Introduction
Security management is unique among all peacetime disciplines for being the only one in which the critical performance measure is a non-event: processes, people, property, and product in storage or transit proceed as expected and are unimpeded. Success on the job is often overlooked because no obstructive or destructive events impede organizational performance towards its goals. Conversely, just one breach into the data center or one case of theft reveals vulnerability and destroys confidence in all policies and procedures so assiduously put in place. Organizations grow complacent when they are secure but a single breach of ethics puts disproportionate blame on the shoulders of security managers.
Not surprisingly, institutional paranoia is a way of life for security managers. On whatever scale an organization operates – from small mom-and-pop enterprises to multinationals operating globally and 24/7 – security management takes on the strategy and multi-threat defenses of a U.S. Army outpost in the middle of Sadr city in Iraq. There are hostiles on all sides and static defense just does not cut it when rockets and mortar shells begin flying.
There are multiple benefits to proper contingency planning in security management:
- Minimize the potential for property damage or loss of life.
- Imbue confidence that the leadership of the organization does care about the wellbeing of the staff.
- Reduce the chance of panic, an unreasoning and extremely contagious phenomenon that often does more damage than external threats.
- Avoid expensive litigation because American jurisprudence is filled with examples of huge awards for “failure to warn and failure to protect” (Mahoney, 24).
Review of Literature
The best security programs are informed by broad considerations of technological developments for detection and defense to meet the type of threat expected. In turn, superb planning yields more palpable benefits when it integrates perimeter and interior architecture, security systems, human resources, procedures, and up-to-date threat intelligence (Patterson 2004, 56). We accept this at face value, given the ordinary view of security management as defending against loss and external attack or intrusion. Given the extraordinary scope of security management in times of natural and manmade disaster, however, developing a comprehensive security plan must also take into account the geographical, weather-related, sociological, political, or religious factors specific to each location.
Scanning the literature in this field immediately brings home the lesson that the issues, strategies, and day-to-day management of security revolve around concentric defense perimeters, as it were. The astute security manager accounts for international and domestic threats that can penetrate to the communities in which his charges operate; then, of course, there are security issues for the immediate surroundings, for access, the internal environment, and the broad field of electronic and Internet security itself.
Besides considering the level of risk, the needs assessment inherent to security planning can be more or less formal, rough, and ready, or highly systematic (Center for Health Information Technology 2008, 1). In a tiny organization such as a three-lawyer partnership, it may be enough for the administrative partner to run through issues mentally. At the other extreme, a large multinational with different types of facilities such as laboratories, offices, factories, warehouses, and complex supply chains to the end-user and operating in nations with different peace and order conditions necessarily starts with formal processes to define needs. A third-party team may even be called in to render a more objective risk assessment; flowchart the necessary, process, and information flow; recommend specific security solutions or turnkey systems; and help train everyone at the end of the process.
In any case, there is a common set of concerns that need to be addressed. What are the workflow constraints to good security? What features or functionality should a security reporting system have? What incidents should be reliably monitored and how should these be reported to those who have oversight? When is a convenient time for security personnel and the rest of the workforce to receive training and security-consciousness orientation?
International and Domestic Threats
Six and a half years after the World Trade Center attack, the after-effects still ripple through many aspects of American life and we are convinced our physical security remains under constant threat. Since then, the country has been on a war footing; troops have been sent abroad to root out an elusive enemy at the source, colossal resources have been mobilized to combat the enemy who hides among us (Wright 2006, 724) and we have even given Homeland Security unprecedented leeway for domestic electronic and financial systems surveillance.
Just to give an idea of how huge the costs of defensive measures have been, the American Water Works Association reports that the seemingly simple matter of securing municipal water supplies from terrorists who might toss in toxins or biological agents has involved hundreds of millions of dollars in more intensive water monitoring programs, physical security infrastructure, planning and emergency training (Lacey 2003, 2).
