Abstract
The phenomenal growth in mobile computing devices use over the last decade has led to revolutionary changes in the computing world. Mobile Ad Hoc Network (MANET) which are dynamically self-organized temporary networks have emerged as ideal networks for implementation in scenarios where adhoc wireless networks are required without the need for a central administration.
While highly effective, these networks are prone to numerous attacks due to the sheer number of nodes in the network and limited energy, memory and computational abilities of the individual devices. This paper identifies the security threats as: flooding attacks, wormhole attacks, unauthorized access. It goes on to propose solutions to this security issues. Protocols that can be used to prevent flood attacks such as AODV are discussed. Various implementations of Intrusion Detection Systems are also reviewed as effective means of ensuring the integrity of the network.
Cryptography and signcryption are proposed as novel means of establishing trust in the network. Hybrid firewall implementations that can work in MANETs are also discussed. To ensure authentication in the network, the use of certification graphs is proposed. To assist in the discovery of wormholes which pose significant risks to the network, trust and time based mechanisms for are reviewed.
Introduction
Today computing is not primarily reliant on the capabilities provided by the personal computers but increasingly on mobile computing devices which include: laptops, and personal digital assistants. Prevalence in mobile computing has made it necessary to implemented wireless networks which sometime need to be set up in an arbitrary manner. The Mobile Ad Hoc Network (MANET) has emerged as a feasible means to provide connectivity for ubiquitous computing.
MANETs are considered as ideal technology in military and civilian applications where instant communication is desirable. In military applications, high security and performance must be guaranteed since these MANETs operate in hostile environments.
A typical characteristic of MANETs is that they operate in unattended areas and are normally made up of a large number of sensor nodes. Meghdadi and Ozdemir (2011) state that these nodes can be in the order of thousands and they have limited resources in terms of energy, memory, and computation abilities.
While MANETs have become popular as a result of their inexpensive set up properties, these networks are open to insider and outsider attacks due to their open nature. Typical security measures such as firewalls and cryptography may be inadequate in protecting MANETs.
Considering the security problem that MANETs face, this paper will set out to propose security solutions. The paper will begin by providing an introduction to MANETs and the security problems that they face. Security Solutions for MANETs including the development of IDS will then be discussed.
Brief Overview to MANETs
Khokhar and Mandala (2006) defines a Mobile Ad hoc NETwork (MANET) as “a system of wireless mobile nodes that dynamically self-organize in arbitrary and temporary network topologies” (p.18).(The technological implementation of MANETs is similar to that of the traditional Mobile Packet Radio Networking). As a result of these self-organizing abilities, people and vehicles possessing computing devices can be interlinked without the need for pre-existing network infrastructure. MANETs are therefore occasional infrastructureless networks that are implemented by a set of mobile wireless hosts in a dynamic manner and without the need for any central administration.
The inherent properties of self-organization and rapid deployment capabilities make MANETs applicable in many situations where wired networks or wireless networks which require access points would be impractical.(For example, MANETs are very relevant in military applications and emergency and disaster situations where ad hoc networks which need to be flexible without any fixed base station need to be implemented.) However, MANETs are susceptible to a number of security risks due to their distributed nature and lack of a centralized control.
Security Problems in MANETs
MANETs are prone to a number of routing attacks which disrupt routing operation. One of these attacks is flooding which involves the malicious node(s) exhausting the network resources such as the network’s bandwidth and computational power. Flooding attacks may result in Denial of Service which is the situation where a computer or the entire network is incapable of providing normal services (Garg & Mahapatra, 2009).
Service to legitimate nodes will be denied as the nodes are busy forwarding unnecessary packets or making irrelevant requests for services. The limited power supply and computational capabilities of mobile devices makes them more susceptible to DOS attacks which are designed to consume the power supply of the devices and also overwhelm them with unnecessary computations.
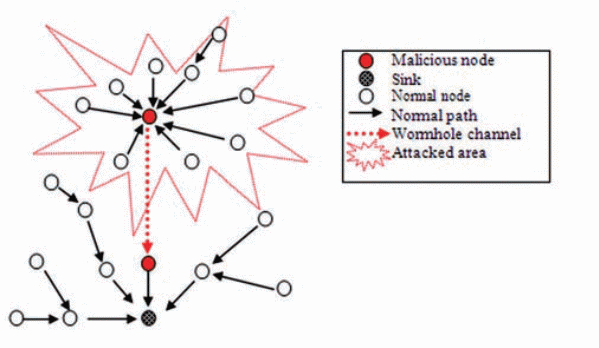
A MANET is also vulnerable to a wormhole attack which involves a malicious node sending false information claiming that it is one hop away from the sought destination. This will cause all nodes to route their data packets to the malicious node and therefore cause all routes to a destination to pass through a compromised node (Garg & Mahapatra, 2009).
