Introduction
The result of September 11 spontaneously changed the meaning of the term “security” to a more composite definition. The attack led to a global concern over the probable repeat of such attacks using other modes of transport.
The deadly bombing of the commuter trains in Madrid and London accentuates the devious intents of the terror networks to strike transport systems, especially the facilities used by a large number of civilians. If the commuter train could be bombed and commercial airlines rammed into the twin towers, the probability of the port facility and infrastructure being the next target is very high.
The security of ports is of great concern because any attack on port facilities and infrastructure would lead to massive loss of life and property, which would ultimately upset the international trade and the global economy. Any form of attack on a cargo port would be very costly to the local and global economy. This could lead to closing down of ports. Eventually, this could result to a massive loss of jobs and destruction of goods and port infrastructure. For this reason, most governments have heavily invested in port security.
Ports are currently considered as a probable target for terror attacks. Therefore, 9/11 has fundamentally transformed the whole landscape of the maritime industry. The maritime industry has been put through numerous security programs with the purpose of preventing any security breach. The post 9/11 security strategies have expanded the realm of the term “port security” beyond the traditional frontiers. The analysis of the design and configuration of ports to tackle the contemporary security challenges will be the basis for this paper.
The growing concern about the safety of commodities and passengers prompted the introduction of numerous security frameworks, which are either voluntary or obligatory with the aim of improving port security. Nonetheless, one of the major challenges facing port officials is negotiating a suitable balance between security and cost involved in the implementation of the new measures. Therefore, there is a need to consider the impact of each alternative.
Rudiments of port security
The objective of port security is to create an atmosphere in which business may be carried out with confidence and without becoming a channel of illegal operations. In other words, the port security department should make every effort to restrict the prospects for illegal use of port facilities and infrastructure. In order to achieve this, port security officials have to embrace a proactive approach, which requires intelligence and exploratory harmonization of all security agencies and departments within the maritime industry.
Security must be given a priority during the planning processes and must command attention and resources of all the port officials. Whereas the responsibility and accountability for port security objectives and standards rest with the directors, the execution and success of the security plans depend on all the stakeholders.
The port operations highly depend on the effectiveness of the security apparatus. Effective port security can only be realized through proper coordination and integration of all the functions with the security department. This is usually achieved through planning and successful implementation of the security strategies and goals.
An effective security plan should be able to document and quantify security threats, weaknesses and the efficiency of the implementation process. This requires a system that is able to continuously monitor and evaluate the implementation process in order to maintain a high level of security. Therefore, security planning is both tactical and strategic. This makes the process very dynamic and flexible because operations can be adjusted in accordance with the prevailing circumstance.
The aspect of change makes port security planning a regular process. In addition, the planning process requires intelligence information to analyze the prevailing and probable security threats. The information can also be used to assess the susceptibility and suitability of the measures already in place.
The intelligence information can also be used to develop and put in place measures that will help to minimize port susceptibilities. This means appropriate measures cannot be developed without understanding and recognizing potential vulnerabilities. For this reason, port security officials should be able to establish the nature and echelon of potential threats. This requires a comprehensive security survey.
Generally, the survey provides a wide-ranging and accurate data as regards port’s susceptibility and the existing and potential threats to port’s operations. The data should be compiled in a way that makes it easy to compute the rate of recurrence and level of the vulnerabilities and threats.
In a nutshell, the port security planning process considers the following criteria:
- the port’s susceptibility to existing and probable threats,
- the impact of the security measures on the operations of the port,
- security constraints brought about by port infrastructure,
- availability of resources,
- available options, and
- the analysis of all the existing security measures both within and without the port.
Port Facility Security Design
Purpose and Legal Basis
As already been mentioned, the security plan for ports is always subject to constant reassessment. Generally, the plan is reviewed every year by the port management based on the results of the yearly appraisal carried out by the port security officers. Most of the designs are based on the risk management approach. Port security design for this paper will be based on the general threats.
This is because the threat levels usually fluctuate from time to time. The main objective of the port facility security design is to prevent existing or potential threats to port infrastructure and various users. The design consist of an array of measures, which include security plans, processes and guidelines for protecting port facilities and infrastructures, officials, and ships.
The port security design is generally developed by state and commercial agencies. In the United States, the U.S Coast Guard is responsible for designing port security. The U.S Coast Guard Captain is in charge of putting together the security team that collects information from port users and other stakeholders, which are vital in designing port security. This is contained in the “U.S. Guideline for Port Security Committees and Security Plans”.