In the interim, with no new catastrophic incidents, security managers may have let their guard down. After all, not even the military is able to maintain high red alert for weeks at a time, let alone years. Nonetheless, as subsequent events in London, Spain, Iraq, and Afghanistan proved, the terrorist threat remains. America remains vulnerable, given its teeming cities, open society, ethnic minorities that openly sympathize with the enemy in the name of freedom of speech and religion, and continued involvement with democratic and human rights movements around the globe. Time after time, we get a sense of how terrorist intimidation works on the citizenry, fostering suspicion, justifying religious and ethnic profiling, undermining our collective sense of safety, and subverting our trust in duly-constituted authority (Mahoney 1994, 24).
Security planners and managers can never afford to let their vigilance down, no matter that the intimidation terrorist groups exercise is the more persistent than threats actually carried out. In the aftermath of 9/11, the Persian Gulf War, the invasions, and continuing occupations of Iraq and Afghanistan, reviews initiated by governments and large multinational corporations recognized that it is not realistic to maintain the highest vigilance indefinitely. By the very nature of underground terrorist cells, it is perhaps impossible to know to what extent more rigorous surveillance deterred further terrorist acts. Still, security professionals take solace in the reasonable assumption that more stringent laws and enhanced security measures must have played a role in preserving collective safety.
All physical facilities everywhere, but especially those U.S. establishments located overseas, are more or less under threat of domestic (within America) and foreign attack. Hence, the Office of Homeland Security released its Homeland Security Advisory System (HSAS) defining five levels of threat. Taking off from the HSAS, the American Society of Industrial Security International drafted guidelines for industry, “Threat Advisory Response Guidelines”, and The Steele Foundation developed corresponding protocols for commercial establishments and industrial facilities:
Going forward, security managers will continue to find realistic compromises that enable their organizations to function as well as possible while maintaining greater security than ever before. In high-threat areas, it pays to be taken into account explosives-related violence. The bomb-defusion or bomb-threat management portion of the security operations manual should consider that:
- Homemade bombs can look innocuous since their design is limited only by the imagination and resources of the bomber.
- Bomb threats will be called in, either directly or through a third party. If false, the threat is designed to sow panic, anxiety and to disrupt the operations of your firm. Plan contingency actions to forestall all possible uncontrollable reactions before they happen. Train telephone operators to handle phoned-in threats, if only to record the information accurately, to stall or elicit more background than the caller had intended to divulge. Surprisingly, some bombers have been known to divulge location details when operators ask outright for the location when reminded that innocent people will die or be injured, or by responding calmly that the building is occupied or cannot possibly be evacuated in time, If the facility exists, have tape recording commenced outright. In any case, investigative efforts can be aided by listening for background noise or being observant of details like accent, gender, mood, and speech defects. Most importantly, take all threats seriously. Only professionals are trained to discern fake and real bomb threats.
- Proper preparation relies fundamentally on hardening your building or facility against bomb attacks. The first layer is defensive and an example of these are the “flower boxes” meant to stop explosive-filled trucks before they get too close to an American embassy. This has become a permanent part of the landscape, even in countries we are not at war with. The embassy in Bangkok has them because peaceful as it is, Thailand has a restless Muslim minority that has been agitated by the Indonesian tentacle of al Qaeda, Jemaayah Islamiyah. Hence, all US businesses in Thailand take the threat of Muslim attacks seriously.
- Another, less obvious example of hardening is imposing stringent limits on access by outsiders, visitors, and suppliers alike. If a bomb threat becomes reality, therefore, it is much easier to do a thorough search of a limited number of public-access areas.
- For the rest, compensate for vulnerable architectural design by adding lighting, fencing, and stringent access control, of course. To diffuse the threat from remote-controlled bombs in vehicles of any sort, move parking at least a hundred meters away from any building. Or at least put visitors’ parking as far away as possible.
- Remove possible areas of concealment by clearing away dense shrubbery, collections of trees, and flower boxes.
- There is accordingly a place for both bomb incidents and physical security plans (the latter discussed elsewhere). It helps if the bomb incident plan covers a definitive chain of command, a physical command center with the necessary authority to override senior management and third parties (e.g. tenants) in times of emergency), ready communications to the police, and fire services.
- By all means, have the police in for a security inspection that may reveal areas of vulnerability the organization never suspected. As well, leave the professions to handle bomb disposal if that dread contingency ever becomes real.
