Executive Summary
As new services grow, the networking system is getting more complicated and making it more complex and harder for carriers to maintain. When problems pile up it becomes quintessential for the networks to uphold a fundamental transformation. The following report emphasizes on the network assessment, solution customization and solution implementation in regard to the retrenchment and security plan highlighting both the software and the hardware requirements.
Introduction
The following report deals with an in-depth analysis about the network security fundamentals of a non profit organization which had employed an external contractor to build an effective networking system in the organization as per the pre determined requirements lay down and well communicated to the contractor. However it was found that the contractor did not install the network as specified, instead has fixed in a complex but secure solution in order to acquire personal gains in the form of future employment after the contract ends through “maintenance”.
There has been identified a long list of both human resource as well as technical issues due to which the management has decided to retrench the contractor, however the managerial decision needs to be backed up through a detailed retrenchment and a security plan along with an audit plan to verify that the current systems are secure and free from Trojans, other malware or covert channels and a sound plan to build a secure solution including software and hardware requirements so as to ensure a smooth, secure and effective running of the organizations networking system.
Retrenchment Plan
In order to safeguard the network security and the infrastructure from the external contractor of the organization, a draft for retrenchment and initial security plan needs to be chalked out focusing both pre and post retrenchment. To accomplish the objective one need to analyze the loopholes through which the contractor can gain access to the confidential information as well as create problems in future. As stated in the case study the contractor is now completing the job “remotely” and is accessing the sites from his laptop which he has been using for all of the configuration and installation and holds all the license keys for all of the new software which may certainly create problems in future. To combat the threat posed a retrenchment plan must be encapsulated based on widespread consultation with workers and their representatives and should seek that reasons for dismissal are fair and transparent.
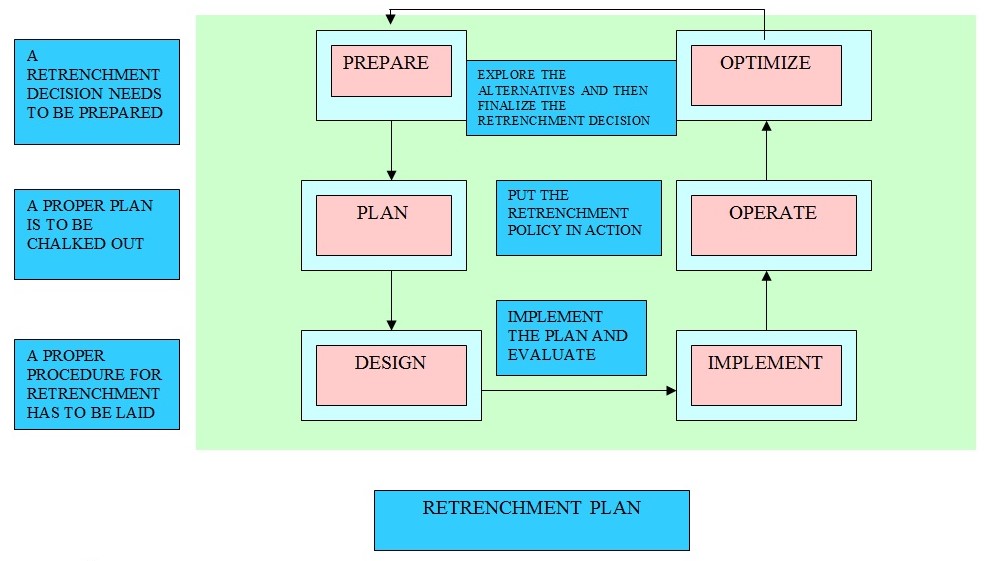
To secure the infrastructure a procedure needs to be followed; firstly the tools are to be prepared to effect the retrenchment, including an appeal or grievance mechanism. The performance of the contractor is one such reason for implementing contractor’s retrenchment. However, retrenchment should be adopted as a last resort (Good Practicing Note, 2004). All alternatives available must be fully exploited, as in the case it is mentioned that contractor has not worked as per the requirements. He can be warned initially before adopting the mode of retrenchment. As the contractor holds access to crucial data, it becomes utmost important to appoint a panel of experts who could take charge and understand the complex system environment created by the contractor in order to incorporate changes. Such action is crucial as retrieving information and blocking resources in order to make it inaccessible would require an in-depth understanding of the current system. As the contractor hold the coding of all software’s, it is essential for the newly appointed team to retrieve the licensing keys back and take charge because it is all an expensive affair.
Next step shall disclose in advance of the consultations and in writing all relevant information regarding retrenchment including, the reasons for the proposed dismissal, the alternatives thought off before proposing the dismissal and the reasons for rejecting the same, the time when the retrenchments is likely to take effect and other relevant information which needs to be imparted to the contractor pre retrenchment. The contractor shall be entitled to make representations on any relevant matter including why he shouldn’t be retrenched.