The security assessment and design are submitted to the International Maritime Organization as satisfying the International Ship and Port Facility Security Code (ISPS Code). The U.S. Coast Guard also requires individual facilities handling international vessels to comply with the ISPS Code. In addition, the U.S. Coast Guard expanded the scope of its regulation to include vessels that do not fall under the International Ship and Port Facility Security Code.
Annual Review and Auditing Process
Port security design should be revised periodically depending on the prevailing circumstances and potential threats. The Port Security Office (PSO) can propose suitable amendments following the reassessment of the design. The proposed amendments must be re-examined, especially those that could alter the previously adopted approaches or affect port operations.
Description of Port Facility
This comprises of basic information describing operations carried out at the port and how they are conducted, for instance, cargo handling, staffing, schedules and other activities. Majority of ports handle, stores, and distributes chemicals and petroleum products besides other commodities. In the recent past, containerized and bulk-type consignments have been targeted by criminals and terrorists.
Chemicals and petroleum products tend to be the main target due to their combustible and poisonous properties. For example, the attack on the Israeli port of Ashdod, which claimed over ten lives, acts as a warning that the ports are not safe from terrorists. The procedure for handling cargo and ships is contained in the operations manual.
Port Security
General Security Policy
Ports are required to observe the international laws and regulations governing the security of the maritime industry, as well as national and internal laws. The port management and official must embrace contemporary management practices. Port security apparatus must ensure that workers, guests, port facilities and infrastructure, cargo and ships are well protected from terrorists and other criminal elements. Port security awareness should be promoted among all workers and users of port facilities and infrastructure.
Facility Security Officer is in charge of the security of port facilities. The security officers must co-operate with relevant authorities and can take necessary action based on their advice. Ports should also have a guideline for responding to security threats, which must be updated regularly. The guideline must contain crisis management structure and recording and reporting systems. Last but not least, Facility Security Officer should be able to make independent decisions and only seek for advice where necessary.
Port Facility Security Officer
Facility Security officers are in charge of designated facilities. They may delegate some of their duties, but they are the one held accountable. Some of the duties and responsibilities of the Facility Security Officer include:
- carrying out a preliminary security survey of port facilities,
- development and amendment of the security plan,
- Execution, coordination and evaluation of the security plan,
- recommending and incorporate suitable amendments to the existing security plan,
- reporting to the relevant authorities on imminent security threat,
- maintain security equipments and standard.
Ship Security Officer
Ship Security Officers are assigned to specific ships berthed at the facility. The duties and responsibilities of these officers include: coordination of cargo handling and ship security, execution of the ship security plan with other security officers, helping Facility Security Officers with any relevant detail concerning a particular vessel or its personnel, and helping Facility Security Officers in identifying stores or cargo offloaded from a given ship.
Port Security Committee
The port security committee comprises of the high ranking port officials and state security representatives. They make ultimate security decisions, especially decisions that are very sensitive, multilateral and have massive ramifications.
Security Program, Drills, and Exercises
All the port employees have a role to play in safeguarding port facilities, infrastructure and users. A continuous, rigorous and potent security program creates general awareness and watchfulness. Facility Security Officers are in charge of promoting and coordinating security programs and training. The program must ensure that all the employees are able to identify, comprehend and take necessary action on any kind of security threat.
The program emphasizes on the fact that security is the responsibility of all the employees and the port users. The objectives of the security programs, drills and exercises include: promoting quick response to security threats, purging security breach and violation, enhancing facility defences against the existing and potential threats, creating security awareness and consciousness, and training security personnel on the procedures and methods used to avert or minimize security threats.
The Awareness Program
The new recruits or employees assigned to the security docket are usually provided with security manual as part of security awareness orientation. The manual contain vital instructions, individual responsibilities, impact of various threats and appropriate measures, and the importance of security awareness. This is followed by training and drills to enhance proficiency and alertness. The training is carried out on a quarterly basis.
Drills and Exercises
The security programs and schedules are drafted by the Facility Security Officer. They must make sure that all the drills and exercises are carried out on a regular basis, especially not less than three times per year.
