (McCarthy, 2007, p.1). The figures have kept on increasing tremendously from that time because, in 2008, the number of such cases reported to only the Crime Complains center amounted to two hundred and seventy-five thousand, two hundred and eighty-four. This was a sharp increase from the previous figure, which was approximately two hundred and six thousand, eight hundred and eighty-four (Internet Crime Complaint Center: IC3, 2009, p.1). The scenario is not different in the UK primarily because, due of the increased numbers of individuals who had interconnection in the country. Figures from the UK show that such a crime occurs every ten seconds currently. In 2008 only more than 3.6 million cases of crime occurred whereby losses resulting from the same amounted to more than 52.5 sterling pounds in the online banking sector (Fafinski & Minnasiam, 2009, p.1-2). With the onset of 2010, the case became more serious globally, because in 2010 as reported by the Javelin Strategies, there was an eleven percent increase from the cases it had received in the year 2009 with souring amounts of losses (Identity Crime Labs, 2009, p.1). Considering these figures, these forms of crime are getting worse each day with more innocent people and organizations losing millions of dollars each passing second.
Cyber Crime Statistics
Forms of Internet Identity Theft
In most common life scenarios, it is very hard for individuals to discover that they are being defrauded via the internet. This is because, the majority of invitations or offers by defrauders are promising; hence, most individuals give them a try without confirming the source of such information. Because of the promising nature of such invitations, the majority of individuals will give out some of their personal details, which are primary elements required by any criminal, for impersonation purposes. Two main forms of these crimes exist in nature namely phishing and pharming. These two types take many forms, which include account takeover, deceitful business dealings, credit card schemes, and criminal identity cloning. Although there seem different ways in which perpetrators of this offense conduct the crime, it is important to note that, acquiring somebody’s personal information is the primary determinant of the successful perpetration of this criminal offense. It is important to note that, the majority of internet frauds are in form of phishing lures. Phishing perpetrators usually have their personal connecting websites; where individuals have to fill in some details as an acceptance confirmation. The majority of such links will be deceitful whereby, the majority of them in most cases have a close resemblance to certain big organizations’ websites. This is very common in many online scenarios in that, most of such offers are in form of pop up or email posts that require immediate feedback (Myers & Jakobsson, 2007, pp. 1-4).
Sometimes for perpetrators of this crime to avoid the owners easily discovering what is happening, the majority of them will open new accounts using the details in their possession hence, conducting business transactions freely with minimal chances of discovery within a specific time limit. This case occurs in most pharming cases whereby, criminals ensure they obtain information of somebody’s internet service provider hence granting them a chance of re-directing all the information of the main site to their newly acquired or created sites under the same name, using personal information entered in the wrong site, criminals will use such data to gain entry to the right website hence conduct whatever transaction they want to obtain (Spam Laws, 2009, p.1).
In account take over cases, crime perpetrators primarily use somebody’s account details to engage in specific business transactions, for example, purchases. The most common form of these theft cases is website cloning. In this case, most thieves use a replica of a specific organization’s account; conduct vending on behalf of the organization; get rewarded, but no purchased stuff will be available for delivery; the entire transaction being a hoax. This like a scenario occurs mostly in auction dealings whereby, individual in the name of a certain auctioneering organization will post good-offer adverts on the internet, and because of the encouraging nature of such offers, most individuals will be quick to ay for them without remembering to confirm the credibility of such firms. The second and also very widespread form of this crime involves conducting deceptive business dealings. The majority of such cases involve criminals taking orders in the name of the owner of the details they are possessing whereby; they will ultimately receive the shipment of any delivered merchandise using the impersonated identity. This is one of the most complex forms of this type of crime in that, the majority of crime investigating centers associate it with extreme damages when it comes to property loss due to large property transfer (Smith, 2005, pp.3-5).
In some scenarios, some criminals use a certainly created virus to retrieve information from individuals’ computers, this case occurs mostly in most unsecured websites through such individuals reading an individual’s browsing history or using spyware to obtain all the information stored in one’s data banks.
Preventing Internet Identity Theft
Considering the nature of losses that may result from accepting and replying to emails that one is not very sure of their credibility or origin, it is very important for all individuals to avoid giving their personal information online. For example, considering what happens in phishing, it is very important for all individuals to avoid giving out their secret codes or login information because the likelihoods of entering giving out personal information to the wrong people are high. Some sites may prompt one to save their passcodes for memory purposes. Regardless of the site, it is advisable for individuals to always reject those like offers because the current condition of most internet protocols have no methodologies of determining genuine company sites.
In addition to avoiding giving out some important personal information online, it is advisable for individuals to ensure their internet browsers are safe and sound for sending any data, in cases where the only available option is to use the internet. The common way of ascertaining the safety of any connections is by use of appropriate software programs, which will ensure any information leaving the computer is either in an encrypted form or goes through the required path. To avoid cases of attack by malicious spyware, it is important for individuals to have some running programs, which will act are scrutinizers of any incoming messages. On the other hand, it is important, for all individuals to delete some crucial personal data from the machine storage devices, which should have a mechanism of tracking cookies and the internet cache (Emigh, 2005, pp.14-28).
For organizations, is advisable for them to always keep track of their transactions. This is because, some employees may the main perpetrators of such online crimes hence, the importance of establishing a correct communication and monitoring system when it some to employees’ affairs. Consumer protection is another major point that an organization’s management should take note of to ensure they protect them from any defrauders. Such attempts are only achievable through an organization establishing a security system, which will ensure all employees, organization, and customers’ information receives the desired protection from password crackers and other internet defrauders (Collins, 2005, pp. 55-82).
Conclusion
In conclusion, the losses associated with internet identity are many. In addition, due to the ever-changing trends and mechanisms used by individuals to perpetrate the crime, it is advisable for any victims to immediately report to the authorities such cases, for governments to be able to take quick action. On the other hand, because it is sometimes very hard to determine genuine internet offers, it is important for individuals to take precautions, and incase they suspect that such offers are hoaxes, it is important for them to report to required sites or authorities. This is because; there exist laws that help to deal with the crime, and still currently such laws are being improved, for effectiveness, by the congress (Smith, 2005, pp. 5-6).
Reference List
Barnes, C. (2010). Internet contributes to the rise of identity theft, FTC says.Cnet News. Web.
Collins, J. M. (2005). Preventing identity theft in your business: how to protect your Business, customers and employees. New Jersey: John Wiley and Sons. Web.
Emigh, A. (2005). Online identity theft: phishing technology, chokepoints and countermeasures. Identity Theft Technology and Countermeasures. Web.
Fafinski, S., & Minassiam, N. (2009). UK cyber crime report 2009. Invenio Research. Web.
Identity Crime Labs. (2009). Identity theft statistics 2010.Identity Crime Labs. Web.
Internet Crime Complaint Center: IC3. (2008). Internet Fraud, Scam and Crime Statistics – 2009.IC3. Web.
McCarthy, C. (2007). Study: identity theft keeps climbing. Cnet. Web.
Myers, S., & Jacobsson, M. (2007). Phishing and countermeasures: understanding the increasing problem Electronic identity. New Jersey: John Wiley & Sons publication. Web.
Smith, S. M. (2005). CRS report for congress: identity theft; the internet connection. CRS. Web.
Spam Laws. (2009). What is pharming?Spam Laws. Web.