The post retrenchment includes settlement of dues towards the organizations, any past grievance against the firm including security issues need to be clarified or settled. The issues which are already identified in the past have to be meticulously analyzed and complete safety and system security need to be ensured in the future contracts.
As per the case the new experts group or an external contractor who would be given the charge must be properly communicated about the system requirements especially the infrastructural changes which need to be imbibed and have not been undertaken properly in the past, apart from them emphasize on complete documentation of every little aspect regarding the network system must be laid followed by regular monitoring and supervision of the data. The plan must ensure that before the post retrenchment is applicable, all past gateways must be closed or in other words all external openings through which the network data can be accessed should be prohibited. It should be taken into consideration that while appointing the new contractor, all norms must be clear which gives no scope of personal gain to the external recruit. A well-managed retrenchment process can help avoid a host of problems which an external contractor may create in the future because of his access to crucial company data and other software’s as well and result in better outcomes for the company, its employees, involving a wider perspective.
System Audit Plan
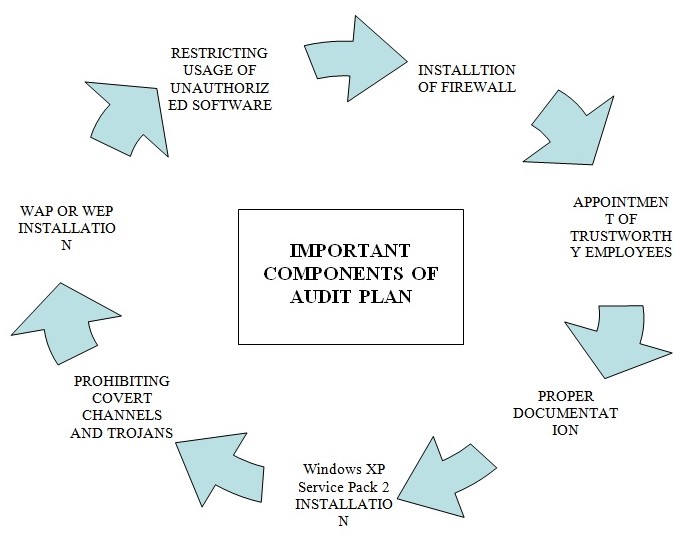
A system audit is a form of transaction record keeping and data collected is called an audit log. Audit plan needs to be framed for verification, that the current systems are secure and free from Trojans, other malware or covert channels. As the case study reveals that there is a wireless network installed at both sites but security is only via MAC address locking, no WEP or WPA, there is no firewall in existence apart from a very basic NAT at the Internet Gateway and there is absence of complete documentation as well, hence it can be stated that the security issues need a through verification of virus free systems.
The plan must ensure to check whether all systems are installed with Windows XP Service Pack 2 which incorporates many enhancements to try to protect systems from malware and other forms of attacks. One of its features is the Windows XP SP2 Firewall which enables users to decide what application can be communicated on the network (Majik, 2001). Another security enhancement of Service Pack 2 is better protection around executable code, to help prevent the propagation of virus and malware programs.
The code verifies the signing attempt, if a program is not signed by a trusted source then a user is notified of this and that user can allow or deny the program. It also prevents it getting affected from Trojan horse which is a program that does more than it is supposed to do, audit plan must incorporate to check the presence of a text editor that may set all files to be publicly readable in addition to performing editing functions.
A covert channel can expose information by some indirect and murky means while Trojan code can affect a system in a way that is not authorized (Cabuk, S., Brodley, C. E. & Shields, C, 2004). Hence, to safeguard against covert channels and Trojans, audit plans needs to check whether the programs are purchased from reputable sources, verifying the source code and its harmlessness, checking whether the programs have been pre evaluated or not, by inspecting all source codes prior to use, by controlling access and modification to codes once programs have been installed. Moreover it must be ensured that trustworthy and sincere staff is appointed on important systems. According to the specifications lay down by the NCSC In 1987, covert channels exceeding more than ten bits per second need to be audited by the TCB (Horenbeeck V M, viewed in 2008).
The audit checklist includes questions such as whether there exists any control against spiteful software usage. Whether the security policy does address on issues such as preventing and restricting usage of unauthorized software? Whether the system incorporates features to verify all warning bulletins and their accuracy? Whether Antivirus software is installed on the computers to check and isolate or remove any viruses from computer and is regularly updated to safeguard from the latest viruses? Whether all the traffic originating from unrealizable sources into the system are checked for viruses? Example: Checking for viruses on email, email attachments etc. positive feedback to questions such as whether there are controls in place to ensure that the covert channels and Trojan codes are not introduced in the system and are of utmost importance.
The audit plan needs to check on the confidentiality aspects confirming that information is available only to authorized parties. Proper authentication records are maintained by establishing the validity of a transmission, message or originator. Audit plan must focus on security threats such as browsing which may lead to searching from main and secondary memory for left over information , leakage may result in transmission of data to an unauthorized user from an accessible process, tampering can make unauthorized changes to valuable information, accidental destruction, masquerading and denial of services.