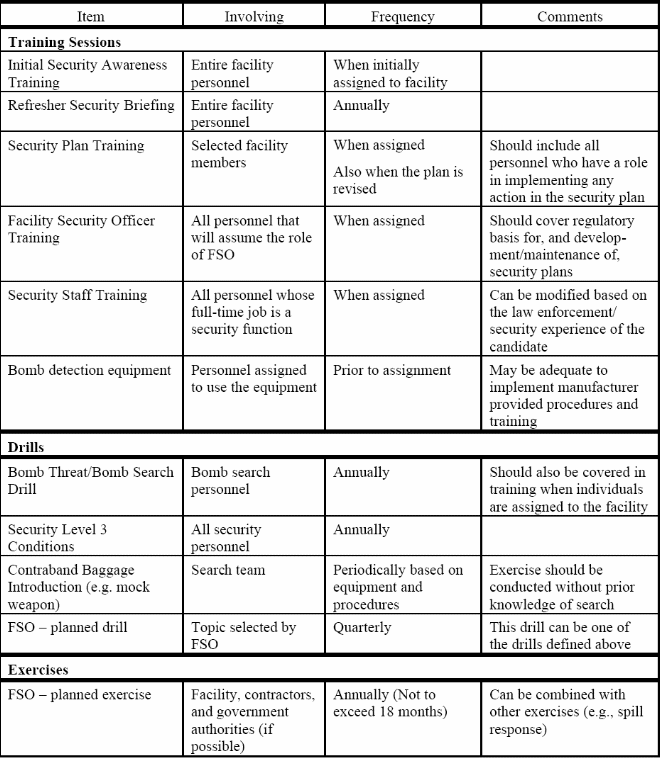
Security Strategy, Processes and Controls
Generally, the security measures must be in line with the established security levels. These levels vary from one jurisdiction to another. The Facility Security Officer is in charge of the security timetable that highlights the tasks and duties of each security personnel. Conventionally, there are three levels for port security, that is, security level1, security level 2, and security level 3.
Security Level 1
Security level 1 is considered to be the lowest level of security. This level deals with the general security threat to port facilities, cargo and ships. For this reason, it must be maintained throughout.
It involves positive identification of illegal persons or intruders, searches on personal effects and vehicles, supervision of cargo loading operations, advance notice for ship arrivals, store searches, full communication with the vessels berthed in the facility, recording details of cargo, visitors and vessels, maintaining high situational awareness, reporting any suspicious activities, ensuring security lights are switched on during darkness, and locking all the unused accesses.
Security Level 2
Security level 2 tackles security threats that have been reported due to intelligence information gathered from different authorities. However, there is no exact target identified. The intelligence can be on a threat to port facility, infrastructure, employees, users, cargo and ships.
Security level 2 involves addition of security personnel to secure access points and perambulate boundaries, advance screening of vessels and individuals requesting access port facilities, enhancing security for ship stores, limiting access to sensitive areas/ restricted areas, making a statement on security between vessels and the port facilities and infrastructure, enhancing cargo screening, enhancing security awareness and alertness, and verifying cargo in storage and visitors who have access to port facilities.
Security Level 3
This represents the highest level of security threat to port facility, employees, infrastructure and users. At this level, a specific vessel, personnel, infrastructure, cargo or facility has been identified as the target and that the threat is imminent.
Security level three involves maximum use of security lights and surveillance tools, restricting non-essential access, securing all the access points, ceasing all the cargo handling activities, following instructions from relevant authorities, adjusting ship schedules, informing all the vessels and users about the imminent threat, preventing unofficial cargo discharge, undertaking waterside surveillance, preparing to evacuate or partly evacuating personnel and users from the facility, and implementing specific or additional measures to eliminate the security threat.
Security Declaration
Since the interface between maritime vessels and port facilities is very crucial in making sure that suitable measures are sustained at all time for all levels of security, and that there is no inhibition on any level of security, there is a need for agreement. This agreement is what is referred to as security declaration. Security declaration describes an agreement between the maritime vessel and the port security personnel, stipulating measures to be implemented by each party.
Security declaration for level 2 and 3 are provided at the first level. Security declaration specifies the requirements for cargo handling, administrative requests, and government policies. When the agreement has been reached between the two parties, Ship security Officer signs it on behalf of the ship. On the other hand, the Facility Security Officer signs it on behalf of the port. A copy is submitted to state agencies upon request.
Access Control
General
Access control basically refers to the regulation of physical access to port facilities. It depends on the existing measures and security levels already discussed. The measures are binding and must be implemented by the Facility Security Officers.