- Train an extremely thorough search team to be familiar with all hallways, restrooms, false ceiling areas, and every other possible hiding place. If no such employees are to be had, fall back on roving guards and maintenance staff. Better yet, call in experts from police or military bomb disposal units.
- Organize an evacuation, marshaled by trained supervisors and managers, only as a last resort, when an explosive device has been located. Otherwise, a stream of fake threats can inundate critical utilities, schools, and company facilities if evacuation-before-search is the primary policy.
- If evacuation must take place, prioritize those on the floor where the bomb is located, the floors above and immediately below. Those occupants are in the most danger. Naturally, direct them to the exits farthest away from the bomb.
Physical and Access Security
The physical security segment of the security procedures manual involves a variety of aspects. In the main, one must cover protection of property, personnel, facilities, and product stocks from unauthorized access, trespass, damage, sabotage, or other illegal or criminal acts (Mahoney, 24). The physical plan seeks to augment already-existent security measures involving prevention and control of access to the building.
Planning for physical security measures takes into account threat levels, techniques for developing appropriate operational concepts, crafting alarm response and action plans for the security forces, seeing to security patrol procedures, maintaining and updating agreed procedures, and training. Security managers must undertake a threat analysis for each company site or plant, plan security needs accordingly and design the requisite physical security program. Even when a plan is in place, the security force reasonably well-trained, alarms and other infrastructure in place and tested, security managers, need to engage the in-house security force on contingency planning and ways to mitigate risk better with the use of systems already in place (Patterson 2004, 54).
In the author’s view, security risk analysis covers three broad areas (see below). Training employees and the security staff will give priority to the operational aspects so that all concerned see how these upgrade the level of security at the facility and thereby protect from crime or loss.
At the minimum, the physical security plan must cover:
- Exterior foot patrols or, if the security staff is undermanned, closed-circuit television cameras for external surveillance and roving inspection inside the facility.
- Burglar alarms and warning signs about them.
- Strong doorways with hinges and hinge pins on the inside so they cannot be removed by an intruder.
- Bar tossed bombs or unwanted entry by shielding windows, vents, transoms, and skylights with grills, bars, mesh screens, and steel shutters.
- Complement access to sensitive areas or departments limited to authorized staff with rigorous package inspection.
- Constant surveillance of hiding places (e.g. stairwells) for unwanted outsiders. Always have maintenance personnel ready to account for keys to normally-locked areas such as computer rooms, data-storage vaults, boiler rooms/cellars, and the mailroom.
- Sign visitors in and out through one receptionist or guard station at the lobby.
- Lastly, train the staff to be suspicious of packages and people that do not belong.
Data and IT Security
A complete security plan cannot overlook the principle that information is an extremely valuable corporate asset, the loss of which can hurt competitive standing in the marketplace, seriously erode accountholder confidence in the case of banks and credit card companies, cause more financial loss than a simple break-in at the office, and even bring litigation down on corporate boards.
Unlike physical security, for which no measure is too extreme to ensure a completely “locked down” mode, the sheer openness of the Web coupled with an ever-increasing reliance on email for intra-corporate communications and financial transactions poses a paradox that many enterprises do not even know exists (Woodward 2000, 23). Very few care to know that robust encryption tools are available to protect both emails and document attachments. And even the knowledgeable ones choose not to implement these on laptops that roam everywhere and are easily stolen.
Security problems are an order of magnitude greater when an enterprise relies on e-commerce for any portion of sales revenue. Certainly, the stakes are huge. By one estimate, online sales in the United States already accounted for some 5% of total retail turnover and were expected to reach $116 billion at the end of 2007 (Richtel and Bob Tedeschi 2007, 1). The more savvy online shoppers may be reassured whenever they see logos of “Verisign” or “security socket layer” that hold the promise of their credit card and other personal information being protected while in transit over the wide-open Internet. But how does a conscientious “e-tailer” plan security systematically and not fall into the trap of just buying encryption utilities off-the-shelf from a fast-talking vendor? After all, one does not have the assurance of endorsements from other dot-com’s. By definition, excellent security means nothing happened, nobody managed to “break-in” and compromise sensitive credit card files and other sensitive financial information.