The audit plan needs to check Policies/procedures including acceptable use, password, training etc. the plan needs to monitor control such as operating system controls, application access restriction, network boundary via a firewall, VPN etc, advanced authentication for instance smart cards and tokens. Check on detection programs and regular penetration testing. Auditing of events such as process tracking can provide a list of processes created or attempted to create along with the duration of each process.
The audit plan should also focus on activities involving checks on operational systems that were a part of the original set up and the actual operating system installed on the machines in order to mitigate the risk of unwanted foreign interruptions. The audit must also guarantee that the access to system audit tools such as software or data files are completely protected from every possible disfigurement and manipulations.
An Information Security Management System including both the perspectives of software and hardware should be based on a business risk approach to establish, implement, operate, monitor, review, maintain and improve information security (CSI Security Solutions, 2008).
A Secure Solution Including Software and Hardware Requirements Plan
The organization must identify all network access points and verify that the safeguards for the work and individual systems are adequate and operational. The security includes wireless access points, network ingress and egress points, and network-attached devices.
In regard to the case study under consideration a plan is needed to build a secure solution including software and hardware requirements. To incorporate such a plan, the following steps must be included: Firstly the system security requirements must be identified especially focusing on infrastructural applications, information systems, business applications and user developed application. For instance in the case , the current solution used is Windows 2000 as the base server to run terminal sessions for all machines, all of the applications are installed on the server, and remote access to the terminal services is not currently possible , creation of another server named DBDEV is just not required , the two sites need to be created, WAP and WEP need to be installed, reduction of excess load needs to be undertaken, proper documentation of setup, accounts, users, policies and adequate backup are few security requirements which have been identified.
Next step in the execution of the plan involves specification of the security controls and requirements such as the new software packages required, the specific security controls which the information system should have, for example the installation of Windows XP service pack 2, anti virus programs, firewalls, mail scanner etc, thirdly to build a secure solution, security needs to be build in the application system by preventing the loss, misuse and alteration of user data.
Fourthly, input data validation needs to be built in the system to ensure that the input of business transactions is correct and appropriate. Fifthly, processing checks and controls have to be incorporated by detecting data corruption using run to run controls. Sixthly, cryptographic techniques and digital signatures should be used to protect important information along with the risk assessment to determine the extent of protection to be extended.
The organization’s system files must be protected. Changes to operating system must be reviewed. Outsourced software development must be sternly controlled. The organization needs to keep track of the hardware bought at regular intervals, like in the case study it is clearly evident that a proper plan out has not been executed as the Linux based machine that has a MySQL instance and appears to be partway through a migration of the existing data is not accountable and the hardware also does not seem to have been bought by the organization. Such loopholes should be mended.
The final stage of the plan should focus on the verification of the complete documentation of the setup, list of accounts, rights, usernames, network map, documentation policy and appropriate back up in order to build up a secured solution and a smooth running of the network security system.
Apart from the above mentioned steps, one should take care that authorized agencies should install robust antivirus software on all LAN servers and workstations. In addition, system antivirus software, including virus signature files must be updated at regular intervals as and when released by the software vendor.
A centralized application is required where unnecessary load on multiple servers must be restricted. All applications must be controlled through a centralized server for better supervision and control of the network.
The hardware management group or the system configuration management must ensure. Maintenance of good backups of critical data and programs. Use of network connections outside the organization must be strictly prohibited.
Conclusion
After analyzing the case study it can be concluded that a proper networking environment is crucial for the maintenance of the organizations valuable sources both internally and externally. The first step towards effective security system is support by the trained staff to respond immediately to the needs and inquiries probed. The next stage requires prompt actions by the management for critical situations in solving the security problems that are difficult for the personnel to handle and are responsible for generating alarming signals and developing serious technical issues. Troubleshooting the identified problems at the right time is the key. Keeping the workforce up to date with regular training sessions and imparting knowledge about the latest tools and techniques for the network’s security to combat new threats is of utmost importance.
All possible Security challenges and threats in networks that can creep up in future should be taken care such as Denial of service, theft of information, hacking etc. Proper security solutions can result in reduction of down time against breaches of security, reduction and prevention of malicious attacks, malfunctions, data manipulations, resource piracy etc. it also results in the satisfaction of the customer data bank, increased revenues and regular maintenance of all its confidential and security products.
Bibliography
Horenbeeck V M. Deception on the network: thinking differently about covert channels. 2008. Web.
Cabuk, S., Brodley, C. E. & Shields, C. (2004) IP Covert Timing Channels: Design and detection. Proceedings of the 11th ACM conference on Computer and communications security, pp. 178187. Washington: ACM Press.
Service Data Sheet, 2002, Cisco Secure Wireless Scoped Planning and Design Service Bundle. 2008. Web.
Good Practicing Note: Managing Retrenchment, 2004, Number 4, IFC, Enrollment and Social Service Department. 2008. Web.
Majik, 2001 , Preventing and Detecting Malware Installations on NT/2K, 2008. Web.