Introduction
The objective of this report is to discuss the issues and solutions thereof that arise in the evolution of enterprise system architecture as a result of organization and business growth. The decentralization of legacy monolithic centralized enterprise network architecture has evolved into distributed client-server architecture with a TCP/IP network backbone. Processing tasks and databases reside on different computing platforms; these servers are connected to the enterprise WAN/LAN. The clients on user personal computers connected to the enterprise WAN/LAN can retrieve data from the servers. The distributed architecture requires cooperated computing between processes and databases located on different servers in order to accomplish the task.
The distributed architecture with cooperated computing has resulted in the replacement of mainframe computers with small hardware platform domains. These domains have a network backbone and are the repository of mission-critical corporate data (Nezlek, 1999). The appropriate and coordinated enterprise architecture has the following benefits (Nezlek, 1999):
- Reduction of undesirable redundancy of system components,
- Appropriate allocation of information processing functions to platforms,
- Meaningful allocation of computing resources to organization locations and
- Ability to share information resources across organizational entities at a manageable cost.
Enterprise System Evolution Issues
The following issues have been identified and discussed in this report:
- The organization of network resources must provide management control automation to prevent conflicts, to avoid redundancy of data for system integrity and for automation of management control.
- The legacy systems must be utilized to reduce the equipment cost. The new system architecture must, however, ensure that the use of legacy systems must not increase system operational costs.
- The above two points must also consider the security of network resources and information processed and stored on these resources.
- The system architecture must provide fast, secure and optimized service to the organization employees and external customers.
Network Resource Organization
The structuring principles for systems architecture to enable management control are (Boutaba, 1995):
- Identify domains for grouping of resources in order to enable the control of resources and delegation of authority for control. The authority has to be assigned for peer-to-peer conflict resolution and sharing of resources.
- Identify the control policies for resource and activity management; the policies must be independent of the heterogeneity of resources.
The organization network resources are grouped into domains. Domains are identified based on the function and physical location of the systems. The management responsibilities are then assigned for the independent control of network resources within the domain.
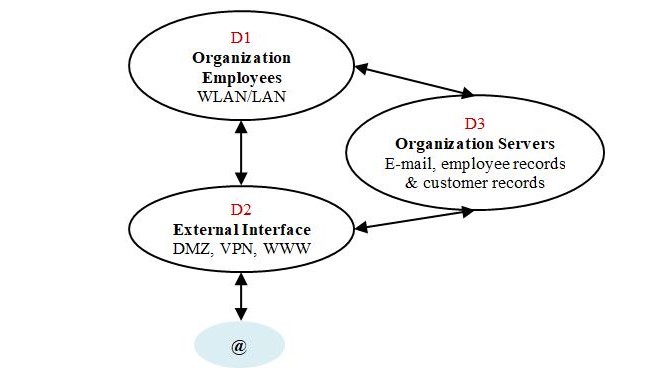
Enterprise Network Domains
Three domains have been identified; each domain may have sub-domains that are managed in a similar fashion as the parent domain. Each domain has the following interfaces:
- An external management interface to receive external service requests such as configuration requests, peer-to-peer conflict resolution and remote management.
- An external user interface to authenticate and authorize users for access to network resources within the domain.
Enterprise Network Client-Server Architecture
By configuring a mission-critical domain, the optimum utilization of resources is achieved, and information sharing and resource maintenance costs are controlled with access control. The design of architecture evolves based on the requirements that determine the technology that shall be used for selecting and configuring the network resources such as file servers (CMS, DMS), processors (CORBA and database servers), database design and bandwidth of physical network link. The development of technology-independent architecture model that shall integrate the newer system with legacy systems requires that no assumption is made about existing technology. The methodology used is (Nezlek, 1999):
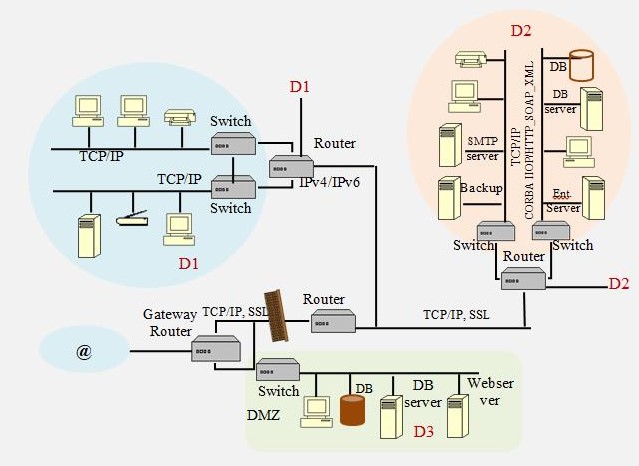
Enterprise Network Architecture
- Identify the business processes,
- Identify the application and data needs for each business process,
- Convert imprecise and inconsistent user requirements into atomic requirements in order to standardize requirements,
- Identify resource requirements for user requirements; the resources may be a flat-file system, RDBMS, OODBMS, etc.
- Allocate resources for higher priority requirements, such as:
Minimization to reduce resource redundancy and improve data integrity
Localization to improve application performance with resource proximity to the user.
In the latter case, there is an inherent data transmission cost in order to ensure the concurrency of multiple instances of data components. The selected resource allocation strategy shall impact the QoS (Quality of Service) provided to the users.
- The network capacity planning simulation tool is used to determine resource processing power, memory requirement and network bandwidth based on weighted user requirements. In order to reuse the legacy systems effectively, the technical capacities of these systems may be considered in simulation models.