One answer comes from Tang (2008, 54) who reported the case of a telecommunications company that had by then earned most of the revenue from e-commerce. Management made it their concern especially since the company strove to conform to ISO/IEC 19977 quality standards. This protocol is all about developing the criteria for an Information /Security Management system. Given the goal of implementing good security planning and the intention to deploy risk management tools to analyze the strengths and weaknesses of online security, it seemed pertinent to use the Deming Plan-Do-Study-Action (PDSA, previously PDCA for “check”) model as a framework for the planning and quality-improvement work that was to take place:
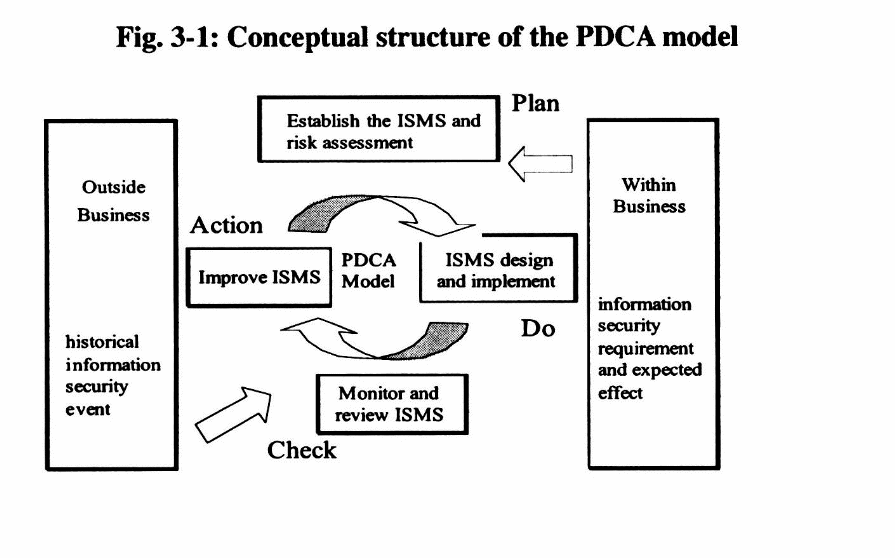
In the planning phase, it was determined that the necessary components were:
- Articulate an information security policy.
- Designate a person or team to oversee the policy.
- Create a system for inventorying, classifying, and controlling assets (mostly the saleable goods and credit card receivables in an e-commerce company).
- Assess the level of risk.
- Arrive at methods for physical and online security, communications, and operations.
- Decide who is to have access to the information (segmented into the “A” team, those directly managing online transactions; “B”, internal and external auditors; and, “C” everybody else in the e-commerce dot-com involved in order fulfillment).
- A strategy for developing and maintaining the information security system itself.
- Manage continuity and change.
Strange as it may seem, even the matter of medical records comes under scrutiny for compliance with HIPAA (Health Insurance Portability & Accountability Act 1996) standards for the security of electronic health information. By now, physicians and primary care administrators are perfectly aware of the need to document all clinical encounters. Since all such documents (including voice recordings before they become transcripts) and patient records are protected by the ethics of the profession concerning patient privacy, it is a small conceptual leap to complying with the published guidelines for administrative, technical, and physical security procedures. For medical establishments that are none too familiar with ensuring the confidentiality of health information in electronic form, Kibbe (2005, 45) reiterated gap analysis and protective measures that are, by now, old hat to IT security managers in mainstream business:
- Have all those who originate, generate, and transmit medical records realize why computer security is important, including briefing them on penalties provided by law.
- Convince the organization to take security seriously.
- Revisit the system design and scrutinize all network links that access protected health information.
- Organize a disaster response plan just as the ER team does for accepting trauma cases. Have dual physical backups for all hard disks and network databases containing patient information, one internal and the other off-site
- Ensure network and communications security is robust. Schedule semi-annual penetration testing.
- Keep antivirus and firewall software up to date against the latest viruses, hacks, Trojans, worms, and assorted “malware.”