The Facility Security Officer must ensure that coast guards are posted at all times, all employees and guests have badges, employees and visitors sign in and out, sensitive and restricted areas are locked up, access to restricted areas are regulated and coordinated, security lights are switched on during darkness, and access control plan is recorded and regularly updated. All the sensitive and restricted areas are documented in the Port Security Plan.
Coast Security Guards
The coast guards are well trained and competent security personnel who operate ad infinitum to secure port premises and regulate access to port facilities at all levels. They report to the Facility Security Officers. They can also initiate security responses for non-security matters. The Coast Security Guards can be recognized by their uniforms and ID cards. In addition, they usually give a hand to the state police during high security incidents.
Access Points to Port Facilities
According to the International Ship and Port Facility Security Code, all unused entrances to the port facilities must always be locked unless they are used for official duties. They must be monitored until they are closed.
The security personnel must not allow unrestrained or unescorted movement. For this reason, employees and visitors must sign in and out when accessing port facilities. They must provide identity cards or Identity Badges, car registration numbers and the name of individuals being visited. Visitors are provided with temporary “pass”.
The ID Badges defines the visitors to be escorted or not. At Security Level 3, prior permission must be granted before gaining access to port facilities. The badges are normally serialized or coded. The visitors are usually instructed on how to wear the badges and what to do in case the badge is lost or misplaced. Security personnel and other employees must log in and out when accessing port facilities. Random searches on vehicles are done at level 1 and 2. At level 3, the searches are thorough and comprehensive.
Sensitive and Restricted Areas
These are areas within the port premise or facility that are given high priority in terms of security. They include control rooms, cargo stores and ICT rooms among others. These areas are usually marked and locked to avert illegal access. At security level 2, access to sensitive and restricted areas is only allowed under escort. However, at access level 3, visitors cannot be granted access unless they are granted prior permission.
Security Lights, Security Equipments and systems
The main objective of security lights is to help in detecting and preventing intruders. Security lights must be installed uniformly along the perimeter and on different facilities. The security systems include security control centre, close circuit television (CCTV) systems, intruder detection and alarm systems, and internal and external communication system. These systems must operate 24 hours. They are used to detect, monitor, document and report security breaches.
CCTV systems and Intruder detection and alarm systems should be placed on all the entrances, along the perimeter and other sensitive/restricted areas. The communication gadgets/equipments should be available to all security personnel. The Security equipments include handheld detectors, radiological detectors, gas detectors, bomb sniffing equipments, handcuffs, handheld radio, pepper spray, and firearms among others.
Conclusion
Port security is a great concern because any attack on its facilities and infrastructure would lead to massive loss of life and property, which would ultimately upset the local and global economy. Any form of attack on a cargo port would be very costly to the local economy in terms of jobs, destruction of goods and infrastructure.
As a result, port security design is a necessity. The designers should embrace a proactive approach, which requires intelligence and exploratory harmonization of all security agencies and departments within the maritime industry.
Bibliography
ABC Consulting. Port Security.Houston, Texas: ABSG Consulting, Inc., 2003.
Banomyong, Ruth, “The impact of port and trade security initiatives on maritime supply-chain management”. Maritime Policy Management 32, no.1 (2005):3-13.
Bichou, Khalid, “The ISPS Code and the cost of port compliance: An initial logistics and supply chain framework for port security assessment and management”. Maritime Economics and Logistics 6, no.4 (2004):322-348.
Bichou, Khalid. Security and Risk-Based Models in Shipping and Ports: Review and Critical Analysis. London, UK: Centre for Transport Studies, 2008.
Hastings, Paul, “Fresh security initiatives to thwart terrorists”. Cargo News Asia 29, no.7 (2005):12.
International Maritime Organization. Maritime Security Manual: Guidance for Port Facilities, Ports and Ships. London, UK: International Maritime Organization, 2011.
Goslin, Charles. Maritime and Port Security. Duos Technology, Inc., 2008.
ISPS Code. Maritime Security. Web.
Nazir, Khalid. Maritime Security Initiative Post -9/11: Implications for the Port Sector. Kuala Lumpur: Maritime Institute of Malaysia, 2007.
Organisation for Economic Co-operation and Development (OECD).Security in Maritime Transport: Risk Factors and Economic Impact. Paris: OECD, 2003.
U.S. Customs.“CTPAT Fact Sheet”. U.S. Customs and Border Protection. Web.
U.S. Department of Transport. Port Security: A National Planning Guide. Washington DC: United States Department of Transport, 1997.