Legacy system reuse
The organization network resources are traditionally connected with Ethernet cables, WLAN is a new technology, and transition shall require installation of wireless NIC or new laptops, Wireless Access Points (WAP) and securing office buildings from wireless hackers.
An organization that transitions from IPv4 to IPv6 network supports dual-stack on routers in order to provide addressing independent mode interface to personal computers during the transition from IPv4 to IPv6.
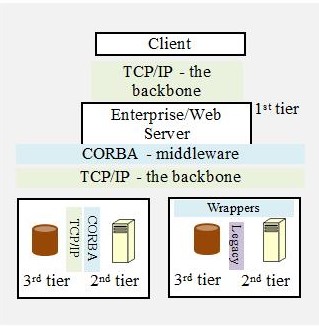
Enterprise 3-tier Architecture
The existing servers may be used in the new architecture model where the performance of legacy technology is not a major issue. The legacy systems are integrated into distributed 3-tier architecture by introducing wrappers on the legacy server (2nd-tier) to integrate into distributed architecture middleware (Juric, 2000). Wrappers shall encode/decode data in compliance with middleware transport protocol (e.g. IIOP, SOAP-XML-HTTP).
- One of the simulated architecture models is adopted for implementation based on the resource acquisition cost, migration effort, capacity etc. The selected architecture may be implemented with alternative technology in order to reuse legacy systems.
- The choice of middleware (OMG DORBA, Microsoft COM, and Java RMI) and modelling tools for application development influences the network resource requirement for application deployment.
Network Security
The organization information security policy document must identify the network resources as information assets and assign them the necessary security level. The vulnerabilities of assets are listed by Myerson (2002), also mentioned in the report are data sheets to record the threats and their impact. The overview of security steps implemented is:
- Mention the security policy for all network resources in the information security policy. Conduct security audits to comply with federal requirements to ensure that policies are implemented and are up-to-date (Walton, 2002).
- Secure personal computers with username & password, firewall and anti-virus software.
- The online access to different segments of the network is controlled by the configuration of the access list on the segment gateway router. SSL connections with data encryption are established between client and 1st-tier server to ensure data security.
- The access list for username & password authorization and authentication is configured on the 1st-tier server. The access list shall include necessary per-user permissions for the respective services. Thus single username and password may be allocated to users for access to all services.
- The organization web server is located in the De-Militarized Zone (DMZ); this zone is located behind the organization gateway router that does not require any authorization. For the privileged data that requires a username and password authentication, the SSL connection is established with the internal database server in D2 that is located behind the firewall router.
- For a wireless office, it is necessary that rogue WAP are eliminated, and office building is secured from external wireless network hackers.
APPENDIX
3-tier client-server architecture
The 3-tier client-server architecture consists of the following components:
User interface: This is a thin client where data processing is not required on a user computer. Data processing is a decision-making process; encoding data into XML-SOAP-HTTP messages is not data processing. This is a fat client where decision making based on data is required on the user computer.
- 1st-tier: (Presentation) This is the server that receives a request message from the client and performs decision making such as decode messages and determine what action is to be taken. Based on the requested action, file server or database server access may be required. This server also performs user authorization and authentication to determine the credentials of the user.
- 2nd-tier: (Application) This is the server that shall process the data stored on the 3rd-tier server in order to perform the task ordered by the 1st-tier server. This activity involves a read-write operation on the 3rd-tier server.
- 3rd-tier: (Data) This is the server that stores data that is processed to perform the user task.
In figure 2, the web user accesses the website and all data input to an online form is received by the 1st-tier web server in DMZ. The request is forwarded to a 2nd-tier DB server in DMZ or in domain D2 based on the action required. The associated 3rd-tier DB storage is located in DMZ and domain D2, respectively.
For organization employees, the 1st-tier decision making and authentication authorization is performed by the Ent. (Enterprise) server in domain D2. This server then forwards the request to respective servers in D2. The architecture illustrated in figure 2, uses CORBA middleware in two steps:
- Between 1st tier & 2nd-tier, the CORBA middleware creates an object list for all other servers connected to the backbone in this domain. This server access list contains access privileges for 2nd tier servers and brokers requests for access to 2nd-tier servers.
- Between 2nd tier & 3rd tier, the CORBA middleware creates an object list for entities stored on 3rd tier storage devices. The Object Request Broker (ORB) operates on these entities.
References
Boutaba, Raouf. & Znaty, Simon. (1995) An Architectural Approach for Integrated Network and Systems Management. ACM SIGCOMM [Internet], 25(5).
CORBA. OMG.
Gokhale, Aniruddha., Schmidt, C. Douglas., Natarajan, Balachandran. & Wang, Nanbor. (2002) Applying Model-Integrated Computing to Component Middleware and Enterprise Applications. Communications of the ACM [Internet], 54(10).
Juric, B. Matjaz., Rozman, Ivan., Hericko, Marjan. & Domajnko, Tomaz. (2000) Integrating Legacy Systems in Distributed Object Architecture. ACM SIGSOFT [Internet], 25(2).
Myerson, M. Judith. (2002) Identifying enterprise network vulnerabilities. International Journal of Network Management [Internet], 12(3) pp. 135-144.
Nezlek, S. George., Jain, K. Hemant. & Nazareth, L. Derkek. (1999) An Integrated Approach to Enterprise Computing Architectures. Communications of the ACM [Internet], 42(11).
Walton, P. Jinx. (2002) Developing an Enterprise Information Security Policy. ACM [Internet]
A Guide to Harvard Referencing. Leeds Metropolitan University.