- In the HIPAA situation, encryption of data files and emails is not mandated. The standards do require an assessment of whether unencrypted transmissions originating from a private practice or a primary care institution put patient information at risk. If the answer is “yes”, both senders and recipients must agree on a convenient encryption platform.
- Lookout for chains of trust and other organizations one does business with. For clinical practice, these external organizations include insurers, transcription outsourcers, billing services, other hospitals, laboratories, and Internet service providers. In the sub-specialty of IT security, “chains of trust” refers to agreements undertaken and authentication protocols employed to ensure that data remains secure in transit.
- Ensure that IT vendors and networking suppliers are able to comply with HIPAA requirements, including by way of example, the one that demands an audit trail. One way to do this, of course, is to adopt the single-vendor solutions for EHR systems: turnkey solutions that do everything from billing, scheduling, and clinical information.
- Make a reasonable and appropriate plan and gap analysis for the level of IT security risk that prevails in your situation.
Guarding Against Employee Theft
In general, one finds that there are both individual and situational factors that lead to worker malfeasance.
Among the many paradigms of individual traits, security managers and police forces have long shared Murphy’s view (1993) workforce crime is related to penurious need, combined with an opportunity presenting itself, the lack of moral scruples, and the skill needed to carry it off. More recently, psychologists and sociologists have attempted more complete explanations. Juvenile-minded employees may filch company assets just as shoplifters do, for the sheer thrill (Latham, 2001). Thirdly, there is peer group pressure (Osland, 1997). Fourth, there may be a lack of commitment, operationalized as planning to leave soon (evoking thoughts of an underlying moral problem and labeled “turnover intentions” by Frazee, 1996; Thomas, et al., 2001), working part-time (Flynn, 1995), and a short tenure with the firm (Sims, 2002).
Peer pressure, Hirschi (1969) suggested, is merely one aspect of Social Bonding. Yielding to peer pressure is a function of the strength of the body within the workgroup. But social bonding also covers the strength of family relationships, personal commitment to group acceptance versus penalties for theft, ethical response to social norms, and identification with positive or negative actions in the workplace.
The organizational literature is also replete with theft impelled by perceptions of unfair treatment by superiors (Greenberg & Scott, 1996) and dissatisfaction with pay (Greenberg, 1990, Hollinger & Clark, 1983). One also acknowledges differential equity sensitivity (Huseman, Hatfield, and Miles, 1987) whereby employees who are high more sensitive are afflicted with greater distress and are motivated to act on the seeming injustice. “Getting back” at the employer for pay inequity has been found to be related not only to a greater incidence of theft but also to the propensity of observant colleagues to behave as if they know nothing about what is going on (Victor, Trevino & Shapiro, 1993). This means employee satisfaction (or the lack of it) is also a predictor.
Finally, there is ethical maturity of the individual (Greenberg, 2002) which HR departments already routinely know to look for in their batteries of personality inventories.
As to the situational factors found to correlate with employee theft, these have included:
- The perceived likelihood of being caught, as well as the forcefulness and certainty of company sanctions (Hollinger and Clark, 1983);
- Ethics policies, briefings, and discussion groups reduce the incidence of theft (Weber et al., 2003);
- The ethical climate of the immediate workgroup as it fosters or discourages deviant behavior (Robinson and O’Leary-Kelly, 1998);
- Organizational size, where the larger and more impersonal company seems bedeviled by a greater incidence of theft (Murphy, 1993);
- “Perceived Organizational Support” where employees feel a sense of obligation in return for the employer demonstrating good citizenship toward the workforce (Moorman, Blakely & Niehoff, 1998; Rousseau, 1995; Gakovic & Tetrick, 2003).
Conclusion
The normal security standards aside, community and national threat levels vary over time and hence must be inputted into security plans. The plan must cover operational procedures for each threat level, as well as the human element by including full operations and security force response manual. These three factors are the fundamentals for optimizing the design and installation of integrated security systems.
The enhanced threats from global terror groups and domestic activists aside, a comprehensive security plan dare not overlook the problem of employee theft. There is an authoritative opinion that this is a widespread phenomenon that causes employers significant if often untraceable losses (Weber, Kurke & Pentico, 2003; Greenberg, 2002). Since most of the literature in this area has analyzed workplace theft against a handful of independent variables, it is perhaps timely to develop a more comprehensive investigative plan.