A wormhole attack is initiated by two or more malicious nodes which possess superior communication resources to the regular nodes in the network. The attackers create high-bandwidth tunnels between attackers in the network and then promote this low-latency links as high-quality routes in order to attract neighboring sensors to these compromised tunnels.
The dynamic nature of the network topology in the MANET also exposes it to risk. Unlike wired networks which have a static network topology, MANETs make use of dynamic topologies which may change in a rapid and arbitrary manner (Zaiba, 2011). The computing devices which make up the MANET suffer from unreliable wireless links with each other due to the energy supply limitations that each device has.(Bandwidth restrictions and the variable capacity of each node make MANETs have diminished processing power and they have a less transmission rates than wired or WIFI systems.)
Another vulnerability comes from compromised nodes which are part of the network. As it is, a MANET is made up of autonomous nodes which join and leave the network at will. In addition to this, the physical security of nodes in a MANET cannot be guaranteed since unlike in traditional wireless networks, nodes in a MANET may exist in hostile environment where a node can be captured and then used to degrade the performance of the network or steal information from the network (Tsaur & Pai, 2008).
The portable devices and the security information they contain are vulnerable to compromise since some of them may have weak protection.(Individual nodes in a MANET have power limitations and they generally try to use the minimal power possible in order to last longer. Most nodes employ the most basic security measures since security implementations consume battery and processing power.) An attacker may gain access to these low-end devices and then use this weak link to compromise the security of the entire network. It is therefore hard for policies for safeguarding the network to be implemented since the individual nodes can be compromised when outside the network and when they join the network, they expose the MANET to the vulnerabilities they have.
Zaiba (2011) states that the threats posed by compromised nodes inside the network exceed attacks from intruders outside the network since such attacks are harder to detect. Further compounding the problem is the fact that the compromised node could be a previously trusted node in the network which behaved normally before being compromised.
Security solutions are traditionally based on access control. Access control for MANETs is especially challenging due to a number of reasons. First, these ad hoc networks do not have an infrastructure which makes it impossible to deploy access control mechanisms at access routers or base stations as would be the case in a wired or wireless cellular network.
The mobile users of the network are able to (and often do) roam freely in a large network and they require ubiquitous services at any point within the network which means that any access control mechanism should be available at each networking node’s locality so as to avoid the need for communication over the undependable multi-hop wireless link.
Tsaur and Pai (2008) reveal that the difficulty in access control in a MANET comes from the access mechanism being required to “prevent unauthorized nodes from becoming a part of the group, and establish trust among members in the absence of a trusted authority” (p.417).
The ADHOC routing protocols used in a MANET as each node is takes responsibility for dynamically discovering other nodes to communicate exposes the network to intruders. Malicious attackers can become a router and therefore gain access to the network communication and cause disruptions (Rai & Shubha, 2010).
Solutions to Security Problems
Garg and Mahapatra (2009) note that two approaches can be used to protect MANETs: proactive approach which tries to prevent attackers from initiating attacks, and reactive approach which tries to identify security threats which are already present and then react accordingly. While preventive measures are preferred to reactive measures, they may not be sufficient in MANETs. A combination of these two approaches is the most prudent means of protecting the network.
Flood Attacks
Flooding attacks can be prevented by use of the Ad hoc on-demand distance vector (AODV) protocol. Khokhar and Mandala (2006) states that in this approach, each node in the network monitors and calculates the request rate of its neighbor and if this request rate exceeds a preset limit, then the network ID of this neighbor is blacklisted and future requests from that node are ignored in future. The information on blacklisted nodes is shared within the network which leads to compromised and malicious nodes being dropped before they can cause significant damage to the network.
Intrusion Detection
The most desirable method in dealing with intruders in any network is to prevent them from accessing the network. However, this method may not work in MANETs due to the absence of a fixed infrastructure that can be used to provide security for the network. Rai and Shubha (2010) assert that while proactive approaches that thwart security threats are desirable, an intrusion detection system is still an integral component in any security solution for MANET.
An Intrusion Detection System (IDS) can be used to protect the computer systems that have been intruded upon by a malicious party. Intrusion detection is defined by Scarfone and Mell (2007) as the process of monitoring the events occurring in the network and analyzing them for “signs of possible incidents, which are violations or imminent threats of violation of computer security policies, acceptable use policies, or standard security practices” (p.2).