Research Approach
In positing the effect of both individual traits and situational factors on the propensity for workforce theft, one assumes that organizations can test for the former and manage the latter. Hence, this research ought to be decisive and action-oriented.
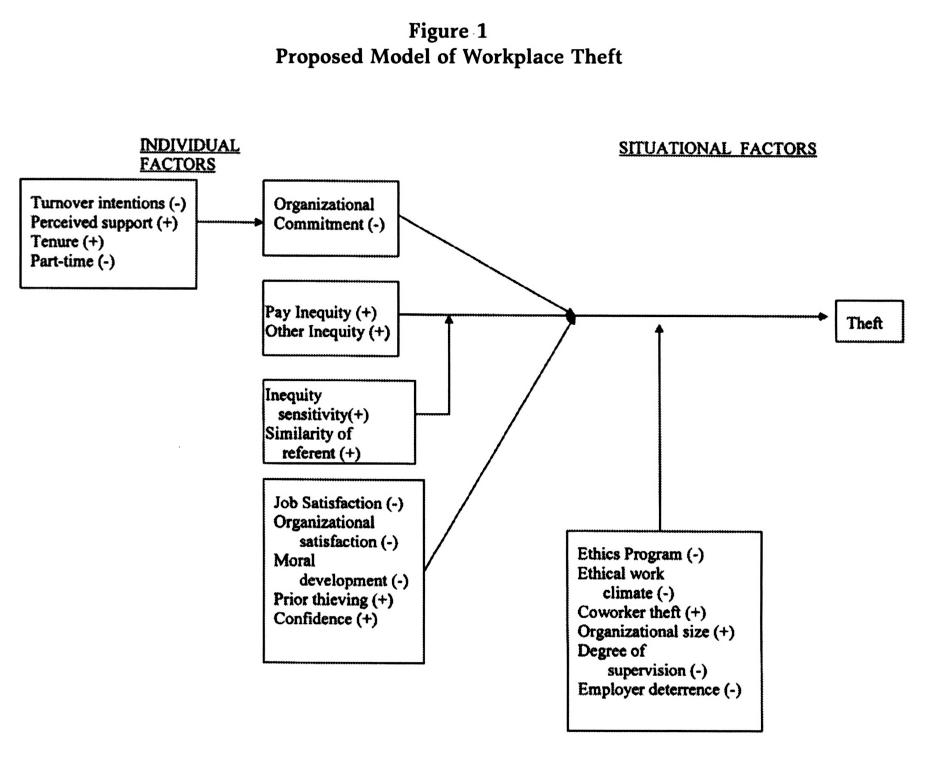
Employing a dichotomy between individual traits and situational factors enables us to sketch a starting model (see overleaf) that, turn, suggests some hypotheses for research:
- H1: Turnover intentions (-), perceived organizational support (+), tenure in the organization (+), and status as full-time (+) or part-time (-) predict organizational commitment.
- H2: Organizational commitment (-), job and organizational satisfaction of workers (-), ethical maturity of individuals (-), and unpunished thieving (+) correlate with workplace theft.
- H3: The effect of pay inequity perceptions (+) are moderated by inequity sensitivity (+) and similarity of the referent chosen (+).
- H4: The moderating factors are an existing ethics program (-), an ethical work climate (-), the extent of thievery by coworkers (+), organizational size (+), degree of supervision (-), and employer sanctions (-).
Means and Methods
The research will identify a sizeable organization of at least 1,000 workers and one where the employee relations department already uses such personality assessment inventories as the Myers-Briggs Test Inventory. This means we already have ready data for individual traits. A second instrument will be a new “Opinion Survey” questionnaire which shall investigate perceptions of organizational commitment, acceptability of petty theft, and projective items about the incidence of theft in one’s workgroup.
Primary data-gathering will be carried out in two randomly selected departments of about the same size, staff profile, pay level, and such. But the essential difference between the two departments is the incidence of material losses reported in each and investigated by the security department.
Data Analysis
Owing to the nominal or categorical nature of the individual trait and situational factor variables, I propose to use stepwise logistical regression to quantify the strength of the relationship between each independent and moderating variable with the dependent variable of theft incidence in the department.
Bibliography
Center for Health Information Technology. 2008. Perform a needs assessment. American Academy of Family Physicians. Web.
Flynn, G. 1995. Part-time employees’ theft packs a punch. Personnel Journal, 74, 22.
Frazee, V. 1996. Why do employees feel free to steal? Personnel Journal, 75, 21.
Gakovic, A., & Tetrick, L. 2003. Perceived organizational support and work status: A comparison of the employment relationships of part-time and full-time employees attending university classes. Journal of Organizational Behavior, 24, 649-663.
Greenberg, J. 1990. Employee theft as a reaction to underpayment inequity: The hidden cost of pay cuts. Journal of Applied Psychology, 75(5), 561-568.
Greenberg, J. & Scott, K. 1996. Why do employees bite the hand that feeds them? Employee theft as a social exchange process. In B.M. Staw and L.L. Cummings Eds.) Research in Organizational Behavior (Vol. 18, pp. 111-155). Greenwich, CT: JAI Press.
Greenberg, J. 2002. Who stole the money and when? Individual and situational determinants of employee theft. Organizational Behavior and Human Decision Processes, 89(1), 985-1003.
Hirshci, T. 1969. Causes of delinquency. Berkeley, GA: University of California Press.
Hollinger, R. & Clark, J. 1983. Deterrence in the workplace: Perceived certainty, perceived severity, and employee theft. Social Forces, 2, 398-419.
Huseman, R. Hatfield, J. & Miles, E. 1987. A new perspective on equity theory: The equity sensitivity constructs. Academy of Management Review, 12, 222-234.
Kibbe, David C. 2005. 10 steps to HIPAA security compliance. Family Practice Management 12, 4: 43-9.
Lacey, Marcia. 2003. Of utmost concern. American Water Works Association. Journal 95, no. 4: 2.
Latham, G. P. 2001. The importance of understanding and changing employee outcome expectancies for gaining commitment to an organizational goal. Personnel Psychology, 54(3), 707-717.
Mahoney, Patrick F. 1994. Business and bombs: Preplanning and response. The International Journal of Bank Marketing 12, 2: 24.
Moorman, R., Blakely, G. & Niehoff, B. 1998. Does perceived organizational support mediate the relationship between procedural justice and organizational citizenship behavior? Academy of Management Journal, 41, 351-359.
Murphy, K. 1993. Honesty in the workplace. Pacific Grove, CA: Brooks/Cole Publishing.
Osland, A. 1997. How to discipline a thief who stole for fellow employees. Journal of Workplace Learning, 9, 56-62.
Patterson, David G. 2004. Adapting security operating procedures to threat levels. Journal of Facilities Management 3, 1: 53-64.
Robinson, S. & O’Leary-Kelly, A. 1998. Monkey see, monkey do: The influence of work groups on the antisocial behavior of employees. Academy of Management Journal, 41, 658-673.
Rousseau, D. 1995. New hire perceptions of their own and their employers’ obligations: A study of psychological contracts. Journal of Organizational Behavior, 11, 389-400.
Sims, R. 2002. Ethical rule breaking by employees: A test of social bonding theory. Journal of Business Ethics, 40, 101-110.
Thomas, P., Wolper, P., Scott, K., & Jones, D. 2001. The relationship between immediate turnover and employee theft in the restaurant industry. Journal of Business and Psychology, 15, 561-579.
Victor, B., Trevino, L., & Shapiro, D. 1993. Peer reporting of unethical behavior: The influence of justice evaluations and social context factors. Journal of Business Ethics, 12, 253-264.
Weber, J., Kurke, L. & Pentico, D. 2003. Why do employees steal? Business and Society, 42, 359-374.
Wright, Bob. 2006. A time of reckoning. Vital Speeches of the Day 72, 25: 723-7.
Woodward, Darrel. 2000. Smart security. The British Journal of Administrative Management no. 18: 22-23.