Intrusion detection is of great significant in MANETs since preventive measures such as encryption and authentication may at times not be effective in protecting network operations. This is so because such intrusion preventive measures cannot defend compromised nodes which may have previously obtained a trust relationship with other nodes within the network.
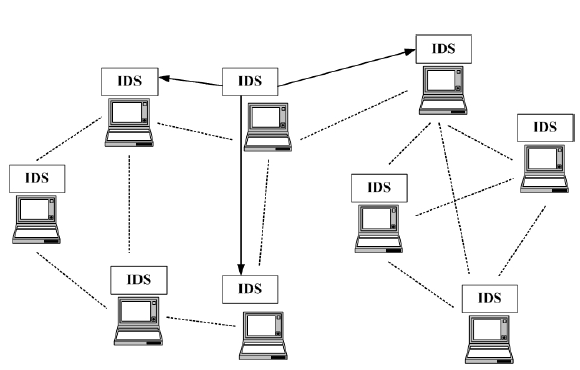
There are various architectures of an IDS that can be implemented in a MANET. One approach involves having every node in the network perform independent intrusion detection and then share its results with neighboring nodes. Such an approach involves nodes reporting anomalies to other nodes so as to track the possible intruder (Zaiba, 2011). Once the intrusion has been identified and confirmed, the response might involve reorganizing the network and removing compromised nodes or reinitializing the communication channels with new secure keys legitimate nodes.
However, this cooperative intrusion detection architecture has significant setbacks due to the huge power consumption required for all the participating nodes. Rai and Shubha (2010) propose that a cluster-based intrusion detection technique would be more efficient in a MANET. In such architecture, each node is a member of at least one cluster which is made up of nodes that reside within the same radio range.
Establishing Trust
A secure MANET should achieve the goals of “availability, confidentiality, integrity, authentication, unforgeability and non-repudiation in the network” (Yavuz & Fatih, 2010, p.2). Among the various security services for MANETs, authentication is the most important issue since knowing who you are communicating with is paramount in any network. Addressing authentication is also the most complex issue owing to the frequent networking reconfiguration and node mobility in MANETs.
The lack of a trusted authority in the MANET makes most of the cryptographic methods which are based on public key impractical since a continuously available trusted third party is required. Yavuz and Fatih (2010) propose the use of a multi-tier adaptive security protocol that makes use of hybrid cryptography and signcryption.
This multi-tire protocol achieves a secure MANET by integrating the signcryption scheme Direct Key Exchange Using Time Stamp (DKEUTS) and Elliptic Curve Pintsov-Vanstone Signature Scheme (ECPVSS).(Key management schemes have to be implemented in order to ensure secure access control in the MANET.) This security mechanism does not overload the network with unnecessary cryptographic operations and still manages to provide sufficient security for each tier.
Firewalls
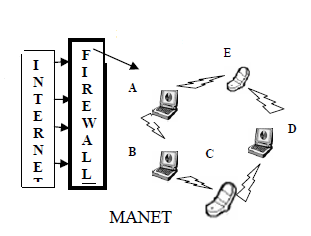
Firewalls which are logical barriers that prevent unauthorized or unwarranted communication between various parts of a network can be implemented to protect the MANET. Firewalls for wired and wireless mobile networks rely on static topologies to construct the outer security wall and therefore control access to and from the network.
Suman and Parvinder (2010) note that conventional firewalls cannot work for MANETs since these networks do not have well defined concepts of “inside” and “outside”; a hybrid firewall implementation is therefore necessary for MANETs. The hybrid firewall implementation makes use of a random selection of MANET nodes to act as firewalls. After a fixed duration of time, a new node is selected for firewall implementation based on parameters such as power available and computational resources. This approach is efficient since the responsibility for implementing the firewall is shared among the available nodes in the network.
Furthermore, Suman and Parvinder (2010) reveal that an intruder will not be able to find the entry point in the MANET since the node serving as the firewall at any one time is selected at random. This firewall implementation will therefore considerably improve the security of the MANET from outside attacks. One implementation of MANET firewalls is by having an architecture that treats port numbers as part of the IP address and therefore makes it possible to drop unwanted traffic at an early stage. Such an implementation will save battery power of the mobile devices by saving them from forwarding unnecessary traffic.
Use of Certificates
Establishment of a Public Key Infrastructure (PKI) can help to solve the problem of public key management that is inherent in MANETs. The PKI in MANETs can use a set of nodes as servers which provide certificates to the other members of the network and therefore make it possible to build certificate chains between communicating nodes. In this approach, the nodes which act as servers only provide partial certificates to the nodes they trust.
Taking into consideration every certificate issued in the network, a certification graph can be developed. This certification graph is used by two nodes to authenticate each other when they wish to exchange public keys and form a common secret (Kambourakis, et al. 2010). Since such an approach suffers from the cumbersome problem of finding a certification path in the graph, a virtual hierarch can be built among the nodes so as to reduce the time and resources spent in finding a certification path.
Wormholes Detection
As has been previously illustrated, MANETs are susceptible to wormhole attacks where malicious nodes advertize false shortest paths to a destination in order to intercept the packets that are being sent to it. Wormhole attacks are hard to identify since the attackers present their link as legitimate and replay valid data packets as the other end of the network and as such, communication is not disrupted by the presence of the wormhole (Meghdadi & Ozdemir, 2011).
The attackers replay data packets in their original format once they have read their contents, and therefore, the traditional cryptographic checks will be unable to flag the presence of the wormhole. Since it is hard to proactively defend against wormholes, detection mechanisms can be utilized to identify wormhole attacks and take necessary measures against this threat. Message Traveling Time Information Solutions can be used to prevent wormhole attacks. These solutions measure the round trip time (RTT) of a message and then use this value to determine whether a wormhole attack is in play.
Meghdadi and Ozdemir (2011) reveal that wormholes are identified based on the fact that “the transmission time between two fake neighbors created by wormhole is considerably higher than that between two real neighbors, which are within radio range of each other” (p.94). An important factor in this solution is that no specialized hardware is required for the TTM mechanism which makes it practical for all networks.
Trust based solutions can also be used in the detection of wormhole attacks. In such a solution, trust information is shared among nodes and each node can monitor the behavior of its neighbors and rate them (Meghdadi & Ozdemir, 2011). Data packets in the network then make use of the most trustworthy path as computed from the trust information. Such an approach ensures that malicious nodes are circumvented since they will have the least trust level.
Discussion and Conclusion
As the computing world becomes more portable and ad hoc, the relevance of MANETs is only going to increase. The paper has observed that MANETs have significant security risks since these networks lack a clear line of defense and malicious attacks can successfully be launched from both inside and outside the network.
From the discussions given in the paper, it has been noted that MANETs are commonly employed in applications where security is of major concern. This paper has articulated the critical nature of MANETs and asserted that the security of network is of great importance. Specialized security services may therefore be required in order to deal with some problems which are unique to these networks.
A number of preventive and detective measures that can be employed to deal with the security risks that are inherent in MANETs have been discussed. Protocols that can be used to ensure secure routing and detect wormholes have been presented and ways in which certification authority can be established in the network highlighted.
By implementing the security solutions proposed in this paper, military and civilian applications will benefit from the numerous benefits offered by MANETs while avoiding losses that may result from malicious attacks on the networks.
References
Garg, N & Mahapatra, RP (2009). MANET security issues. International Journal of Computer Science and Network Security, 9(8), 241-246.
Kambourakis, E. et al. (2010). Efficient Certification Path Discovery for MANET. EURASIP Journal on Wireless Communications and Networking, 3(2), 1-16.
Khokhar, R.H. & Mandala, S. (2006). A Review of Current Routing Attacks in Mobile Ad Hoc Networks. International Journal of Computer Science and Security, 2(3), 18-29.
Meghdadi, M. & Ozdemir, S. (2011). A Survey of Wormhole-based Attacks and their Countermeasures in Wireless Sensor Networks. IETE Technical Review, 28(2), 89-102.
Rai, P. & Shubha, S. (2010). A Review of ‘MANET’s Security Aspects and Challenges’, IJCA, 162-166.
Scarfone, K., & Mell, P. (2007). Guide to Intrusion Detection and Prevention Systems. NY: National Institute of Standards and Technology.
Suman, R.B. & Parvinder, S. (2010). Random Time Identity Based Firewall In Mobile Ad hoc Networks. NY: American Institute of Physics.
Tsaur, W. & Pai, H. (2008). Dynamic Key Management Schemes for Secure Group Access Control Using Hierarchical Clustering in Mobile Ad Hoc Networks. NY: American Institute of Physics.
Yavuz, A.A. & Fatih, A. (2010). A new multi-tier adaptive military MANET security protocol using hybrid cryptography and signcryption. Turk J Elec Eng & Comp Sci, 18(1), 1-21.
Zaiba, I. (2011). Security issues, challenges & solution in MANET. IJCST, 2(4), 108-112.